The Equation, Carbanak, Desert Falcons: Report with Security Analyst Summit
 The fourth annual conference of the Kaspersky Security Analyst Summit was held on February 16 and 17 in Cancun (in Mexico). This is a very important event for Kaspersky Lab, where we share our research and invite colleagues from other companies in the information security industry to speak. Two of our presentations have already been discussed at Habré: the studies of The Equation APT and Carbanak attracted a lot of attention (thanks, I enjoyed reading the comments, ready to answer the questions here). In this post - a brief report on the presentations of the research of Carbanak, The Equation and on the activities of another, previously unknown group, which we called Desert Falcons. All three - with links to detailed reports of our researchers on the site Securelist. Well, a few photos. Important: almost all performances will be available later in the video, we will post them in a separate post.
The fourth annual conference of the Kaspersky Security Analyst Summit was held on February 16 and 17 in Cancun (in Mexico). This is a very important event for Kaspersky Lab, where we share our research and invite colleagues from other companies in the information security industry to speak. Two of our presentations have already been discussed at Habré: the studies of The Equation APT and Carbanak attracted a lot of attention (thanks, I enjoyed reading the comments, ready to answer the questions here). In this post - a brief report on the presentations of the research of Carbanak, The Equation and on the activities of another, previously unknown group, which we called Desert Falcons. All three - with links to detailed reports of our researchers on the site Securelist. Well, a few photos. Important: almost all performances will be available later in the video, we will post them in a separate post.Carbanak. Great robbery.
Article on Securelist (rus). Full report with technical details (eng). Indicators of compromise (format. IOC ).
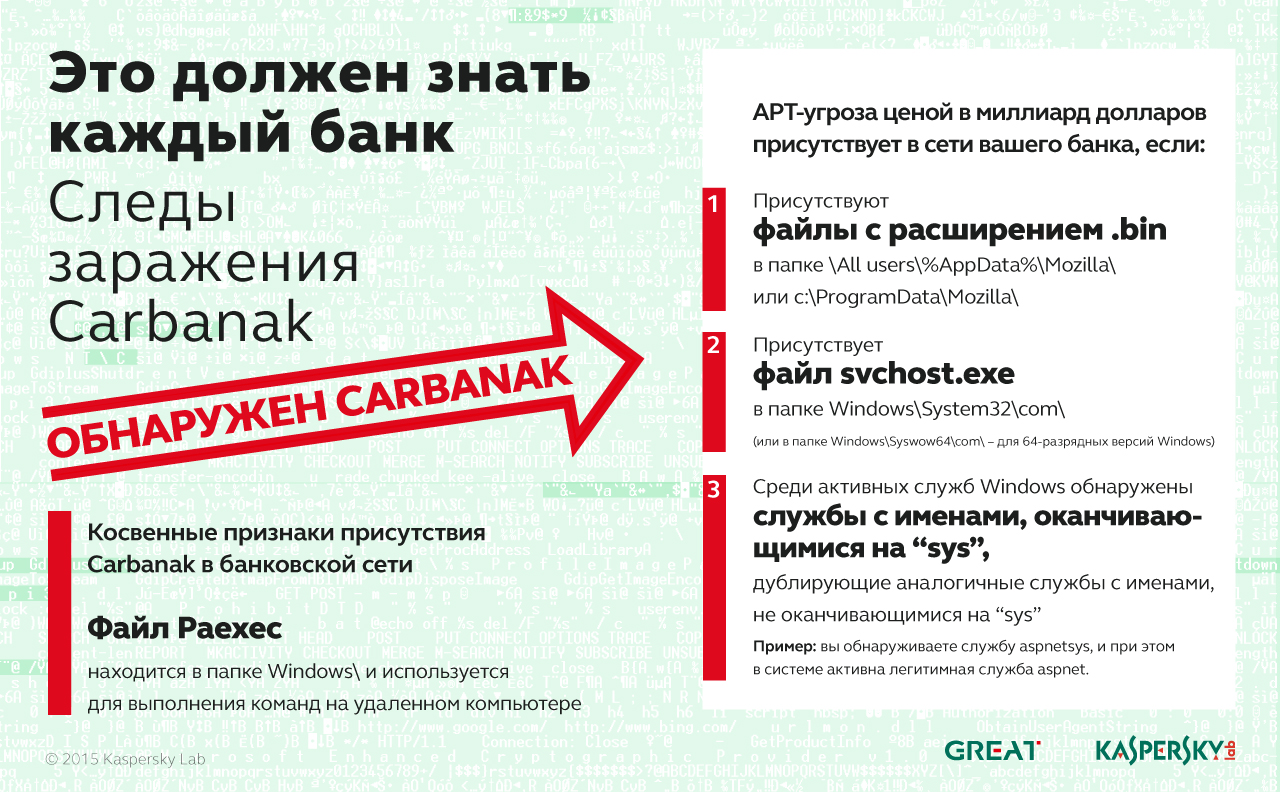
In discussions to this post, the most attention was paid to hacking ATMs. Indeed, this is probably the most resonant part of the history of Carbanak: we give the command and the ATM begins to issue money, without a card, a pin-code, just like that.
')

