Connect users to the corporate cloud

Connection to the cloud can be viewed from two sides:
- technology connecting end users to the cloud,
- connecting the local infrastructure of the corporate client to the IaaS infrastructure in the cloud.
In this post, we will look at the end-user connection to the cloud service: possible methods, options and tools.
Often, many small and even medium-sized companies do not have their own local IT infrastructure, preferring to deploy all the solutions and services necessary for a business in the cloud of an IaaS provider (for example, such as IT-GRAD). This approach is economically justified, profitable and convenient. The only thing that sometimes raises questions and disputes is the choice of the appropriate connection method. What is better, more convenient, safer in a given situation? We'll figure out.
')
To connect to cloud services by end users, as a rule, combinations of various solutions are used. Consider them individually, our choices for today are as follows:
- RDP client
- Remoteapp,
- Web access,
- Remote access VPN,
- VPN site-to-site
- DirectAccess,
- VDI.
As practice shows, the choice of a particular remote connection tool depends directly on the needs of a particular client / employee / department. It may be more convenient for an accountant, analyst, marketer to use a web-based interface, while a developer, application tester, ERP consultant can use the RDP connection option or something else. Consider each technology separately.
RDP client (connection via remote desktop)
Remote desktop is one of the most common, convenient, versatile and frequently used tools that enable remote access to a workplace, which is deployed, including in the cloud.
The basis of this type of access is RDP (Remote Desktop Protocol) - a proprietary application-level protocol. It is he who ensures the remote work of the user with the computer on which the terminal access service is running. Today, there are clients for almost all operating systems of the Windows, Linux, FreeBSD, Mac OS X, iOS, Android, Symbian family.
The remote desktop client can be further configured. The user can save their username / password so that when connecting, do not enter them again each time. However, from a security point of view, it’s better not to. You can also customize the screen settings, keyboard layouts, playback sounds, and more. If there is a need to use the local resources of the computer from which the remote desktop connection is being made, and the clipboard, this is also “please”. In addition to the above options, the user can change the graphics settings, which in the case of low Internet speed will make work more comfortable.
| Service Provider Requirements | Client connection |
| The presence of a dedicated terminal server (Terminal Server). | Run RDP client (Windows, Linux, FreeBSD, Mac OS X, iOS, Android, Symbian). |
What it looks like from the user: using the RDP client, the user connects to the terminal server and sees the desktop of the remote system. Within an established session, it can launch applications deployed on a terminal server.
But what about security and how can such a connection be considered reliable?
If you select the default settings when connecting via RDP, weak encryption will be used when implementing remote access and traffic can be decrypted along the way. However, there are a number of additional methods that will help protect and optimize RDP.
An example is the Remote Desktop Gateway technology, previously known as Terminal Services Gateway (TSG).
Remote Desktop Gateway is a tool through which remote authorized users can connect to both the resources of the physical network of an enterprise and the network in the cloud of an IaaS provider.
Remote Desktop Gateway uses Remote Desktop Protocol (RDP) over HTTPS, while ensuring a secure connection with a secure encryption method between remote Internet users and resources in the cloud that are necessary for user applications to work.
RemoteApp (Remote Terminal Services Applications)
The RemoteApp solution is a variation of the above option. What are the similarities and differences?
The fact is that RemoteApp is a tool that allows you to organize remote access to installed applications on a server in the cloud.
The client can still use the applications as if they were installed locally. If at this stage of the narrative the difference is not quite obvious, move on.
Considering the option with RDP, we talked about connecting directly to a remote desktop, giving the opportunity to work with an instance of the operating system. The user sees the desktop, programs, icons, control panel, and more. With the RemoteApp option, the situation is different: the user sees only the launched remote application within his physical device.
The client, for example, launches the Microsoft Word shortcut located on the desktop of its local computer, after which the authentication process is initiated. In this case, Word is not installed on the local user station. After successful authentication / authorization, the application starts and is ready to go. How is this implemented?
The application is “published” on the remote server. And when the shortcut is started using RemoteApp, it connects to the remote server. As part of the launch of the application shortcut, an RDP session is formed, after which the application itself starts and runs without displaying the remote desktop. This process for the user creates the effect of local installation of the application.
This option will be useful, for example, in the following cases:
- When you need to restrict access to specific applications.
- When the user needs to combine work on the local machine with the use of some application rendered to the cloud.
- When the application should be available in specific conditions and at low Internet speed.
| Service Provider Requirements | Client connection (possible options) |
| Availability of a configured RD Session Host Server with a list of relevant programs (RemoteApp Programs list) placed on it. |
|
What it looks like from the user’s side: for a user, the launched remote terminal services applications look as if they were executed directly on the user's system. The remote desktop of the remote system with applications running on it is displayed, and the applications are integrated into the user's desktop with window scaling and its own application icon in the taskbar.
