Win32 / Virlock - the first self-propagating extortionist
The Win32 / Virlock malware is the first ransomware known to date (ransomware), which specializes in infecting executable files, that is, it behaves like a file virus. Virlock is able to block the user's desktop with a ransom demand, encrypt user files, and also propagate his body as a polymorphic virus.

Families of ransomware, which we saw earlier, in fact, can be divided into two large groups: screen blockers (LockScreen) and file encryption (Filecoder). In the first case, the extortioner blocks the user from accessing the desktop until a ransom is received, and in the second case, encrypts the user's files, making it impossible to use them. At the same time, a ransom request message may appear as desktop wallpaper, as an open text file, and also through a simple window (as is the case with Cryptolocker ).
')
In some cases, the extortioner may use a hybrid approach and contain both of these possibilities, that is, blocking access to the desktop or device is accompanied by encryption of files on it. At the same time, the malicious code will use special mechanisms to prohibit closing the window that appears. An example of such a malicious program is the extortionist Android / Simplocker .
In October, we fixed a new type of malware like the extortionist. The Win32 / Virlock malware could block a user's desktop with a ransom request, encrypt files, and also infect executable files as a polymorphic virus, embedding their code into them. We recently discovered several new modifications of this virus, which indicates its active development by intruders. The VirLock code demonstrates a high level of technical training for the authors of this malicious program.
Win32 / Virlock uses a special trick to encrypt files. Instead of the usual method of byte-grade encryption of the entire file or its beginning, such a file is converted to an executable and the Virlock code is added to it. The malicious program specializes in compromising the following file types: * .exe, * .doc, * .xls, * .zip, * .rar, * .pdf, * .ppt, * .mdb, * .mp3, * .mpg, * .png, * .gif, * .bmp, * .p12, * .cer, * .psd, * .crt, * .pem, * .pfx, * .p12, * .p7b, * .wma, * .jpg , * .jpeg. In this case, Virlock is able to infect files on network drives and removable media.
When infecting (encrypting) a file that is not executable, Virlock creates a new Win32 executable PE file for it that records the virus code and the encrypted contents of the document. The original file is deleted, and in its place a new one appears with the same name and the .exe extension added to the name. When launching such a file for execution, it decrypts the original file, writes it to the current directory and opens it.
Running an infected Virlock file is accompanied by the creation of two of its new files, which are similar to the original dropper, but because of polymorphism they contain different executable code. One file is created in the% userprofile% directory, and the second in% alluserprofile%. To ensure autoload, the malware writes the path to its file in the appropriate Run registry key of both the HKLM and HKCU sections. We also observed modifications of Virlock, which extracted from themselves the third executable file. He registered as a service. These extracted files were responsible for further infection of the files in the system.
A part of the extortioner's code is responsible for displaying the lock screen to the user, while using the already typical methods of self-defense, including the completion of the conductor and task manager processes.

Fig. Screen lock one of the modifications of the malicious program.
The message in the blocking window contains the warning text for the user and offers to pay the ransom amount in bitcoins. Recently, we wrote about another extortionist TorrentLocker, who also extorts money from the user in this cryptocurrency. Below is the lock screen of a newer version of Virlock, which allows the user to use the web browser and notepad applications.

