Lenovo attacked in retaliation for the spyware Superfish

At midnight, a slideshow with images of teenagers appeared on the Lenovo.com main page, which was clearly not intended to advertise the company's laptops and smartphones. When the page opened, the song “Breaking Free” from the movie “High School Musical” started playing. At 7 am (Moscow time) a stub hung on the site, and it was restored to work only after a few hours.
According to The Hacker News, hackers from the Lizard Squad were involved in the hacking of the site, which follows from the message on the group's twitter . The slide show featured photos of its active participants Ryan King (Ryan King) and Rory Andrew Godfrey (Rory Andrew Godfrey), who were arrested after recent attacks on gaming services. In addition, a phrase about a new rebranding of the Lenovo website with Ryan King and Rory Andrew Godfrey has been added to the webpage code.
')
The Verge publication suggests Jonathan Zdzyarski about the mechanism of attack on the site, which links it to the substitution of the domain. He discovered changes in Whois — in particular, a change in DNS servers and a move to Cloudflare.
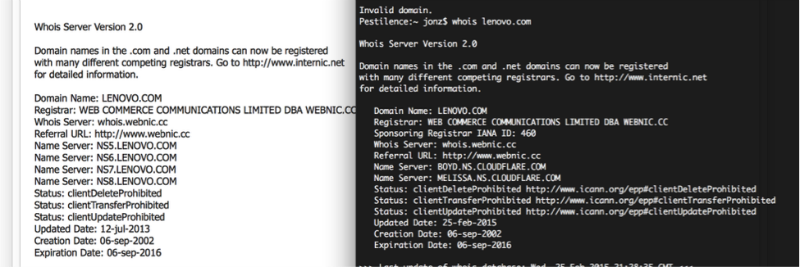
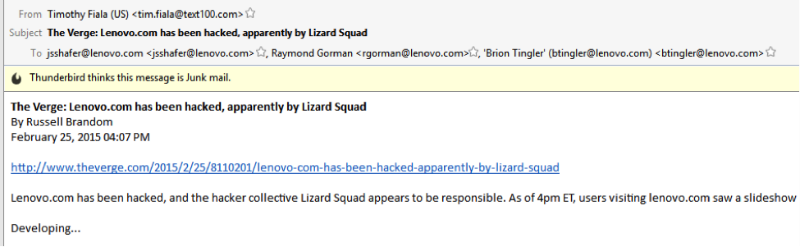
In addition to the site, hackers gained access to Lenovo employee correspondence.
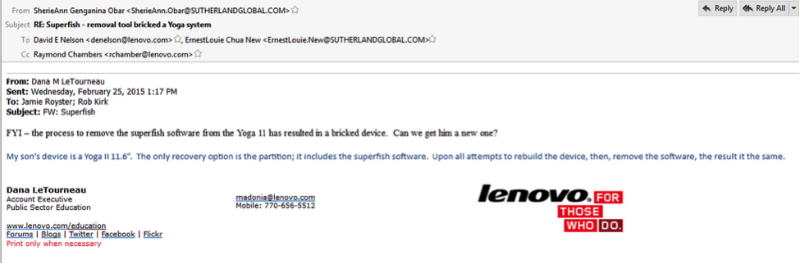
Another letter says that deleting Superfish from one of the users resulted in a computer crash.
Recall that on February 19th it became known about the Superfish program, which since summer 2014 comes with laptops of the G, U, Y, Z, S, Flex, Miix, Yoga and E series. The utility listens for traffic, including HTTPS, forges SSL- certificates of third-party sites, analyzes the user's search queries and inserts advertising on the pages of third-party resources. After the scandal, Lenovo released an official letter in which it recognized the problem of Superfish and presented various ways to remove the utility.
Interestingly, a few days before the sabotage against the largest computer manufacturer, Facebook’s security department conducted its own investigation, which resulted in the discovery of several more programs using the same library from Komodia as in Superfish.
- CartCrunch Israel LTD
- WiredTools LTD
- Say Media Group LTD
- Over the rainbow
- Tech System Alerts
- Arcadegiant
- Objectify media inc
- Catalytix Web Services
- Optimizer monitor
The Komodia library modifies the Windows network stack and installs a new root authentication center, which allows such applications to impersonate any site that supports SSL.
The Hacker News lists hashes that allow you to identify malicious utilities containing the Komodia library.
0cf1ed0e88761ddb001495cd2316e7388a5e396e
473d991245716230f7c45aec8ce8583eab89900b
fe2824a41dc206078754cc3f8b51904b27e7f725
70a56ae19cc61dd0a9f8951490db37f68c71ad66
ede269e495845b824738b21e97e34ed8552b838e
b8b6fc2b942190422c10c0255218e017f039a166
42f98890f3d5171401004f2fd85267f6694200db
1ffebcb1b245c9a65402c382001413d373e657ad
0a9f994a54eaae64aba4dd391cb0efe4abcac227
e89c586019e259a4796c26ff672e3fe5d56870da
Source: https://habr.com/ru/post/251609/
All Articles