Electronic signature on Russian regulations: practical use in enterprises
State and commercial enterprises
The first part of the article dealt with the use of electronic signatures in commercial enterprises. In state-owned enterprises and banks, things are a little different. Here you need to use a certified cryptographic provider, and the keys themselves must be stored on tokens. Therefore, the second part of this article will show how to use certified crypt provider and tokens to store keys outside the computer. First we will talk about the crypto-provider, and then we will consider the practical use of the program.
In Russia, certified crypto providers provide not so many companies: LLC KRIPTO-PRO, LLC Lissi, OJSC InfoTeKS, CJSC Signal-KOM and some others.
The CyberSafe program supports work with a certified crypt provider from CRIPTO-PRO LLC, which provides the ability to generate and verify an electronic signature in accordance with national standards GOST R 34.11-94 / GOST R 34.11-2012 and GOST R 34.10-2001 / GOST R 34.10- 2012
Can I use the CyberSafe program?
Encryption of personal files is one thing, but the government and banking sector is another. What norms allow CyberSafe to be considered as a program using the SKZI certified by the FSB of Russia and not requiring appropriate certification? The answer to this question can be obtained in the passport (form) for the CryptoPro CSP software product and in the methodological recommendations on ensuring the security of personal data using cryptographic tools when processing them in personal data information systems using automation tools. The latter were approved by the FSB of Russia on February 21, 2008 No. 149 / 54-144.
In the passport of the CryptoPro CSP, we read clause 1 of section 2:
It is allowed to use SKZI for cryptographic protection of personal data.
')
Next, open the guidelines and read paragraph 1 of section 5:
5.1. Embedding of cryptographic tools of class 1 and 2 is carried out without control from the FSB of Russia (if this control is not provided for by the technical task for the development (modernization) of the information system).
In accordance with the Requirements for ES facilities and the Requirements for CA facilities, which are approved by order of the FSB of Russia of December 27, 2011 No. 796, six classes of cryptographic tools are established - KS1, KS2, KS3, KV1, KV2, KA1. Embedding of cryptographic tools of class KS3, KV1, KV2 and KA1 is carried out only under the control of the FSB of Russia. As for the classes KS1 and KS2, no control is exercised by the FSB. You can read more about cryptographic protection classes at the link provided at the end of the article.
As you can see, CyberSafe is not only possible to use, but necessary. The source code of the encryption library that the program uses is available to everyone (a link to it is on the home page of the cybersafesoft.com website) at: www.assembla.com/spaces/cybersafe-encryption-library/wiki
The following is the encryption and signature function code to ensure the reliability of the implementation (sheet 1).
Listing 1. Encryption and signature function (GOST)
function EncryptAndSign (ASignCertContent: string; AEncCerts: TStringList;
FileName, OutFileName: string; out ErrText: String): Boolean;
var
hProv: HCRYPTPROV;
hStoreHandle: HCERTSTORE;
pSignerCert: jwawincrypt.PCCERT_CONTEXT;
encCert: jwawincrypt.CRYPT_DATA_BLOB;
SigParams: jwawincrypt.CRYPT_SIGN_MESSAGE_PARA;
pCertContext: PCCERT_CONTEXT;
