Secure cisco
Hello!
Many of you have seen and read wonderful materials under the general title "Networks for the smallest." Actually, I do not claim laurels, but decided to write something similar in the area of network security based on Cisco equipment.
The first material will be devoted to BaseLine / L2 Security, i.e. those mechanisms that can be used in initial device configuration and on L2 switches under IOS control.
Anyone interested is gone!
Let's say we have brand-new [switch / router], for the first chapter it doesn't matter. We connect to it with the help of the console wire ( Part 1 of the Network for the smallest is described in more detail). Since we do not want the piece of hardware to be on our table or (if it is already in the rack) to stand and freeze in the server room, we will immediately set up remote control on it.
Remote control & credentials
')
In order to connect remotely you need to have your own credentials. When connected via the console, we can get into the privileged mode without restrictions. This, as you understand, is not particularly secure, although if the attacker has already been able to physically gain access to the piece of hardware, what kind of security can we talk about in principle ... But taking into account the defense-in-depth approach, you should set a password for the privileged mode.
In IOS there are 4 options-levels of password storage: 0, 4, 5, 7:
Consider them on the example of the enable command with parameters.For switch emulation, we use IOU on GNS3v1.0, as described here .
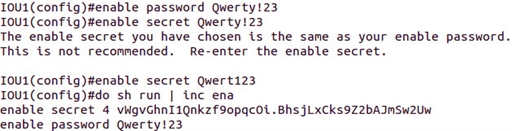
Let's see the configuration, as we see, it was not possible to set the same passwords (since I have Version 15.1 on IOU Switch - level 4 is used):
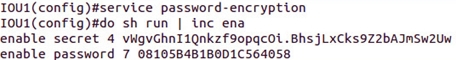
And level 7: service password-encryption, after entering this command, only 0 storage level is converted to 7 using Cisco encryption protocol:
It can be assumed that level 7 is more reliable than 4 and 5 from the point of view of security, but this is not the case, which can be read about, for example, in this material .
To further increase the level of secure connection to the device, we will enter the following commands (commands are entered here on the router from IOS ver. 15.4, because the necessary commands on the switch did not appear due to the release features):
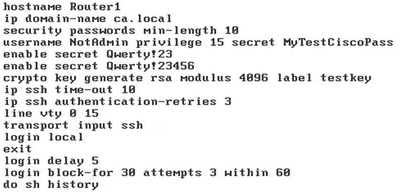
What did: set the requirement for a minimum password length of 10 characters, created a user with the highest level of privileges and called it "NotAdmin".
Use usernames like cisco, admin, root, etc. Not recommended. As you can see, the Qwerty password! 23 did not match because of control of its length (if you have difficulty with passwords, try something from this practice (I can never remember my password =! CNrmp, Quarter pounder with cheese = .25 # erwchz, How I then need to generate keys for a secure connection and set connection parameters using only ssh. Also with this config, we control the number of failed login attempts in a period of time, thereby protecting against brute -force.
With all this, the local database will be used with user names. Similarly, (local) configure the console port. If we use another account whose privilege level is not specified or lower than 15 (the default is three privilege levels: 0, 1, 15), you will need to enter the password when you log in to the account and when you activate the privileged mode for enable.
When configuring password access, it is strongly not recommended to use the password command.
It remains to hang the IP address on the device (maybe also dg, depending on whether you have the OOB management network), and it is desirable that the management network be separately allocated.
Everything, the device is ready for remote use.
Yes, if suddenly you forgot passwords, then help is here . Of course, if you have not used no service password-recovery .
There are, let's say, two approaches to using secure mechanisms for remotely managing Cisco devices. Without AAA we reviewed above. Now using AAA.
What is AAA - authentication, authorization, accounting or control over allocated resources. As you can see, AAA is very granular in terms of access, which just increases the level of security. How relevant its use depends on the specific architecture. Everything is activated simply:
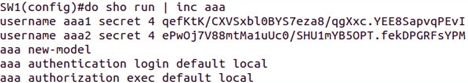
So, the commands on the screen: created 2 users, activated AAA and applied 2 methods (Method-List) with parameters - default local, which means that the local database on the entire piece of hardware will be checked during authentication and authorization, except for the authorization on the console port, for this you need to enter aaa authorization console .
Actually, in a similar way, you can create custom Method-Lists and apply it on vty:

