Detection of mobile malware in the wild
Smartphones are increasingly penetrating our lives, for many people they have become an indispensable everyday companion. These gadgets give us connections with other people and entertain us. We trust them with more and more confidential and personal information, and it is not surprising that attackers are paying ever closer attention to the mobile segment. Since 2004, when Kaspersky Lab detected the first network mobile worm Cabir, more and more new malware samples appear every year. Accordingly, the development of methods for detecting malware “in the wild”, that is, in mobile app stores, is becoming increasingly relevant.
What is malware?
Malicious software (malware) is called an application designed to carry out all sorts of illegal actions. This includes viruses, botnets, worms, trojans, etc. Today, malware is widely used to extract profits from all sorts of ways, from stealing bank accounts to direct extortion. And in this shadow business big money is spinning, which attracts more and more new participants.
Malware detection technologies in “large” operating systems are already quite diverse and very effective. However, the mobile segment in the information security industry is still in its infancy.
')
In addition to malware, two more categories of threats for mobile devices should be mentioned - spyware (spyware) and conditionally malicious software (grayware). Spyware applications collect information about his movements, SMS-messaging, call history, etc. secretly from the user. In the strict sense, if spyware does not send information collected somewhere, then it cannot be called illegal. But the fact of installation without the knowledge of the user of such an application can not be called ethical.
Conditionally harmful software is much more harmless than the "classic", but at the same time quite annoying. For example, a program belonging to a similar class may change the system fonts or their color, or give all sorts of ridiculous and mocking messages. In general, by analogy with human society, conditionally-harmful software is a petty bully, a dirty dog. We can say that grayware is on the edge of legality: the authors usually do not hide their intentions and give a description of the functionality of their software, but users usually press the “I agree” button without reading the terms of the license agreement.
Many security professionals prefer to classify malware based on behavioral patterns and the motivation of their authors. Below are the most important views:
- Offering users all kinds of new items and entertainment. Usually such software is developed for the purpose of entertaining the author himself and demonstrating his skills, mainly with the help of senseless destructive actions on the victim's device. Example: Android.Walkinwat
- Trading user information. Such applications secretly collect data about the user's location, installed applications, download history and contact list contents. For this information there is a steady demand from advertisers and marketers. Example: DroidDreamLight
- Stealing financial information. Most often these are accounts to bank accounts. Intercepted text messages, recorded all the buttons pressed, apply phishing attacks. Example: Ikee.B
- Manipulating the delivery of various content. Such software is intended for personal calls and SMS sending with technical support offers, stock reports, intimate services, etc. Example: FakePlayer
- Send SMS spam. From the number of the victim begins sending spam, usually containing advertising and phishing links. Example: Geinimi
- Manipulating search results. Artificially raise various sites in search results. Example: Hong Tou Tou
Ways to detect malware
Each of the existing methods for determining mobile malware has its own advantages and disadvantages.
Static code analysis
This is a fast and low-cost method. It consists in searching for malicious characteristics or suspicious pieces of code without launching the application. The techniques shown below are widely used for preliminary analysis when you first need to test a suspicious application for the most obvious malicious functionality.

The first two branches are typical for detecting malware on Symbian OS and iOS, so we’ll omit its description. We are interested in the third branch of the scheme, which describes the algorithm of actions for Android. Using the decompiler , the source code of the application is generated. Further, it is subjected to static analysis by tools from the Fortify SCA software package. The disadvantages of this technique include the fact that, in general, it is only suitable for analyzing applications with a relatively small number of access rights and API calls.
Dynamic code analysis
In contrast to static, dynamic analysis involves the execution of an application in an isolated environment. For example, inside a virtual machine or emulator, so that you can monitor the behavior of the application. Most often, dynamic analysis is used when tracing system calls or taint-tracking.
