We configure authorization in IIS according to certificates using OneToOne
Good day to all. It just so happened that at work it was necessary to set up a server with IIS, and not just to set up, but hang up authorization for different services using only a specific certificate service. This problem can be solved using several generation centers, but we will not complicate everything and proceed to setting up the “One-way” of our IIS.
The generation of the necessary keys is described in great detail on the Internet (the article on Habré) and should not cause any special problems, therefore I will omit this part.
Getting down to business:
1) Install IIS and necessary components. Be sure to check "Authentication with IIS client certificate mapping".
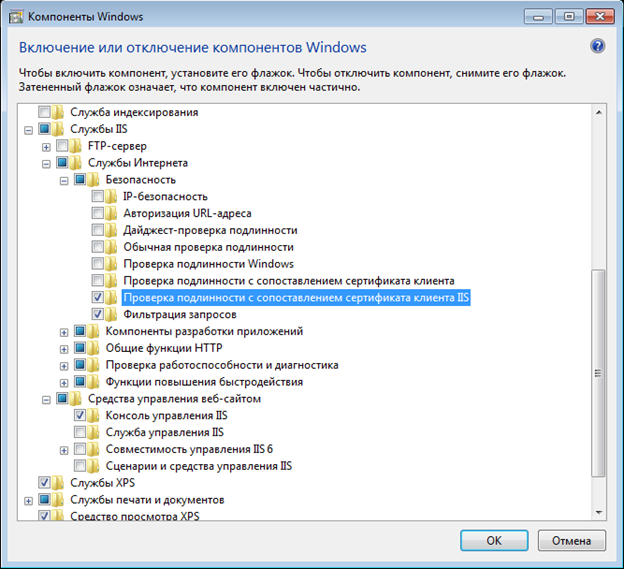
')
2) To bind, we need a client certificate encoded in base64, it is very easy to export from the certificate (certmgr.msc) "Certificates" or from "Internet Options".
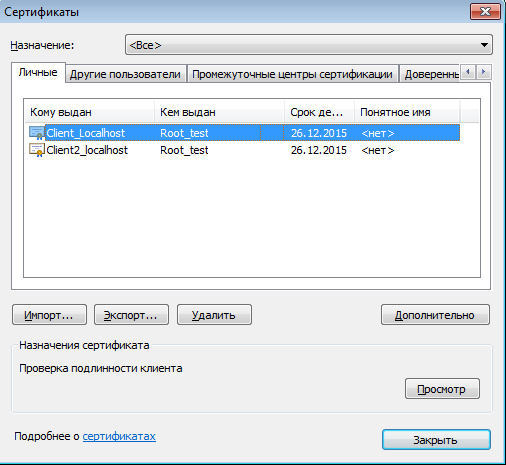
3) The received certificate is opened in a text editor and we stand in one line, after deleting the lines "BEGIN CERTIFICATE" and "END CERTIFICATE".
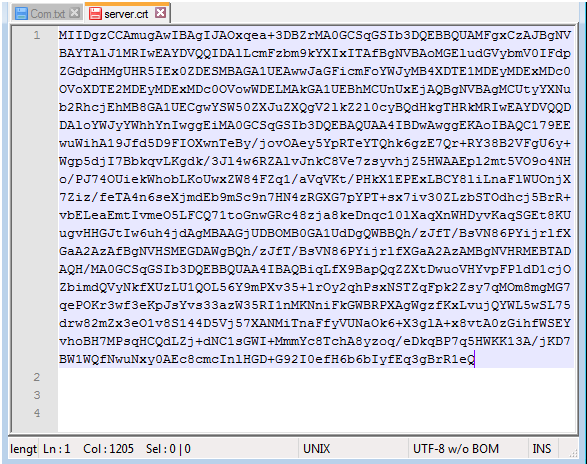
With the preparation finished go to the server.
4) Run the toolbar (inetmgr) "IIS Manager", and install the server certificate. In my case, the CN certificate is Localhost.

