We read the correspondence of Ubank customers with support

I already wrote about the vulnerability in the Alfa-Bank mobile application , which allowed to get statements for any bank client.
This time I decided to check out the Ubank payment acceptance service mobile application.
To analyze the requests sent to the server, I again used the Fiddler program. How to set it up, I will not re-describe, who are interested, can read about it in the above article . The only thing I did differently was to reproduce requests not through the Postman plug-in on Google Chrome, but using the Composer tool built into Fiddler.
Investigating the requests sent by the application to the server, I found that when downloading the correspondence history with the support, no check is performed to bind the message identifier to the user's session, and accordingly, sorting through the message id, we can receive the other users' correspondence with support.
')
So, using Fiddler, I recorded a request to receive the contents of the message from the correspondence with the support:

Then I opened it in Composer:
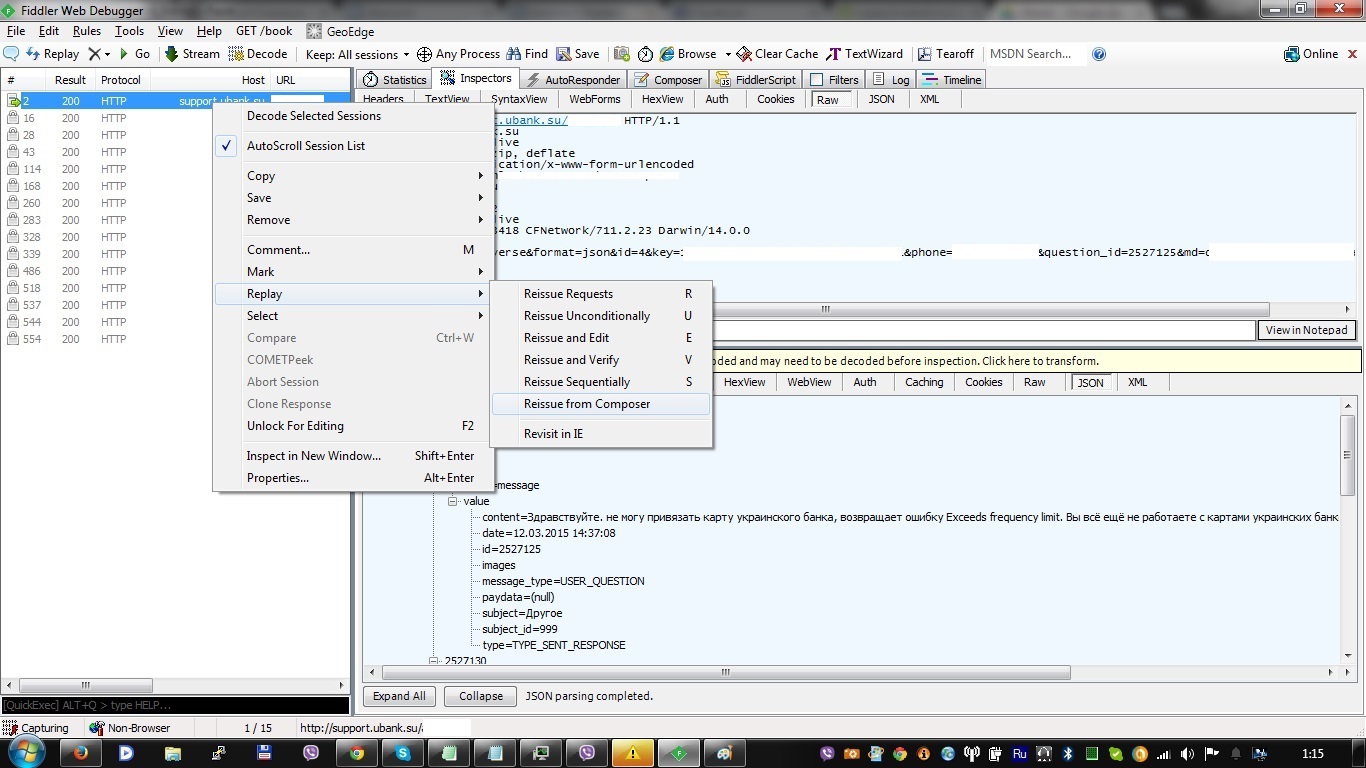
The request increased the value of the parameter question_id by one and sent it to the server.