For a dynamic system-wide taint analysis, you can use the TaintDroid tool. The illustration below shows how an application is first sent to a virtual machine, where it is evaluated at four levels: variables, methods, messages, and files. During taint-tracking, any data requests from the geolocation module, microphone, camera, etc. This method implies that all native libraries are called only from a virtual machine, and not directly. Finally, dynamic analysis identifies potential data leaks before information is transferred from the system to the network interface.
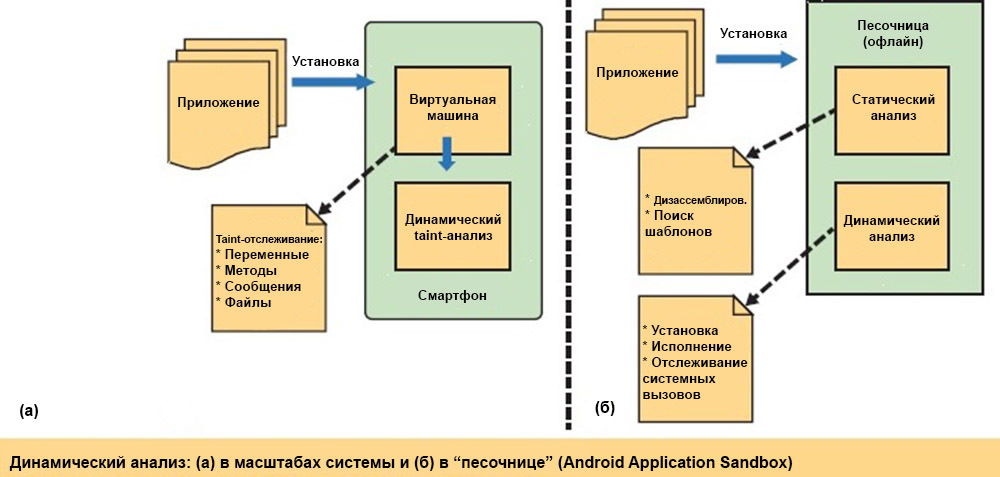
Testing of many popular Android applications from third-party developers has shown that a significant number of them send information on the location of users to advertising companies. Some even send phone IDs to remote servers. However, TaintDroid can produce both false-negative and false-positive analysis results. In addition, this tool allows you to analyze only one type of vulnerabilities - data streams.
The second part of the illustration shows a two-step analysis system for Android applications using the sandbox (AASandbox). In it, binary files are first disassembled, and in the resulting code a search is made for characteristic patterns. Then, during the dynamic analysis, the application is executed in the Android emulator, and all system calls are recorded in the log. If it is not possible to take real user-generated input data, then you can use the Android Monkey tool (ADB Monkey).
Application Access Analysis
In mobile applications, access rights play a key role: they show the user the intentions of the application and the activity of the backend. In smartphones, access rights are explicitly set, so application authors should also explicitly request them. However, some deliberately hide the rights used by the application, which leads to the appearance of vulnerabilities.
Below is a diagram of the tool for analyzing the permissions of Android applications, Kirin. During the installation of the application being studied, it retrieves the security settings and verifies them with the existing security policy. If the application fails validation, then Kirin warns the user, or even deletes the application.