As you understand, in addition, you must configure the radius / tacacs server: radius-server host 192.168.1.100 .
The order of verification in Method-List: radius (yes / no), if not available, then check in enable. The logic of the Method-List is such that first the name sheets are checked, and only then the default sheet.
Another interesting security command is: aaa local authentication attempts max-fail 3 . If the user runs out of 3 attempts, his account is blocked.
What else, honestly a lot of things ...
Remote control via vty can be limited using ACLs (what ACLs are and what they eat can be found in the very first link, in the section on NAT and ACL), this is done approximately like this:
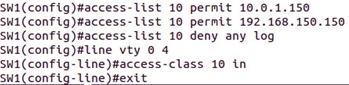
In principle, it is better to separate the control network from the rest of the data transmission network.
Unused management ports must be disabled to enter commands:
Another good practice is to install various informational messages - banners. For what? Well, for example, in order to notify "accidentally" the admin who got to the control interface of the piece of iron about this:
Cisco has such a good protocol as CDP , and from an IS point of view, we would need to extinguish it either globally no cdp run or separately on the interface interface, no cdp enable . Consider disconnecting carefully if you have Cisco VoIP, because CDP transmits the configuration to the phones.
To control (if possible) we do not use HTTP, only HTTPS:
Turning off Gratuitous ARP is from the category of “not waiting, but it came to a hitch”, such packets can be used with APR Poisoning, turned off with the command no ip gratuitous-arps .
IOS also has auto security configuration: auto secure - Wizard to configure basic security settings.
You need to inspect and such parameters that it would be desirable to disable (in the latest versions of IOS, they are disabled by default and most relate to L3): TCP / UDP Small-Servers, Finger, Identification (auth) Protocol, PAD, Autoloading Device Configuration, IP Source Routing, IP Directed Broadcast
And one more thing: turn off all unnecessary services and protocols, administratively extinguish unused interfaces, don't forget about NTP (ntp server), logging and baseline config:
It seems to be all, if you forgot, please unsubscribe in the comments, at least JDima , always made worthwhile comments.
L2 Security
After you have dealt with secure access, let's proceed to L2 information security risk mitigation. There is such a document: CISCO LAYER 2 ATTACKS & MITIGATION TECHNIQUES, which reflects the following:

So, what is a switch, how does it work, a broadcast domain, VLAN and other basic theoretical parts are abruptly described in ... yes and yes “Networks for the smallest. Part 2. Switching.
VLAN Hopping - type of attack when an attacker gains access to the VLAN, for example, when forcibly agreeing on the port operation mode. This can be done with the help of this utility , it is also in Kali. In general, on new switches this does not work out very well, but the essence of the problem lies in the DTP operation in auto mode by default. But if you enter the switchport mode access command on the user ports (on the trunk DTP should work, no negotiate ), then the attacker will not agree on the mode.
Also, transfer all unused ports to any VLAN 2451, never use or disable the VLAN1 interface ( interface vlan 1, shutdown ) and specify it on the trunk port, for example, native vlan 20 , because by default the native vlan has id = 1.
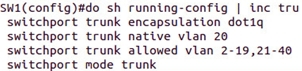
The same does the vlan dot1q tag native command from the global configuration mode, but I did not have it ...
In addition to the usual VLAN there are these ( Keith Barker copyright):
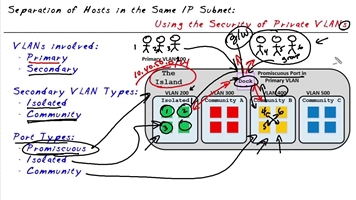
What can be seen from this illustration:
I will not repeat much, everything is described in detail here or here . A small example:
Apply or not you decide, depending on the purpose.
Everything seems to be clear, however, if we route the Promiscuous port, then it is possible to get from ISOLATED to other VLANs by sending a sub-packet to the L3 device. This feature closes with an ACL on the router.
Approximately similar c Isolated VLAN functionality is available when configuring PVLAN Edge or Protected port. This is configured on each interface separately with the command: switchport protected .
Well, in the end with the VLAN consider the ACL for VLANs: VLAN ACL (VACL) or VLAN map as well as MacSec.
If it is necessary to control the traffic inside the VLAN, you need to determine the traffic and hang it on the desired VLAN, like this:
Create a regular access list that will be used in the VACL. We define the VLAN access map. We define the action when the traffic matches the list. Applicable to VLAN. 1 traffic class will stop, all other traffic will be sent.
An interesting feature in IOS is MacSec .
Here is a set of commands (for example, on 2 devices):
Having configured on L2 devices, on ports through which two switches are interconnected, we get a symmetrically encrypted channel (pmk on devices should be the same).
CAM protection
If you take the macof utility (available in Kali) and launch it to generate MAC addresses from the client connected to the switch, then depending on the switch model, it will become a hub after a while. Why? Due to the fact that the place in the CAM table will end. In order to prevent this, there is a port security mode on the interface of interest to us:
 and
and 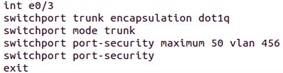
This mode works only on the trunk or access port, but not on the dynamic port.
The mode has parameters: Protect (no packets if violation, no log), Restrict (no packets if violation, log: snmp, sylog), Shut down port (default, max = 1, log: snmp, sylog), Shut down Vlan . There are Dynamic modes (memorize 5 first mac), Static (write write running static static mac) and another sticky (brand new network -> auto write in running config).
And at the end of the settings you need to remember to activate the mode itself.
Snooping table
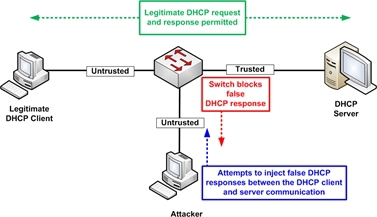
In order to protect yourself from attacks on dhcp, you can use dhcp snooping table . The bottom line is that the switch remembers which port it has a legal dhcp server, thus performing dhcp starvation attack (well, or someone just brought from dlink house) from access ports will not work.
The mode is switched on separately for the whole piece of hardware and vlans:
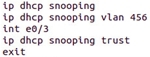
To limit the number of dhcp requests, use the ip dhcp snooping limit rate 20 command. And if necessary, see the available links:

Initially, in this mode, by default, all ports are not trusted.
DAI
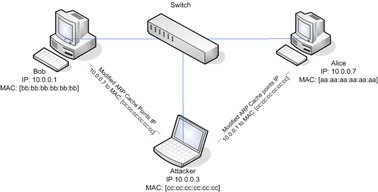
DAI (dynamic arp inspection) works on the basis of the snooping table, i.e. dynamically compares MAC-IP and thereby prevents ARP poisoning: ip arp inspection vlan 456 .
This is a type of attack in which ARP packets with modified MAC addresses are sent, after updating the ARP table, MITM is performed.
If there is no DHCP in the infrastructure, then similar functionality can be achieved using the arp access-list:
There is also a functionality for comparing ARP Validation Checks .
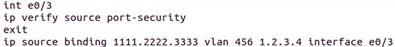
IP Spoofing / Source Guard
Again, based on the snooping table, IP Spoofing / Source Guard functions.
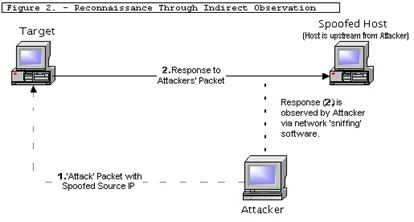
A striking example of an attack with IP spoofing when an attacker generates different packets with different IP DESTINATION and the same IP SOURCE. As a result, all Destinations are trying to answer Source and pass it DDoS.
This command set will help protect against IP Spoofing attacks.
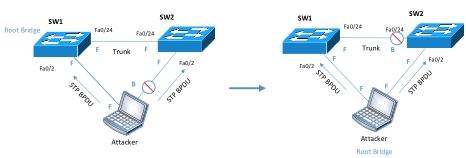
STP
As you know, the main task of STP is to eliminate loops in the topology, in which there are redundant connections. But it is possible to implement such a scheme, when the violator becomes the root bridge and again implements the MITM:
In order to activate protection globally on all ports you need to use the spanning-tree portfast bpduguard default command .
Then we transfer the port to portfast mode and get ... Instead of a thousand words:

Separately on the interface, this is done with the command: spanning-tree bpduguard enable .
Storm control