Fig. Another kind of lock screen. The payment tab is displayed.
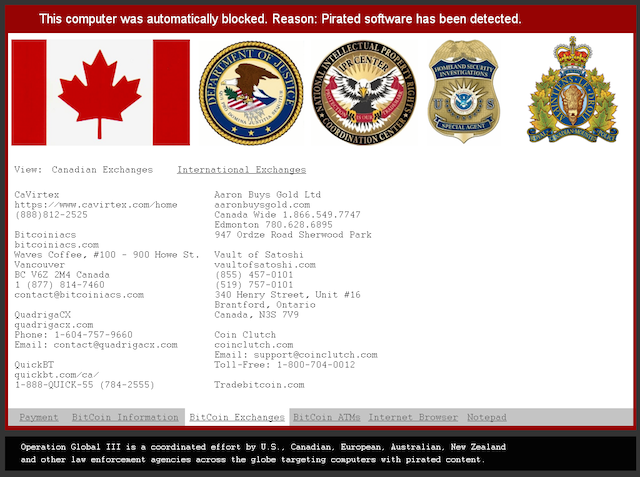
Fig. Tab with information about working with bitcoins in the case of Canada.
Malware code, which is responsible for displaying the lock screen, is able to perform some localization of the interface of the screen itself (window). To do this, use the connection to the website google.com and further analysis of the domain to which the redirection is carried out, for example, google.com.au, google.ca, google.co.uk, google.co.nz. The GetUserGeoID function is also used. For countries that correspond to the above domains, displays its flag, the value of bitcoins and the current exchange rate of the national currency.
From a technical point of view, the most interesting part of the malware is the file infection mechanism and polymorphism. Virlock's polymorphism ensures the uniqueness of the malware body in each infected file. Virlock uses several file encryption layers.
The Virlock executable file includes a special code, which we call the XOR stub builder . It is located in a file in an unencrypted state. The remaining data of the malicious program and its code, as well as the data of the original file (in case we are dealing not with the original dropper, but with the file that was infected) are in encrypted form.
The mentioned XOR stub builder consists of eight blocks of code and is used to generate XOR type instructions that will be used to decrypt the file data. One of these blocks is shown below.

Fig. Block code XOR stub builder .
The blocks of the XOR stub builder code are polymorphic, that is, they differ from one infected file to another. In any case, the execution of each of them leads to the computation of a certain double word (DWORD) and its recording at a fixed offset in memory. These words are XOR stub instructions, i.e. stubs with XOR instructions that decrypt the rest of the file.
We talked about the multi-level approach that Virlock uses when encrypting a file. In this scheme, the XOR stub is used to decrypt a small portion of the executable file code (Part 1). This code consists of several functions. The screenshot below shows a snippet of XOR code stubs. For decryption, the key 0x6B130E06 was used, and the size of the decrypted part is 0x45c.

Fig. The XOR code is a stub. Then control is transferred to the decoded block of code of size 0x45C bytes.
An interesting feature of Virlock is the structure of its decoded code (Part 2). Almost every function in it is encrypted again and starts with a stub that decrypts the code of the function itself. This significantly complicates the analysis of a malicious program, since the function code cannot be analyzed in a disassembler. The stub code is quite simple and uses the XOR algorithm to decrypt the function body. After the function is executed, its code in memory is encrypted back, while encryption is performed using a new key. The figure below shows an example of such a code. The rdtsc instruction is used to obtain an encryption key, then the XOR operation is used to encrypt several variables and the function body.

Fig. Encryption code of the function body after its execution.
This feature of the malware can be called a run-time polymorphism polymorphism. When you run several copies of it, the memory dumps of the executable file will differ.
When decrypting Part 2, the malicious code also resorts to using another decryption procedure. As we mentioned, Part 1, which is decrypted using the XOR stub, decrypts the rest of the malware file and the contents of the infected file, if it is present. The decryption procedure consists of applying the cyclic right shift operation ROR. The decryption key used is hardwired in the body of the malware.
Thus, Virlock uses a three-level encryption scheme:
Virlock contains code that implements file polymorphism (file infection) in the second part. When management receives the corresponding function, it copies the body of the malicious program into the allocated memory. Thus, file polymorphism is a consequence of polymorphism in memory (run-time), since the body of the malicious program copied to the memory section has already been modified by encryption algorithms and code modification (by the functions of the second part, which were executed before the infector code). Further, this code is subjected to re-encryption, in accordance with the levels described above. The copied code is the so-called second part, which, together with the contents of the infected file, is encrypted using new keys. After that, a block of XOR stub builder functions is formed in memory, it will be responsible for decoding the first part.
After completing all the specified steps, Virlock writes a generated file that contains the encrypted virus body and the original file data to disk. To do this, the original file that has been infected is overwritten. If the infected file was not an executable PE file, a new .exe extension is appended to its name and existing extension.
Conclusion
Our LiveGrid telemetry system shows that a small number of users have been infected with Virlock. Their number is not comparable with the number of users who have been infected with TorrentLocker or other extortionists like it. However, an analysis of the transactions conducted on the specified Bitcoin account shows that some victims have already paid the ransom to the attackers.

