Nginx and https. We get class A +
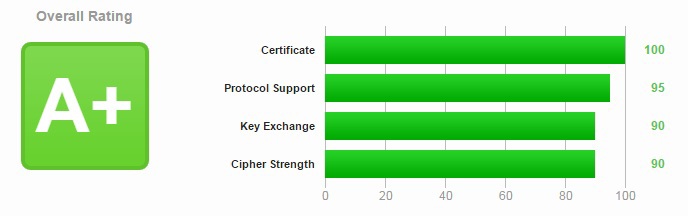
Recently I remembered that there is such a service - StartSsl, which distributes trusted certificates to domain owners for personal use absolutely free of charge. Yes, and the weekend got free. So now I’ll write how to configure HTTPS in nginx so that when checking in SSL Labs I get an A + rating and protect myself from the latest bugs by cutting SSL.
So let's get started. We will assume that you have already registered with StartSsl, have been personally verified and received the coveted certificate. To begin, I will publish the final config, and after that I will sort it out.
Here's what I got:
')
server { server_name dsmirnov.pro www.dsmirnov.pro; listen 80; return 301 https://dsmirnov.pro$request_uri; } server { listen 443 ssl spdy; server_name dsmirnov.pro; resolver 127.0.0.1; ssl_stapling on; ssl on; ssl_certificate /etc/pki/nginx/dsmirnov.pro.pem; ssl_certificate_key /etc/pki/nginx/dsmirnov.pro.clean.key; ssl_dhparam /etc/pki/nginx/dhparam.pem; ssl_session_timeout 24h; ssl_session_cache shared:SSL:2m; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_ciphers kEECDH+AES128:kEECDH:kEDH:-3DES:kRSA+AES128:kEDH+3DES:DES-CBC3-SHA:!RC4:!aNULL:!eNULL:!MD5:!EXPORT:!LOW:!SEED:!CAMELLIA:!IDEA:!PSK:!SRP:!SSLv2; ssl_prefer_server_ciphers on; add_header Strict-Transport-Security "max-age=31536000;"; add_header Content-Security-Policy-Report-Only "default-src https:; script-src https: 'unsafe-eval' 'unsafe-inline'; style-src https: 'unsafe-inline'; img-src https: data:; font-src https: data:; report-uri /csp-report"; } In the first section, everything seems to be clear, any input via http with any URI redirect with the same URI in the https scheme.
Let's start the analysis of the server section for https. 443 ssl spdy; immediately turn on spdy. Here is the difference in the picture:

The next step is to enable ssl_stapling on; - we allow the server to attach OCSP responses, thereby reducing the time of loading pages for users. A chain of certificates (domain - intermediate authorization center - root authorization center) may contain 3-4 levels. And at each level, the browser must establish a connection and receive a certificate. You can send all the certificates (including intermediate: it was for this that the TCP sending windows were configured so that the chain of certificates would fit in one packet forwarding) at a time, then the browser checks the entire chain locally and only requests the root (which in most cases is already on client). For this function to work, it is necessary to describe the resolver - I have raised my own DNS server, so 127.0.0.1 is specified as a value, you can specify 8.8.8.8, but many have cursed it recently. What is ssl on; I think it makes no sense to tell.
Further by the directives ssl_certificate and ssl_certificate_key we specify the paths to the certificates obtained via StartSsl. You already have 3 files: domain.ru.key, domain.ru.crt and sub.class1.server.ca.pem. Copy the keys in (my case) / etc / pki / nginx.
Do not forget that the pem file for nginx should be bundled with a CA certificate (It should be 3 to 2 files.):
cp domain.ru.key /etc/pki/nginx cat domain.ru.crt sub.class1.server.ca.pem > /etc/pki/nginx/domain.ru.pem Now about ssl_dhparam /etc/pki/nginx/dhparam.pem; - it is necessary for us to earn Forward Secrecy. Direct secrecy means that if a third party recognizes a session key, then it can only get access to data that is protected only by that key. In order to maintain perfect forward secrecy, the key used to encrypt the transmitted data should not be used to obtain any additional keys. Also, if the key used to encrypt the transmitted data was derived (derived) from some other key material, this material should not be used to obtain any other keys.
You can generate a key like this:
openssl dhparam -out /etc/pki/nginx/dhparam.pem 4096 Further simple settings ssl_session_timeout 24h; and ssl_session_cache shared: SSL: 2m ;, which do not require special descriptions - the expiration date of the session and the size of the memory allocated for storing the cache - my blog is small, so 2 MB is enough.
Further - important parameters : ssl_protocols TLSv1 TLSv1.1 TLSv1.2; and ssl_ciphers kEECDH + AES128: kEECDH: kEDH: -3DES: kRSA + AES128: kEDH + 3DES: DES-CBC3-SHA:! RC4:! aNULL:! eNULL:! MD5:! EXPORT:! LOW:! SEED:! CAMIA :! IDEA:! PSK:! SRP:! SSLv2; - here we indicate that we want only TLS and with the second line we burn all SSL with a hot iron. In the light of the latest files with SSL - very important, as I advise you. Well, with the ssl_prefer_server_ciphers on directive ; we force nginx to strictly observe this.
Directive add_header Strict-Transport-Security "max-age = 31536000;"; tells browsers how much they need to remember these security requirements for my domain. In this case - 1 year. By the way, if you write a directive like this: add_header Strict-Transport-Security “max-age = 31536000; includeSubDomains; preload; , then these conditions will apply to all domains of the third and higher level of your domain. Be careful here! I originally described it this way, but since StartSsl issues certificates for a limited number of subdomains, I stumbled upon the inability to even get to my subdomains that serve a variety of admin areas, only those for which trusted certificates were issued. Therefore, I chose the first option for myself.
Next - add_header Content-Security-Policy-Report-Only “default-src https :; script-src https: 'unsafe-eval' 'unsafe-inline'; style-src https: 'unsafe-inline'; img-src https: data :; font-src https: data :; report-uri / csp-report "; - I really deeply have not studied the properties of this title. Content Security Policy (CSP) is a new standard that defines Content-Security-Policy and Content-Security-Policy-Report-Only HTTP headers that tell the browser a white list of hosts from which it can download various resources.
Temporarily, I took this line from a Yandex article about the use of CSP in them, you can read in detail here: http://www.html5rocks.com/en/tutorials/security/content-security-policy/ .
That seems to be all. Several references where you can check the results of their own and others' works:
1. SPDY Check is the result of my work .
2. SSL Labs - checking the quality of protection of your server .
Good luck, colleagues!
Source: https://habr.com/ru/post/252821/
All Articles