On this, the creators of Carbanak and pierced: it is clear that ATMs without outside interference themselves do not lead. Further investigation revealed that breaking into ATMs was just one of the ways to withdraw money. Attackers could transfer funds to their own accounts, manipulate the balance in such a way that numerous security systems did not notice. Without complete control over the domestic banking systems, it was impossible to turn such an operation. Therefore, after the penetration, various methods were used to collect information on how the bank's infrastructure is arranged, including video recording:

And the attack began quite simply, or rather familiarly:

An infected attachment letter that exploits Microsoft Office vulnerabilities (CVE-2012-0158; CVE-2013-3906) and Microsoft Word (CVE-2014-1761).
Where did the billion dollars come from?
The Carbanak study was conducted in close collaboration with law enforcement agencies from different countries. This part of the work at the SAS conference was told by Peter Zinn from the National Hi-Tech Crime Unit.

Information from law enforcement agencies allowed us to estimate the total number of victims of Carbanak - about one hundred financial organizations. Given that the loss of each victim ranged from 2.5 to 10 million dollars, the maximum damage from Carbanak could be just a billion dollars.
Batniki
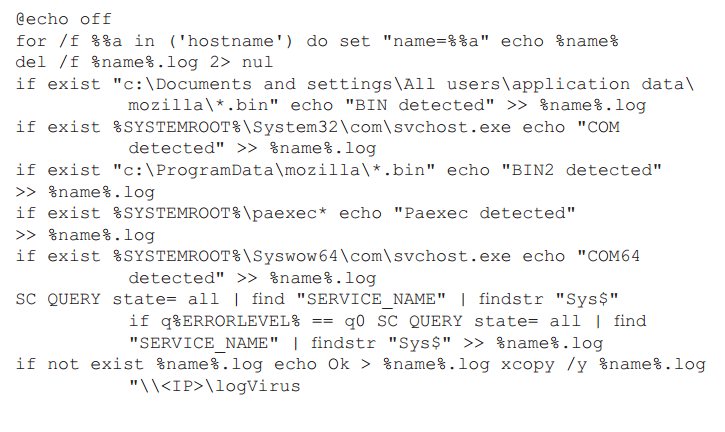
An interesting story occurred during the investigation, when the fact of infection was already confirmed and it was necessary to identify infected computers. It was necessary to do this as quickly as possible: firstly, to block the threat, and secondly - to collect samples for research. A simple script was written for this:
The Equation or “Staxnet, I Am Your Father” or the difficulties of attribution.
Article on Securelist (eng). Q & A (eng). Research module Fanny (eng).
All SAS guests this year were presented with a book by Kim Zetter about Stuxnet autographed by the author. For you to understand: this is such a Talmud of 500 pages, and, according to Zetter, the publisher asked for the maximum (as far as is generally possible) to reduce the technical details. If you ever write a book about The Equation, then its size will be no less. Important point: now the research of this operation is at the initial stage. We published only general details and disassembled one of the modules in detail. Further research will require time and effort from both the Lab and other companies. Why? Those who stand behind Equation APT have been in the business for more than 10 years, and maybe more than 20 (if you count the date of registration of the first domains for C & C servers).

