Sharing Cryptodisks on PC and Android
This article will look at an example of sharing CyberSafe Mobile cryptodisks on a personal computer and an Android device.

With the help of the CyberSafe program, as already shown in the article “CyberSafe - a cryptographer for all occasions” , you can create an encrypted virtual disk. In this article, we will look at sharing encrypted cryptodisk on a PC and Android device.
The scenario is the following: a virtual disk file is created on the computer and placed in a folder, this folder is “shared”, and CyberSafe Mobile (from CyberSoft LLC ) accesses this folder and mounts the virtual disk file it contains. Thus, the data (even in encrypted form!) Is not stored on your phone at all, it is stored only on a computer, and when working with files on a mobile phone, the virtual disk container on the PC is not mounted. Due to this, additional protection is achieved: the container on the computer is not even opened and not mounted, since the mounting is done on the phone, and the phone itself does not physically have a virtual disk file.
To solve the problem we need:
The article will show:
Before we begin to consider CyberSafe Mobile, I want to make a few comments about the program itself. First, CyberSaft Mobile prohibits taking screenshots of some of its screens for security reasons. So, a screenshot of entering a password or choosing a virtual container file will not work. It would be possible to use an emulator, but I really wanted to test everything on real devices, so some screenshots would be taken using the method of photographing, when the screen of one device is captured by the camera of the second device. Because of this, quality suffers, but you can be sure that everything written in the article will work for you - on real devices. If you're interested, I used an Acer Iconia B1 tablet and a Fly Era Style 3 smartphone (IQ4415 Quad).
Secondly, to operate the CyberSafe Mobile program, you need root rights, because without them you will not be able to mount the shared folder. You can read about how to get root rights specifically for your device . For my devices, I used the Universal Root program.
Thirdly, the article discusses the full version of the program - CyberSafe Mobile. Google Play has a free “lite” version of CyberSafe Mobile Lite, but it does not support mounting and does not know how to work with network folders.
')
Launch CyberSafe TopSecret and go to Disk Encryption, Virtual Disk . Click the Create button. In the Virtual Disk File window that appears, select the location of the virtual disk file, enter its name, and click the New button. Next, specify the parameters of the virtual disk (Fig. 1): the password for accessing the encrypted disk, the size in megabytes, the type of encryption and the file system (the default is NTFS).
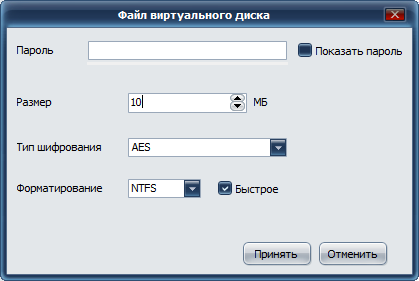
Fig. 1. Create a virtual disk
I think you should not read a separate and long lecture on how to choose the right password. As for the size of the disk, it should be noted that the program does not limit the size of the container file. Therefore, you can not be afraid to set the size of the virtual disk that exceeds the size of the operating memory of the smartphone - there is no need to limit the memory of the device.
When set all necessary parameters, click Accept . In fig. Figure 2 shows that two virtual disk files were created — one 100 MB in size, the second 10 MB in size. Both files are placed in the C: \ test folder (Fig. 3).
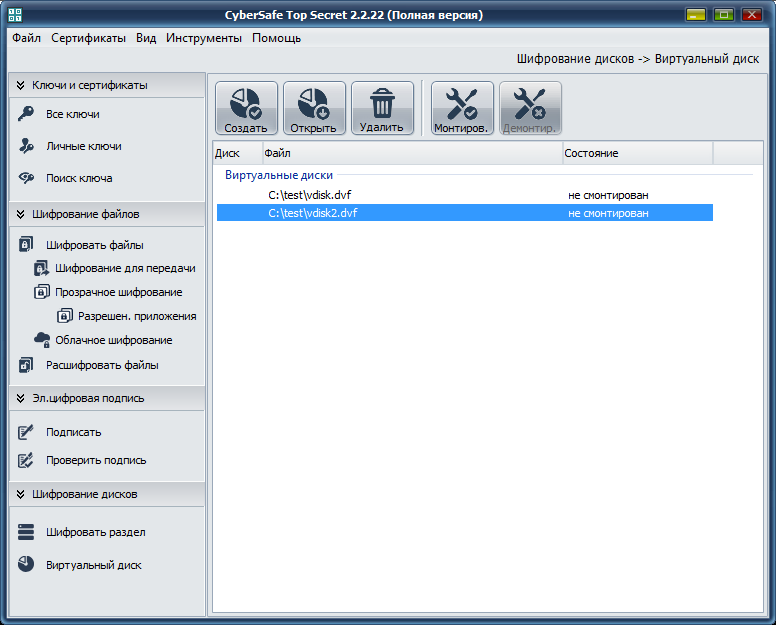
Fig. 2. CyberSafe TopSecret: Created Virtual Disks
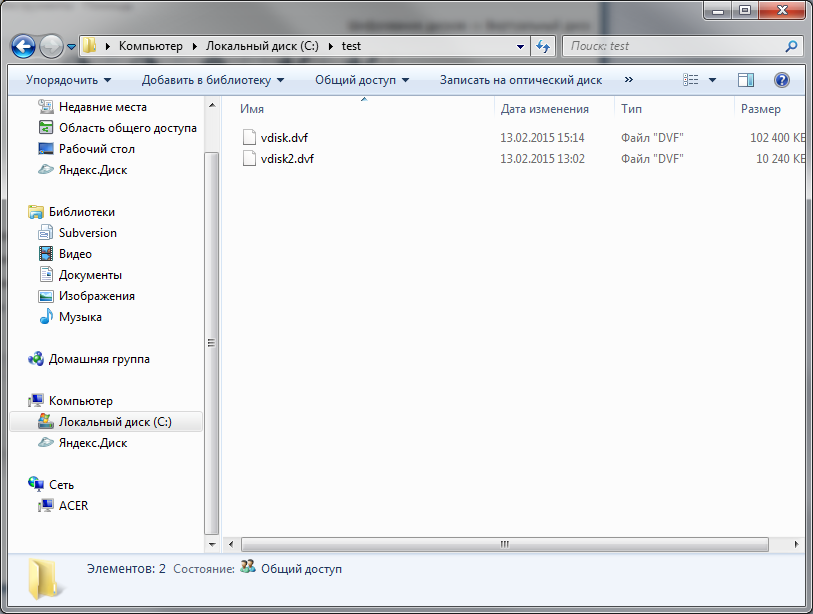
Fig. 3. Explorer: location of virtual disks and their sizes
Highlight one of the virtual disks and click Montirov . In the window that appears (Fig. 4), select the letter for the virtual disk. Next, the program will ask you to enter a password to access the disk.

