Got access to iPhone diagnostic console
The Lightning connector introduced by Apple, along with the release of iPhone 5, replaced the usual 30-pin connector. The appearance of a new connector marked the end of an era of free connectivity to devices. In the old connector, sound, video, data, power were transmitted by individual pins and there was no problem with using non-original cables. In the new connector, a separate chip appeared responsible for the originality of the accessory origin, as well as its type (USB-HOST, USB-DEVICE, SERIAL, POWER-ONLY).
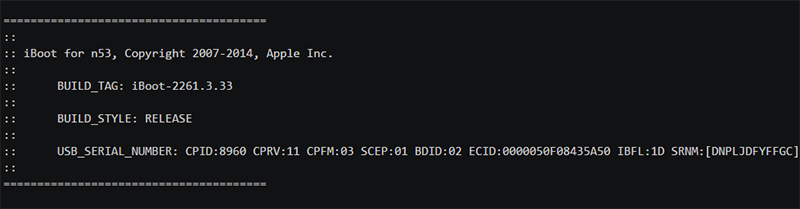
For a long time, the protocol remained a mystery. Recently, he was able to crack the French explorer Ramtin Amin (Ramtin Amin). He was able to access the serial console (serial console) via the Lightning connector. Probably this will become a new direction in the search and exploitation of vulnerabilities.
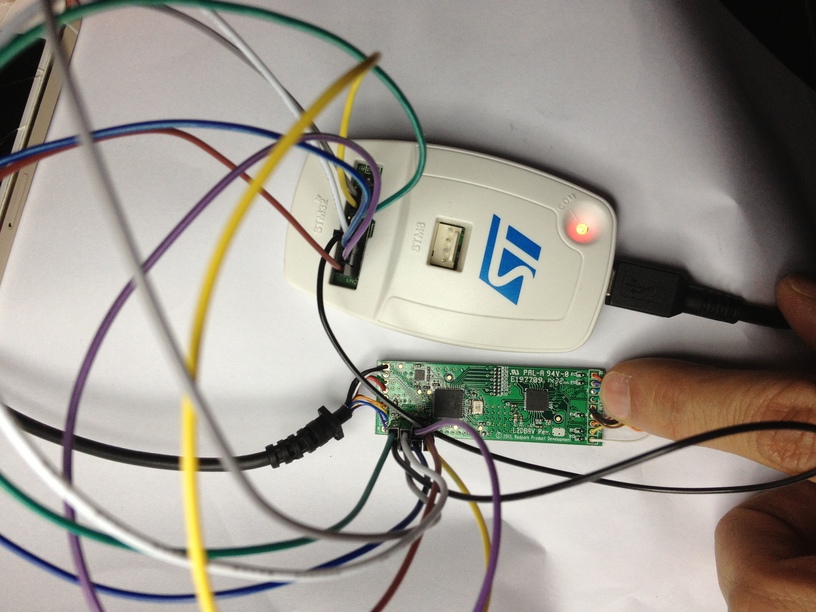
Ramtin began with reverse engineering with examining patents, searching for suppliers and other devices using similar equipment. He found a Lightning to Serial converter built on an STM32 chip. According to the results of the study of the controller's firmware, information from the logic analyzer, he managed to recover part of the protocol, most of the wiring diagram.
')
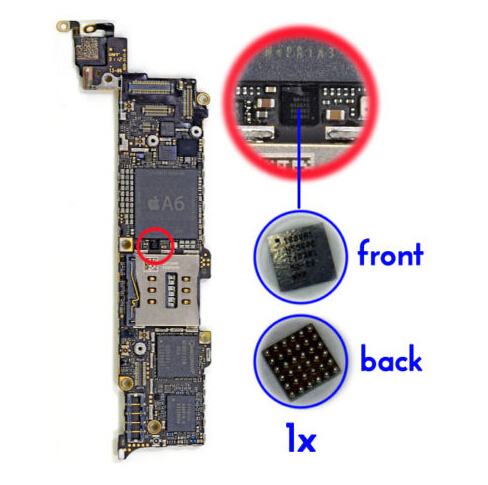
During the first research of the internal device of the iPhone 5 immediately after it became commercially available, many identified a chip better known as Tristar (more specifically CBTL1608A1) as a DisplayPort multiplexer. It turned out that this is a multiplexer, but not for DisplayPort, but for connecting accessories with a Lightning connector to the UART, debug UART, baseband, SoC, JTAG.
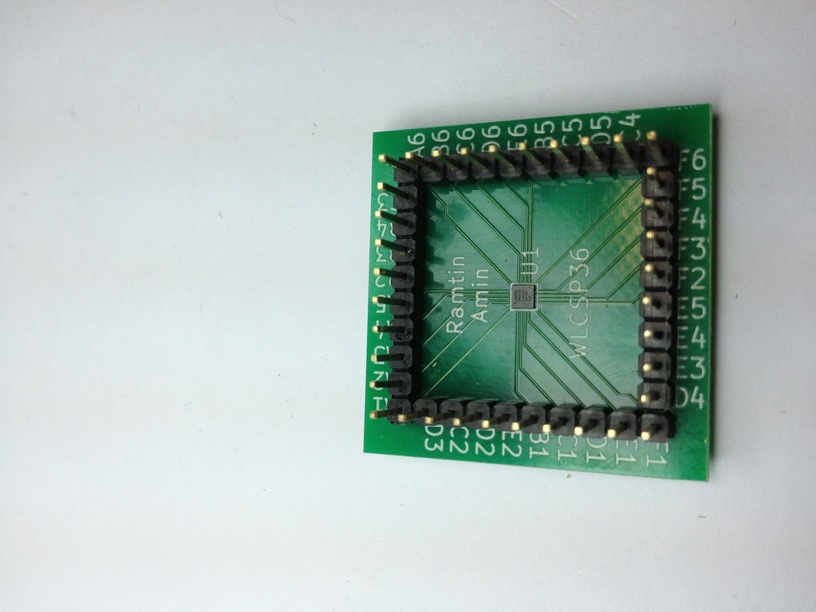
Working with a microcircuit turned out to be quite complicated, since This is a BGA chip measuring 2.5x2.5 mm and having 36 soldering points with 0.35 mm pitch. Ramtin managed to drop out and transfer the chip to the prototyping board. Having connected using the STM32F4Discovery card, he managed to look into the principles of operation of the device.
While it does not give full control over the device. But perhaps future exploits will start with this:
Link with a detailed description of the process http://ramtin-amin.fr/#tristar
I will be glad to hear your error messages or other suggestions in the LAN .