Stream: TMemoryStream;
Certificates: array [0 .. 100] of PCCERT_CONTEXT;
EncParams: CRYPT_ENCRYPT_MESSAGE_PARA;
cbEncrypted: DWORD;
i: Integer;
pszObjId: LPSTR;
begin
Result: = False;
for i: = 0 to 100 do
Certificates [i]: = nil;
if not jwawincrypt.CryptAcquireContext (hProv, nil, nil, PROV_GOST_2001_DH,
CRYPT_VERIFYCONTEXT) then
Exit;
hStoreHandle: = CertOpenSystemStore (hProv, 'MY');
if (hStoreHandle = nil) then
begin
ErrText: = 'ErrorOpenStore';
Exit;
end;
for i: = 0 to AEncCerts. Count - 1 do
begin
try
encCert: = GetCertContent (FileToStr (AEncCerts.Strings [i]));
except
ErrText: = 'ErrorCertLoad';
Continue;
end;
pCertContext: = jwawincrypt.CertCreateCertificateContext (MYTYPE,
encCert.pbData, encCert.cbData);
pCertContext: = jwawincrypt.CertFindCertificateInStore (hStoreHandle, MYTYPE,
0, CERT_FIND_EXISTING, pCertContext, nil);
if (pCertContext = nil) then
begin
ErrText: = 'ErrorCertInStoreNotFound';
Continue;
end;
Certificates [i]: = pCertContext;
end;
encCert: = GetCertContent (FileToStr (ASignCertContent));
// Open the certificate store
pSignerCert: = nil;
pSignerCert: = jwawincrypt.CertCreateCertificateContext (MYTYPE,
encCert.pbData, encCert.cbData);
pSignerCert: = jwawincrypt.CertFindCertificateInStore (hStoreHandle, MYTYPE, 0,
CERT_FIND_EXISTING, pSignerCert, nil);
if (pSignerCert = nil) then
begin
Exit;
end;
with TMemoryStream.Create do
try
LoadFromFile (FileName);
try
try
// Initialize the structure required for a digital signature
pszObjId: = szOID_RSA_MD5; // get the certificate algorithm
FillChar (SigParams, SizeOf (CRYPT_SIGN_MESSAGE_PARA), # 0);
SigParams.cbSize: = SizeOf (CRYPT_SIGN_MESSAGE_PARA);
SigParams.dwMsgEncodingType: = MYTYPE;
SigParams.pSigningCert: = pSignerCert;
SigParams.HashAlgorithm.pszObjId: = pszObjId;
// for Signal - Com szOID_RSA_MD5; // 1.2.643.2.2.21
SigParams.HashAlgorithm.Parameters.cbData: = 0;
SigParams.cMsgCert: = 1;
SigParams.rgpMsgCert: = @pSignerCert;
SigParams.cAuthAttr: = 0;
SigParams.dwInnerContentType: = 0;
SigParams.cMsgCrl: = 0;
SigParams.cUnauthAttr: = 0;
SigParams.dwFlags: = 0;
SigParams.pvHashAuxInfo: = nil;
SigParams.rgAuthAttr: = nil;
ZeroMemory (@EncParams, SizeOf (CRYPT_ENCRYPT_MESSAGE_PARA));
EncParams.cbSize: = SizeOf (CRYPT_ENCRYPT_MESSAGE_PARA);
EncParams.dwMsgEncodingType: = MYTYPE;
EncParams.HCRYPTPROV: = hProv;
EncParams.ContentEncryptionAlgorithm.pszObjId: = szOID_CP_GOST_28147;
// Encryption algorithm GOST 28147-89 1.2.643.2.2.21
if CryptSignAndEncryptMessage (@SigParams, @EncParams, AEncCerts.Count,
@Certificates, Memory, Size, nil, cbEncrypted) then
begin
Stream: = TMemoryStream.Create;
try
Stream.SetSize (cbEncrypted);
if CryptSignAndEncryptMessage (@SigParams, @EncParams,
AEncCerts.Count, @Certificates, Memory, Size, Stream.Memory,
cbEncrypted) then
begin
Stream.SetSize (cbEncrypted);
Stream.SaveToFile (OutFileName);
Result: = True;
end
else
ErrText: = SysErrorMessage (GetLastError);
finally
FreeAndNil (Stream);
end;
end
else
ErrText: = SysErrorMessage (GetLastError);
except
ErrText: = SysErrorMessage (GetLastError);
end;
finally
CertCloseStore (hStoreHandle, CERT_CLOSE_STORE_CHECK_FLAG);
end;
finally
Free;
end;
end;
Practical use of the program
The first step is to install a certified crypto-provider CryptoPro CSP. Download the software product is absolutely free, but after pre-registration at
www.cryptopro.ru/downloads
Download and run the installation file. Click the Install button and wait for the message indicating the successful installation of the software product (Fig. 1).