Fig. 4. Select a letter for a virtual disk

Fig. 5. Password for access to virtual encrypted disk
In the program, the virtual disk will be marked as mounted, the letter to which this disk is mounted is also displayed (Fig. 6).
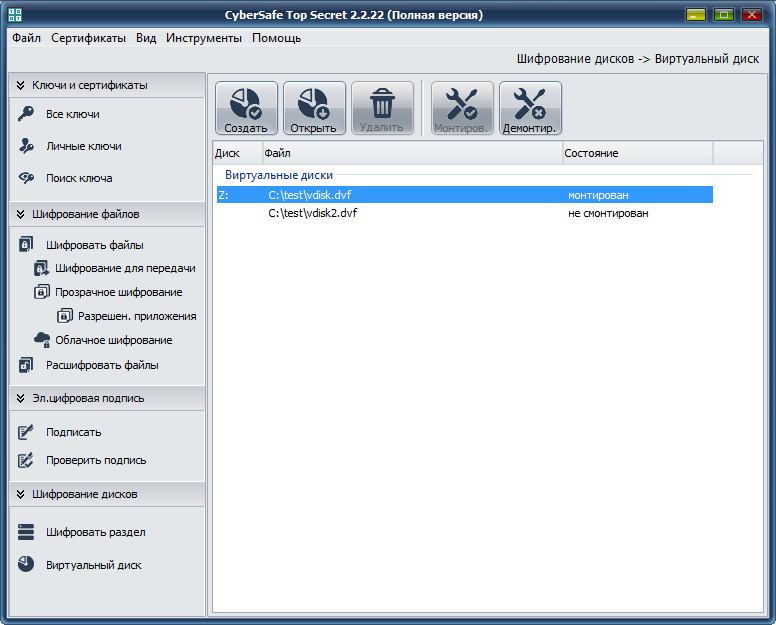
Fig. 6. Drive Z: mounted
Further, with the disk Z: you can work as with a regular disk, that is, write files to it, read files, etc. There are no restrictions, except that a virtual disk may run a little slower than a regular one. I put on disk Z: a few photos (Fig. 7).
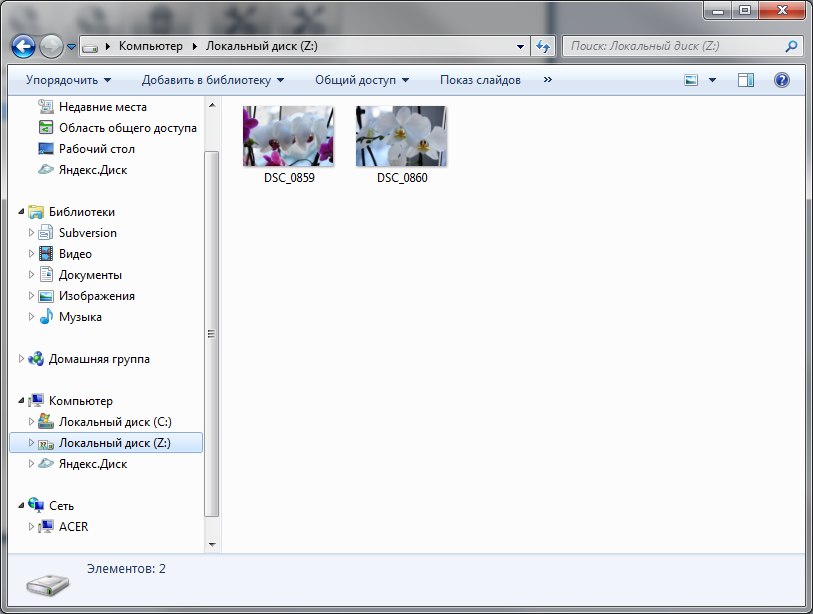
Fig. 7. The contents of the disk Z: (file vdisk.dvf)
The participation of the CyberSafe TopSecret program in our scenario is over. The disk can be unmounted, and the program itself can be closed.
Since the disk Z: you can work as with a regular disk, then you can come up with a fairly simple solution: “share” the disk Z: (Fig. 8) and mount it in the ES Explorer program on your Android device. In this case, the CyberSafe Mobile program is supposedly not needed at all. Consider this case in more detail so that you have no doubts.
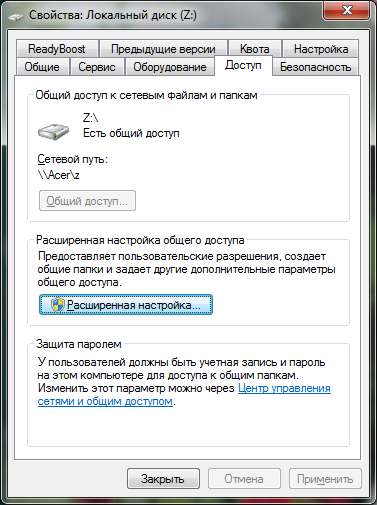
Fig. 8. Drive Z: shared
In the ES Explorer program, go to the Network, LAN section and click the Scan button to scan computers on the network (Fig. 9). Then everything, as usual - enter the username and password to connect to the share (it all depends on the settings of the shared access). The program will display a list of shared resources (Fig. 9), select the Z drive and see its contents - photos previously copied onto it (Fig. 10).

