OpenSMTPD + UW IMAP as an alternative to heavy mail systems
 Almost everyone who has servers with domains associated with them has to deal with the mail one way or another, at least with the availability of webmaster / postmaster / abuse @ domain addresses.
Almost everyone who has servers with domains associated with them has to deal with the mail one way or another, at least with the availability of webmaster / postmaster / abuse @ domain addresses.Someone teaches M4 and configures built-in sendmail, someone uses third-party services (for example, from Google), someone - raises the standard postfix + courier-imap + mysql bundle (or equivalent).
I was lazy to do the first, the second — I didn’t want for ideological reasons, and the third was too redundant. Therefore, I found my “middle way”, which I want to talk about in this article.
Prerequirements
When writing this guide, I assumed that the user is able to interact with * nix-systems through the console, can install the packages of his distribution and owns at least one text editor for editing configs. As an example, I will install packages on Arch Linux, since this is my home distribution.
Formulation of the problem
Before you do something you need to understand why to do it. The described configuration makes sense if:
- The number of local users is small and it is permissible for them to create entries in / etc / passwd
- The number of accepted domains is> 1, otherwise “default sendmail” rescues us OR
- Some extra things are needed, such as SSL / TLS or authentication OR
- Server configuration is insufficient to run heavy MTAs there.
In my case, all the points coincided: a small virtual, on which I park a dozen domains for friends and acquaintances.
')
Installing UW IMAP is an optional part. I did not install it until I had additional users in the system, because I myself went to ssh without any problems and made a mutt.
Installation and initial configuration of OpenSMTPD
In Arch Linux installation takes 5 seconds :-)
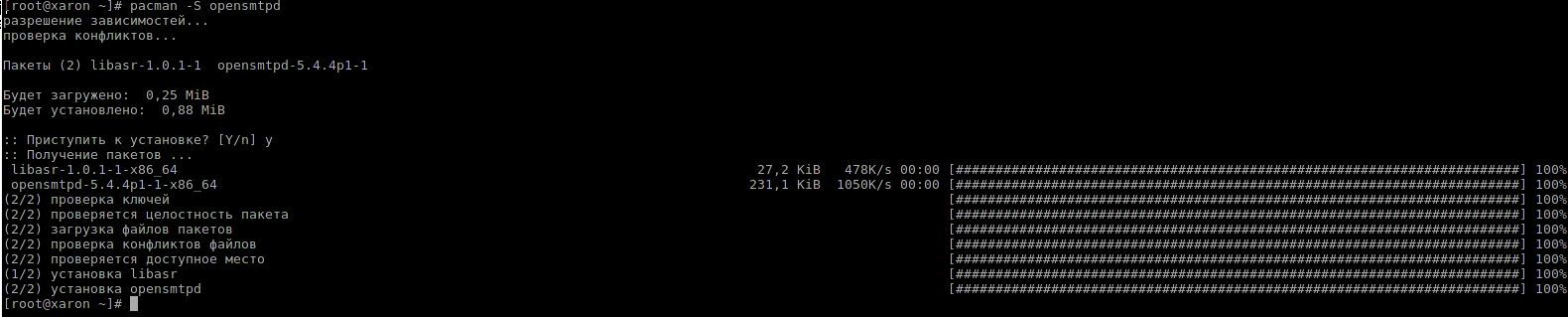
The configuration consists of a single smtpd.conf file and optional files with tables. My initial config looks like this:
smtpd.conf
# ipv4 limit mta inet4 # 25 all, server.com listen on 0.0.0.0 port 25 hostname server.com # . table aliases { root = xxx, abuse = xxx, postmaster = xxx, webmaster = xxx } table domains { server.com, domain1.ru, domain2.net, domain3.in } # (mbox) accept from any for domain <domains> alias <aliases> deliver to mbox # , ( mail ) accept from local for any relay # - reject from any for any As you can see - nothing complicated, any mail passes through all the chains of reject / accept until it falls under any rule.
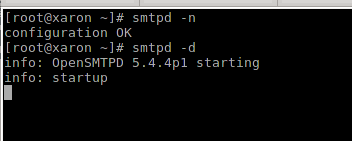
Health check
Now you can check if the mail is working. Run smtpd -n to check the config and smtpd -d to run in the foreground with logs in stdin:
We are trying to send mail to root@domain1.ru ...
And we look at the output of the server


We are trying to send mail to root@domain1.ru ...

