“Perfect” coin toss: The NIST Randomness Beacon
In statistical terms, “random variable” is a function that yields a value that is unknown until a certain time and is constant after.
Since September 5, 2013, NIST publishes a random number of 512 bits every minute. This number, the previous number, the time when it was generated and some more information are digitally signed by NIST, so you can easily verify that the number was generated by NIST.
')
NIST Randomness Beacon (hereinafter - "beacon") solves three interesting problems
- Actually, it generates a fairly high-quality pseudo-random number.
- Provides it for public viewing (by the way, so they have a big red font that says “Do not use this as an encryption key!”)
- Makes it possible to verify that the number has not been compromised
We will understand the points
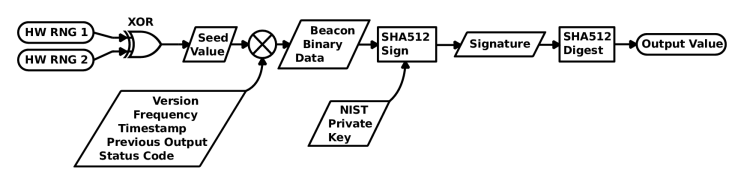
1) The scheme is quite simple: The output of two iron generators is taken, it turns out, it turns out Seed Value (it is also published).
Then it is concatenated with service fields, the previous value and is passed through SHA-512.
This hash is signed by the NIST private key and the signature is again driven through SHA-512, giving us the desired pseudo-random number.
2) This is the meaning of a random beacon so that you can get the same pseudo-random data from anywhere.
For example, you and your family want to determine who will wash the dishes next time. Numbered, agree to look at the lighthouse at 17:00, and at certain times, see who was lucky.
3) This is the most interesting. The scheme is constructed in such a way that the probability of manipulating the final data is very close to zero. That is, we have every right not to trust the numbers from NIST and we can make sure that nothing has affected them.
Suppose an attacker was able to change the value of Seed. But between Seed and Output Value there are two passes SHA-512 + digital signature. Even if he gets access to the NIST private key, he is unlikely to be able to defeat SHA-512.
In addition, no one forbids to use the previous values to get the Output Value that you need. You can take the current one, and xorit with what was a day ago and take as a result. In this case, a cracker would have to break 2 * 24 * 60 = 2,880 calls to SHA-512, which is even worse.
Even if we assume that all this is real, you can still easily defend yourself against such attacks using your own Output Value processing scheme, the main thing is that it should be the same for everyone who uses it.
For example, take the Output Value as an encryption key (not for real encryption, but to get a pseudo-random number) and encrypt itself with the AES algorithm, then run it through SHA-3, and so on. The attacker will scratch it all specifically for you.
Now about the real chance. NIST uses two commercial RNGs, which, although they are hardwired, we still cannot prove that there is truly random data. And they want . Using quantum effects and Bell’s theorem, NIST wants to achieve data that is proven unknown until a certain time.
Also, no one bothers you to build and launch such a lighthouse yourself and mix it with NIST's. The more beacons, the more reliable the random numbers.
shell script that verifies the current value of the beacon.
#!/bin/sh ## NIST Randomness Beacon verification routine ## Only slightly adapted by Elliot Williams ## from code provided by Lawrence Bassham, NIST ## The UNIX time that you'd like to test: ## whichRecord=1400878200 ## --------------- Utility Functions ---------------- ## Extracts specified record from xml file getValue() { xmllint --xpath "/record/$1/text()" $2 } ## Converts little-endian to big-endian byteReverse() { len=${#1} for((i=${len}-2; i>=0; i=i-2)) do rev="$rev${1:$i:2}" done echo ${rev} } ## ---------------- Get an arbitrary record ----------------- echo "Downloading data for: ${whichRecord}" curl -s https://beacon.nist.gov/rest/record/${whichRecord} -o rec.xml ## ------------- Pack data into correct format -------------- echo echo "## Create a summary of all of the data, save as beacon.bin" ## Strangest choice of format ever! ## Version number (ascii text) ## Update frequency (4 bytes) ## Time Stamp (8 bytes) ## The HW RNG seedValue (64 bytes) ## The previous output value, does the chaining (64 bytes) ## Status code (4 bytes) getValue version rec.xml > beacon.bin printf "%.8x" `getValue frequency rec.xml` | xxd -r -p >> beacon.bin printf "%.16x" `getValue timeStamp rec.xml` | xxd -r -p >> beacon.bin getValue seedValue rec.xml | xxd -r -p >> beacon.bin getValue previousOutputValue rec.xml | xxd -r -p >> beacon.bin printf "%.8x" `getValue statusCode rec.xml` | xxd -r -p >> beacon.bin ## ------------------ Verify signature on data -------------------- echo "## Verify that the signature and NIST's public key correctly SHA512 sign the data" ## Download Beacon's public key echo "Downloading Beacon's public key" curl -s https://beacon.nist.gov/certificate/beacon.cer -o beacon.cer ## Create a bytewise reversed version of the listed signature ## This is necessary b/c Beacon signs with Microsoft CryptoAPI which outputs ## the signature as little-endian instead of big-endian like many other tools ## This may change (personal communication) in a future revision of the Beacon signature=`getValue signatureValue rec.xml` byteReverse ${signature} | xxd -r -p > beacon.sig ## Pull public key out of certificate /usr/bin/openssl x509 -pubkey -noout -in beacon.cer > beaconpubkey.pem ## Test signature / key on packed data /usr/bin/openssl dgst -sha512 -verify beaconpubkey.pem -signature beacon.sig beacon.bin echo echo ## ------------------ Verify Signature -> Output and Chaining ------------ echo "The following three values should match: " echo " a direct SHA512 of the extracted signature" echo " the reported output value" echo " next record's previous output value" echo ## Just print output value echo "Reported output value" getValue outputValue rec.xml echo ## Now turn the signature into the output value: again SHA512 echo "SHA512 of the signature" getValue signatureValue rec.xml | xxd -r -p | sha512sum ## Now test chaining ## Get next record echo "Downloading the next record" curl -s https://beacon.nist.gov/rest/record/next/${whichRecord} -o next.xml ## Make sure that this period's output shows up as next period's "previous output" echo "Next value's reported previous output (test of forward chaining)" getValue previousOutputValue next.xml echo echo ## --------------------- The End ----------------------------------------- ## If this all worked, we've verified that the signature (plus NIST's key) ## sign the hash of the random number and its support info ## _and_ we've verified that the outputValue is derived from them, ## so we know that this output value is in the chain. ## If we run this on every entry in the chain, and all works out just fine, ## then we'd know all is well Source: https://habr.com/ru/post/247309/
All Articles