Fig. 9. Network scan result (left) and list of shared resources (right)

Fig. 10. Share Content
Everything would be fine if it were not for one thing. On your computer, the virtual encrypted disk is mounted, and the files are accessible to anyone who has physical access to it. Maybe when you need to copy several files from a virtual encrypted disk to a smartphone (where they will not be encrypted!) This method is suitable, but it completely kills all the advantages of encryption. Yes, and the network data is transmitted in unencrypted form. More information about the vulnerabilities of cryptocontainers with a remote attack was written in this article . This way of sharing a cryptodisk is wrong and it is strongly not recommended to use it.
This section will show you how to create an encrypted virtual disk file using CyberSafe Mobile and how to use it later. That is, the usual use of the program, not involving the use of network resources. These are the basics of using the program and without them you will not be able to fully use it.
Launch CyberSafe Mobile on your Android device. By default, you do not have registered safes (Fig. 11). The + button on the control panel allows you to create a new safe (that is, a virtual disk file), and the button that follows it will add an existing file. Using the add button of an existing virtual disk will be discussed further, but for now click the + button.

Fig. 11. No safes registered
Enter or select the path to the safe, specify its size (I left the default size - 5 MB, who is confused by such a small size, do not forget that we work with a mobile device) and password, see fig. 12. Next, the created safe will appear in the list on the Safes tab (fig. 12).
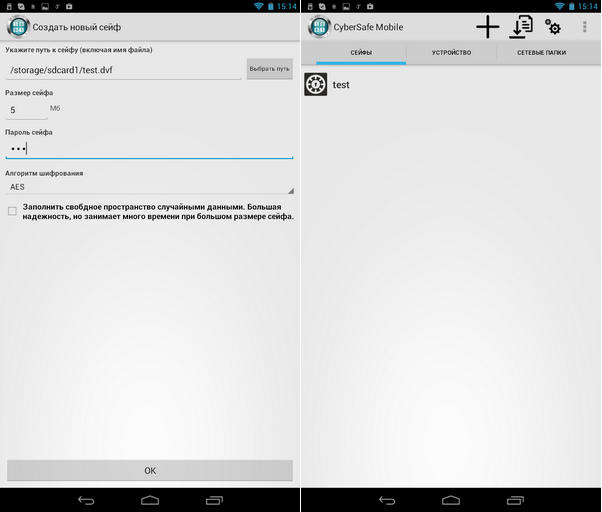
Fig. 12. Create a virtual disk on your Android device (left) and the Safes tab (right)
Before you open the safe, you need to set several important parameters of the program. Click the button with the image of the gear and in the appeared menu select Mount options (fig. 13). Here you need to choose:
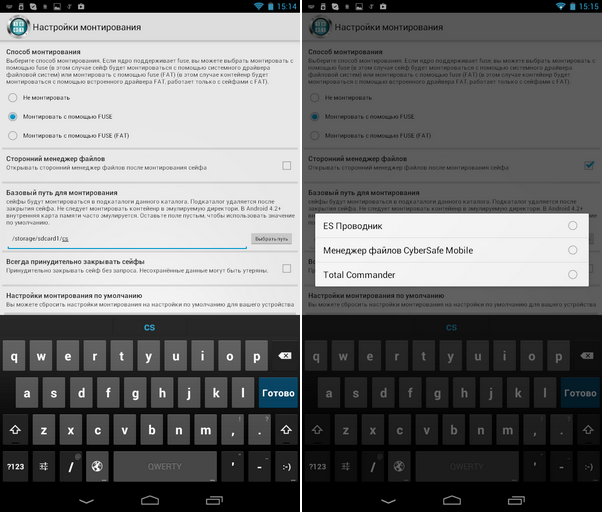
Fig. 13. Mount options (left) and select third-party file manager (right)
