Practical aspects of using DHCP relay + option82
In this article, I would like to highlight the practical aspects of using DHCP relay + option82 as an authorization option (later this link will be in view) , as well as provide examples of the configuration of the Dlink DES-3200-10 and isc-dhcp-server switch. In almost all articles, dhcp relay interprets this: “you can take a dhcp server outside the broadcast domain”. However, for some reason they do not mention or almost do not mention that this is a good opportunity to get rid of weight gain requests within the same weight range domain. And most importantly, what I focus on - we can be sure, thanks to option82, that the request came precisely from the switch with the specified poppy and it was from the port with the specified number, and therefore - this way you can “authorize” the user.
I'll do a little bit and remind how the DHCP relay works. It will intercept the broadcast request (VLAN, and for which it is configured), wrap it in L3 and send it to the unicast specified DHCP server. Well, it will not be superfluous to remind you what makesoption82. It adds two additional parameters to the DHCP packet:
I also want to say about the methods of implementing this option in the package. There are two ways in the Dlink equipment:
')
A little deviate from the topic. The fact is that I found the dhcp_local_relay design only in Dlink equipment. I wondered why other manufacturers did not implement such a wonderful option? It turns out, implemented, and for a long time. It is called DHCP snooping.
Maybe someone will have a question: “why do we need to get rid of broadcast traffic”? The fact is that in practice I very often met with the phenomenon that when a switch fails, for example, as a result of a thunderstorm, loops occur, which leads to a broadcast storm. Of course, you guessed it, we still can’t get rid of one broadcast traffic in IPv4 - this is ARP traffic. It is he who is responsible for building the MAC-IP tables. Of course, you can prohibit this and fill in the tables manually. But, I am afraid that the inconvenience arising from this will nullify all the delights of static ARP tables.
All articles indicate that the DHCP client and the DHCP server may (must) be on different subnets - this is not true. Here is our scheme:
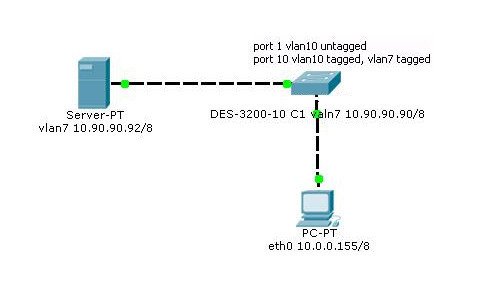
Next, I will give an example of the configurations:
DLINK DES-3200
Now the isc-dhcp-server config (isc-dhcpd-4.2.4) on
Linux big-A75F-M2 3.13.0-24-generic # 47-Ubuntu SMP Fri May 2 23:30:00 UTC 2014 x86_64 x86_64 x86_64 GNU / Linux:
Of course, this is only a poster config, but the most important thing for us is to deal with the principle of operation. Nevertheless, running into the front, I can say that I have a billing system with option82 and the dhcp_local_relay (dhcp snooping) construct, and freeradius2 with perl-selection of IP addresses from the postgres database is used as a server. But this is already beyond the scope of this article.
On the machine with the server, we run:
And if we saw something like:
That is, there are not any broadcasts, so everything is going well and it is time to start our DHCP server.
For the first time, I recommend running it just by typing in the line:
Then you will immediately see all the errors, if any, and there must be a record of the form:
Just in case, you can check after a few seconds:
Should return the UID of the process, if nothing does not display, check the configuration.
What is this check for? I remember cases when the server started, hung in memory for a few seconds and crashed. And I tried in vain to get an IP address.
If everything went well, in the logs we will find something like:
Now one very important thing is not written about it anywhere, but I reached it experimentally. The switch IP address must be on the same subnet as the addresses given to subscribers . Under no other combinations I managed to make Dlink DES-3200 (Boot PROM Version: Build 4.00.002 Firmware Version: Build 4.04.004 Hardware Version: C1) and isc-dhcp-server 4.2.4 work.
And not a big bonus, as not to die from Broadcast. Config for Dlink DES-3200 C1:
This article is not a clone and not an attempt to rewrite other people's articles in your own words. Below is a list of similar publications and differences from them. In my article, I focused on using this design as an authorization method, rather than trying to move a DHCP server outside the network.
