Microsoft released a set of updates for its products, February 2015
Microsoft updated its products, releasing three updates with Critical status and six Important. Windows, Internet Explorer, Office, and Server software products were repaired, 56 vulnerabilities were fixed for them, and 41 vulnerabilities were fixed in IE ( MS15-009 ). This is the maximum number of vulnerabilities that have been closed for this browser over the past few years. Most of these vulnerabilities are of the Remote Code Execution type and can be used by attackers to conduct drive-by download attacks. One of the vulnerabilities closed in IE (CVE-2015-0071) is used by attackers in targeted attacks to bypass the ASLR security mechanism .

Update MS15-009 fixes 41 vulnerabilities in IE 6-11. Most of the fixed vulnerabilities are of the Remote Code Execution (RCE) type and can be used by attackers to install malware using a specially crafted web page. The exceptions are the following vulnerabilities.
')

ASLR bypass vulnerabilities can only be exploited by attackers in conjunction with other RCE vulnerabilities in IE and make the exploit more reliable in providing information about addresses in memory. Critical. Exploitation detected .
The MS15-010 update fixes six different types of vulnerabilities in kernel-mode drivers (Windows 2003 Server - 8.1 / RT 8.1).
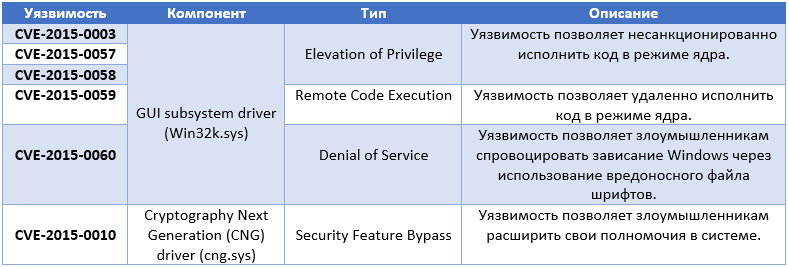
Vulnerability CVE-2015-0059 is very dangerous because it allows attackers to remotely execute code in kernel mode. For this purpose, a specially formed font file can be placed on a resource on the network. The exploitation of such a vulnerability allows you to execute shellcode from a font file directly in kernel mode ( user mode restrictions bypass ). Critical. Exploitation Less Likely .
The MS15-011 update fixes one CVE-2015-0008 vulnerability of the Remoe Code Execution type in the Group Policy mechanism. Using a vulnerability, an attacker can remotely execute code in a vulnerable system by luring a user to a malicious website on a network that is under the control of an attacker. Critical. Exploitation More Likely .
Update MS15-012 fixes three vulnerabilities in all supported versions of Office 2007-2010-2013. Vulnerabilities in Word & Excel allow attackers to remotely execute their code through a specially crafted Office document. To exploit a vulnerability, such a document can be sent to the victim in an email attachment. Important. Exploitation More Likely .
The MS15-013 update fixes one Security Feature Bypass (SFB) CVE-2014-6362 (use-after-free) vulnerability in all supported versions of Office. The vulnerability allows attackers to bypass ASLR (ASLR bypass) and develop more stable exploits for remote code execution via Office or IE. For the latest version of Office 2013, Otkloadr_msosec.dll (x64), Msosec.dll, Msvcr71.dll, Otkloadr.dll are subject to upgrade. Important. Exploitation More Likely .
The MS15-014 update fixes one SFE-type CVE-2015-0009 vulnerability in the Group Policy component (Windows 2003 Server - 8.1 / RT 8.1). Using the Man-in-the-Middle attack mechanism, an attacker could compromise a domain controller. Important. Exploitation Less Likely .
The MS15-015 update fixes one CVE-2015-0062 type Elevation of Privilege vulnerability in the Windows kernel (ntoskrnl.exe & hal.dll). An attacker can increase his privileges in the system due to a flaw in the process creation function (WIndows 7 - Windows 8.1 / RT 8.1). Important. Exploitation Less Likely .
Update MS15-016 fixes one Information Disclosure VEVE-2015-0061 vulnerability in the component for processing graphic TIFF files in Windows 2003 Server - 8.1 / RT 8.1. The attacker may unauthorized access to the information of the user (client) when placed on a web resource in a specially formed TIFF file. Important. Exploitation Less Likely .
Update MS15-017 fixes one vulnerability CVE-2015-0012 of type Elevation of Privilege in the Virtual Machine Manager (VMM) component for System Center Virtual Machine Manager. Using a vulnerability, an attacker can elevate his privileges in the system to the SYSTEM level. Important. Exploitation Less Likely .
0 - Exploitation Detected
Vulnerability is exploited in-the-wild. That is, it was established that attackers use an exploit for this vulnerability to successfully attack users. Highest hazard index.
1 - Exploitation More Likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploitation Less Likely
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).