Next, go back to the Safes tab and click the created safe test to open it. The program will ask you to enter the password specified when creating the safe. After that, you will see the contents of the safe in the file manager of your choice (in our case - in the ES Explorer), see fig. 14. Clear business, in the safe is empty. Therefore, copy several files into it (Fig. 14).
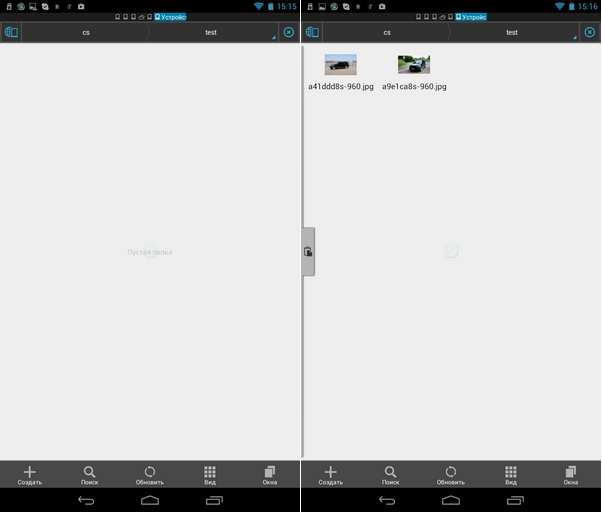
Fig. 14. Safe is open (left) and files are copied into it (right)
To close the safe, go back to CyberSafe Mobile, press and hold the safe test. In the menu that appears (fig. 15), select the Close command.
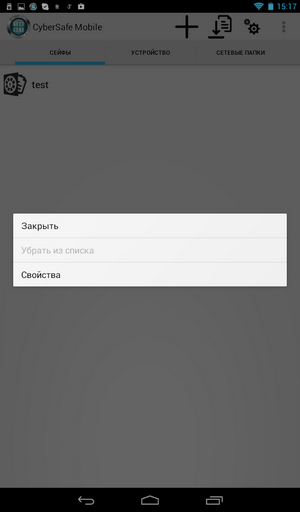
Fig. 15. How to close the safe
We have just reviewed the usual sequence of actions when working with a safe. In the next section, the task will be a little more difficult - after all, the safe will be on a remote computer.
Now it will be shown how to share cryptodisk correctly. Let me remind you that we have two virtual disk files stored in the test folder. This folder is shared, and the folder itself is stored on the Acer machine (Figure 16).

Fig. 16. The folder C: \ test is shared
It should also be noted that the virtual disk should not be mounted on a PC, and the CyberSafe TopSecret program on the Windows computer should be closed - for the purity of the experiment.
Click the Network Folders tab (Figure 17) of CyberSafe Mobile. By default, no network folder is registered.
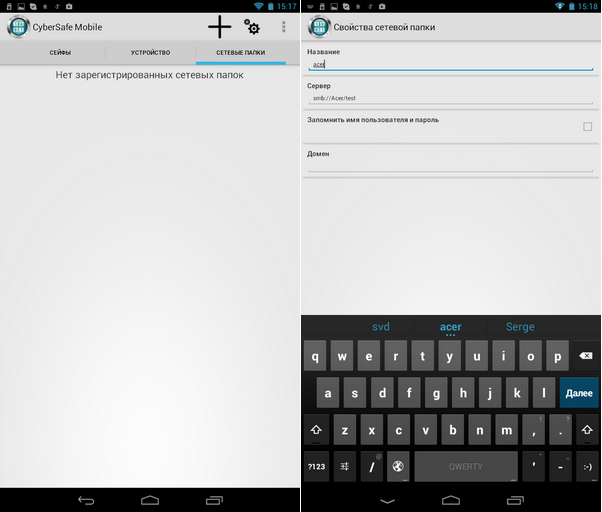
Fig. 17. No network folders (left). Add network folder (right)
Click the + button to add a network folder. Enter the path to the network folder in the format smb: // machine / resource. In our case, you need to enter smb: // Acer / test. As the name of the network folder, I used the name of the machine (Acer), you can use whatever you want. Please note that when mounting to the mount point specified in the settings, not the name you entered (Acer) will be used, but the name of the “shared” folder (test).
The network folder will be added to the list (Fig. 18). If you click on this folder, you will see a window for entering a username and password to connect to your Acer computer. After that you will see the contents of the "shared" folder. And here I apologize for the quality of the illustration - the program does not allow taking a screenshot and viewing the contents of the network folder, so I had to take a photo with a mobile phone. Everything was photographed on the Fly IQ4415 - in everything except the camera, an excellent phone (Fig. 19).