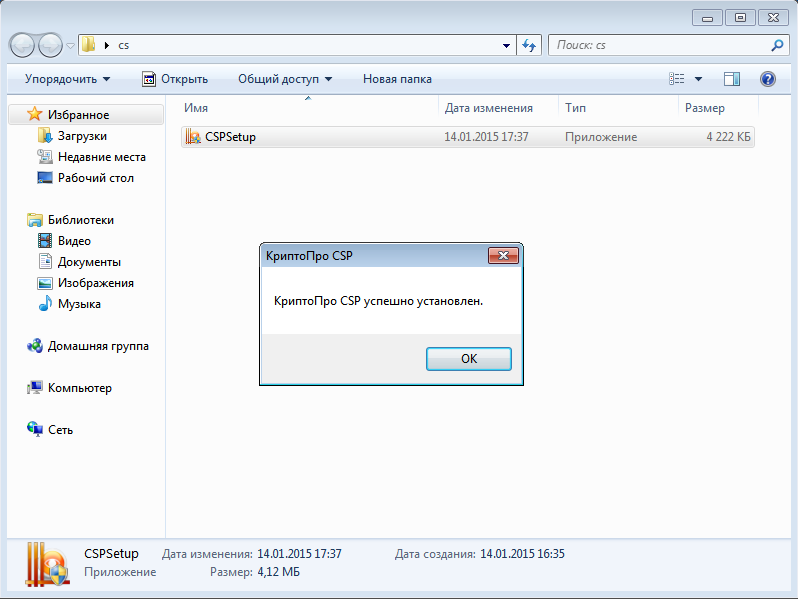
Fig. 1. CryptoPro CSP successfully installed
Next, run the CyberSafe program. When you first start up after installing the CryptoPro CSP, you must install the CyberSafe GOST CA certificate (Fig. 2).

Fig. 2. Install certificate
After installing the certificate CyberSafe GOST CA it's time to talk about tokens. A token is a USB device that is used to authenticate a user, protect electronic correspondence, secure access to remote information resources, and also to store cryptographic keys. Since tokens are quite expensive devices, CyberSafe can use regular flash drives instead. Keys placed on it will be stored on the flash drive. However, on tokens your keys are protected from copying, but not on a flash drive. But given the cost of tokens, such a decision is fully justified. In other words, CyberSafe saves you money.
When using both tokens and ordinary flash drives for storing keys, your keys will not be stored on a computer, but on an external medium (token or flash drive).
So, create a Crypto Pro certificate. Select the menu command Certificates, Create . In the Create Certificate window, enter the email address, password, name, and other information. Make sure that you enable the Create Crypto Pro Certificate check box (Figure 3). If this check box is not present, make sure that you install the CryptoPro CSP and restart CyberSafe after the installation.
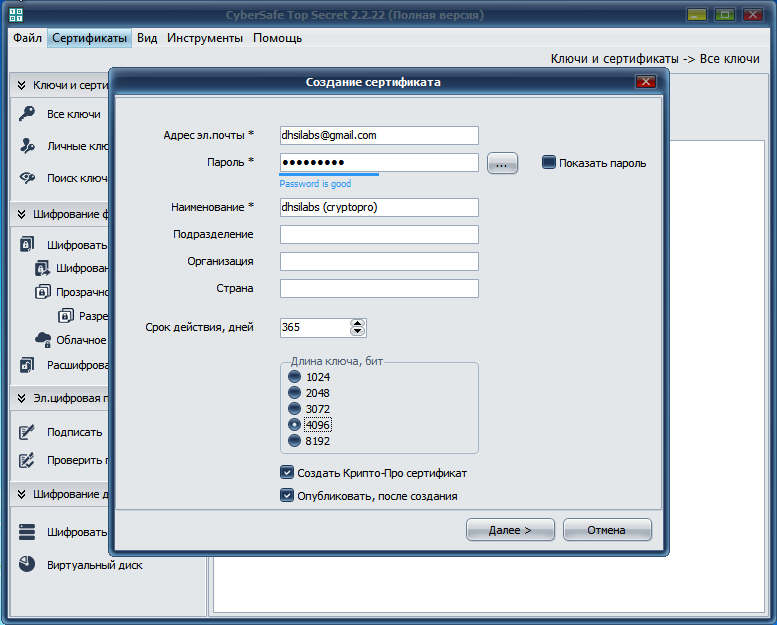
Fig. 3. Creating a Crypto Pro Certificate
The next step is very important. You need to choose exactly where to store the container of the private key - on a USB drive (Fig. 4a) or on a token (Fig. 4b). Select the token or removable disk on which you want to store the certificate (just make sure you select the correct one), or select the Registry if you want to store the certificate in a computer.

Fig. 4a. The certificate will be stored on a flash drive

Fig. 4b. The certificate will be stored on a token.
Next, you will need a little physical work - you need to press the keys on the keyboard or move the mouse pointer until the key is created (Fig. 5).
