Personal data of users of Rozetka.ua in public access
I came across this data source by chance. In my opinion, it's time to check what data our users and our projects give to users.
For reasons that I do not want to explain, I needed to get feedback on products from rozetka.ua. When the site does not have a public API, then you have to look for more sophisticated options. Parsing the HTML code of the pages was left as an extreme option and began to search for more optimal ways to extract data.
First I discovered the mobile version of the site and, as it turned out, it is a SPA . All data using simple API pulled through AJAX-requests. There is access to everything that is required to receive feedback:
')
Category List:
Product List:
Review list:
The value of p [0], by the way, needed to be URL encoding 2 times. Why this was done is a mystery.
As soon as I got to get feedback, the following picture appeared to my eyes:
As you can see, besides the username is present and his email. It is necessary to mention a few facts about the reviews in this online store:
So, we have a large database of emails with names, and sometimes with last names, targeted for certain groups of goods. Since I have never dealt with the internals of the "Socket", I decided that this answer might be corrected soon and forgot about this site for a month.
In February of this year, “Rosette” rolled out a redesign and I decided to check the status of the vulnerability in the mobile version. It turned out that the API version was updated to the 3rd (apparently, there was a second version earlier), in which the structure of requests and responses was slightly changed. Going to the feedback page and opening the developer tools showed that email no longer comes in response to the request. Only the name field remains. On this one could stop and forget about this case. But interest overwhelmed me and I decided to execute the query on the old link. To which the browser successfully returned the same answer to me. The old API is not closed, the vulnerability is in place.
The next day, a letter was written to the developers of the online store. I was promptly answered, they confirmed the vulnerability and after a few hours the API of the second version was covered up. As I understand it, this API was originally used for internal needs, and when it was brought to the public, the email remained. After the arrival of the third version, the second version continued to work.
As always, the simplest inattention in our profession can lead to sad consequences ...

For reasons that I do not want to explain, I needed to get feedback on products from rozetka.ua. When the site does not have a public API, then you have to look for more sophisticated options. Parsing the HTML code of the pages was left as an extreme option and began to search for more optimal ways to extract data.
First I discovered the mobile version of the site and, as it turned out, it is a SPA . All data using simple API pulled through AJAX-requests. There is access to everything that is required to receive feedback:
')
Category List:
http://m.rozetka.ua/?action=getJSONDataFromAdapter&m[0]=getOffersSections&p[0]=['123',0,15] Product List:
http://m.rozetka.ua/?action=getJSONDataFromAdapter&m[0]=getOffersByParams&p[0]=['123',{},0,15] Review list:
http://m.rozetka.ua/?action=getJSONDataFromAdapter&m[0]=getCommentsByOffer&p[0]=['123',0,15] The value of p [0], by the way, needed to be URL encoding 2 times. Why this was done is a mystery.
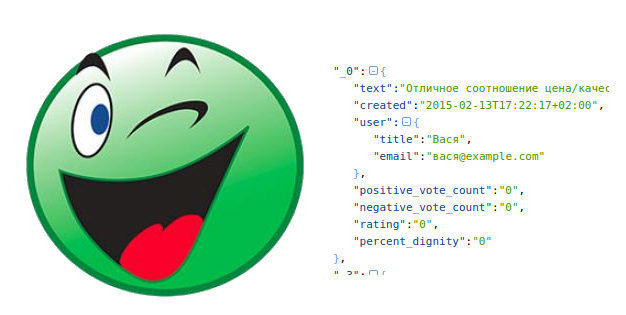
As soon as I got to get feedback, the following picture appeared to my eyes:
{ "content": [ { "result": { "_0": { "text": "[]", "created": "2015-02-13T17:22:17+02:00", "user": { "title": "", "email": "@example.com" }, "positive_vote_count": "0", "negative_vote_count": "0", "rating": "0", "percent_dignity": "0" }, ... "_3": { "text": "[]", "created": "2015-02-09T11:30:44+02:00", "user": { "title": " ", "email": "@example.com" }, "positive_vote_count": "1", "negative_vote_count": "0", "rating": "0", "percent_dignity": "100" } }, "code": "0" } ], "code": 1 } As you can see, besides the username is present and his email. It is necessary to mention a few facts about the reviews in this online store:
- Email for authorized users is automatically substituted;
- Without specifying an email, you cannot post a review;
- All reviews are moderated;
- Some people indicate in addition to the name and last name / patronymic.
So, we have a large database of emails with names, and sometimes with last names, targeted for certain groups of goods. Since I have never dealt with the internals of the "Socket", I decided that this answer might be corrected soon and forgot about this site for a month.
In February of this year, “Rosette” rolled out a redesign and I decided to check the status of the vulnerability in the mobile version. It turned out that the API version was updated to the 3rd (apparently, there was a second version earlier), in which the structure of requests and responses was slightly changed. Going to the feedback page and opening the developer tools showed that email no longer comes in response to the request. Only the name field remains. On this one could stop and forget about this case. But interest overwhelmed me and I decided to execute the query on the old link. To which the browser successfully returned the same answer to me. The old API is not closed, the vulnerability is in place.
The next day, a letter was written to the developers of the online store. I was promptly answered, they confirmed the vulnerability and after a few hours the API of the second version was covered up. As I understand it, this API was originally used for internal needs, and when it was brought to the public, the email remained. After the arrival of the third version, the second version continued to work.
As always, the simplest inattention in our profession can lead to sad consequences ...
Source: https://habr.com/ru/post/252475/
All Articles