In response, I received the contents of someone else's message:
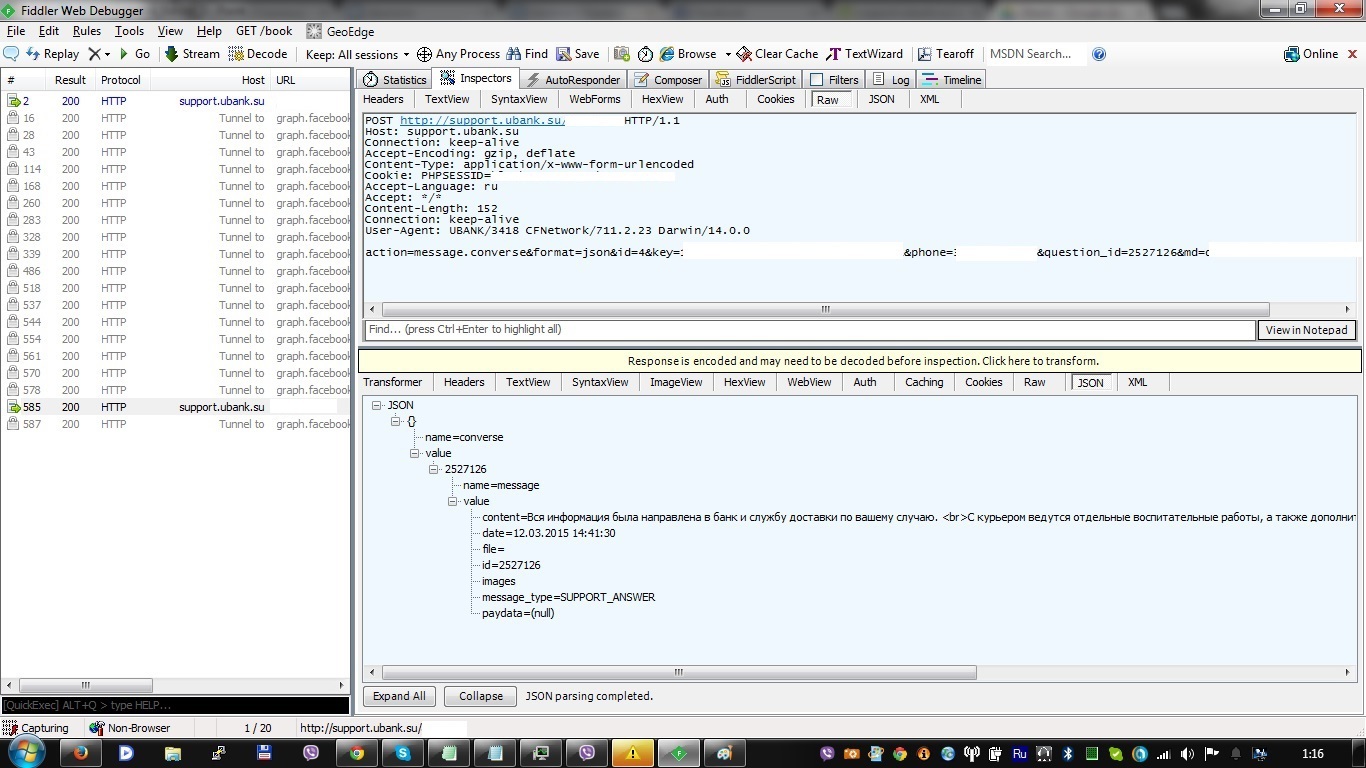
Upon further analysis, we managed to find out that, in addition to the id, the messages were not checked for binding to the user's session and the files sent in the message.
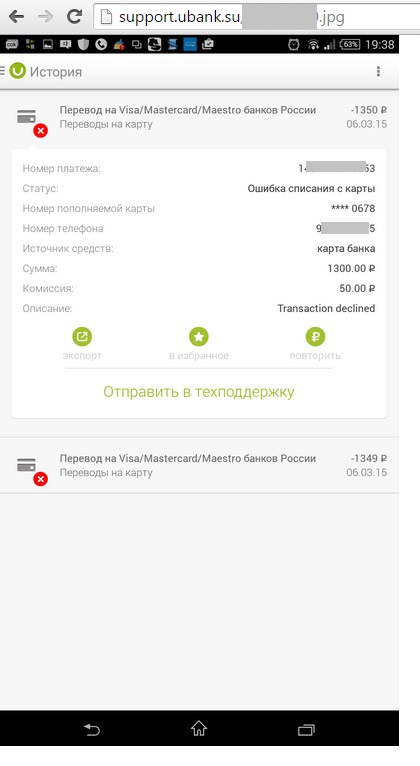
As with the Alfa-Bank mobile application, the Ubank application also did not use SSL Pinning , which in turn made it possible to carry out a MitM attack if the attacker manages to install his certificate on the victim's device, which is realizable in the following ways:
1) the user does everything himself because of ignorance. For example, to access the wi-fi access point in a public place
2) the purchased used phone may already contain a malicious certificate installed
3) the certificate is installed on the phone with iOS in a few seconds if it happens to be in the hands of an attacker (for example, he asked to call)
4) infection of network equipment through a vulnerability
Conducting an MitM attack on this application is fraught with the loss of its financial resources, since the application's functionality allows you to replenish the wallet with a card, make p2p transfers and other financial transactions. Also, when making a victim of payment, an attacker can replace his account details, thus redirecting funds to his account.
Unfortunately, my communication with representatives of the company did not lead to anything, except to a dispute over the feasibility of SSL Pinning.
At the moment, after more than 2 months after my contact with the company, the vulnerability remains open.
Source: https://habr.com/ru/post/252877/
All Articles