Not all antiviruses are equally useful: Sergey Gordeychik and Vladimir Kropotov webinar
Recently, the New York Times published an article about how evidence was obtained of North Korea’s involvement in a massive attack on Sony. Back in 2010, specialists from the US National Security Agency hacked DPRK computer networks and secretly monitored the activity of North Korean hackers.
In addition to sources in the special services, this version is confirmed by documents previously published by Edward Snowden in the magazine Spiegel. NSA staff managed to infiltrate Chinese networks that connect North Korea’s Internet with the rest of the world and spread the malware to local hacker groups.

')
According to the New York Times, NSA experts watched the first phishing attacks on Sony when the password of one of the system administrators of the corporation was stolen, which became the starting point for implementation.
Curiously, in 2011, Sony has already been subjected to massive hacking (and in 2010 it sued the regular member of PHDays - Geohot'om), and reorganized the information security division, but this did not help. From September to November 2014, Koreans studied Sony's internal network infrastructure, identifying servers with the most valuable information. The NSA did not think that it would go so far, and did nothing. The consequences were very serious - the speech of Barack Obama, new sanctions against North Korea, harsh statements from the opposite side.
In this regard, it is worth remembering another series of targeted attacks related to targeted phishing. They were conducted by Chinese intelligence services against Tibetan and Uyghur activists, attacking the resources of organizations advocating Tibetan independence. As a result, the Chinese authorities managed to identify individual conspirators, although they checked every file received by mail with antivirus programs. Precautions did not save them from being infected by exploits that exploit various vulnerabilities in Microsoft Office (Exploit.MSWord.CVE-2010-333, Exploit.Win32.CVE-2012-0158, etc.).
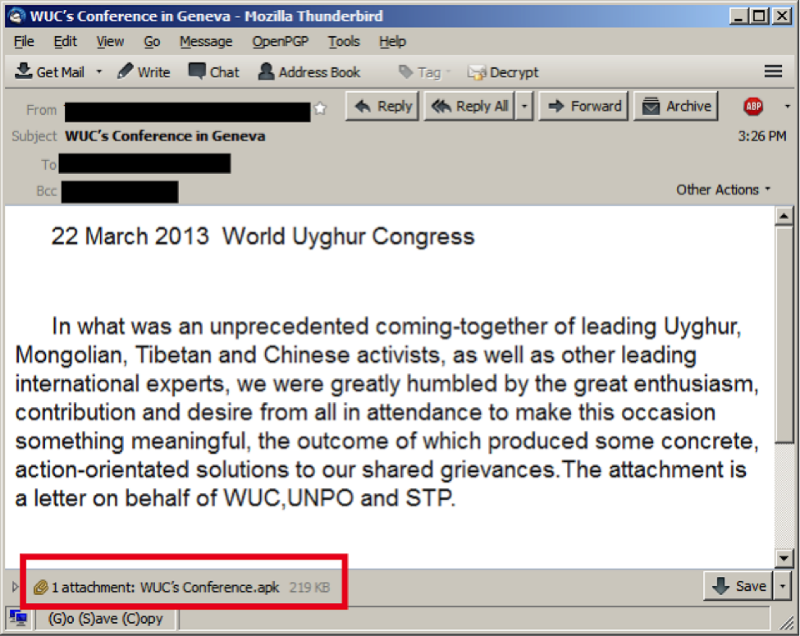
In the future, in some cases, the NetTraveler malware, which was developed for covertly monitoring the computer: recording keystrokes, copying documents, and other actions, was downloaded to the victims' computers. Interestingly, NetTraveler was also used to spy on governments, oil companies, research organizations from dozens of countries, from Australia to Belarus.
We in our blog more than once talked about the ineffectiveness of signature methods when dealing with targeted attacks. Its reasons are that there are simple ways to reduce the detectability of a malicious program, and it is difficult to keep signature databases up to date with the growing volume of new and modified malware.

Tibetan human rights activists downloaded emails on VirusTotal to block viruses embedded directly into an e-mail, but this not only did not help, but also complicated the situation: all correspondence remained on VirusTotal and after some time became public.
The topic of APT and targeted virus outbreaks will continue on this Thursday, Sergey Gordeychik and Vladimir Kropotov at a free webinar. Experts at Positive Technologies will talk about targeted attacks from the point of view of the “cleaner of the August stables”, the benefits of retrospective analysis and the new product of the company - PT Multiscanner.
The webinar will begin on January 22, 2015 at 14:00 (registration on the site ).
In addition to sources in the special services, this version is confirmed by documents previously published by Edward Snowden in the magazine Spiegel. NSA staff managed to infiltrate Chinese networks that connect North Korea’s Internet with the rest of the world and spread the malware to local hacker groups.

')
According to the New York Times, NSA experts watched the first phishing attacks on Sony when the password of one of the system administrators of the corporation was stolen, which became the starting point for implementation.
Curiously, in 2011, Sony has already been subjected to massive hacking (and in 2010 it sued the regular member of PHDays - Geohot'om), and reorganized the information security division, but this did not help. From September to November 2014, Koreans studied Sony's internal network infrastructure, identifying servers with the most valuable information. The NSA did not think that it would go so far, and did nothing. The consequences were very serious - the speech of Barack Obama, new sanctions against North Korea, harsh statements from the opposite side.
In this regard, it is worth remembering another series of targeted attacks related to targeted phishing. They were conducted by Chinese intelligence services against Tibetan and Uyghur activists, attacking the resources of organizations advocating Tibetan independence. As a result, the Chinese authorities managed to identify individual conspirators, although they checked every file received by mail with antivirus programs. Precautions did not save them from being infected by exploits that exploit various vulnerabilities in Microsoft Office (Exploit.MSWord.CVE-2010-333, Exploit.Win32.CVE-2012-0158, etc.).

In the future, in some cases, the NetTraveler malware, which was developed for covertly monitoring the computer: recording keystrokes, copying documents, and other actions, was downloaded to the victims' computers. Interestingly, NetTraveler was also used to spy on governments, oil companies, research organizations from dozens of countries, from Australia to Belarus.
We in our blog more than once talked about the ineffectiveness of signature methods when dealing with targeted attacks. Its reasons are that there are simple ways to reduce the detectability of a malicious program, and it is difficult to keep signature databases up to date with the growing volume of new and modified malware.

Tibetan human rights activists downloaded emails on VirusTotal to block viruses embedded directly into an e-mail, but this not only did not help, but also complicated the situation: all correspondence remained on VirusTotal and after some time became public.
The topic of APT and targeted virus outbreaks will continue on this Thursday, Sergey Gordeychik and Vladimir Kropotov at a free webinar. Experts at Positive Technologies will talk about targeted attacks from the point of view of the “cleaner of the August stables”, the benefits of retrospective analysis and the new product of the company - PT Multiscanner.
The webinar will begin on January 22, 2015 at 14:00 (registration on the site ).
Source: https://habr.com/ru/post/248351/
All Articles