This is another control mechanism for forwarding packets with STP enabled, which has the following parameters:
In addition to the above, there are technologies such as: Root Guard, EtherChannel Guard, Loop Guard, Port Blocking .
Behind this all, thank you for reading to the end. I hope the information will be useful.
PS It would be interesting to know which security mechanisms in the context of this material do you use in the infrastructure? Write in the comments.
Many of you have seen and read wonderful materials under the general title "Networks for the smallest." Actually, I do not claim laurels, but decided to write something similar in the area of network security based on Cisco equipment.
The first material will be devoted to BaseLine / L2 Security, i.e. those mechanisms that can be used in initial device configuration and on L2 switches under IOS control.
Anyone interested is gone!
Let's say we have brand-new [switch / router], for the first chapter it doesn't matter. We connect to it with the help of the console wire ( Part 1 of the Network for the smallest is described in more detail). Since we do not want the piece of hardware to be on our table or (if it is already in the rack) to stand and freeze in the server room, we will immediately set up remote control on it.
Remote control & credentials
')
In order to connect remotely you need to have your own credentials. When connected via the console, we can get into the privileged mode without restrictions. This, as you understand, is not particularly secure, although if the attacker has already been able to physically gain access to the piece of hardware, what kind of security can we talk about in principle ... But taking into account the defense-in-depth approach, you should set a password for the privileged mode.
In IOS there are 4 options-levels of password storage: 0, 4, 5, 7:
- Level 0: enable password Qwerty! 23 - storing data in the clear.
- Level 4: enable secret Qwerty! 23 - data conversion in SHA256 Encryption in IOS 15, since "Change to new encryption, md5 can be deprecated soon."
- Level 5: enable secret Qwerty! 23 - convert data to MD5 Hash.
Consider them on the example of the enable command with parameters.
Let's see the configuration, as we see, it was not possible to set the same passwords (since I have Version 15.1 on IOU Switch - level 4 is used):

And level 7: service password-encryption, after entering this command, only 0 storage level is converted to 7 using Cisco encryption protocol:

It can be assumed that level 7 is more reliable than 4 and 5 from the point of view of security, but this is not the case, which can be read about, for example, in this material .
To further increase the level of secure connection to the device, we will enter the following commands (commands are entered here on the router from IOS ver. 15.4, because the necessary commands on the switch did not appear due to the release features):

What did: set the requirement for a minimum password length of 10 characters, created a user with the highest level of privileges and called it "NotAdmin".
Use usernames like cisco, admin, root, etc. Not recommended. As you can see, the Qwerty password! 23 did not match because of control of its length (if you have difficulty with passwords, try something from this practice (I can never remember my password =! CNrmp, Quarter pounder with cheese = .25 # erwchz, How I then need to generate keys for a secure connection and set connection parameters using only ssh. Also with this config, we control the number of failed login attempts in a period of time, thereby protecting against brute -force.
With all this, the local database will be used with user names. Similarly, (local) configure the console port. If we use another account whose privilege level is not specified or lower than 15 (the default is three privilege levels: 0, 1, 15), you will need to enter the password when you log in to the account and when you activate the privileged mode for enable.
When configuring password access, it is strongly not recommended to use the password command.
It remains to hang the IP address on the device (maybe also dg, depending on whether you have the OOB management network), and it is desirable that the management network be separately allocated.
Everything, the device is ready for remote use.
Yes, if suddenly you forgot passwords, then help is here . Of course, if you have not used no service password-recovery .
There are, let's say, two approaches to using secure mechanisms for remotely managing Cisco devices. Without AAA we reviewed above. Now using AAA.
What is AAA - authentication, authorization, accounting or control over allocated resources. As you can see, AAA is very granular in terms of access, which just increases the level of security. How relevant its use depends on the specific architecture. Everything is activated simply:

So, the commands on the screen: created 2 users, activated AAA and applied 2 methods (Method-List) with parameters - default local, which means that the local database on the entire piece of hardware will be checked during authentication and authorization, except for the authorization on the console port, for this you need to enter aaa authorization console .
Actually, in a similar way, you can create custom Method-Lists and apply it on vty:

As you understand, in addition, you must configure the radius / tacacs server: radius-server host 192.168.1.100 .
The order of verification in Method-List: radius (yes / no), if not available, then check in enable. The logic of the Method-List is such that first the name sheets are checked, and only then the default sheet.
Another interesting security command is: aaa local authentication attempts max-fail 3 . If the user runs out of 3 attempts, his account is blocked.
What else, honestly a lot of things ...
Remote control via vty can be limited using ACLs (what ACLs are and what they eat can be found in the very first link, in the section on NAT and ACL), this is done approximately like this:

In principle, it is better to separate the control network from the rest of the data transmission network.
Unused management ports must be disabled to enter commands:
line aux 0 no exec no transport input no transport output Another good practice is to install various informational messages - banners. For what? Well, for example, in order to notify "accidentally" the admin who got to the control interface of the piece of iron about this:
banner login c Warning! Non Authorization Access Is Restricted c Cisco has such a good protocol as CDP , and from an IS point of view, we would need to extinguish it either globally no cdp run or separately on the interface interface, no cdp enable . Consider disconnecting carefully if you have Cisco VoIP, because CDP transmits the configuration to the phones.
To control (if possible) we do not use HTTP, only HTTPS:
no ip http server ip http secure-server Turning off Gratuitous ARP is from the category of “not waiting, but it came to a hitch”, such packets can be used with APR Poisoning, turned off with the command no ip gratuitous-arps .
IOS also has auto security configuration: auto secure - Wizard to configure basic security settings.
You need to inspect and such parameters that it would be desirable to disable (in the latest versions of IOS, they are disabled by default and most relate to L3): TCP / UDP Small-Servers, Finger, Identification (auth) Protocol, PAD, Autoloading Device Configuration, IP Source Routing, IP Directed Broadcast
And one more thing: turn off all unnecessary services and protocols, administratively extinguish unused interfaces, don't forget about NTP (ntp server), logging and baseline config:
service tcp-keepalives in service tcp-keepalives in out snmp-server enable traps cpu threshold ......... service timestamps log datetime secure boot-image secure boot-config It seems to be all, if you forgot, please unsubscribe in the comments, at least JDima , always made worthwhile comments.
L2 Security
After you have dealt with secure access, let's proceed to L2 information security risk mitigation. There is such a document: CISCO LAYER 2 ATTACKS & MITIGATION TECHNIQUES, which reflects the following:

So, what is a switch, how does it work, a broadcast domain, VLAN and other basic theoretical parts are abruptly described in ... yes and yes “Networks for the smallest. Part 2. Switching.
VLAN Hopping - type of attack when an attacker gains access to the VLAN, for example, when forcibly agreeing on the port operation mode. This can be done with the help of this utility , it is also in Kali. In general, on new switches this does not work out very well, but the essence of the problem lies in the DTP operation in auto mode by default. But if you enter the switchport mode access command on the user ports (on the trunk DTP should work, no negotiate ), then the attacker will not agree on the mode.
Also, transfer all unused ports to any VLAN 2451, never use or disable the VLAN1 interface ( interface vlan 1, shutdown ) and specify it on the trunk port, for example, native vlan 20 , because by default the native vlan has id = 1.

The same does the vlan dot1q tag native command from the global configuration mode, but I did not have it ...
In addition to the usual VLAN there are these ( Keith Barker copyright):

