One ring to rule them all or TeddyID authentication
Recently, I was asked to express my opinion on the new service, which promises to solve all the problems of sclerotic users,
Terms of use
As a true paranoid and open source advocate, I start to get acquainted with such things with the user agreement. Skimming through the text and making sure that the company has traditionally never been responsible for anything, the look caught on three key points:
- Our company is Russian. Registered as Platform Matrix LLC. In principle, there is nothing special in this, but there are certain risks of trust. Access to resources and personal information may be somewhat “expanded” for an indefinite number of persons due to the nature of the administrative resource in our country.
The User is aware that information about himself that the User enters on the Matrix Company's websites or otherwise transfers the Matrix to the Company may become available to other Matrix Company Users and Internet users, may be copied and distributed by such users;
This item is frankly embarrassed. What is related to such information, why should it be available to whom it is not clear? Perhaps lawyers were reinsured.- The traditional paragraph about changing the rules at any time with an alert in the form of changes to the corresponding page on the site. That is, certain items may suddenly change.
In principle, nothing particularly critical, but trusting access to a third party, I want more transparency in the contract.
Key features and capabilities
We recall TRIZ and the concept of an ideal end result : the most effective solution to a problem is one that is achieved “by itself”, only at the expense of the resources already available.
What is the main problem for most regular users with authentication on different resources? The need to remember many different passwords or use the same one, reducing security. And I want to somehow everything worked.
The service just helps to solve this problem once and for all through the use of a mobile application. Instead of the traditional input of a username / password on the site, you get a request to match the images on the PC monitor and on the phone. One click and you are inside.

Actually, this is what I immediately checked by registering on the site. By the way, the registration system was extremely pleased. Minimum unnecessary movements by the user, no boring questionnaires. You install the application and scan the QR-code, after which the account is considered to be created. Subsequently, you can add additional information, verify the mailbox and so on. All this serves the purpose of increasing security.
')
For TeddyID integration, it is proposed to use an uncomplicated API . As a result, the user gets the opportunity to log into your account in one click.
Also, the creators of the service promise simple integration within CMS Bitrix and Wordpress in the form of plug-ins.
"Half-factor authentication"
If for some reason a full service integration is impossible, then TeddyID offers a kind of LastPass option. To add to the site, simply add the following script to the page code:
<script src="https://www.teddyid.com/js/teddypass.js" async></script> In this case, the TeddyID will work as a password manager. During login, the user will be prompted to save the password, and during registration, Teddy will generate for the user a complex unbreakable password. Passwords are stored in encrypted form, and the key for decrypting passwords is stored in the user's browser, and passwords are decrypted in the user's browser only when they are used. Thus, even Teddy never sees the user's password in decrypted form.
The main difference from the same encrypted storage in Firefox, Keepass, LastPass is that the user does not need to remember even the master password. Instead, he gets all the same system of comparing the identity of pictures on the phone and PC.
Comparison of two use cases:

Password Manager
This feature was especially liked. If it takes off, it can greatly press down competitors. In fact, you get the same classic password manager, but with the advantage of two-factor authentication. Their extension is installed in the browser, which provides a connection between the input form, service servers and your phone. Perhaps this is the most functional functionality at the moment, since it does not require any action by the webmasters and runs exclusively on the client side.
This functionality is paid, but the symbolic amount is only $ 0.99 for a lifetime license.
Browsers are supported:
- Chrome
- Firefox
- Internet Explorer
- Safari
- Opera (coming soon)
- Yandex Browser (coming soon)
Subjective feelings of use
The first impression of the system is a very high responsiveness. The application reacts almost instantly to an attempt to enter, the delay on the home channel is not more than half a second. We check the work in the absence of an Internet channel:
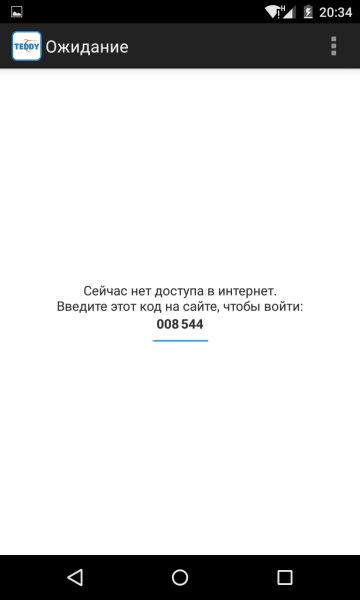
Here, the principle of operation is identical to the Google Authentificator application. The pin code is generated every 30 seconds based on a random grain, obtained during the initial registration of the application. Of the minuses - the numbers are small, and the screen area is wasted. Not very convenient, but it works. Synchronization of keys is ensured by the exact match of the time on the server and the device. For especially forgetful, it is possible to log in with a password.
Upon further study, I was somewhat disappointed with the extremely simplified manual. I do not overly welcome the current tendency to hide information from the user so that he does not accidentally overwork and be frightened. Find some intelligible documentation, wiki, examples of use, even the analysis of menu items in your personal account did not work. The project is young, but it seems to me that new users should immediately find answers to all their questions.
For example:
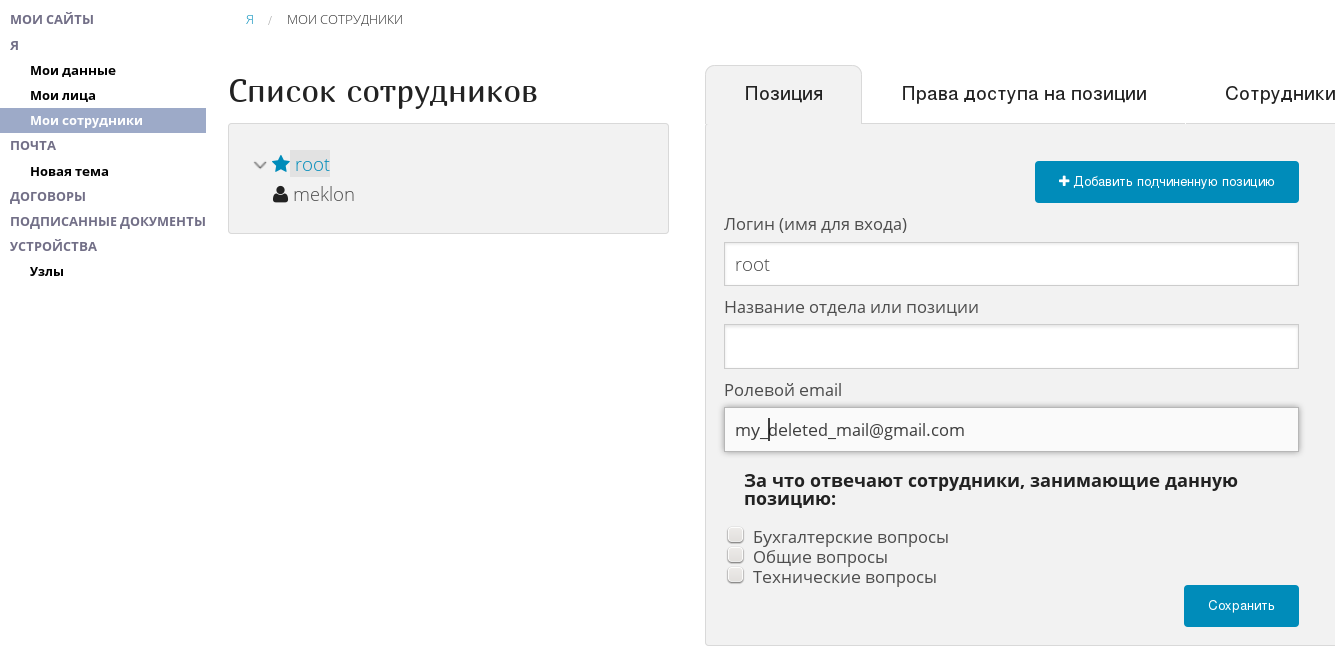
or
It clearly has advanced functionality designed to increase business security, EDS and other goodies. But why do I need this in the main section of my personal account as a regular user? Who are all these contractors and other entities? Answers, apparently, are hidden somewhere in non-obvious sections of the site.
Trust crisis

I think all of us remember the compromise of iCloud accounts, which received the ironic nickname The Fappening . Why did I remember this? You know, it is believed that the key keeper is the best way to lose all the keys at the same time.
When we trust all our keys and passwords to a third-party service, we want to be absolutely sure of its security. And, when even such monsters of the IT market as Apple allow punctures in ensuring data security, it will be very difficult to win the trust of new users. Yes, the average user is careless and
The target audience

In my opinion, the target audience of the service is still not very clear. The average user lives in a personal hell among Yandex-bars, Guard'ov, search panels and other garbage. And as the password uses his birthday. In order to want to use the convenience and security of two-factor authentication, you need to think about it for at least a second. But among such users, such “thoughtfulness” is almost not found. Most of them sincerely confess the slogan "I have nothing interesting, who needs me?" They also usually sincerely believe in an evil hacker who will personally hack his page at Odnoklassniki at night. As a result, such users join the ranks of bot-net nodes.
Another, smaller part of the network population is harsh and bearded. Red eyes gaze impassively at the logs flashing in the console ... Such users, as a rule, understand the basics of security on the network and rarely give care to someone else. It will not be easy to convince them that using the phone as a means of access is better than the encrypted KeePassX database synchronized through a lovingly configured owncloud.
At the same time, the direction of monetization towards services for business projects is clearly felt. As a result, it is not easy to understand the direction of the project in the near future.
Prevalence of TeddyID
Virtually none. The startup is now in a typical situation, when even a good and convenient initiative with great difficulty conquers the first users. Even if you now invest huge amounts of money and create the most convenient social network in the world, Facebook will be almost impossible to catch up with. The window of opportunity is gone. The project offers a really interesting concept, which allows you to conveniently and securely access, but such competitors are such giants as Facebook, Google and others that offer users convenient authorization without using a password. Therefore, the project team will not only have to convince the largest platforms to add the integration of their system, but also to convince users that they are more comfortable and safer than Google+, integrated, in my opinion, into each kettle.
In general, I liked the project, but it feels that there is still a lot of work to be done until he heals a full life.
Source: https://habr.com/ru/post/248575/
All Articles