And we look at the output of the server

Mutt confirms - mail delivered!
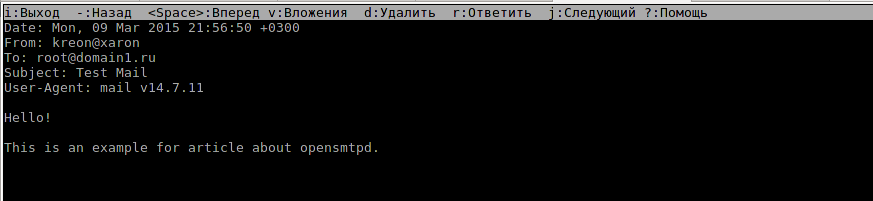
This minimal configuration is quite enough for receiving technical mail for a dozen or so domains.
SMTPS / TLS and Authentication
In opensmtpd, the authenticated user becomes local. Authentication is enabled with the auth (or auth-optional ) keyword in the listen string, but you must first configure smtps / tls. A trusted certificate can be obtained in different places, for example from StartSSL. In any case, we assume that you have 3 PEM files:
- server.crt - server certificate
- server.key - private key from the certificate
- cachain.crt - chain of supporting certificates
Now we can enable smtps / tls and authentication:
smtpd.conf
# , ca pki server certificate "/etc/ssl/certs/server.crt" pki server key "/etc/ssl/private/server.key" pki server ca "/etc/ssl/certs/cachain.crt" # ipv4 limit mta inet4 # 25 all, server.com, startssl listen on 0.0.0.0 port 25 tls pki server hostname server.com auth-optional # 465 all, server.com, ssl , ip listen on 0.0.0.0 port 465 smtps pki server hostname server.com auth mask-source # . table aliases { root = xxx, abuse = xxx, postmaster = xxx, webmaster = xxx } table domains { server.com, domain1.ru, domain2.net, domain3.in } # (mbox) accept from any for domain <domains> alias <aliases> deliver to mbox # , ( mail ) accept from local for any relay # - reject from any for any Now clients can send mail outside with ssl and authentication.
We are testing
Configure smtp-server:
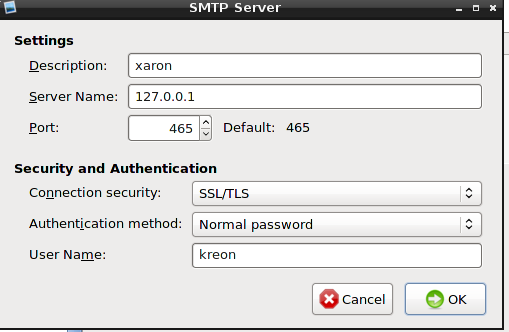
We send the letter:
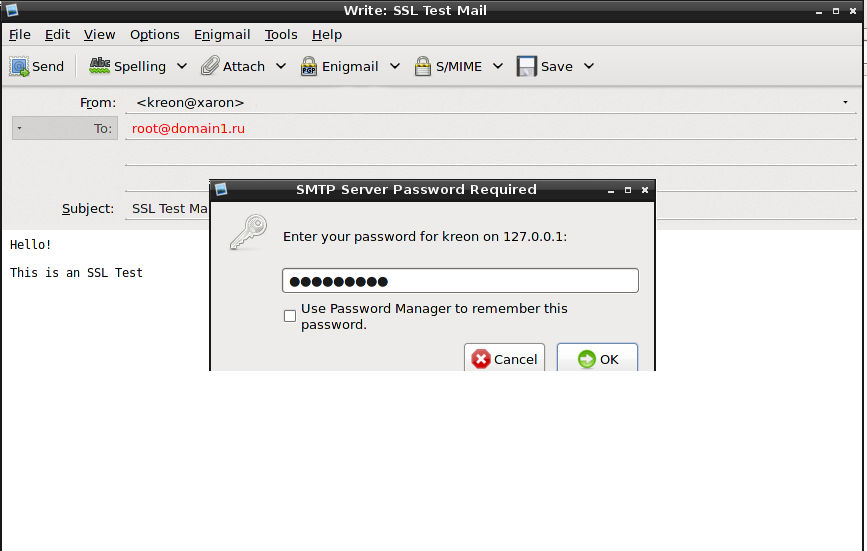
We look at the output of the server:
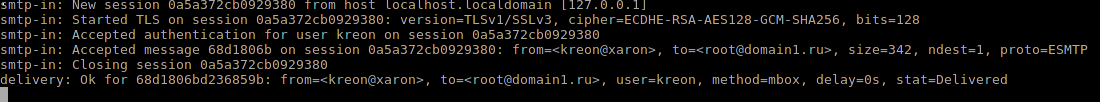

