NSA Curious Look: What is the War of Internet Security (Part 2)?

The assumptions that intelligence agencies are ahead of us so much that it makes no sense to defend themselves against encryption are incorrect. As one document from the Snowden archive shows, the NSA did not succeed in deciphering a number of communication protocols, at least in 2012. The presentation for the conference held that year contained a list of encryption programs that the Americans failed to crack. In the process of decryption, the NSA cryptologists divided their goals into five levels according to the difficulty level of the attack and the result obtained, starting with “trivial” to “catastrophic”.
[ first part ]
')
Monitoring the path of moving a document on the Web is classified as a “trivial” goal. Recording a chat on Facebook is a “simple” task, while the difficulty level of decrypting emails sent through the Russian Internet service provider Mail.ru is considered as a task of “moderate complexity”. But all three of these levels of classification do not pose serious problems for the NSA.
Things get harder on the fourth level. According to the presentation, the NSA is experiencing "significant" problems in trying to decrypt messages sent via email providers that use enhanced encryption methods - for example, the Zoho service, or when monitoring users of the Tor network, which was designed for anonymous web search. . Tor, also known as The Onion Router, is free, open source software that allows users to access the Internet through a network of over 6,000 interconnected and donated computers. The software automatically encrypts data so that no computer on the network contains all the information about the user. Thus, it becomes very difficult for surveillance experts to track the whereabouts of a person visiting a particular website or to attack someone who uses Tor to search the Internet.
“Significant” problems for the NSA are also caused by Truecrypt , a program for encrypting files on a computer. Its developers stopped the development of the program in May last year, which caused suspicions about pressure on them by the state Agency. A protocol called Off-The-Record (OTR) for end-to-end instant messaging encryption also seems to cause considerable difficulties for the NSA. The code for both of these programs can be freely viewed, modified and distributed. Experts agree that intelligence agencies are much more difficult to manipulate open source software than many of the closed systems developed by companies such as Apple and Microsoft. Since everyone can view the code of such software, it is extremely difficult to implement a backdoor that would not be detected. The transcripts of intercepted OTR chats, provided to the Agency by its partners in Prism - a NSA data collection program from at least nine US Internet companies, such as Google, Facebook and Apple - show that in this case the efforts of the NSA did not succeed: a message encrypted using OTR cannot be decrypted. ” This means that the OTR protocol at least sometimes makes it possible to make communications inaccessible for viewing in the NSA.

For the Agency, the situation becomes “catastrophic” at the level of “five”: when, for example, the subject uses a combination of Tor, another “anonymization” service, the CSpace instant messaging system and the Internet Telephony System (VoIP) called ZRTP . Such a combination, as stated in the NSA document, leads to "an almost complete loss of the ability to track the location and communications of the selected object."
The ZRTP system, which is used to securely encrypt conversations and chats on mobile devices, is used in free open source programs such as RedPhone and Signal.
“It’s nice to know that the NSA considers encryption of communications through our services really opaque,” says RedPhone developer under the pseudonym Daring Sheep Marlin (Moxie Marlinspike).
"Die Hard" for Fort Meade
The letter "Z" in the name of ZRTP is a tribute to one of the system developers, Phil Zimmermann, who created the Pretty Good Privacy system, which remains the most widely used letter and document encryption program today. PGP was created more than 20 years ago, but, surprisingly, it is still too tough for the NSA. “This message encrypted with PGP cannot be decrypted” is in the NSA document, which fell into the hands of the Spiegel edition, about letters sent via Yahoo.
Phil Zimmermann wrote PGP in 1991. An activist of the termination of the American nuclear weapons program wanted to create an encryption system that would allow him to safely exchange information with other like-minded people. His system quickly became very popular among dissidents around the world. Given the widespread use of the program outside the United States, the US government in the 1990s began to prosecute Zimmermann, allegedly for violating the Arms Export Control Act. Prosecutors agreed that creating an encryption system of such complexity and distributing it outside the country is illegal. Zimmermann responded by publishing the source code of the system in the form of a book - it was a manifestation of freedom of speech, protected by the constitution.
