CTB-Locker - a new modification of the FileCoder cryptographer
We have already written several times about various families of encryption Trojans. We are talking about modifications of the FileCoder malware family, as well as the Win32 / Virlock extortionist . A few days ago, our anti-virus laboratory began receiving messages about a malicious campaign targeting users in Latin America and Eastern Europe. Phishing e-mails contained information about the “arrived fax”. Attachments of such messages contained malware that specializes in encrypting user files and requesting a ransom for decryption in Bitcoins.

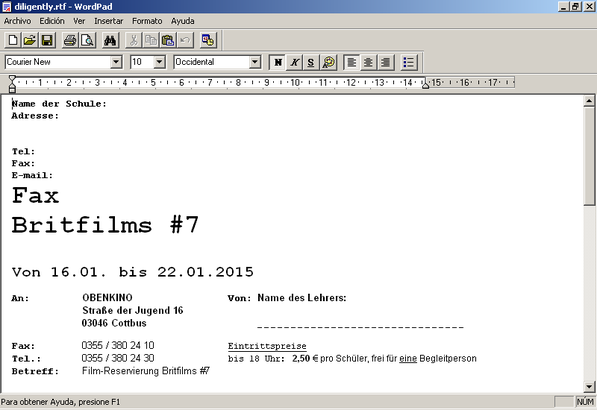
An example of such a malicious message is shown below in the screenshot.

')
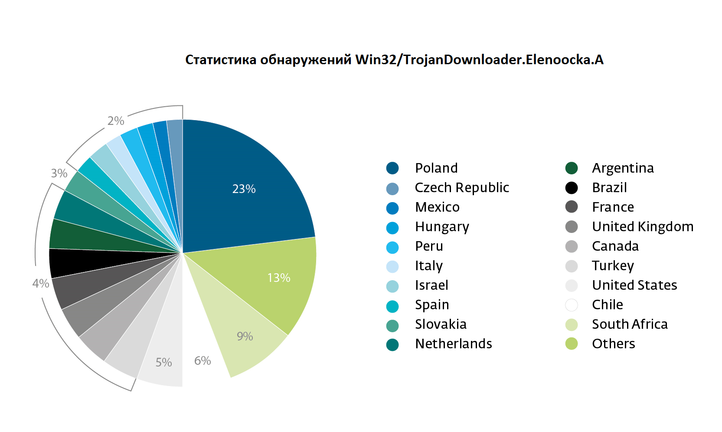
In this post, we will look at a malicious campaign to distribute this malicious program, which has been distributed in Poland, the Czech Republic, Mexico and many other countries.
As we mentioned above, the main CTB-Locker distribution vector is a phishing email message. A malicious executable file that is attached to an email is detected by ESET AV products as Win32 / TrojanDownloader.Elenoocka.A . This bootloader (or downloader) downloads the FileCoder modification (CTB-Locker) mentioned above to the user's computer. This modification is detected as Win32 / FileCoder.DA . After running this malware file on disk are encrypted.
The CTB ‑ locker itself is similar to another well-known cryptographer called CryptoLocker . The difference between them is the use of different file encryption algorithms. The result of the CTB ‑ locker activity is similar to CryptoLocker or TorrentLocker , that is, it leads to encryption of files with the extensions mp4, .pem, .jpg, .doc, .cer, .db. After the file encryption operation is completed, the malware displays a warning message to the user. For this purpose, CTB ‑ locker can personalize the user's desktop, i.e., change the wallpaper there for the following.
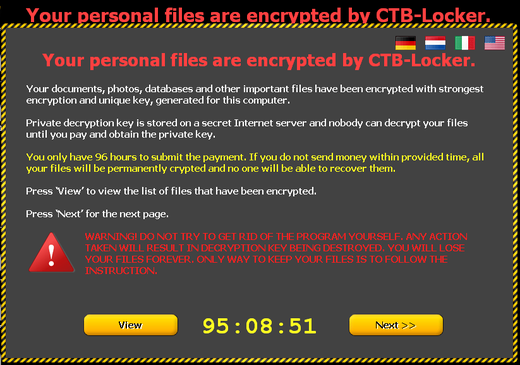
Extortionist supports text display in various languages, including, German, Dutch, Italian, English. There is no Spanish in the list of supported languages, although we have seen infections by this malicious program in those countries for which this language is the main one.
CTB-Locker is distinguished by the fact that attackers use a special method to convince the user to pay the ransom. They show him what will happen after his payment, that is, they convince the user that they will not deceive him and decrypt the files.
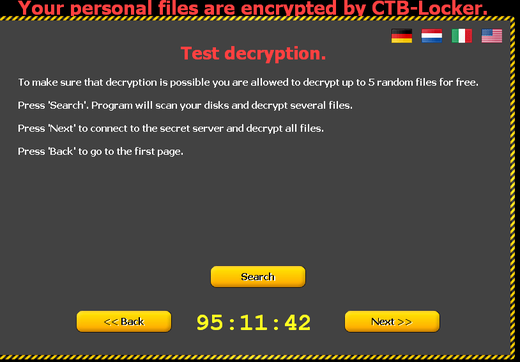
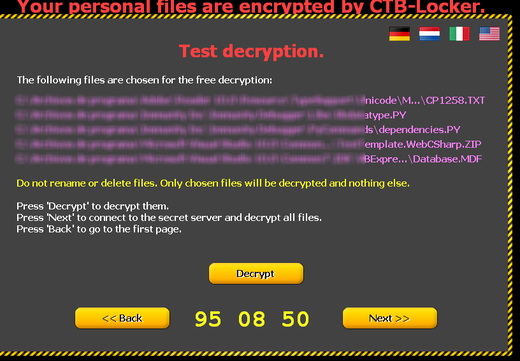
After that, the user will be shown how he can decrypt files and to what account he will need to transfer Bitcoins for this.
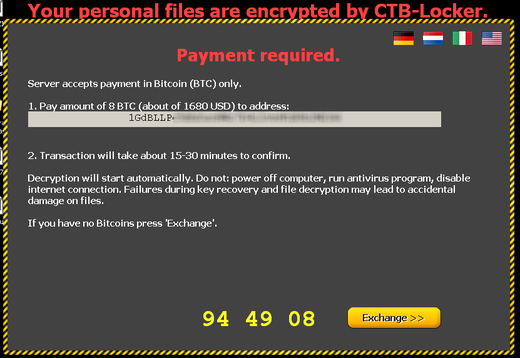
As can be seen above in the screenshot, CTB-Locker can demonstrate the exchange rate of bitcoins based on the currency that corresponds to the location of the locked computer. At the time of taking the screenshot, eight bitcoins were $ 1680.
From a technical point of view, the ransomware downloader himself, who shows up as Win32 / TrojanDownloader.Elenoocka.A , is a rather small in terms of size and simple from a technical point of view malware. We have observed the use of this downloader by attackers in other malicious campaigns. In one of these campaigns, phishing emails were used, which included malicious files with the names invoice_% YEAR_% MONTH_% DAY-1% HOUR_% MIN.scr (eg invoice_2015_01_20-15_33 .scr). To disguise its launch on the system, the executable file contains a fake Word document in its resources, which will be shown to the user in the background of the malicious file.
CTB-Locker malware is a type of extortionist, after whose activity it is impossible to decrypt files without a key received from intruders. As we have repeatedly stressed, the use of backup is the main method that can be used to restore data after the activities of such malware, in addition to the timely update of the anti-virus database is also a necessary measure to prevent infection.