Families of ransomware, which we saw earlier, in fact, can be divided into two large groups: screen blockers (LockScreen) and file encryption (Filecoder). In the first case, the extortioner blocks the user from accessing the desktop until a ransom is received, and in the second case, encrypts the user's files, making it impossible to use them. At the same time, a ransom request message may appear as desktop wallpaper, as an open text file, and also through a simple window (as is the case with Cryptolocker ).
')
In some cases, the extortioner may use a hybrid approach and contain both of these possibilities, that is, blocking access to the desktop or device is accompanied by encryption of files on it. At the same time, the malicious code will use special mechanisms to prohibit closing the window that appears. An example of such a malicious program is the extortionist Android / Simplocker .
In October, we fixed a new type of malware like the extortionist. The Win32 / Virlock malware could block a user's desktop with a ransom request, encrypt files, and also infect executable files as a polymorphic virus, embedding their code into them. We recently discovered several new modifications of this virus, which indicates its active development by intruders. The VirLock code demonstrates a high level of technical training for the authors of this malicious program.
Win32 / Virlock uses a special trick to encrypt files. Instead of the usual method of byte-grade encryption of the entire file or its beginning, such a file is converted to an executable and the Virlock code is added to it. The malicious program specializes in compromising the following file types: * .exe, * .doc, * .xls, * .zip, * .rar, * .pdf, * .ppt, * .mdb, * .mp3, * .mpg, * .png, * .gif, * .bmp, * .p12, * .cer, * .psd, * .crt, * .pem, * .pfx, * .p12, * .p7b, * .wma, * .jpg , * .jpeg. In this case, Virlock is able to infect files on network drives and removable media.
When infecting (encrypting) a file that is not executable, Virlock creates a new Win32 executable PE file for it that records the virus code and the encrypted contents of the document. The original file is deleted, and in its place a new one appears with the same name and the .exe extension added to the name. When launching such a file for execution, it decrypts the original file, writes it to the current directory and opens it.
Running an infected Virlock file is accompanied by the creation of two of its new files, which are similar to the original dropper, but because of polymorphism they contain different executable code. One file is created in the% userprofile% directory, and the second in% alluserprofile%. To ensure autoload, the malware writes the path to its file in the appropriate Run registry key of both the HKLM and HKCU sections. We also observed modifications of Virlock, which extracted from themselves the third executable file. He registered as a service. These extracted files were responsible for further infection of the files in the system.
A part of the extortioner's code is responsible for displaying the lock screen to the user, while using the already typical methods of self-defense, including the completion of the conductor and task manager processes.

Fig. Screen lock one of the modifications of the malicious program.
The message in the blocking window contains the warning text for the user and offers to pay the ransom amount in bitcoins. Recently, we wrote about another extortionist TorrentLocker, who also extorts money from the user in this cryptocurrency. Below is the lock screen of a newer version of Virlock, which allows the user to use the web browser and notepad applications.

Fig. Another kind of lock screen. The payment tab is displayed.

