Attack "Man In The Middle" (MITM) in Wi-Fi network
Many have already heard about such an attack as a “man in the middle” , or, in a different way, the MiTM attack . However, the theory is dead without practice. Therefore, in the article I would like to talk about how I implemented this attack in the wireless network. It turned out, however, primitive, but oh well.
There is a regular router that distributes the Internet to its customers, forming a wireless Wi-Fi network.
I play the role of an attacker who, like everyone, is a regular client with a regular PC. On my machine, the operating system is Windows 7. I also have a network sniffer (network traffic analyzer) WireShark (shark) .
')
Additionally, the method I propose makes sense if it is possible to connect to the router’s webmord, or alternatively if you can force the router to temporarily disconnect, fail and reboot (see the DDos attack on the router).
So, my goal: Organize a "wiretapping" of traffic from clients on the network. For this you need to "stand in the middle."
Tasks are reduced to four steps:
1. Preparation of the twin of the present access point.
2. Allowing Internet access to the created wireless network interface.
3. Restarting the router as an administrator, or a DDOS attack on the router.
4. At the moment of sagging of the present router, activate the double.
First step. It is necessary to prepare an access point. To do this, we use the netsh program built into Windows.
In my case, the SSID of this Rostelecom_16 access point and, since I am a network client, I know the password to this access point. Create an access point with the same name and password:
netsh wlan set hosted network mode = allow ssid = "Rostelecom_16" key = "password of this TD" keyUsage = persistent
A new wireless interface will appear in the network connections.
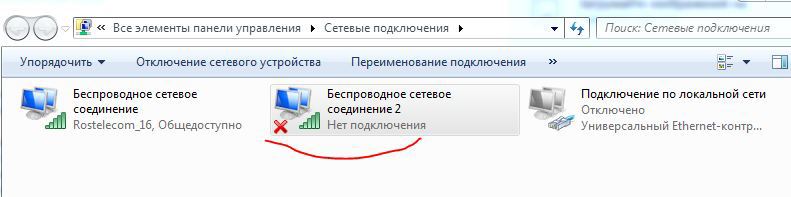
Do not rush to run this connection!
Note: if nothing appears in the network connections, restarting the Wi-Fi adapter will help.
The second step. We make the Internet from Rostelecom_16 common for the connection created (but not yet launched!):

The third step. As I have already noted, in my case there is the possibility of administering the router. By the way, it is no secret that passwords and default settings are one of the most common vulnerabilities. For routers by default, login and pass: admin are most often set.
In the settings of the router there is always a "reset" button. We will use it to temporarily reset all customers.
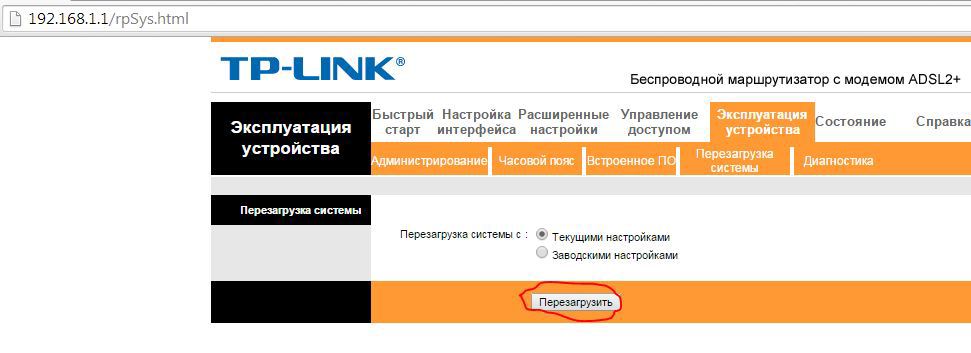
Fourth step. When the reset begins (at this very moment!), You need to activate the twin access point.