PGP continues to be refined, and today there are many versions of the system available. The most widespread is GNU Privacy Guard (GnuPG), a program developed by German programmer Werner Koch. One of the documents shows that representatives of the Five Eyes Alliance sometimes use PGP themselves. It turns out that hackers who are obsessed with their own security, and the US authorities have much more in common than one could imagine. Initially, the Tor project was developed with the support of the US Naval Research Lab.
Today, as stated in one of the documents, the NSA and its allies are trying with all their might to destroy the system that the US military helped create. Tor “de-anonymization” is obviously one of the main priorities of the NSA, but the Agency has hardly succeeded in this area. One of the documents for 2011 even mentions an attempt to decrypt the results of using Tor by the Agency itself - as a test.
The Snowden documents should, to a certain extent, cause a feeling of relief from people who believed that nothing could stop the NSA in its inexhaustible desire to gather information. It seems that we still have secure communication channels. However, the document also shows how far intelligence agencies have gone in their work of preserving and deciphering our data.
Internet security is carried out at several levels - and the NSA, together with allies, are obviously capable of “using” (that is, “hacking”) - some of the most widely used of them on a scale unthinkable.
The security of virtual private networks is indeed “virtual”
One example is virtual private networks (VPN), which are often used by companies and institutes operating in several offices and locations. In theory, VPN creates a secure tunnel between two points on the web. All data, cryptographically protected, is sent to this tunnel. But when it comes to the security level of a VPN, the word “virtual” is best suited to describe it. This is because the NSA is working on a large-scale VPN use project for hacking a large number of connections, which allows the Agency to intercept information transmitted via VPNs - including, for example, the Greek government's VPN network. According to the document that fell into the hands of Spiegel, the NSA team responsible for working with Greek VPN communications consists of 12 people.
The NSA's goal was the SecurityKiss Irish VPN service. The following “digital fingerprint” for Xkeyscore, a powerful spyware program created by the agency, was, according to NSA reports, tested and used to extract service data:
fingerprint('encryption/securitykiss/x509') = $pkcs and ( ($tcp and from_port(443)) or ($udp and (from_port(123) or from_por (5000) or from_port(5353)) ) ) and (not (ip_subnet('10.0.0.0/8' or '172.16.0.0/12' or '192.168.0.0/16' )) ) and 'RSA Generated Server Certificate'c and 'Dublin1'c and 'GL CA'c;According to a NSA document dated 2009, the Agency processed 1,000 requests per hour from VPN connections. It was expected that this number would increase to 100,000 per hour by the end of 2011. The goal of the system was the complete processing of “at least 20%” of these requests, which means that the data received had to be decrypted and transmitted to the addressee. In other words, by the end of 2011, the NSA planned to continuously monitor up to 20,000 supposedly secure VPN connections per hour.
VPN connections can be built on the basis of various protocols. The most commonly used Point-to-Point Tunneling Protocol (PPTP) and Internet Protocol Security (IPsec) security protocols. These protocols do not pose any particular problems for NSA spies if they really want to break the connection. Experts have already called PPTP unsafe, but it continues to be used in many commercial systems. The authors of one of the NSA presentations bragged about a project called FOURSCORE, which stores information including encrypted metadata transmitted over PPTP protocols.
The NSA documents state that, using a large number of different programs, Agency services penetrated into many corporate networks. Among those who have been monitored are: the Russian airline Transaero, Royal Jordan Airlines, as well as a telecom provider from Moscow “World of Telematics”. Another achievement of this program is the establishment of monitoring the internal communications of diplomats and government officials of Afghanistan, Pakistan and Turkey.