Fig. 18. Network folder added to list

Fig. 19. Network folder contents
As you can see, our network folder contains the same two files (vdisk.dvf and vdisk2.dvf) created at the beginning of the article. Now press the Back button (this is the Android button, not the program) to return to the list of network folders. Press the folder and hold your finger for a few seconds to display the folder menu (fig. 20). Choose Mount .

Fig. 20. Mounting the folder (left). Network folder mounted (right)
You can open ES Explorer to make sure that the folder has been mounted to the / storage / sdcard1 / cs directory and there are those two files in it (fig. 20).
The only thing left is to go to the Safes section and click the Add Safe button (it is located right behind the + button). The screen again appears, a screenshot of which cannot be made. Therefore, again - low-quality illustration (Fig. 21a, 21b). Go to / storage / sdcard1 / cs / test and select the virtual disk file you need.

Fig. 21a. Selecting a virtual disk file
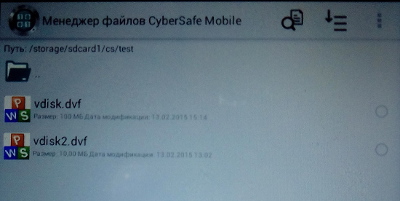
Fig. 21b. Selecting a virtual disk file
After that, the program will request a password to access the safe. If the password is correct, the program will place the safe in the list of safes, mount it and launch ES Explorer to work with its files (Fig. 22).
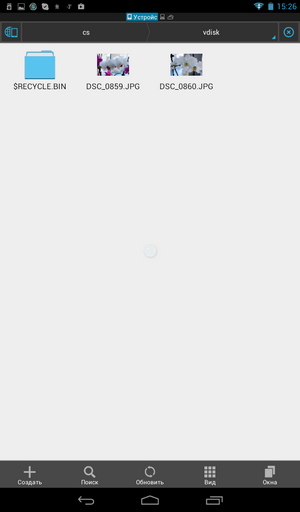
Fig. 22. The contents of the virtual disk
As you can see, we are contemplating the same photos that I put on a virtual disk when it was created at the beginning of the article. It is worth noting that the program works equally well, both with large disks and relatively small disks, which I created to demonstrate the work of the program. The performance of the program is enough to view the movie stored in the safe without copying it to the SD card of the device.
The article “Protecting personal photos on Android phones” showed how using the URSafe Media Redirector program to automatically redirect photos taken by your smartphone’s camera to a safe. So no one can view your photos after closing the safe. In this article we will use the same principle, only the safe will be removed - it will be located on your computer.
First of all, install the URSafe Media Redirector program, launch it and click the Add button to create a new redirect (Fig. 23).