Command: netsh wlan start hostednetwork
To make sure that “you are in the middle” , we look at our customers with the command: netsh wlan show hostednetwork
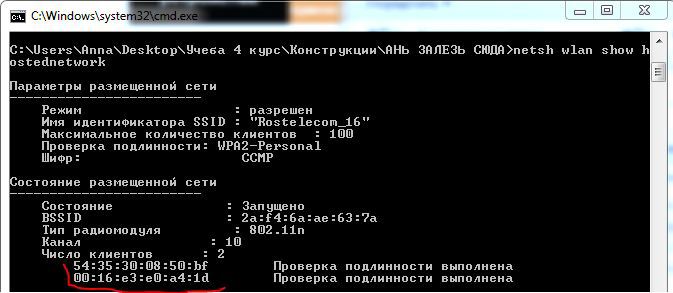
Everything! What happened? It is not difficult to guess that we took advantage of the moment of downtime and made the substitution of the real server, by moving the real server to the background. During the reset (reboot) of the router, it disappears from the field of view, so at the beginning of the reset all clients unlinked from the network, but when they found the same SSID (our twin), they immediately picked up, it seemed, back. But in fact, the server is a double, which also distributes the Internet, so regular users will not even notice this substitution, but what can we say about regular users when wireless devices do not notice the substitution. For me personally, this is strange.
Finally, in order to finally achieve the goal, we launch the so-called shark program WireShark and listen to the traffic from customers.
Good luck!
Source network
There is a regular router that distributes the Internet to its customers, forming a wireless Wi-Fi network.
I play the role of an attacker who, like everyone, is a regular client with a regular PC. On my machine, the operating system is Windows 7. I also have a network sniffer (network traffic analyzer) WireShark (shark) .
')
Additionally, the method I propose makes sense if it is possible to connect to the router’s webmord, or alternatively if you can force the router to temporarily disconnect, fail and reboot (see the DDos attack on the router).
So, my goal: Organize a "wiretapping" of traffic from clients on the network. For this you need to "stand in the middle."
Tasks are reduced to four steps:
1. Preparation of the twin of the present access point.
2. Allowing Internet access to the created wireless network interface.
3. Restarting the router as an administrator, or a DDOS attack on the router.
4. At the moment of sagging of the present router, activate the double.
First step. It is necessary to prepare an access point. To do this, we use the netsh program built into Windows.
In my case, the SSID of this Rostelecom_16 access point and, since I am a network client, I know the password to this access point. Create an access point with the same name and password:
netsh wlan set hosted network mode = allow ssid = "Rostelecom_16" key = "password of this TD" keyUsage = persistent
A new wireless interface will appear in the network connections.
Do not rush to run this connection!
Note: if nothing appears in the network connections, restarting the Wi-Fi adapter will help.
The second step. We make the Internet from Rostelecom_16 common for the connection created (but not yet launched!):
The third step. As I have already noted, in my case there is the possibility of administering the router. By the way, it is no secret that passwords and default settings are one of the most common vulnerabilities. For routers by default, login and pass: admin are most often set.
In the settings of the router there is always a "reset" button. We will use it to temporarily reset all customers.
Fourth step. When the reset begins (at this very moment!), You need to activate the twin access point.
Command: netsh wlan start hostednetwork
To make sure that “you are in the middle” , we look at our customers with the command: netsh wlan show hostednetwork
Everything! What happened? It is not difficult to guess that we took advantage of the moment of downtime and made the substitution of the real server, by moving the real server to the background. During the reset (reboot) of the router, it disappears from the field of view, so at the beginning of the reset all clients unlinked from the network, but when they found the same SSID (our twin), they immediately picked up, it seemed, back. But in fact, the server is a double, which also distributes the Internet, so regular users will not even notice this substitution, but what can we say about regular users when wireless devices do not notice the substitution. For me personally, this is strange.
Finally, in order to finally achieve the goal, we launch the so-called shark program WireShark and listen to the traffic from customers.
Good luck!
Source: https://habr.com/ru/post/249181/
All Articles