IPsec is a protocol that, at first glance, creates more problems for spies. But the NSA has the resources to conduct multiple attacks on routers involved in the process of creating connections, to get the keys and decrypt rather than decrypt the transmitted information - a message from the NSA department called Tailored Access Operations (Special Access Operations) shows: “TAO I got access to the router through which the main banking traffic passes, ”one of the presentations says.
Nothing to do with security
Presumably secure systems that regular Internet users constantly rely on for financial transactions, paying for electronic purchases or accessing email accounts are even less secure than VPN. A man in the street can easily recognize these “secure” connections by looking at the address bar in the browser: with such a connection, the address will not begin with “http” - but with “https”. "S" in this case means "secure", "secure." The problem is that these protocols have nothing to do with security.
Such compounds of the NSA and its allies crack effortlessly - one million per day. According to the NSA document, the Agency planned to increase the volume of hacked https connections to 10 million per day by the end of 2012. Intelligence services are particularly interested in collecting user passwords. By the end of 2012, the system had to “monitor the status of at least 100 applications using encryption and working on the basis of entering a password” for each use case about 20,000 times a month.
For example, the British Government Communications Center collects information about encryption using the TLS and SSL protocols — these are https connections encryption protocols — in a database called the FLYING PIG. British spies create weekly reports on the current state of the system for cataloging the services that most often use SSL protocols, and keep the details of these connections. Services such as Facebook, Twitter, Hotmail, Yahoo and iCloud are notable for their particularly frequent use of such protocols, and the number of connections recorded weekly by the British service amounts to billions - and this is only for the 40 most popular sites.
Monitoring hockey sites
The Canadian Communications Security Center even monitors sites dedicated to the most popular national pastime: “We have tracked a significant increase in activity in chats on hockey discussion sites. This is probably due to the start of the play-off season, ”says one of the presentations.
The NSA also created a program through which, as it states, the SSH protocol can be decrypted. It is usually used by system administrators to remotely access employees' computers, mainly for use by Internet routers, business infrastructure systems, and other such services. The NSA combines data obtained in this way with other information to control access to important systems.
Weakening cryptographic standards
But how does the Five Eyes Alliance manage to crack all these standards and encryption systems? The short answer is: they use all available features.
One of them is a serious weakening of the cryptographic standards used to create such systems. Documents from the Spiegel edition indicate that NSA agents attend meetings of the Internet Engineering Task Force (IETF), which develops these standards, to gather information and, presumably, to influence the discussions held at meetings. “The new policy extension session can improve our ability to passively track two-way communications,” appears in the short description of the IETF meeting in San Diego in the NSA internal information system.
This process of weakening cryptographic standards has been going on for quite some time. A collection of classifiers, a document explaining how to classify certain types of secret information, marks "the fact that the NSA / Central Security Service conducts cryptographic modifications of commercial devices or security systems for later use" with the "Top Secret" label.

Collection of NSA classifiers: “Cryptographic modifications”
Cryptographic systems, thus weak enough or defective, are then processed using supercomputers. The NSA created a system called Longhaul - “the service of orchestrating through attacks and key recovery for Data Network Cipher traffic and Data Network Session Cipher”. In essence, Longhaul for the NSA is a source of searching for opportunities to decrypt various systems.