What can be seen from this illustration:
- Vlans are: Primary and Secondary: Isolated or Community.
- Vlans types: Isolated (maybe only in a single copy, there is no connection within vlan, only with Promiscuous), Community (many, there is a connection within Vlan with Promiscuous)
- Ports Types: Promiscuous - Primary Vlan port something like dg, also Isolated and Community
- Private Vlans require the inclusion of VTP transparent: vtp mode transparent .
I will not repeat much, everything is described in detail here or here . A small example:
vlan 101 private-vlan primary vlan 201 private-vlan community vlan 202 private-vlan community vlan 301 private-vlan isolated ........... vlan 101 private-vlan association 201-202,301 Apply or not you decide, depending on the purpose.
Everything seems to be clear, however, if we route the Promiscuous port, then it is possible to get from ISOLATED to other VLANs by sending a sub-packet to the L3 device. This feature closes with an ACL on the router.
Approximately similar c Isolated VLAN functionality is available when configuring PVLAN Edge or Protected port. This is configured on each interface separately with the command: switchport protected .
Well, in the end with the VLAN consider the ACL for VLANs: VLAN ACL (VACL) or VLAN map as well as MacSec.
If it is necessary to control the traffic inside the VLAN, you need to determine the traffic and hang it on the desired VLAN, like this:
access-list 1 permit 192.168.1.0 0.0.0.255 access-list 2 permit any vlan access-map mymap 10 match ip address 1 action drop exit vlan access-map mymap 20 match ip address 2 action forward exit vlan filter mymap vlan-list 5-10 end Create a regular access list that will be used in the VACL. We define the VLAN access map. We define the action when the traffic matches the list. Applicable to VLAN. 1 traffic class will stop, all other traffic will be sent.
An interesting feature in IOS is MacSec .
Here is a set of commands (for example, on 2 devices):
int gig0/2 cts manual sap pmk Qwerty123 Having configured on L2 devices, on ports through which two switches are interconnected, we get a symmetrically encrypted channel (pmk on devices should be the same).
CAM protection
If you take the macof utility (available in Kali) and launch it to generate MAC addresses from the client connected to the switch, then depending on the switch model, it will become a hub after a while. Why? Due to the fact that the place in the CAM table will end. In order to prevent this, there is a port security mode on the interface of interest to us:
 and
and 
This mode works only on the trunk or access port, but not on the dynamic port.
The mode has parameters: Protect (no packets if violation, no log), Restrict (no packets if violation, log: snmp, sylog), Shut down port (default, max = 1, log: snmp, sylog), Shut down Vlan . There are Dynamic modes (memorize 5 first mac), Static (write write running static static mac) and another sticky (brand new network -> auto write in running config).
And at the end of the settings you need to remember to activate the mode itself.
Snooping table
In order to protect yourself from attacks on dhcp, you can use dhcp snooping table . The bottom line is that the switch remembers which port it has a legal dhcp server, thus performing dhcp starvation attack (well, or someone just brought from dlink house) from access ports will not work.

The mode is switched on separately for the whole piece of hardware and vlans:

To limit the number of dhcp requests, use the ip dhcp snooping limit rate 20 command. And if necessary, see the available links:

Initially, in this mode, by default, all ports are not trusted.
DAI
DAI (dynamic arp inspection) works on the basis of the snooping table, i.e. dynamically compares MAC-IP and thereby prevents ARP poisoning: ip arp inspection vlan 456 .
This is a type of attack in which ARP packets with modified MAC addresses are sent, after updating the ARP table, MITM is performed.

If there is no DHCP in the infrastructure, then similar functionality can be achieved using the arp access-list:
arp access-list NEW-ARP-ACL permit ip host 10.1.1.11 mac host 0011.0011.0011 ip arp inspection filter arpacl vlan 456 There is also a functionality for comparing ARP Validation Checks .
IP Spoofing / Source Guard
Again, based on the snooping table, IP Spoofing / Source Guard functions.
A striking example of an attack with IP spoofing when an attacker generates different packets with different IP DESTINATION and the same IP SOURCE. As a result, all Destinations are trying to answer Source and pass it DDoS.

This command set will help protect against IP Spoofing attacks.

STP
As you know, the main task of STP is to eliminate loops in the topology, in which there are redundant connections. But it is possible to implement such a scheme, when the violator becomes the root bridge and again implements the MITM:

In order to activate protection globally on all ports you need to use the spanning-tree portfast bpduguard default command .
Then we transfer the port to portfast mode and get ... Instead of a thousand words:

Separately on the interface, this is done with the command: spanning-tree bpduguard enable .
Storm control

This is another control mechanism for forwarding packets with STP enabled, which has the following parameters:
- Monitoring done: Broadcast / Multicast / Unicast
- Set thresholds:% / PPS / BPS
- Action is selected: Slow / Shutdown
storm-control broadcast pps 500 100 storm-control action shutdown errdisable recovery cause storm-control errdisable recovery interval 60 In addition to the above, there are technologies such as: Root Guard, EtherChannel Guard, Loop Guard, Port Blocking .
Behind this all, thank you for reading to the end. I hope the information will be useful.
PS It would be interesting to know which security mechanisms in the context of this material do you use in the infrastructure? Write in the comments.
Source: https://habr.com/ru/post/251547/
All Articles