Fig. 23. URSafe Media Redirector program (left) and redirection setting (right)
By clicking the Browse Folder button opposite the Path From label, select the folder in which the Camera application places your photos. On my Acer B1 tablet, the photos are placed in the / storage / sdcard0 / DCIM / Camera directory. You may have another folder. Then click the Browse Folder button and select the folder to which you are mounting the safe (Fig. 23). Click the Save button to save the redirect.
Next you will see a list of redirections created. In the free version of the URSafe Media Redirector program, only the first redirect will work (in our case, the first and only). Highlight it and press the On / Off button to turn it on. In fig. 24 redirection is already included, as evidenced by the green daw.
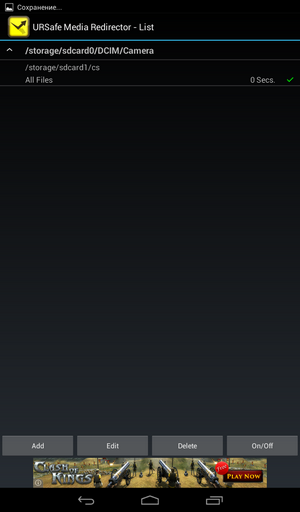
Fig. 24. Redirect is active
Launch the Camera app and take any picture. Then close the safe and go to the computer. Mount the virtual disk file and view its contents - you will find a new photo on it (Fig. 25).
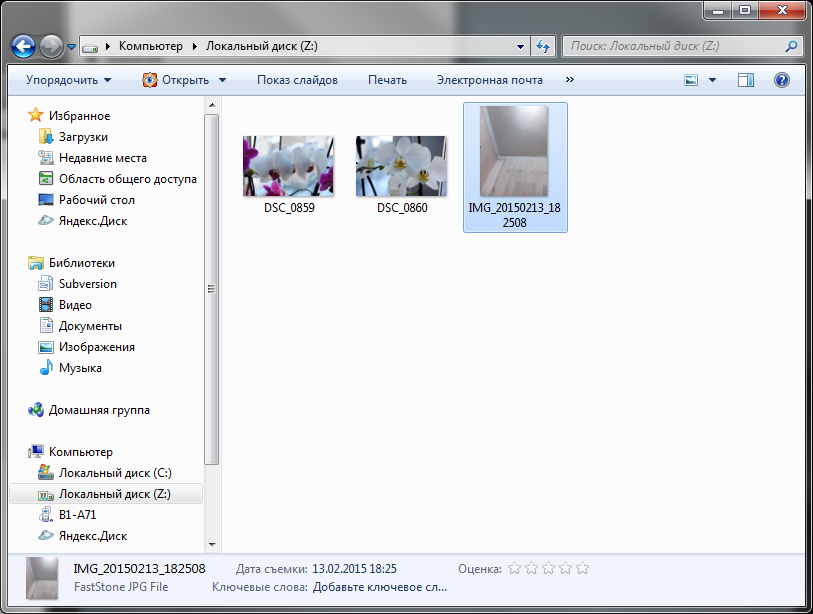
Fig. 25. Photo taken on Android device
The task is completed. The data is not stored in the phone, but on the computer, and collaboration with the cryptocontainer is ensured. If you wish, you can not be limited to a local wireless network, but create a remote “ball”. You can read about this in the article “Storing data in a crypto-container on a remote server and working with them from Android devices” .
CyberSafe Mobile Software Description
CyberSafe Mobile on Google Play
Mount safe (video)

Formulation of the problem
With the help of the CyberSafe program, as already shown in the article “CyberSafe - a cryptographer for all occasions” , you can create an encrypted virtual disk. In this article, we will look at sharing encrypted cryptodisk on a PC and Android device.
The scenario is the following: a virtual disk file is created on the computer and placed in a folder, this folder is “shared”, and CyberSafe Mobile (from CyberSoft LLC ) accesses this folder and mounts the virtual disk file it contains. Thus, the data (even in encrypted form!) Is not stored on your phone at all, it is stored only on a computer, and when working with files on a mobile phone, the virtual disk container on the PC is not mounted. Due to this, additional protection is achieved: the container on the computer is not even opened and not mounted, since the mounting is done on the phone, and the phone itself does not physically have a virtual disk file.
To solve the problem we need:
- PC or laptop with Windows operating system (this article uses 64-bit Windows 7);
- Android device with root access (smartphone or tablet);
- CyberSafe TopSecret installed on your computer;
- CyberSafe Mobile installed on a mobile device.
The article will show:
- How to use CyberSafe Mobile without mounting a remote container file (normal use of the program).
- How to mount a remote virtual disk container and do it correctly.
- How to use folder redirection to automatically encrypt your photos
Before we begin to consider CyberSafe Mobile, I want to make a few comments about the program itself. First, CyberSaft Mobile prohibits taking screenshots of some of its screens for security reasons. So, a screenshot of entering a password or choosing a virtual container file will not work. It would be possible to use an emulator, but I really wanted to test everything on real devices, so some screenshots would be taken using the method of photographing, when the screen of one device is captured by the camera of the second device. Because of this, quality suffers, but you can be sure that everything written in the article will work for you - on real devices. If you're interested, I used an Acer Iconia B1 tablet and a Fly Era Style 3 smartphone (IQ4415 Quad).
Secondly, to operate the CyberSafe Mobile program, you need root rights, because without them you will not be able to mount the shared folder. You can read about how to get root rights specifically for your device . For my devices, I used the Universal Root program.
Thirdly, the article discusses the full version of the program - CyberSafe Mobile. Google Play has a free “lite” version of CyberSafe Mobile Lite, but it does not support mounting and does not know how to work with network folders.
')
Creating a virtual disk container on a PC
Launch CyberSafe TopSecret and go to Disk Encryption, Virtual Disk . Click the Create button. In the Virtual Disk File window that appears, select the location of the virtual disk file, enter its name, and click the New button. Next, specify the parameters of the virtual disk (Fig. 1): the password for accessing the encrypted disk, the size in megabytes, the type of encryption and the file system (the default is NTFS).