For a long time, the protocol remained a mystery. Recently, he was able to crack the French explorer Ramtin Amin (Ramtin Amin). He was able to access the serial console (serial console) via the Lightning connector. Probably this will become a new direction in the search and exploitation of vulnerabilities.
Ramtin began with reverse engineering with examining patents, searching for suppliers and other devices using similar equipment. He found a Lightning to Serial converter built on an STM32 chip. According to the results of the study of the controller's firmware, information from the logic analyzer, he managed to recover part of the protocol, most of the wiring diagram.
')

During the first research of the internal device of the iPhone 5 immediately after it became commercially available, many identified a chip better known as Tristar (more specifically CBTL1608A1) as a DisplayPort multiplexer. It turned out that this is a multiplexer, but not for DisplayPort, but for connecting accessories with a Lightning connector to the UART, debug UART, baseband, SoC, JTAG.

Working with a microcircuit turned out to be quite complicated, since This is a BGA chip measuring 2.5x2.5 mm and having 36 soldering points with 0.35 mm pitch. Ramtin managed to drop out and transfer the chip to the prototyping board. Having connected using the STM32F4Discovery card, he managed to look into the principles of operation of the device.

While it does not give full control over the device. But perhaps future exploits will start with this:
Link with a detailed description of the process http://ramtin-amin.fr/#tristar
I will be glad to hear your error messages or other suggestions in the LAN .
Source: https://habr.com/ru/post/250579/
All Articles