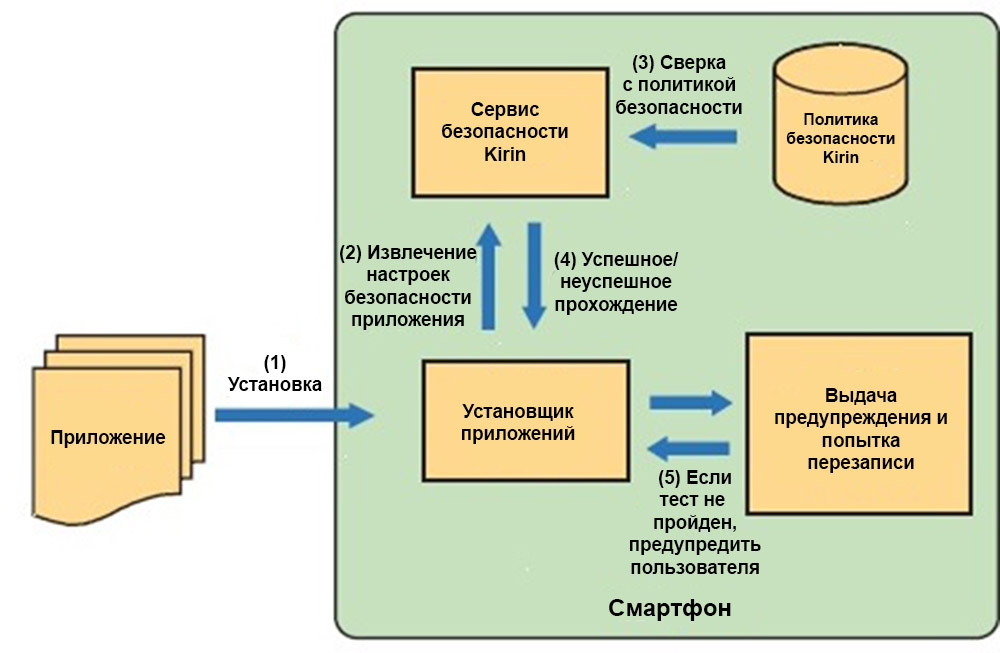
Kirin security policy example:
An application must not have PHONE_STATE,RECORD_AUDIO, and INTERNET permission labels'This rule prohibits the application to record audio or access the Internet while the user is on the phone. This avoids telephone tapping.
A study of 100 paid and 856 free Android applications conducted in 2011 showed that about 93% of free and 82% of paid ones request obtaining at least one potentially dangerous access right. Among them, the most common was a request for network access, even if the purpose of the application did not imply its use.
The disadvantages of Kirin include the fact that the analysis of requests for rights is not enough to detect malware, it is an auxiliary tool that must be used simultaneously with static or dynamic code analysis.
Analysis using cloud services
Obviously, the smartphone will not be able to fully analyze suspicious applications due to the limited resources of the device itself. A simple file scan will take a lot of time and “eat” a noticeable fraction of the battery charge. One way to solve this problem is to analyze using cloud services.
The following illustration shows a diagram of the operation of Paranoid Android, a cloud service for protection against malicious software. The advantage is obvious - all computational and analytical operations are carried out not on the user device, but in the emulators on remote servers. On the smartphone, only the tracer works, which records all the information necessary for the analysis of the application operation. Then the tracer sends data to the cloud emulator. It can carry out several different checks, including dynamic analysis, memory scanning, detection of suspicious system calls and anti-virus scanning.
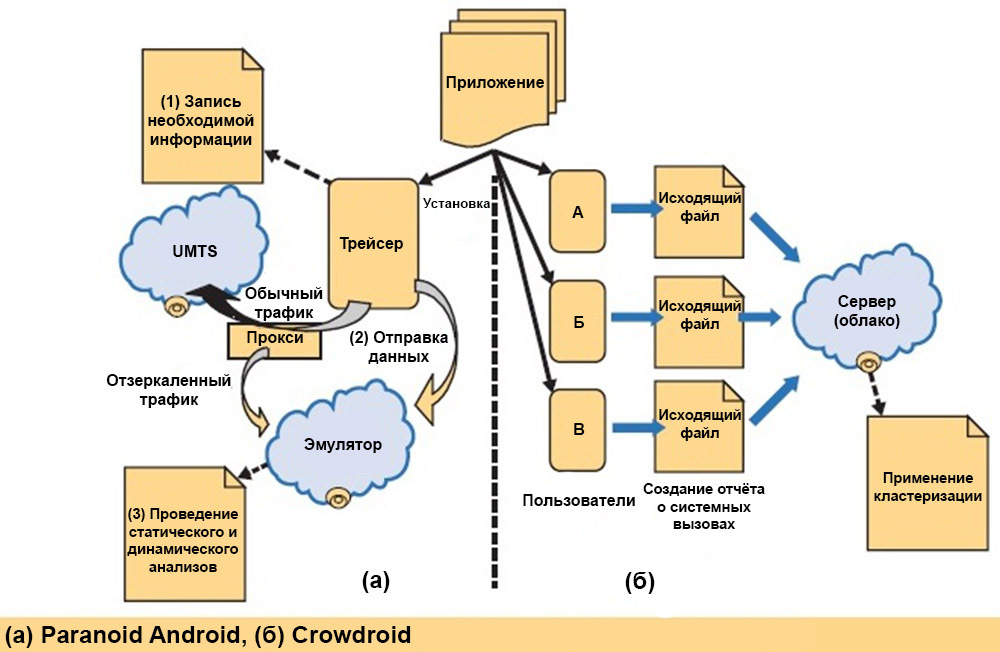
For the temporary storage of incoming traffic, Paranoid Android uses a proxy, which saves the battery power of the smartphone and does not send the same data to the server. He can directly contact the proxy and get the necessary data to emulate the analyzed application. Nevertheless, the use of RA for the analysis of "heavy" applications still significantly increases the power consumption and the load on the processor. And since the tracer works in the user environment, system calls load the processor much more than the native code execution. Conventionally, the trace of the read () system call takes 0.7 milliseconds in the user environment, and 0.1 in the kernel.
The right half of the previous illustration shows a diagram of Crowdroid, a tool for analyzing application behavior. This is a lightweight client application that monitors system calls initiated by a monitored application, pre-processes them, and sends them to the cloud. And there already using clustering determines whether the application is malicious or not. Unfortunately, Crowdroid has false positive results if there is very little data to analyze.
Battery consumption monitoring
Higher, compared with peers, energy consumption when running an application can be an indirect evidence of harmfulness. Of course, this works if the user’s behavior, battery condition, signal level, network traffic volume and other parameters are well known.