Fig. 1. Create a virtual disk
I think you should not read a separate and long lecture on how to choose the right password. As for the size of the disk, it should be noted that the program does not limit the size of the container file. Therefore, you can not be afraid to set the size of the virtual disk that exceeds the size of the operating memory of the smartphone - there is no need to limit the memory of the device.
When set all necessary parameters, click Accept . In fig. Figure 2 shows that two virtual disk files were created — one 100 MB in size, the second 10 MB in size. Both files are placed in the C: \ test folder (Fig. 3).

Fig. 2. CyberSafe TopSecret: Created Virtual Disks

Fig. 3. Explorer: location of virtual disks and their sizes
Highlight one of the virtual disks and click Montirov . In the window that appears (Fig. 4), select the letter for the virtual disk. Next, the program will ask you to enter a password to access the disk.

Fig. 4. Select a letter for a virtual disk

Fig. 5. Password for access to virtual encrypted disk
In the program, the virtual disk will be marked as mounted, the letter to which this disk is mounted is also displayed (Fig. 6).

Fig. 6. Drive Z: mounted
Further, with the disk Z: you can work as with a regular disk, that is, write files to it, read files, etc. There are no restrictions, except that a virtual disk may run a little slower than a regular one. I put on disk Z: a few photos (Fig. 7).

Fig. 7. The contents of the disk Z: (file vdisk.dvf)
The participation of the CyberSafe TopSecret program in our scenario is over. The disk can be unmounted, and the program itself can be closed.
Incorrect sharing of cryptodisk on PC and Android
Since the disk Z: you can work as with a regular disk, then you can come up with a fairly simple solution: “share” the disk Z: (Fig. 8) and mount it in the ES Explorer program on your Android device. In this case, the CyberSafe Mobile program is supposedly not needed at all. Consider this case in more detail so that you have no doubts.

Fig. 8. Drive Z: shared
In the ES Explorer program, go to the Network, LAN section and click the Scan button to scan computers on the network (Fig. 9). Then everything, as usual - enter the username and password to connect to the share (it all depends on the settings of the shared access). The program will display a list of shared resources (Fig. 9), select the Z drive and see its contents - photos previously copied onto it (Fig. 10).

Fig. 9. Network scan result (left) and list of shared resources (right)

Fig. 10. Share Content
Everything would be fine if it were not for one thing. On your computer, the virtual encrypted disk is mounted, and the files are accessible to anyone who has physical access to it. Maybe when you need to copy several files from a virtual encrypted disk to a smartphone (where they will not be encrypted!) This method is suitable, but it completely kills all the advantages of encryption. Yes, and the network data is transmitted in unencrypted form. More information about the vulnerabilities of cryptocontainers with a remote attack was written in this article . This way of sharing a cryptodisk is wrong and it is strongly not recommended to use it.
Normal Use CyberSafe Mobile
This section will show you how to create an encrypted virtual disk file using CyberSafe Mobile and how to use it later. That is, the usual use of the program, not involving the use of network resources. These are the basics of using the program and without them you will not be able to fully use it.
Launch CyberSafe Mobile on your Android device. By default, you do not have registered safes (Fig. 11). The + button on the control panel allows you to create a new safe (that is, a virtual disk file), and the button that follows it will add an existing file. Using the add button of an existing virtual disk will be discussed further, but for now click the + button.

Fig. 11. No safes registered
Enter or select the path to the safe, specify its size (I left the default size - 5 MB, who is confused by such a small size, do not forget that we work with a mobile device) and password, see fig. 12. Next, the created safe will appear in the list on the Safes tab (fig. 12).

Fig. 12. Create a virtual disk on your Android device (left) and the Safes tab (right)
Before you open the safe, you need to set several important parameters of the program. Click the button with the image of the gear and in the appeared menu select Mount options (fig. 13). Here you need to choose:
- Mount Method — Mount is off by default, so you need to turn it on. On my devices, mount using FUSE worked fine, but if you have problems with this method, select FUSE (FAT).
- Base Mount Path - click the Select Path button to select the folder to which the mount will be performed. The folder must exist. I will mount safes and “shared” folders to / storage / sdcard1 / cs. For each safe / shared folder in the directory you selected, a subdirectory will be created, the name of which will be the same as the name of the resource being mounted. For example, if you try to mount the test.dvf file created earlier, it will be mounted to the / storage / sdcard1 / cs / test folder. After unmounting this subdirectory (test) will be deleted.
- Third-party file manager - CyberSafe Mobile has a built-in file manager, but I think many Android users will be more accustomed to using ES Explorer (Figure 13).

Fig. 13. Mount options (left) and select third-party file manager (right)
Next, go back to the Safes tab and click the created safe test to open it. The program will ask you to enter the password specified when creating the safe. After that, you will see the contents of the safe in the file manager of your choice (in our case - in the ES Explorer), see fig. 14. Clear business, in the safe is empty. Therefore, copy several files into it (Fig. 14).