We send the letter:

We look at the output of the server:

Mutt (note the Received header):
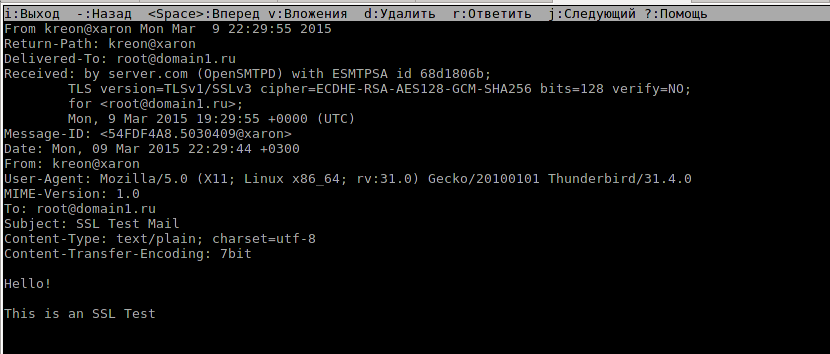
Antispam and stuff
For example, you can add antispam via spampd .
smtpd.conf
# , ca pki server certificate "/etc/ssl/certs/server.crt" pki server key "/etc/ssl/private/server.key" pki server ca "/etc/ssl/certs/cachain.crt" # ipv4 limit mta inet4 # 25 all, server.com, startssl listen on 0.0.0.0 port 25 tls pki server hostname server.com auth-optional # 465 all, server.com, ssl , ip listen on 0.0.0.0 port 465 smtps pki server hostname server.com auth mask-source # spampd - listen on 127.0.0.1 port 10026 tag Filtered # . table aliases { root = xxx, abuse = xxx, postmaster = xxx, webmaster = xxx } table domains { server.com, domain1.ru, domain2.net, domain3.in } # mbox accept tagged Filtered for domain <domains> alias <aliases> deliver to mbox # spampd accept from any for domain <domains> relay via "smtp://127.0.0.1:10025" # Filtered - - - reject tagged Filtered # , ( mail ) accept from local for any relay # - reject from any for any And again, nothing complicated, easily configured by analogy with a firewall or other in-line filter.
Install and configure UW IMAP