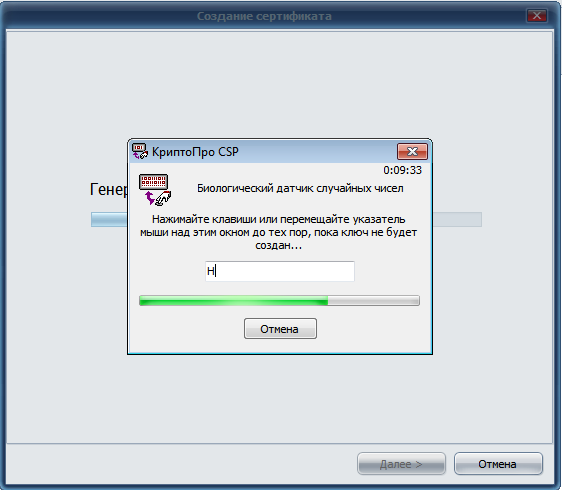
Fig. 5. Key creation process
Next, you need to create a password for the container itself (Fig. 6a) or a pin code (Fig. 6b) for the token. This password must be different from the certificate password for security reasons.
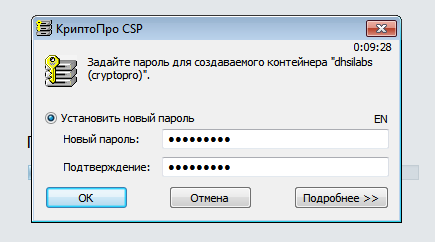
Fig. 6a. Container password (flash drive)

Fig. 6b. Pin for container (token)
Then you will see a message that the certificate was successfully created (Fig. 7), and after clicking the Finish button, you need to open your mailbox and find the certificate’s publication confirmation code (if, of course, you chose to publish the certificate) and enter it into the window (fig. 8).
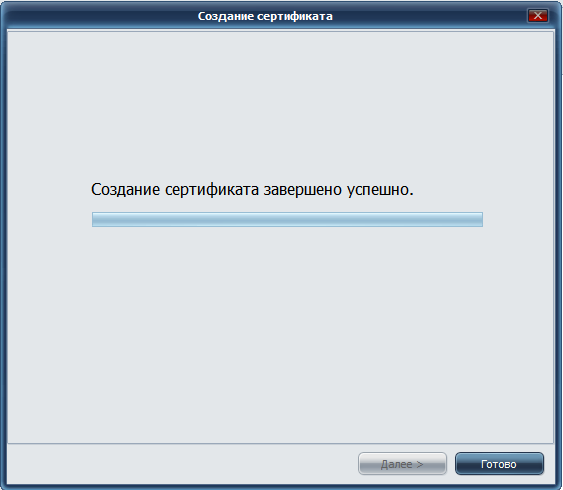
Fig. 7. Certificate successfully created
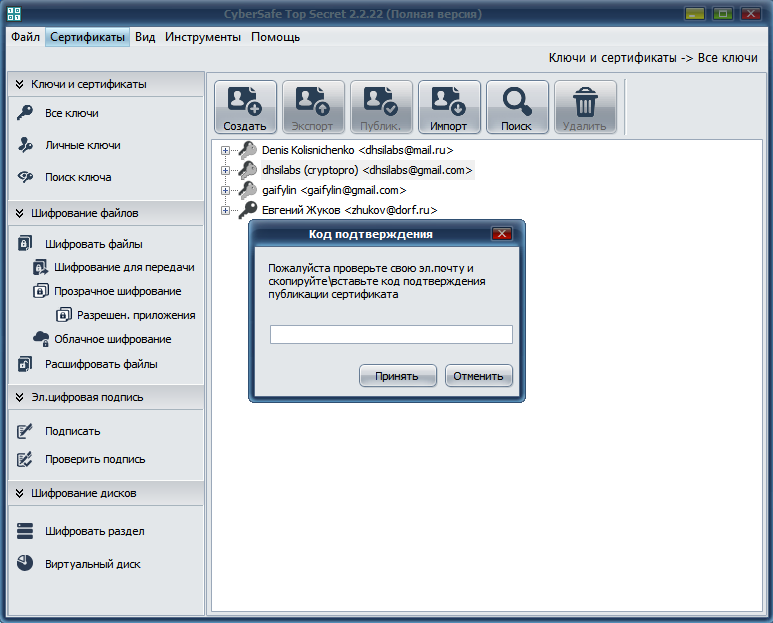
Fig. 8. Enter the certificate verification code
During the publication of the certificate you will see that it consists of six files (Fig. 9). After publishing the certificate, you will see a message about its successful publication on the server. It is clear that at the time of publication an Internet connection must be established. Open Explorer and view the contents of the flash drive. In the <name> .000 directory you will find the private keys (Fig. 10).