- xgu.ru/wiki/%D0%9E%D0%BF%D1%86%D0%B8%D1%8F_82_DHCP - there is an error here, I spent a lot of time to find it. Above, I wrote about it (the ip-address of the switch must be on the same subnet as the addresses given to subscribers. For no other combinations could I get the Dlink DES-3200 connection to work (Boot PROM Version: Build 4.00.002 Firmware Version : Build 4.04.004 Hardware Version: C1) and isc-dhcp-server 4.2.4.) ;
habrahabr.ru/post/143846 - here dhcp is taken out of the network;
www.dlink.ru/ru/faq/62/228.html - here also dhcp is taken out of the network.
I'll do a little bit and remind how the DHCP relay works. It will intercept the broadcast request (VLAN, and for which it is configured), wrap it in L3 and send it to the unicast specified DHCP server. Well, it will not be superfluous to remind you what makesoption82. It adds two additional parameters to the DHCP packet:
DHCP-Relay-Circuit-Id - port number from which the request came.
DHCP-Relay-Remote-Id - (by default) the switch makadres from which the request came.
I also want to say about the methods of implementing this option in the package. There are two ways in the Dlink equipment:
dhcp_relay - adds Option82 and, as stated above, will wrap it in L3 and send it to the specified DHCP server unicast
dhcp_local_relay (DHCP Snooping) - only adds Option82 and forwards the broadcast packet further.
')
A little deviate from the topic. The fact is that I found the dhcp_local_relay design only in Dlink equipment. I wondered why other manufacturers did not implement such a wonderful option? It turns out, implemented, and for a long time. It is called DHCP snooping.
Maybe someone will have a question: “why do we need to get rid of broadcast traffic”? The fact is that in practice I very often met with the phenomenon that when a switch fails, for example, as a result of a thunderstorm, loops occur, which leads to a broadcast storm. Of course, you guessed it, we still can’t get rid of one broadcast traffic in IPv4 - this is ARP traffic. It is he who is responsible for building the MAC-IP tables. Of course, you can prohibit this and fill in the tables manually. But, I am afraid that the inconvenience arising from this will nullify all the delights of static ARP tables.
All articles indicate that the DHCP client and the DHCP server may (must) be on different subnets - this is not true. Here is our scheme:

Next, I will give an example of the configurations:
DLINK DES-3200
config vlan default delete 1-10 # Remove all ports from default VLAN create vlan VLAN7 tag 7 # Create a VLAN in which our DHCP server is located config vlan VLAN7 add tagged 9-10 # Add tagged ports 9 and 10 there (look towards the provider) create vlan VLAN10 tag 10 # Create VLAN 10 in which subscribers are sitting config vlan VLAN10 add tagged 9 -ten # Add there tagged ports 9 and 10 config vlan VLAN10 add untagged 1-8 # Add untagged ports 1-8 (subscriber ports) config ipif System ipaddress 10.90.90.90/8 # Set the IP address of the switch config ipif System vlan VLAN7 # We hang it on VLAN7 enable dhcp_relay # Activate the option config dhcp_relay option_82 policy replace # We say that if the information in the package already has something to replace config dhcp_relay option_82 remote_id default # Just save the default settings (Mac) config dhcp_relay option_82 circuit_id default # Just save the default settings (port number) config dhcp_relay add vlanid 10 10.90.90.92 # We say that all traffic from VLAN10 to intercept and send it to the DHCP server with the address 10.90.90.92 create iproute default 10.90.90.92 # Create a default route, in this example I’m not sure what I need at all, but it’s supposed to be
Now the isc-dhcp-server config (isc-dhcpd-4.2.4) on
Linux big-A75F-M2 3.13.0-24-generic # 47-Ubuntu SMP Fri May 2 23:30:00 UTC 2014 x86_64 x86_64 x86_64 GNU / Linux:
$ sudo apt-get install vlan-tools isc-dhcp-server
$ sudo vconfig add eth0 7
$ sudo ifconfig eth0.7 10.90.90.92/8
# Create VLAN7 and assign the address 10.90.90.92/8 on which we will have a DHCP server
local-address 10.90.90.92;
Theoretically, this should indicate where the socket will be created for the interception, but in practice I understood that this option is a rudiment, I tried to change and comment on anything that did not change, but as they say on Feng Shui :). In general, I must say that the server will “spit” on all your instructions and will automatically hang onto IP interfaces that fall into the subnet described in the subnet section!
if exists agent.circuit-id
{
log (info, concat ("Lease for", binary-to-ascii (10, 8, ".", leased-address) ,.