As I already wrote, this part is optional, if on the server one user is a sysadmin, then most likely imap is not needed there.
Installation:
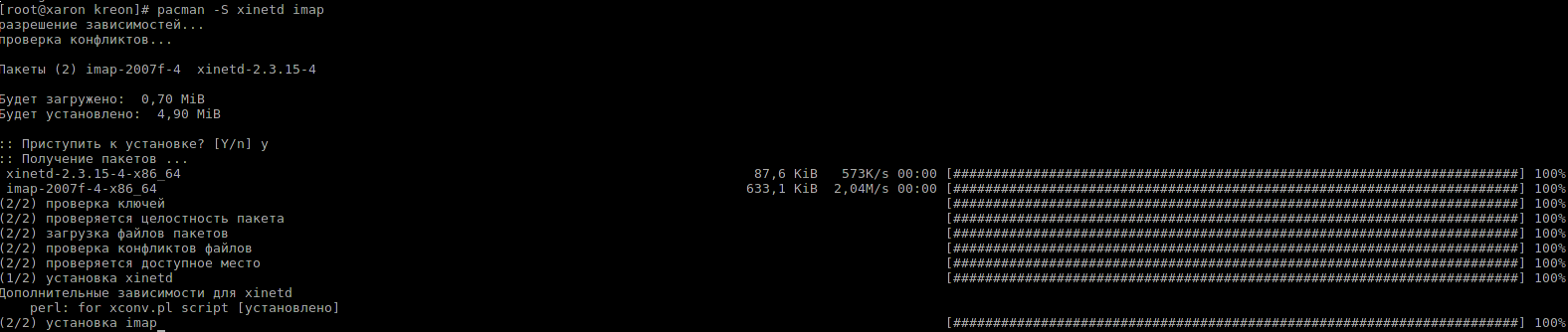
Setup:
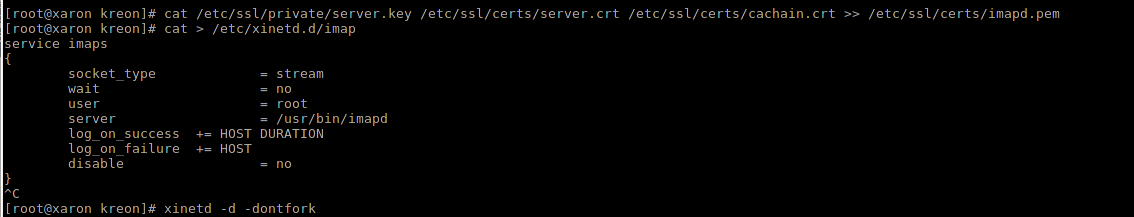
First, from the key, server certificate, and CA certificates, we create a PEM file for imapd (its name is fixed), then we create xinetd-unit for xinetd and start xinetd, respectively. Everything, hooray :-)
We are testing
Set up an email client to work with IMAP
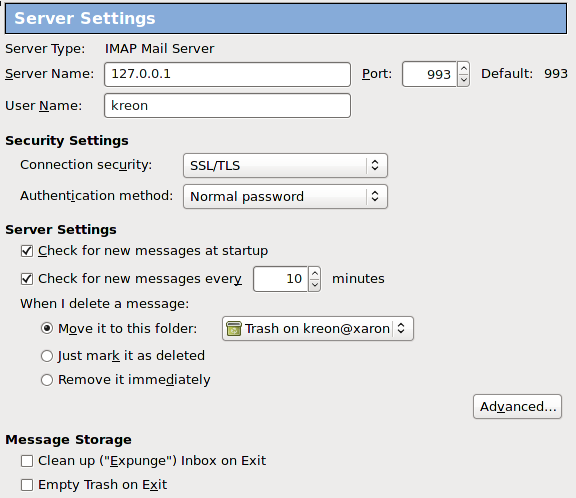
We check mail and compare it with what was in MUTT
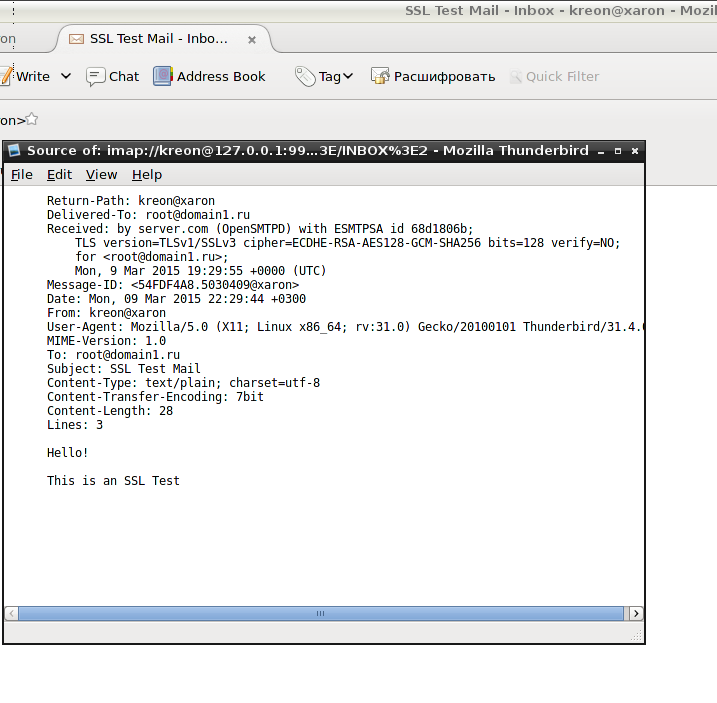

We check mail and compare it with what was in MUTT

Total
We received a full-fledged mail system, with SSL / TLS and authentication, capable of working even on a microwave and without requiring hours of thoughtful reading of mana. Optionally, you can expand it further by adding for example DKIM, backup MX, Greylisting and more. As a bonus: OpenSMTPD is made by the OpenBSD team, which means there is very little chance of a critical vulnerability there.
Thanks for attention.
Source: https://habr.com/ru/post/252567/
All Articles