Lenovo laptops come with Superfish malware and its CA certificate and private key in storage
The Superfish program, which comes with Lenovo Y50, Z40, Z50, G50 and Yoga 2 Pro laptops, is a typical Malware that listens for traffic, analyzes user search queries and inserts advertisements on third-party websites. This application works at the system level, intercepting, among other things, HTTPS traffic. To do this, the application installs the Superfish CA certificate in the Windows keystore and proxies all traffic between the host and the browser, replacing the certificate with its own. This software has been delivered at least since June 2014. The first post about this program on the Lenovo forum is dated September 2014.
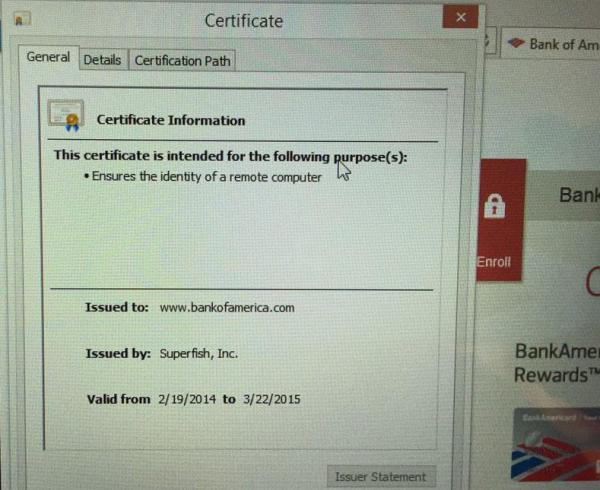
The news itself is already unpleasant, but today one detail has become known that significantly increases the danger level for the owners of these laptops: it turned out that the program has not only a public CA certificate, but also a private key to it, in encrypted form. Choosing a password for this key is not a problem - “komodia”:

twitter picture supersat
')
This means that any attacker who has the ability to perform a MitM attack (for example, in a public Wi-Fi network) can use this certificate to proxy HTTPS traffic through his computer and decrypt it unnoticed by the victim.
A Lenovo representative at the forum said that they had stopped supplying this software with new laptops since January 2015 and turned off Superfish for all owners of already purchased laptops. An instruction is available for removing malware , which, however, does not include removing the root certificate from the repository.
Service to verify the presence of a Superfish certificate in the OS repository
Certificate and private key Superfish in PEM format
An article in Forbes (does not mention the presence of a private key)
Article from Marc Rogers (does not mention the presence of a private key)
Article from Errata Security
How to get a private key and password
Information on the EFF website
Windows Defender detects Superfish

The news itself is already unpleasant, but today one detail has become known that significantly increases the danger level for the owners of these laptops: it turned out that the program has not only a public CA certificate, but also a private key to it, in encrypted form. Choosing a password for this key is not a problem - “komodia”:

twitter picture supersat
')
This means that any attacker who has the ability to perform a MitM attack (for example, in a public Wi-Fi network) can use this certificate to proxy HTTPS traffic through his computer and decrypt it unnoticed by the victim.
A Lenovo representative at the forum said that they had stopped supplying this software with new laptops since January 2015 and turned off Superfish for all owners of already purchased laptops. An instruction is available for removing malware , which, however, does not include removing the root certificate from the repository.
Service to verify the presence of a Superfish certificate in the OS repository
Certificate and private key Superfish in PEM format
An article in Forbes (does not mention the presence of a private key)
Article from Marc Rogers (does not mention the presence of a private key)
Article from Errata Security
How to get a private key and password
Information on the EFF website
Windows Defender detects Superfish
Source: https://habr.com/ru/post/251069/
All Articles