Mobile Malware Protection Tips
Given the limited computing and energy resources of smartphones, it can be assumed that in the future, the protective functionality will be mainly represented by cloud services. With the development of payment systems based on NFC, we can also expect the emergence of malicious software aimed specifically at stealing payment data through this channel. Surely there will be attempts to obtain bank card details using reverse engineering applications for payments through NFC. Such threats must be prevented in advance, for example, by using strong encryption and admitting a limited number of developers to create payment software.
But despite the development of tools to identify malware and protect their devices, it is best to avoid infection and its consequences altogether. After all, our own negligence and lack of caution can lead to very poor results. Therefore, it is better to follow the tips below:
- Install a good protective application that will protect against attacks and alert you if you detect suspicious application activity.
- Download applications only from trusted sources.
- Before installing it is better to read the reviews and see the rating, even if you have heard a lot about the author of the application.
- Always carefully read the list of requested permissions. If there are any suspicions, it is better to refuse installation. You can also leave a comment that will alert other users.
- If you currently do not need Wi-Fi, Bluetooth and other wireless modules, turn them off. So it will be safer, and the battery will live longer. Connect to public access points with care: activate the firewall in advance, turn off file sharing and use SSL or VPN.
- Regularly update your applications, as well as the firmware of your smartphone.
- Use encryption to store all important data stored on your smartphone. Also do not forget to make regular backups. Make sure that critical information is not cached anywhere.
- Wherever possible, put passwords to access important files and applications.
- Do not follow suspicious or untrusted links. If you still really need, it is better to type the address manually, and do not copy and paste into the browser. This will protect against attacks using shadow boot.
- Regularly monitor battery consumption, sent SMS and call log. Any oddities should be considered as a reason to check the entire system, especially recently installed applications.
- Finally, if the smartphone has been lost or stolen, erase all applications, contacts and confidential information remotely. And also block the device itself.
In general, it is highly unlikely that truly serious malware will be evaluated falsely positively. So following the above tips will surely protect you from various troubles, be vigilant and careful in the open spaces of the network. We, in turn, are preparing various solutions for the information protection of our smartphones, read about it in one of the next publications.
Source: https://habr.com/ru/post/251929/
All Articles