Researchers at Kaspersky Lab, who spoke about The Equation at SAS: Igor Sumenkov, Sergey Mineev, Vitaly Kamlyuk, Kostin Raya.
Grzegorz Brzęczyszczykiewicz
We were able to reliably identify more than 500 victims of The Equation. Considering the fact that a self-destruction mechanism is built into the malicious modules of the operation, the total number of victims can amount to tens of thousands. Among them - government agencies, telecommunications companies, representatives of the aircraft industry, oil and gas sector and so on. And our investigation began when a man named Grzhegorzh Brzheshchikevich began to suspect that he was the victim of a malicious attack after he inserted a photo disk into the CD-ROM drive. The disc was sent to him from a scientific conference in Houston, in which he had previously participated.
Of course, we changed the name of this person because of confidentiality. It is possible that such a pseudonym was chosen thanks to this video:
What do we know about The Equation now? Judging by the dates of domain registration and compilation of modules, the campaign has been active for decades. The oldest modules, in particular, support Windows 95/98. To attack and gather information, different modules and different methods of infection were used (for example, through infection of forums). One of the modules, known as Fanny, was used to gather information about victims in Asia and the Middle East, was created in 2008 and exploited two Zero-Day vulnerabilities. The same vulnerabilities were later used in Stuxnet. The key word here is “later”, this fact, as well as some others, give a hint of a connection between Stuxnet and The Equation.
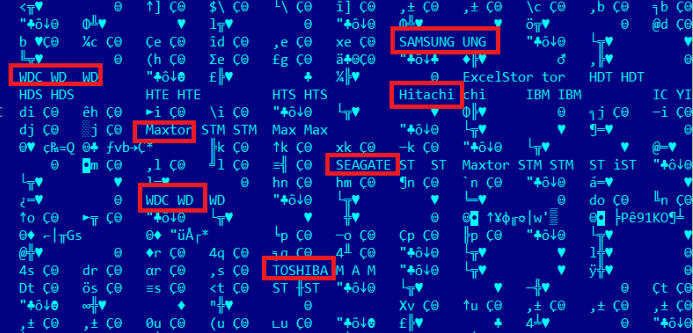
And this plugin is perhaps the most interesting. Known only by the file name (nls_933w.dll), it seems to be used very rarely, in exceptional cases, allowing to modify the firmware of the hard disk (or SSD). What for? Well, firstly, to regain control over the victim's computer, even in case of complete removal of information from the drive. Secondly, for reliable and most secretive data storage. The plugin code contains identifiers of 12 drive models that could have been subjected to this procedure. Given the complexity of analyzing the firmware and the fact that any error in the code in this case leads to a complete inoperability of the hard disk, this module shows how wide the possibilities of the group that created it are.
Attribution
This is a very important point: Kaspersky Lab cannot yet say anything about who exactly stands behind Equation APT. We simply do not have enough facts to reasonably accuse someone of involvement in this campaign, or at least identify the region or country from which the operation was conducted. Everything else at the moment - speculation and speculation, we do not do it. Attribution is generally a very difficult task, as even explicit hints about the origin of the malware creators found in the code (not in the Equation code, but in general) are sometimes made to direct researchers (or investigators) in the wrong direction.
The complexity of the attribution has been discussed more than once during the two days of the Security Analyst Summit. Here is an anecdotal example of a speculative approach in the presentation of Christopher Hoff of Juniper Networks:

Desert Falcons: New APT Campaign in the Middle East
Article on Securelist (eng). Detailed study (eng, pdf).

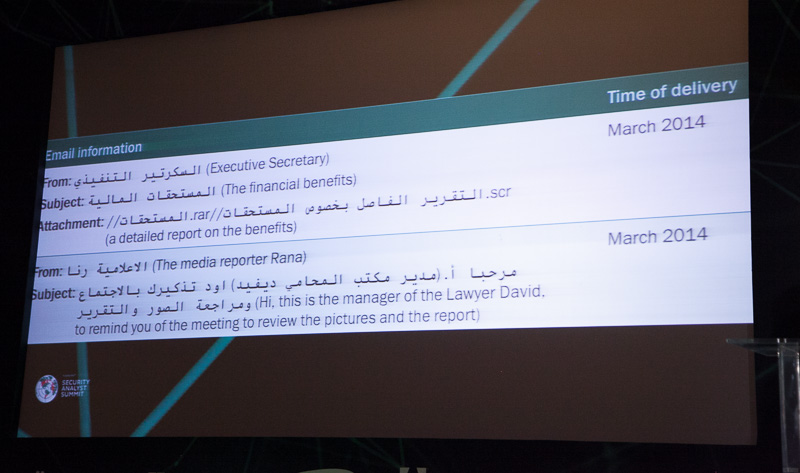
In Dmitri Bestuzhev's story about the Desert Falcons campaign, I was most surprised by how thoughtfully the attackers use social engineering techniques. Naturally, they attack via e-mail:
But not only. Use Facebook. Stuffing friends, chatting in private, preparing for months , enter into trust, to finally send a link to the infected file. Or simply: use the fact that influential people do not close the posting on their wall from other users. Immediately react to sign events that are important for potential victims and adapt their messages and mailings by e-mail.
Those behind the Desert Falcons campaign know their victims very well. Most likely because they themselves live in one of the countries of the Middle East. This is the main thing in this study: we see a new player developing his own tools for attacking and collecting information (and not using stolen), who knows the local landscape well. In contrast to The Equation, long and now inactive operations, “desert falcons” began to work relatively recently (since 2011), and are now in the best shape. Result: malware infecting computers and Android-based mobile devices to steal data and, according to our data, over a million files and documents from 3000+ victims fell into the hands of attackers.
Next in our blog. We are preparing several more topics on the basis of presentations at the Security Analyst Summit, including on the features of the use of legitimate software for criminal purposes, in particular - in crypto-fiber, which will be a separate review and statistics. You can get acquainted with quotes from almost all the speeches on SAS and the most interesting replicas of the audience in social networks in this epic live blog on Kaspersky Daily.
Source: https://habr.com/ru/post/250991/
All Articles