5) After that we can bind this certificate to services. Go to the bindings and select Https and specify the desired port and certificate.
6) In the SSL settings, check “Require SSL” and client certificate “require”.
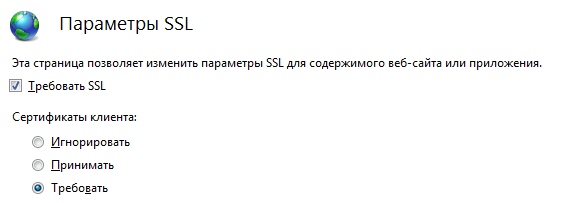
7) Now any certificate issued by our CA is suitable for authorization, but the purpose of this article is to show the next step when clients with certificates need to be divided. Go to the "Configuration Editor" at: "system.webServer / security / authentication / iisClientCertificateMappingAuthentication".
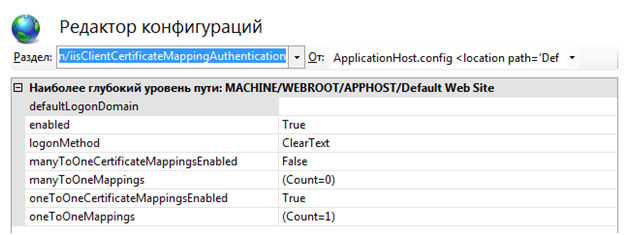
8) Here you have to make a choice, or we let on specific certificates or a specific field in the certificate (for example, a unique OID).
9) Consider the "oneToOneCertificateMappingsEnabled" parameter. By setting its value to “True” we will be able to bind a specific certificate to a user.

10) The certificate received on the second paragraph is inserted into the “certificate” field. The “userName” and “password” fields are filled with the account that you previously created.
11) Now, upon presentation of the registered client certificate, we will get access with the rights of the specified account. However, all other certificates will continue to work quietly and get anonymous access, to avoid this it is necessary in iis to disable anonymous authentication.

At this stage, authorization should take place only on the specified certificate.
Code for appcmd:
The generation of the necessary keys is described in great detail on the Internet (the article on Habré) and should not cause any special problems, therefore I will omit this part.
Getting down to business:
1) Install IIS and necessary components. Be sure to check "Authentication with IIS client certificate mapping".

')
2) To bind, we need a client certificate encoded in base64, it is very easy to export from the certificate (certmgr.msc) "Certificates" or from "Internet Options".

3) The received certificate is opened in a text editor and we stand in one line, after deleting the lines "BEGIN CERTIFICATE" and "END CERTIFICATE".

With the preparation finished go to the server.
4) Run the toolbar (inetmgr) "IIS Manager", and install the server certificate. In my case, the CN certificate is Localhost.

5) After that we can bind this certificate to services. Go to the bindings and select Https and specify the desired port and certificate.
6) In the SSL settings, check “Require SSL” and client certificate “require”.

7) Now any certificate issued by our CA is suitable for authorization, but the purpose of this article is to show the next step when clients with certificates need to be divided. Go to the "Configuration Editor" at: "system.webServer / security / authentication / iisClientCertificateMappingAuthentication".

8) Here you have to make a choice, or we let on specific certificates or a specific field in the certificate (for example, a unique OID).
9) Consider the "oneToOneCertificateMappingsEnabled" parameter. By setting its value to “True” we will be able to bind a specific certificate to a user.

10) The certificate received on the second paragraph is inserted into the “certificate” field. The “userName” and “password” fields are filled with the account that you previously created.
11) Now, upon presentation of the registered client certificate, we will get access with the rights of the specified account. However, all other certificates will continue to work quietly and get anonymous access, to avoid this it is necessary in iis to disable anonymous authentication.

At this stage, authorization should take place only on the specified certificate.
Code for appcmd:
appcmd.exe set config "Default Web Site" -section:system.webServer/security/authentication/iisClientCertificateMappingAuthentication /enabled:"True" /oneToOneCertificateMappingsEnabled:"True" /commit:apphost appcmd.exe set config "Default Web Site" -section:system.webServer/security/authentication/iisClientCertificateMappingAuthentication /+"oneToOneMappings.[userName='22',password='22',certificate=' base64']" /commit:apphost appcmd.exe set config "Default Web Site" -section:system.webServer/security/access /sslFlags:"Ssl, SslNegotiateCert, SslRequireCert" /commit:apphost Source: https://habr.com/ru/post/249503/
All Articles