"raw option-82 info is CID:", binary-to-ascii (10, 8, ".", option agent.circuit-id), "AID:",
binary-to-ascii (16, 8, ".", option agent.remote-id)));
}
# It simply displays entries in our log file if option 82 is found.
subnet 10.0.0.0 netmask 255.0.0.0 {
pool {
range 10.0.0.155;
}
}
# Set the subnet and pool
Of course, this is only a poster config, but the most important thing for us is to deal with the principle of operation. Nevertheless, running into the front, I can say that I have a billing system with option82 and the dhcp_local_relay (dhcp snooping) construct, and freeradius2 with perl-selection of IP addresses from the postgres database is used as a server. But this is already beyond the scope of this article.
On the machine with the server, we run:
$ sudo tcpdump -i eth0.7 -e -n -t
And if we saw something like:
c0: a0: bb: 48: e5: b0> 00: 15: 17: db: e3: e0 , ethertype IPv4 (0x0800), length 345: 10.90.90.90.68> 10.90.90.92.67 : BOOTP / DHCP, Request from 48: 5b: 39: 43: 78: e5, length 303
That is, there are not any broadcasts, so everything is going well and it is time to start our DHCP server.
For the first time, I recommend running it just by typing in the line:
$ sudo dhcpd
Then you will immediately see all the errors, if any, and there must be a record of the form:
Listening on LPF / eth0.7 / 00: 15: 17: db: e3: e0 / 10.0.0.0 / 8
Sending on LPF / eth0.7 / 00: 15: 17: db: e3: e0 / 10.0.0.0 / 8
Just in case, you can check after a few seconds:
$ pgrep dhcpd
Should return the UID of the process, if nothing does not display, check the configuration.
What is this check for? I remember cases when the server started, hung in memory for a few seconds and crashed. And I tried in vain to get an IP address.
If everything went well, in the logs we will find something like:
Dec 2 20:36:17 big-A75F-M2 dhcpd: DHCPREQUEST for 10.0.0.155 from 48: 5b: 39: 43: 78: e5 (big-1001PX) via 10.90.90.90
Dec 2 20:36:17 big-A75F-M2 dhcpd: DHCPACK on 10.0.0.155 to 48: 5b: 39: 43: 78: e5 (big-1001PX) via 10.90.90.90
Dec 2 20:38:06 big-A75F-M2 dhcpd: Lease for 10.0.0.155 raw option-82 info is CID: 0.4.0.10.0.3 AID: 0.6.c0.a0.bb.48.e5.b0
Now one very important thing is not written about it anywhere, but I reached it experimentally. The switch IP address must be on the same subnet as the addresses given to subscribers . Under no other combinations I managed to make Dlink DES-3200 (Boot PROM Version: Build 4.00.002 Firmware Version: Build 4.04.004 Hardware Version: C1) and isc-dhcp-server 4.2.4 work.
And not a big bonus, as not to die from Broadcast. Config for Dlink DES-3200 C1:
config safeguard_engine state enable config safeguard_engine utilization rising 90 falling 30 state enable # This is CPU overload protection. config traffic control 1-8 broadcast enable multicast disable unicast disable drop drop threshol d 64 countdown 5 time_interval 5 # This will save clients from multiple broadcasts. enable loopdetect config loopdetect ports 1-8 state enable config loopdetect recover_timer 1200 interval 10 mode port-based # And it will save from loops if they already formed
This article is not a clone and not an attempt to rewrite other people's articles in your own words. Below is a list of similar publications and differences from them. In my article, I focused on using this design as an authorization method, rather than trying to move a DHCP server outside the network.
- xgu.ru/wiki/%D0%9E%D0%BF%D1%86%D0%B8%D1%8F_82_DHCP - there is an error here, I spent a lot of time to find it. Above, I wrote about it (the ip-address of the switch must be on the same subnet as the addresses given to subscribers. For no other combinations could I get the Dlink DES-3200 connection to work (Boot PROM Version: Build 4.00.002 Firmware Version : Build 4.04.004 Hardware Version: C1) and isc-dhcp-server 4.2.4.) ;
habrahabr.ru/post/143846 - here dhcp is taken out of the network;
www.dlink.ru/ru/faq/62/228.html - here also dhcp is taken out of the network.
Source: https://habr.com/ru/post/252929/
All Articles