XSS vulnerability in Mobli
Most recently, I had to upload a video to Mobli, but since after the last incident , I had a habit of checking sites on XSS, I decided to check out Mobli.
')
I decided to start with the banal
I put it in the name of my post and, you won’t believe it, it worked.
Moreover, it worked in the Desktop version of the application through which I downloaded the photo.
Honestly, I did not expect this.

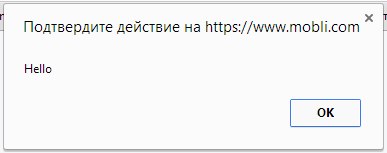
Here is the same post , only in the browser

The same situation with comments, i.e. You can insert any JS script in the comments of the photo and it will work. Of course, there is a limit of 150 characters, but it can be easily circumvented by connecting third-party JS, but you need to take into account that they have https and they do not connect js scripts from domains with http: //
This, too, can be easily circumvented, you just need to find Online proxy with https connection, but it works until the link from the proxy dies and the third-party script is not connected to the Desktop version of the application.
PS I wrote in support of Mobli, tried to write via LinkedIn, but it seems they don’t care.
PPS In fact, it is even embarrassing for me to call it a vulnerability, because, as it seems to me, everyone who starts developing a project takes care of filtering data.
UPD: Mobli fixed the vulnerability.
Mobli is a social network for sharing photos and videos. Approximate number of users 22 million.

')
I decided to start with the banal
<script>alert('Hello');</script> I put it in the name of my post and, you won’t believe it, it worked.
Moreover, it worked in the Desktop version of the application through which I downloaded the photo.
Honestly, I did not expect this.

Here is the same post , only in the browser

The same situation with comments, i.e. You can insert any JS script in the comments of the photo and it will work. Of course, there is a limit of 150 characters, but it can be easily circumvented by connecting third-party JS, but you need to take into account that they have https and they do not connect js scripts from domains with http: //
This, too, can be easily circumvented, you just need to find Online proxy with https connection, but it works until the link from the proxy dies and the third-party script is not connected to the Desktop version of the application.
PS I wrote in support of Mobli, tried to write via LinkedIn, but it seems they don’t care.
PPS In fact, it is even embarrassing for me to call it a vulnerability, because, as it seems to me, everyone who starts developing a project takes care of filtering data.
UPD: Mobli fixed the vulnerability.
Source: https://habr.com/ru/post/249891/
All Articles