For the capture of the author Zeus appointed maximum reward
Last year, we wrote that US law enforcement agencies wanted the author of the well-known banking malware Zeus. Using this malicious program, hundreds of millions of dollars were stolen from bank accounts from users all over the world, and the bot itself has long produced a large number of its clones. Recently, the FBI increased the reward for information leading to its capture up to the sum of $ 3 million. This is the maximum reward that has ever been announced for cyber-defendants (cyber).
The person involved under the pseudonym "slavik" is known in the underworld for a long time and is mentioned as the author of one of the earliest versions of Zeus. At the beginning of last year, we also wrote about the capture of another cybercriminal by law enforcement officers. We are talking about the author of another SpyEye banking trojan under the pseudonym “Gribodemon”. This bot was based on Zeus source code.
')

Fig. Orientation to the author Zeus from the site fbi.gov.
The story with Zeus stretches for quite some time. The first versions of the bot were born in 2007 or even earlier. Zeus was distinguished from other malicious programs by the fact that it became a kind of first crimeware toolkit or a full-featured tool for stealing online banking data from various banks and transmitting this information to the attacker's server. To carry out such operations, he had in its composition a configuration file, which allowed attackers to quickly redirect it to the goals they needed (banking sites). Since then, several generations or versions of Zeus have appeared, the cumulative financial damage from which is estimated at more than half a billion dollars. The number of different families or modifications of this malicious program and botnets based on it already amounts to several dozen.
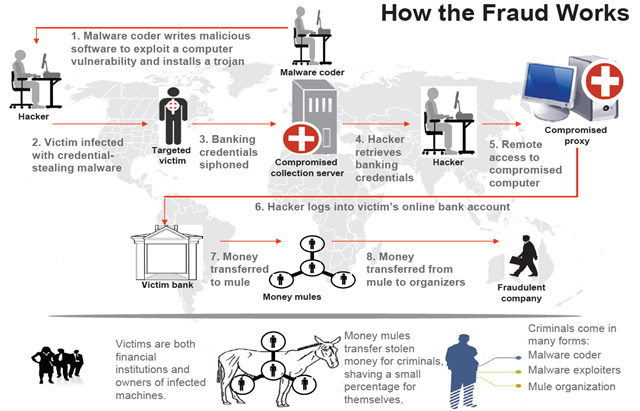
Fig. A typical pattern of cybercriminals who use bank malware tools, including Zeus.

The person involved under the pseudonym "slavik" is known in the underworld for a long time and is mentioned as the author of one of the earliest versions of Zeus. At the beginning of last year, we also wrote about the capture of another cybercriminal by law enforcement officers. We are talking about the author of another SpyEye banking trojan under the pseudonym “Gribodemon”. This bot was based on Zeus source code.
')

Fig. Orientation to the author Zeus from the site fbi.gov.
The story with Zeus stretches for quite some time. The first versions of the bot were born in 2007 or even earlier. Zeus was distinguished from other malicious programs by the fact that it became a kind of first crimeware toolkit or a full-featured tool for stealing online banking data from various banks and transmitting this information to the attacker's server. To carry out such operations, he had in its composition a configuration file, which allowed attackers to quickly redirect it to the goals they needed (banking sites). Since then, several generations or versions of Zeus have appeared, the cumulative financial damage from which is estimated at more than half a billion dollars. The number of different families or modifications of this malicious program and botnets based on it already amounts to several dozen.

Fig. A typical pattern of cybercriminals who use bank malware tools, including Zeus.
- The author of the Trojan is developing the necessary functionality of the bot.
- The operator (hacker) is responsible for distributing the compiled executable files of the Trojan program. He can use the services of spammers to organize spam mailings, “iframes” to redirect legitimate users of hacked sites to a Trojan or other methods known in the cybercrime world.
- The user is infected with a banking trojan, after which he uses a browser (in the process of which the malicious code is located) to work with online banking. The confidential data specified when working with the online banking system is sent to the attacker's server.
- The operator (hacker) receives the data sent by the bot in the previous step.
- The operator may use another compromised computer (proxy) to conduct fraudulent operations with the victim’s account, thus hiding the source of the attack.
- Using the proxy specified in the previous paragraph, the operator logs on to the user's online banking account using the login / password pairs stolen in step 4.
- Funds from the victim’s account are transferred to several dummy bank accounts in small portions, and then cashed at ATMs by various persons participating in the criminal scheme (mules).
- The organizer (coordinator) of the entire criminal scheme receives funds from the “mules”, and each of them “mules” receives its share.
Source: https://habr.com/ru/post/251613/
All Articles