Fig. Tab with information about working with bitcoins in the case of Canada.
Malware code, which is responsible for displaying the lock screen, is able to perform some localization of the interface of the screen itself (window). To do this, use the connection to the website google.com and further analysis of the domain to which the redirection is carried out, for example, google.com.au, google.ca, google.co.uk, google.co.nz. The GetUserGeoID function is also used. For countries that correspond to the above domains, displays its flag, the value of bitcoins and the current exchange rate of the national currency.
From a technical point of view, the most interesting part of the malware is the file infection mechanism and polymorphism. Virlock's polymorphism ensures the uniqueness of the malware body in each infected file. Virlock uses several file encryption layers.
The Virlock executable file includes a special code, which we call the XOR stub builder . It is located in a file in an unencrypted state. The remaining data of the malicious program and its code, as well as the data of the original file (in case we are dealing not with the original dropper, but with the file that was infected) are in encrypted form.
The mentioned XOR stub builder consists of eight blocks of code and is used to generate XOR type instructions that will be used to decrypt the file data. One of these blocks is shown below.

Fig. Block code XOR stub builder .
The blocks of the XOR stub builder code are polymorphic, that is, they differ from one infected file to another. In any case, the execution of each of them leads to the computation of a certain double word (DWORD) and its recording at a fixed offset in memory. These words are XOR stub instructions, i.e. stubs with XOR instructions that decrypt the rest of the file.
We talked about the multi-level approach that Virlock uses when encrypting a file. In this scheme, the XOR stub is used to decrypt a small portion of the executable file code (Part 1). This code consists of several functions. The screenshot below shows a snippet of XOR code stubs. For decryption, the key 0x6B130E06 was used, and the size of the decrypted part is 0x45c.

Fig. The XOR code is a stub. Then control is transferred to the decoded block of code of size 0x45C bytes.
An interesting feature of Virlock is the structure of its decoded code (Part 2). Almost every function in it is encrypted again and starts with a stub that decrypts the code of the function itself. This significantly complicates the analysis of a malicious program, since the function code cannot be analyzed in a disassembler. The stub code is quite simple and uses the XOR algorithm to decrypt the function body. After the function is executed, its code in memory is encrypted back, while encryption is performed using a new key. The figure below shows an example of such a code. The rdtsc instruction is used to obtain an encryption key, then the XOR operation is used to encrypt several variables and the function body.

Fig. Encryption code of the function body after its execution.
This feature of the malware can be called a run-time polymorphism polymorphism. When you run several copies of it, the memory dumps of the executable file will differ.
When decrypting Part 2, the malicious code also resorts to using another decryption procedure. As we mentioned, Part 1, which is decrypted using the XOR stub, decrypts the rest of the malware file and the contents of the infected file, if it is present. The decryption procedure consists of applying the cyclic right shift operation ROR. The decryption key used is hardwired in the body of the malware.
Thus, Virlock uses a three-level encryption scheme:
- The first part (Part 1) of the malware code is decrypted by the XOR stub code, which in turn is formed using the XOR stub builder .
- The second part (Part 2) of the malware code is decrypted using the first part (Part 1).
- Each function code of the second part (Part 2) is encrypted and decrypted by its own stub, which is located at the very beginning of the function. After executing the function, its code in memory is encrypted back.
Virlock contains code that implements file polymorphism (file infection) in the second part. When management receives the corresponding function, it copies the body of the malicious program into the allocated memory. Thus, file polymorphism is a consequence of polymorphism in memory (run-time), since the body of the malicious program copied to the memory section has already been modified by encryption algorithms and code modification (by the functions of the second part, which were executed before the infector code). Further, this code is subjected to re-encryption, in accordance with the levels described above. The copied code is the so-called second part, which, together with the contents of the infected file, is encrypted using new keys. After that, a block of XOR stub builder functions is formed in memory, it will be responsible for decoding the first part.
After completing all the specified steps, Virlock writes a generated file that contains the encrypted virus body and the original file data to disk. To do this, the original file that has been infected is overwritten. If the infected file was not an executable PE file, a new .exe extension is appended to its name and existing extension.
Conclusion
Our LiveGrid telemetry system shows that a small number of users have been infected with Virlock. Their number is not comparable with the number of users who have been infected with TorrentLocker or other extortionists like it. However, an analysis of the transactions conducted on the specified Bitcoin account shows that some victims have already paid the ransom to the attackers.
Source: https://habr.com/ru/post/247267/
All Articles