Terminal Services Web Access
Access to certain applications and desktops in the cloud (both options considered earlier) can be organized using a browser that is installed on the vast majority of devices today. For the user, this option looks like this: launches the browser, enters the required address, authenticates it, and then works with the published application / applications or remote desktop / desktops. In this case, application shortcuts are placed on a pre-configured web page.
| Service Provider Requirements | Client connection |
| The presence of a dedicated terminal server (Terminal Server). Example: OS Windows Server 2008/2012 + TS Web Access service. | Use the URL to access the resource through a web browser. |
What it looks like from the user: using a web browser, the user enters the corresponding URL to access the resource, is authenticated and authorized, and then gets access to applications or remote desktop using the web.
Another option to connect to cloud services is to connect VPN.
Recall that VPN (Virtual Private Network) is a virtual private network, being the generic name of a technology that allows you to provide one or more reliable network connections over an insecure network such as the Internet, using various cryptographic tools.
There are two types of VPN tunnels: Remote access VPN and Site-to-site VPN. Consider each of them in more detail.
Remote access VPN
Another convenient, secure and frequently used tool for connecting to cloud resources is Remote access VPN.
| Service Provider Requirements | Client connection |
| Availability of configured VPN device / server. |
|
What it looks like from the user side: on the client side, an outgoing VPN connection is established, which the user uses as needed. To implement access to a remote resource, the user launches a VPN shortcut, enters his credentials and, upon successful authentication, gets access to the necessary resources. In other words, the user's computer, due to the IP configuration parameters issued during the VPN connection, enters the virtual remote office network in the cloud and can use resources as if it were directly in the office (in the local network) of the company.

To access the file server resources in the cloud, each user needs to use a VPN connection. After successful authentication and authorization, the user gets access to File_server1.
Site-to-site VPN
However, such a scenario is possible: the company's employees from their non-virtualized, non-cloud infrastructure need to connect to a resource in the cloud.
What would it look like with the already familiar implementation of Remote access VPN?
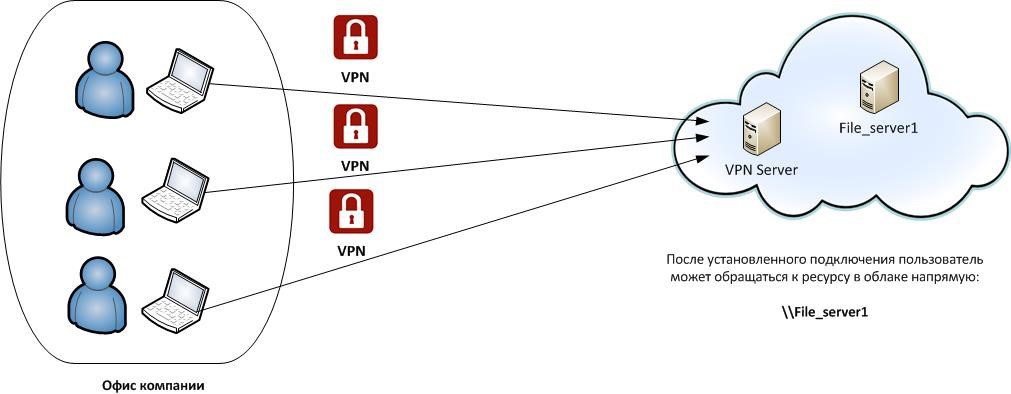
Each user, before accessing resources in the cloud, establishes a separate VPN connection to the VPN server, and then accesses the resources of the file server \\ File_server1. What does the same thing look like with Site-to-site VPN? Let's start with the definition.
Site-to-site VPN - implies the presence of two devices (for example, VPN Server 1 and VPN Server 2 of Figure 4) between which a tunnel is established. In this case, users are behind devices in local networks, and their computers do not need to install any special software.
For example, if the number of users in a company who need access to file server resources is large enough, it is easier to implement a Site-to-Site VPN connection at the level of a VPN server in the cloud and a VPN server at the company's office. To do this, you need to additionally deploy a VPN server at the company's office, and the process of accessing file server resources will look like this:
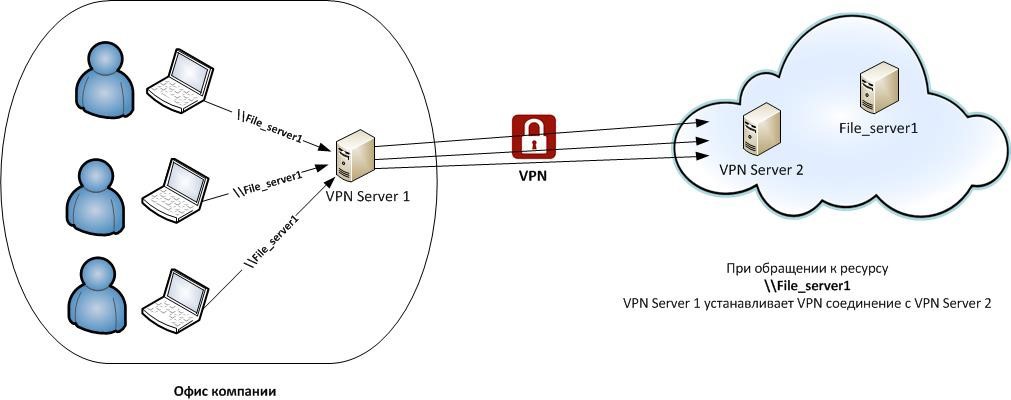
In such a scenario, the user accesses the resource in the cloud directly. In our example, the \\ File_server1 resource in the cloud subnetwork with this access VPN Server 1 establishes a VPN connection with VPN Server 2 in the cloud, after which the user sees the contents of the requested resource. On the client side, there is no need to create an outgoing VPN connection. This configuration is called Site-to-Site VPN.