Fig. 9. The process of publishing the certificate
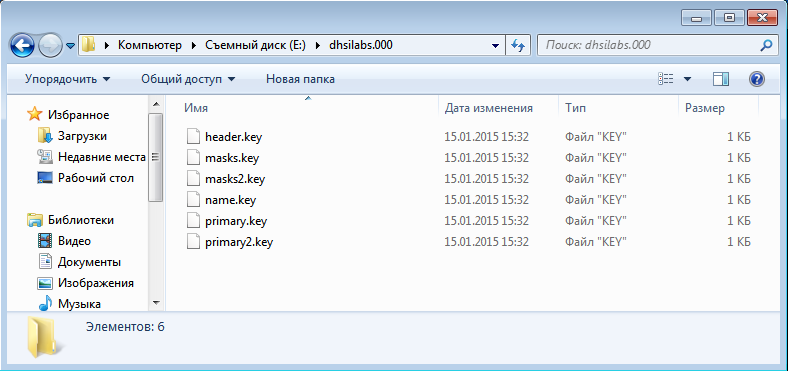
Fig. 10. Private keys
Go to the Keys and Certificates section , All keys and make sure that the certificate you created is in the list of certificates (Fig. 11).
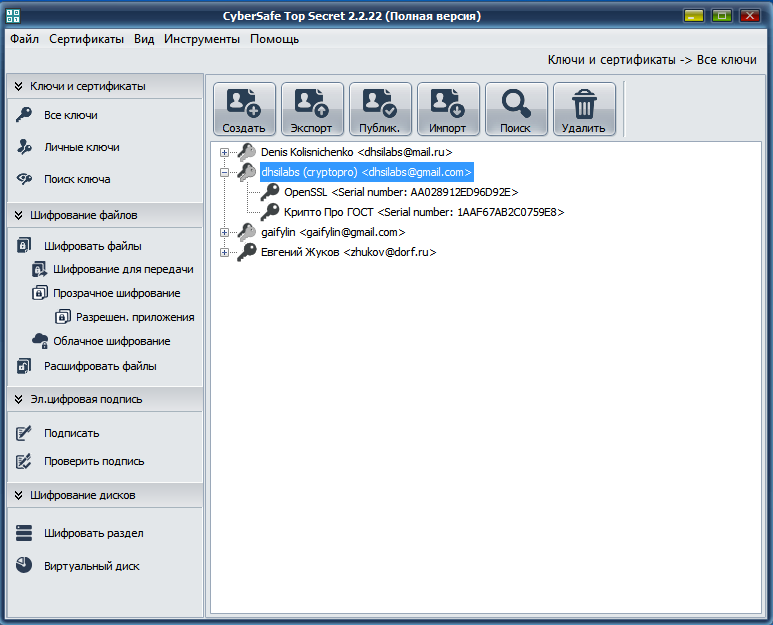
Fig. 11. Created certificate in the general list
Further, the created certificate can be used as usual (as was shown in the first part of the article). For example, it can be used to encrypt files. The encryption process is the same, so we will not consider it in detail. Let me just say that when encrypting files, you need to select the crypto-provider Crypto Pro GOST from the list Choose a crypto provider (fig. 12). Further you will see a list of keys corresponding to this crypto-provider.

Fig. 12. File encryption according to GOST
Similarly, with transparent folder encryption (when you need to encrypt all files from this folder), you need to select the cryptographic provider Crypto Pro GOST from the corresponding list (Fig. 13).

Fig. 13. The choice of cryptographic provider with transparent encryption
You can also choose encryption according to GOST, you can choose when encrypting a disk / partition (see. Fig. 14). In the Encryption type list, select the GOST and set the encryption parameters.

Fig. 14. Disk Encryption
findings
The CyberSafe program is not only possible, but also should be used in government organizations and banks, since the program supports a certified cryptographic provider (Crypto Pro) and allows you not to store certificates (keys) on your computer, but transfer them to external media.
Links
The level of cryptographic protection in the implementation of the exchange of electronic messages protected by electronic signature
ZTTYAI form 00050-03 30 01 (CryptoPro Pro CSP)
Guidelines
Encryption Library Source Code
The first part of the article
Source: https://habr.com/ru/post/248271/
All Articles