Study: Interception of mobile Internet traffic through GTP and GRX

Most subscribers believe that working through a cellular network is fairly safe, because a major telecom operator probably took care of protection. Alas, in practice in the mobile Internet there are many loopholes that provide ample opportunities for intruders.
The researchers at Positive Technologies have discovered vulnerabilities in the infrastructure of mobile networks, which allow intercepting GPRS traffic in the clear, replacing data, blocking access to the Internet, and determining the subscriber’s location. Not only mobile phones are at risk, but also specialized devices connected to 2G / 3G / 4G networks using modems: ATMs and payment terminals, remote control systems for transport and industrial equipment, telemetry and monitoring, etc.
')
Cellular operators, as a rule, encrypt GPRS traffic between the mobile terminal (smartphone, modem) and the subscriber service center (SGSN) with GEA-1/2/3 algorithms, which complicates the interception and decryption of information. To circumvent this limitation, an attacker can penetrate into the operator’s backbone where data is not protected by authentication mechanisms. The Achilles heel is the routing nodes (or gateway nodes), which are called GGSN. They are easy to detect, in particular, using the search engine Shodan. Problem nodes have open GTP ports, which allows an attacker to establish a connection and then encapsulate GTP control packets into the tunnel created. With proper selection of parameters, GGSN will perceive them as packets from legitimate devices of the operator’s network.
The GTP protocol described above should not be “visible” from the Internet in any way. But in practice this is not the case: there are more than 207,000 devices on the Internet with open GTP ports around the globe. More than half a thousand of them are components of the cellular network and respond to a request to establish a connection.

Another possibility for attacks is related to the fact that GTP is far from the only control protocol on the found nodes. Telnet, FTP, SSH, Web, etc. are also found. Using vulnerabilities in these interfaces (for example, standard passwords), an intruder can connect to a mobile operator's site.
Experimental site search Shodan issues several vulnerable devices, including open Telnet and a disabled password. It is enough to connect to this device and make the necessary settings in it in order to be inside the operator's network in the Central African Republic.

At the same time, anyone who accessed the gateway node of any operator automatically gets access to the GRX network, which connects all cellular operators and is used to provide Internet access to subscribers in roaming. Taking advantage of a single error in the configuration on one device, an attacker gets the opportunity to conduct various attacks on subscribers of any operator in the world.
Among the many options for using a compromised border node, the following should be noted: disconnecting subscribers from the Internet or blocking their access to it; Internet connection under the guise of another subscriber and at another's expense; intercept victim traffic and phishing. An attacker can also determine the subscriber ID (IMSI) and monitor the location of the subscriber around the world until he changes the SIM card.
We describe some of the threats in more detail.
Internet at someone else's expense
Purpose: exhaustion of the subscriber's account, use of the connection for illegal purposes.
Attack Vector: An attacker acts through a GRX network or from an operator’s network.
The attack consists in sending “Create PDP context request” packets from the IMSI of a previously known subscriber, thus connecting to the network with its credentials. Unsuspecting subscriber will receive huge bills.
A non-existent subscriber connection with IMSI is possible, since subscriber authorization occurs at the stage of connecting to SGSN, and already “tested” connections reach GGSN. Since the SGSN is compromised in this case, no verification has been carried out.
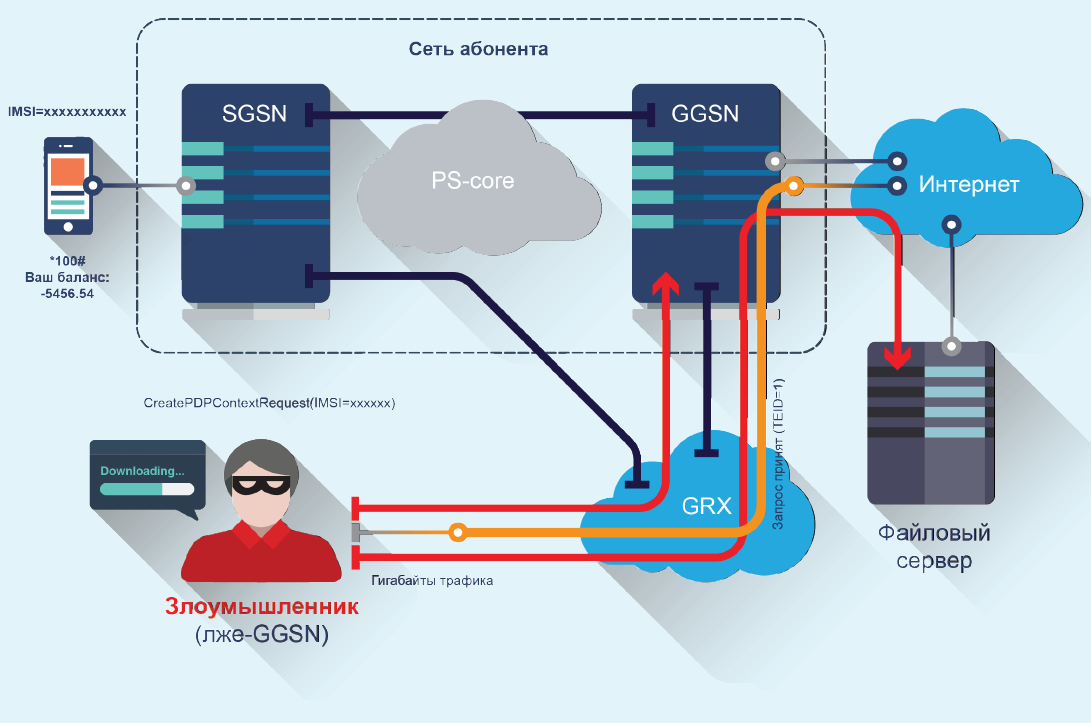
Result: Internet connection under the guise of a legitimate subscriber.
Interception of data
Purpose: eavesdropping on victim traffic, phishing.
Attack Vector: An attacker acts through a GRX network or from an operator’s network.
An attacker can intercept the data transmitted between the subscriber device and the Internet by sending an “Update PDP Context Request” message to the serving SGSN and GGSN with altered GSN addresses. This attack is an analogue of the ARP Spoofing attack at the GTP protocol level.