be secure.

Update MS15-009 fixes 41 vulnerabilities in IE 6-11. Most of the fixed vulnerabilities are of the Remote Code Execution (RCE) type and can be used by attackers to install malware using a specially crafted web page. The exceptions are the following vulnerabilities.
')

ASLR bypass vulnerabilities can only be exploited by attackers in conjunction with other RCE vulnerabilities in IE and make the exploit more reliable in providing information about addresses in memory. Critical. Exploitation detected .
The MS15-010 update fixes six different types of vulnerabilities in kernel-mode drivers (Windows 2003 Server - 8.1 / RT 8.1).

Vulnerability CVE-2015-0059 is very dangerous because it allows attackers to remotely execute code in kernel mode. For this purpose, a specially formed font file can be placed on a resource on the network. The exploitation of such a vulnerability allows you to execute shellcode from a font file directly in kernel mode ( user mode restrictions bypass ). Critical. Exploitation Less Likely .
The MS15-011 update fixes one CVE-2015-0008 vulnerability of the Remoe Code Execution type in the Group Policy mechanism. Using a vulnerability, an attacker can remotely execute code in a vulnerable system by luring a user to a malicious website on a network that is under the control of an attacker. Critical. Exploitation More Likely .
Update MS15-012 fixes three vulnerabilities in all supported versions of Office 2007-2010-2013. Vulnerabilities in Word & Excel allow attackers to remotely execute their code through a specially crafted Office document. To exploit a vulnerability, such a document can be sent to the victim in an email attachment. Important. Exploitation More Likely .
The MS15-013 update fixes one Security Feature Bypass (SFB) CVE-2014-6362 (use-after-free) vulnerability in all supported versions of Office. The vulnerability allows attackers to bypass ASLR (ASLR bypass) and develop more stable exploits for remote code execution via Office or IE. For the latest version of Office 2013, Otkloadr_msosec.dll (x64), Msosec.dll, Msvcr71.dll, Otkloadr.dll are subject to upgrade. Important. Exploitation More Likely .
The MS15-014 update fixes one SFE-type CVE-2015-0009 vulnerability in the Group Policy component (Windows 2003 Server - 8.1 / RT 8.1). Using the Man-in-the-Middle attack mechanism, an attacker could compromise a domain controller. Important. Exploitation Less Likely .
The MS15-015 update fixes one CVE-2015-0062 type Elevation of Privilege vulnerability in the Windows kernel (ntoskrnl.exe & hal.dll). An attacker can increase his privileges in the system due to a flaw in the process creation function (WIndows 7 - Windows 8.1 / RT 8.1). Important. Exploitation Less Likely .
Update MS15-016 fixes one Information Disclosure VEVE-2015-0061 vulnerability in the component for processing graphic TIFF files in Windows 2003 Server - 8.1 / RT 8.1. The attacker may unauthorized access to the information of the user (client) when placed on a web resource in a specially formed TIFF file. Important. Exploitation Less Likely .
Update MS15-017 fixes one vulnerability CVE-2015-0012 of type Elevation of Privilege in the Virtual Machine Manager (VMM) component for System Center Virtual Machine Manager. Using a vulnerability, an attacker can elevate his privileges in the system to the SYSTEM level. Important. Exploitation Less Likely .
0 - Exploitation Detected
Vulnerability is exploited in-the-wild. That is, it was established that attackers use an exploit for this vulnerability to successfully attack users. Highest hazard index.
1 - Exploitation More Likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploitation Less Likely
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).

be secure.
Source: https://habr.com/ru/post/250315/
All Articles