An example of such a malicious message is shown below in the screenshot.

')
In this post, we will look at a malicious campaign to distribute this malicious program, which has been distributed in Poland, the Czech Republic, Mexico and many other countries.

As we mentioned above, the main CTB-Locker distribution vector is a phishing email message. A malicious executable file that is attached to an email is detected by ESET AV products as Win32 / TrojanDownloader.Elenoocka.A . This bootloader (or downloader) downloads the FileCoder modification (CTB-Locker) mentioned above to the user's computer. This modification is detected as Win32 / FileCoder.DA . After running this malware file on disk are encrypted.

The CTB ‑ locker itself is similar to another well-known cryptographer called CryptoLocker . The difference between them is the use of different file encryption algorithms. The result of the CTB ‑ locker activity is similar to CryptoLocker or TorrentLocker , that is, it leads to encryption of files with the extensions mp4, .pem, .jpg, .doc, .cer, .db. After the file encryption operation is completed, the malware displays a warning message to the user. For this purpose, CTB ‑ locker can personalize the user's desktop, i.e., change the wallpaper there for the following.

Extortionist supports text display in various languages, including, German, Dutch, Italian, English. There is no Spanish in the list of supported languages, although we have seen infections by this malicious program in those countries for which this language is the main one.
CTB-Locker is distinguished by the fact that attackers use a special method to convince the user to pay the ransom. They show him what will happen after his payment, that is, they convince the user that they will not deceive him and decrypt the files.


After that, the user will be shown how he can decrypt files and to what account he will need to transfer Bitcoins for this.

As can be seen above in the screenshot, CTB-Locker can demonstrate the exchange rate of bitcoins based on the currency that corresponds to the location of the locked computer. At the time of taking the screenshot, eight bitcoins were $ 1680.
From a technical point of view, the ransomware downloader himself, who shows up as Win32 / TrojanDownloader.Elenoocka.A , is a rather small in terms of size and simple from a technical point of view malware. We have observed the use of this downloader by attackers in other malicious campaigns. In one of these campaigns, phishing emails were used, which included malicious files with the names invoice_% YEAR_% MONTH_% DAY-1% HOUR_% MIN.scr (eg invoice_2015_01_20-15_33 .scr). To disguise its launch on the system, the executable file contains a fake Word document in its resources, which will be shown to the user in the background of the malicious file.
CTB-Locker malware is a type of extortionist, after whose activity it is impossible to decrypt files without a key received from intruders. As we have repeatedly stressed, the use of backup is the main method that can be used to restore data after the activities of such malware, in addition to the timely update of the anti-virus database is also a necessary measure to prevent infection.
Source: https://habr.com/ru/post/248987/
All Articles