Fig. 14. Safe is open (left) and files are copied into it (right)
To close the safe, go back to CyberSafe Mobile, press and hold the safe test. In the menu that appears (fig. 15), select the Close command.

Fig. 15. How to close the safe
We have just reviewed the usual sequence of actions when working with a safe. In the next section, the task will be a little more difficult - after all, the safe will be on a remote computer.
Proper cryptodisc sharing on PC and Android
Now it will be shown how to share cryptodisk correctly. Let me remind you that we have two virtual disk files stored in the test folder. This folder is shared, and the folder itself is stored on the Acer machine (Figure 16).

Fig. 16. The folder C: \ test is shared
It should also be noted that the virtual disk should not be mounted on a PC, and the CyberSafe TopSecret program on the Windows computer should be closed - for the purity of the experiment.
Click the Network Folders tab (Figure 17) of CyberSafe Mobile. By default, no network folder is registered.

Fig. 17. No network folders (left). Add network folder (right)
Click the + button to add a network folder. Enter the path to the network folder in the format smb: // machine / resource. In our case, you need to enter smb: // Acer / test. As the name of the network folder, I used the name of the machine (Acer), you can use whatever you want. Please note that when mounting to the mount point specified in the settings, not the name you entered (Acer) will be used, but the name of the “shared” folder (test).
The network folder will be added to the list (Fig. 18). If you click on this folder, you will see a window for entering a username and password to connect to your Acer computer. After that you will see the contents of the "shared" folder. And here I apologize for the quality of the illustration - the program does not allow taking a screenshot and viewing the contents of the network folder, so I had to take a photo with a mobile phone. Everything was photographed on the Fly IQ4415 - in everything except the camera, an excellent phone (Fig. 19).

Fig. 18. Network folder added to list

Fig. 19. Network folder contents
As you can see, our network folder contains the same two files (vdisk.dvf and vdisk2.dvf) created at the beginning of the article. Now press the Back button (this is the Android button, not the program) to return to the list of network folders. Press the folder and hold your finger for a few seconds to display the folder menu (fig. 20). Choose Mount .

Fig. 20. Mounting the folder (left). Network folder mounted (right)
You can open ES Explorer to make sure that the folder has been mounted to the / storage / sdcard1 / cs directory and there are those two files in it (fig. 20).
The only thing left is to go to the Safes section and click the Add Safe button (it is located right behind the + button). The screen again appears, a screenshot of which cannot be made. Therefore, again - low-quality illustration (Fig. 21a, 21b). Go to / storage / sdcard1 / cs / test and select the virtual disk file you need.

Fig. 21a. Selecting a virtual disk file

Fig. 21b. Selecting a virtual disk file
After that, the program will request a password to access the safe. If the password is correct, the program will place the safe in the list of safes, mount it and launch ES Explorer to work with its files (Fig. 22).

Fig. 22. The contents of the virtual disk
As you can see, we are contemplating the same photos that I put on a virtual disk when it was created at the beginning of the article. It is worth noting that the program works equally well, both with large disks and relatively small disks, which I created to demonstrate the work of the program. The performance of the program is enough to view the movie stored in the safe without copying it to the SD card of the device.
Use redirector to protect your photos
The article “Protecting personal photos on Android phones” showed how using the URSafe Media Redirector program to automatically redirect photos taken by your smartphone’s camera to a safe. So no one can view your photos after closing the safe. In this article we will use the same principle, only the safe will be removed - it will be located on your computer.
First of all, install the URSafe Media Redirector program, launch it and click the Add button to create a new redirect (Fig. 23).

Fig. 23. URSafe Media Redirector program (left) and redirection setting (right)
By clicking the Browse Folder button opposite the Path From label, select the folder in which the Camera application places your photos. On my Acer B1 tablet, the photos are placed in the / storage / sdcard0 / DCIM / Camera directory. You may have another folder. Then click the Browse Folder button and select the folder to which you are mounting the safe (Fig. 23). Click the Save button to save the redirect.
Next you will see a list of redirections created. In the free version of the URSafe Media Redirector program, only the first redirect will work (in our case, the first and only). Highlight it and press the On / Off button to turn it on. In fig. 24 redirection is already included, as evidenced by the green daw.

Fig. 24. Redirect is active
Launch the Camera app and take any picture. Then close the safe and go to the computer. Mount the virtual disk file and view its contents - you will find a new photo on it (Fig. 25).

Fig. 25. Photo taken on Android device
The task is completed. The data is not stored in the phone, but on the computer, and collaboration with the cryptocontainer is ensured. If you wish, you can not be limited to a local wireless network, but create a remote “ball”. You can read about this in the article “Storing data in a crypto-container on a remote server and working with them from Android devices” .
Links
CyberSafe Mobile Software Description
CyberSafe Mobile on Google Play
Mount safe (video)
Source: https://habr.com/ru/post/250599/
All Articles