Result: eavesdropping or changing the victim’s traffic, disclosing confidential information.
DNS tunneling
Objective: to get non-chargeable access to the Internet from the subscriber’s mobile station.
Attack vector: the attacker is a subscriber of a cellular network, acting through a mobile phone.
The long-known attack, rooted in dial-up times, lost its meaning when a cheap and fast dedicated Internet appeared. However, in mobile networks it is used, for example, in roaming, when prices for mobile Internet are unreasonably high, and data transfer speed is not so important (for example, for checking mail).
The essence of the attack is that some operators do not charge for DNS-traffic, usually in order to redirect the subscriber to the operator’s page to replenish the account. This can be used - by sending specialized requests to the DNS-server; it also requires a specialized site on the Internet through which access will be made.

The result: non-tariffable access to the Internet at the expense of the cellular operator.
DNS spoofing on GGSN
Purpose: eavesdropping on victim traffic, phishing.
Attack vector: The attacker operates through the Internet.
In the case of gaining access to the GGSN (which, as we have already noted, it is quite possible), you can replace the DNS address with your own one, redirect all subscriber traffic through your site and thus “eavesdropping” all mobile traffic.

Result: eavesdropping or replacing the traffic of all subscribers, collecting sensitive data, phishing
How to protect
Some such attacks would not have been possible if the equipment was properly configured. But the results of the Positive Technologies study suggest that incorrect configuration is not uncommon in the world of telecommunications companies. Often, device manufacturers leave some services enabled, which should be disabled on this equipment, which gives violators additional features. Due to the large number of nodes, it is recommended to automate such control using specialized tools, such as MaxPatrol.

In general, the security measures required to protect against such attacks include the correct configuration of the equipment, the use of firewalls at the GRX network’s borders and the Internet, the use of 3GPP TS 33.210 recommendations for configuring security inside the PS-Core network, perimeter security monitoring, and the development of secure configuration standards equipment and periodic monitoring of compliance with these standards.
A number of specialists are pinning their hopes on new communication standards, which include new security technologies. However, despite the emergence of such standards (3G, 4G), completely abandon the networks of the old generation (2G) will not succeed. The reasons for this are the features of the implementation of mobile networks, in particular the fact that 2G base stations have better coverage, as well as the fact that 3G networks also work on their infrastructure. The LTE standard still uses the GTP protocol, and therefore the necessary protection measures will be relevant in the foreseeable future.
The results of this study were obtained by experts from Positive Technologies in 2013 and 2014 in the course of consulting work on the security analysis of several large mobile operators. The full report “Vulnerabilities of Mobile Internet (GPRS)” can be downloaded from our website: www.ptsecurity.ru/download/GPRS%20security.pdf
PS February 19 at 14.00 one of the authors of the study, Pavel Novikov, will be able to tell you more about these problems during a free webinar. Registration for the webinar will begin on February 12 at: www.ptsecurity.ru/lab/webinars/#40018 .
Source: https://habr.com/ru/post/250111/
All Articles