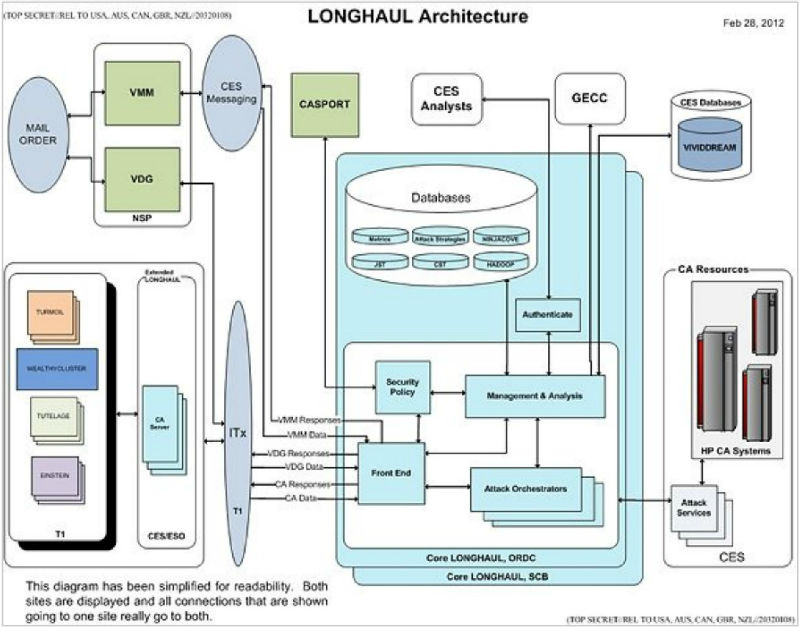
According to the NSA document, the system uses the power of the Tordella Supercomputer supercomputer in Fort Meade, Maryland, and the Oak Ridge data center in Oak Ridge, Tennessee. The service can transmit decrypted data to systems such as Turmoil — this is part of a secret network that the NSA has deployed around the world to intercept data. The code name for developments in this direction is Valientsurf. A similar program called Gallantwave is designed for "hacking tunnel protocols and session protocols."
In other cases, spies use their infrastructure to steal cryptographic keys from router configuration files. The repository called Discoroute contains "configuration data of routers obtained in an active and passive manner." Active collection involves hacking or otherwise penetrating computer systems; passive collecting means receiving data transmitted over the Internet through secret computers operated by the NSA.
An important part of the work of the Five Eyes Alliance to decipher is simply to collect huge amounts of data. For example, they collect so-called SSL handshake messages — information that computers exchange to establish an SSL connection. A combination of connection metadata and encryption protocol metadata can help you get keys, which in turn allow you to read or write the decrypted traffic.
Finally, if other methods do not help, the NSA and the allies rely on brute force methods: they organize a hacker attack on the target computer or router to obtain secret data - or intercept the computers themselves on the way to the place of delivery, reveal them and introduce bugs there - this process called "the difficulty of the actions of the enemy."
Serious security threat
For the NSA, decryption is a constant conflict of interest. The agency and its allies have their own secret encryption methods for internal use. But the NSA is also required to provide the US National Institute of Standards and Technology (NIST) with "guidelines for choosing reliable technologies" that "can be used in cost-effective systems to protect sensitive data." In other words, quality control of cryptographic systems is part of the work of the NSA. One of the encryption standards recommended by NIST is the Advanced Encryption Standard (AES). It is used in various systems, from encrypting the PIN of a bank card to encrypting the hard disk of a computer.
One of the documents from the NSA indicates that the Agency is actively looking for ways to hack a standard that itself recommends - this section is marked “Top Secret”: “Electronic codebooks such as the Advanced Encryption Standard are both widely distributed and well protected from crypto attack The NSA owns only a small amount of internal techniques for their hacking. The TUNDRA project is investigating a potentially new technique to determine its usefulness when analyzing electronic codebooks. ”

The fact that a huge number of cryptographic systems that flooded the Internet are deliberately weakened or cracked by the NSA and its allies represents a huge security threat to everyone who relies on the Internet - from users who expect security to the Network, to institutions and companies that work with cloud computing. Many of these “holes” can be used by anyone who learns about them - and not only the NSA.
This is well known in the intelligence directorate itself: according to the 2011 document, 832 employees of the Government Communications Center themselves became participants in the BULLRUN project, whose goal is a wide-scale attack on Internet security.
Two authors of the article, Jacob Appelbaum and Aaron Gibson, work on the Tor project. Appelbaum also works in the OTR project and is involved in the creation of other data encryption programs.
Source: https://habr.com/ru/post/248675/
All Articles