GHOST (dot) WEB: First Blood
Despite the skepticism of the Metasploit community about the prospects of mass exploitation of the vulnerability CVE-2015-0235 , the first victims appeared. Researchers at Positive Technologies have reported a “combat” exploit for this vulnerability in the popular phpBB forum. Wordpress and a number of other popular applications are also vulnerable.
Using a vulnerability in the gethostbyname function allows an attacker to gain complete control over the operating system of the vulnerable server.
')
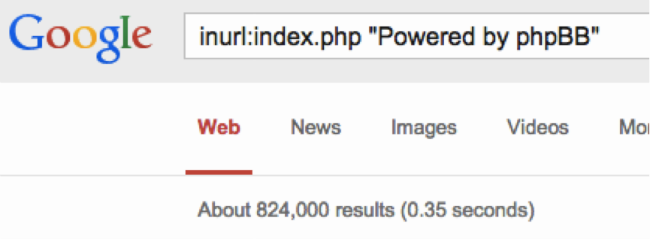
The phpBB system is one of the popular means of adding forum functions to websites. A quick Google search shows that this system is installed on more than 800,000 sites.
Naturally, not all of them are vulnerable to attacks related to the GHOST vulnerability, since this requires a combination of several factors. However, rich host identification mechanisms allow you to create a specialized exploit through http and achieve almost 100% success of the attack.
Users of Positive Technologies Application Firewall , as in the case of ShellShock or WordPress , may not be in a hurry to update their operating system applications, but to do so in a planned manner. PT AF self-learning mechanisms reliably identify and block the attack. Of course, if the lock is on.


You will not pass GHOST! I'm PT AF. Return to TCP RST. YOU WILL NOT PASS!
Naturally, this information was passed on to the developers of phpBB and a number of other popular applications. But the problem is not phpBB. An urgent need to update your system .

Using a vulnerability in the gethostbyname function allows an attacker to gain complete control over the operating system of the vulnerable server.
')
The phpBB system is one of the popular means of adding forum functions to websites. A quick Google search shows that this system is installed on more than 800,000 sites.
Naturally, not all of them are vulnerable to attacks related to the GHOST vulnerability, since this requires a combination of several factors. However, rich host identification mechanisms allow you to create a specialized exploit through http and achieve almost 100% success of the attack.
Some advertising
Users of Positive Technologies Application Firewall , as in the case of ShellShock or WordPress , may not be in a hurry to update their operating system applications, but to do so in a planned manner. PT AF self-learning mechanisms reliably identify and block the attack. Of course, if the lock is on.


You will not pass GHOST! I'm PT AF. Return to TCP RST. YOU WILL NOT PASS!
Naturally, this information was passed on to the developers of phpBB and a number of other popular applications. But the problem is not phpBB. An urgent need to update your system .
Source: https://habr.com/ru/post/249137/
All Articles