| Service Provider Requirements | Client connection |
| Having two configured VPN servers. Example: a VPN server in a company and a VPN server in the cloud. |
|
Directaccess
In addition to the usual implementations of VPN, which can be used for remote connection to the cloud, there is another technology that can rightly be called rather "young." This is DirectAccess.
DirectAccess allows you to realize the ability to remotely access corporate network resources in the following way: as soon as a user's computer connects to the Internet, it immediately gains access to both Internet resources and the entire corporate network.
That is, a user computer that is configured as a DirectAccess client automatically establishes a tunnel to the DirectAccess server and through it gains access to the entire corporate network. At the same time, no additional actions are required from the user. The tunnel between the client and the DirectAccess server is established automatically, and this process is completely transparent to the user. You do not need to run any VPN connections, you do not need to enter credentials - username and password, pin code for a smart card, etc. Moreover, if the connection with the Internet is lost for some time (and, of course, the tunnel is broken), and then restored, then again automatically, without user intervention, the tunnel to the corporate network is also restored.
| Service Provider Requirements | Client connection |
|
|
VDI (desktop virtualization)
Since the high mobility of business today requires constant availability of applications for employees, the approach to the implementation and solution of such tasks is constantly changing. Today, the virtual desktop infrastructure (VDI, Virtual Desktop Infrastructure) is implemented on many cloud platforms of corporate IaaS providers. This technology allows you to centralize user workstations on virtualization servers, creating a single point of control, deployment and maintenance.
On the client side, everything is just as simple: you need an Internet connection and a desktop PC / laptop / mobile phone / tablet. If these conditions are met, the user has access to his virtual workplace from anywhere in the world, and this is a merit of VDI.
Virtualization of desktops in practice may look as follows.
The server is allocated in the cloud of the IaaS provider on which the hypervisor is installed. On it, in turn, separate virtual machines are deployed - usually with the client OS. The client program is launched on the user's end device and the connection to the infrastructure takes place. This type of connection, at first glance, is not much different from RDP connection. But what is the difference?
In the case of a RDP connection to a terminal server, this is a separate session on a shared Windows server. In the case of VDI (desktop virtualization) , this is a separate, isolated container with the client OS. Thus, two key differences can be distinguished: server OS versus client and separate session (which shares resources of one OS) versus isolated virtual machine.
When operating in terminal mode, isolation occurs at the session level, and if the application causes a crash at the OS level, then the rest of the users running on the same server will restart along with the user who started the application. And when using desktop virtualization, only one virtual machine will be rebooted.
| Service Provider Requirements | Client connection |
| Deployed virtual desktop infrastructure VDI (solutions from VMware, Citrix, Microsoft). | The user gets his own virtual PC to which you can connect using a thin client, desktop PC, laptop, tablet, mobile phone. |
In conclusion, we present a general table with the considered technologies of connecting users to the cloud.
| Requirements on the side of the service provider | Client connection | |
| RDP client | Availability of a dedicated terminal server (Terminal Server) | Run RDP client (Windows, Linux, FreeBSD, Mac OS X, iOS, Android, Symbian) |
| Remoteapp | Availability of a configured RD Session Host Server with a list of relevant programs (RemoteApp Programs list) placed on it |
|
| Web access | Availability of a dedicated terminal server (Terminal Server) + TS Web Access service | Use the URL to access the resource through a web browser. |
| Remote access VPN | Having a configured VPN server |
|
| VPN site-to-site | Having two configured VPN servers. Example: VPN server in the head office and VPN server in the cloud |
|
| Directaccess |
|
|
| VDI | Deployed VDI Virtual Desktop Infrastructure (VMware, Citrix, Microsoft solutions) | The user gets his own virtual PC to which you can connect using a thin client, desktop PC, laptop, tablet, mobile phone. |
Additionally, the options for connecting the company's local infrastructure to the IaaS infrastructure in the cloud can be found in our corporate IaaS blog, in the article “ Connecting to the corporate cloud ”.
Source: https://habr.com/ru/post/252861/
All Articles