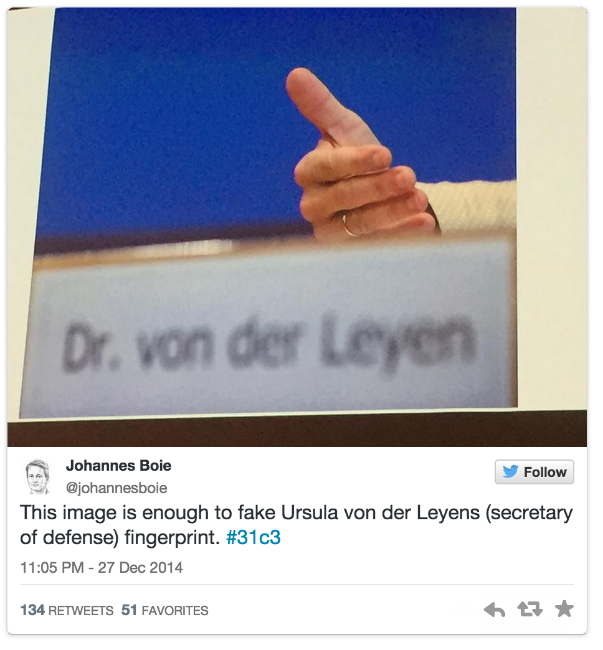
News from the 31C3 Forum: New Intrigues of the NSA, Computer Brain Management and Internet Toilet
On December 27, one of the world's largest hacker conferences, Chaos Communications Congress (31C3), opened in Hamburg. The annual congress gathers a huge number of engineers, makers, political activists, artists and hackers in the broad sense of the word. More than 12,000 participants attended the 31st congress who witnessed very interesting events.
This year, the situation at the event can hardly be called peaceful. Best of all, you can characterize it with a quote from a tweet : "SCADA is still broken, SS7 is hacked, biometrics is hacked and everyone needs to learn cryptography."
')
The key speaker was Alec Empire, a member of the popular techno-hardcore band Atari Teenage Riot, who noted that there is a lot in common between techno-world, art, and hacking, and called on the representatives of these “oceans” for friendship and the exchange of ideas.
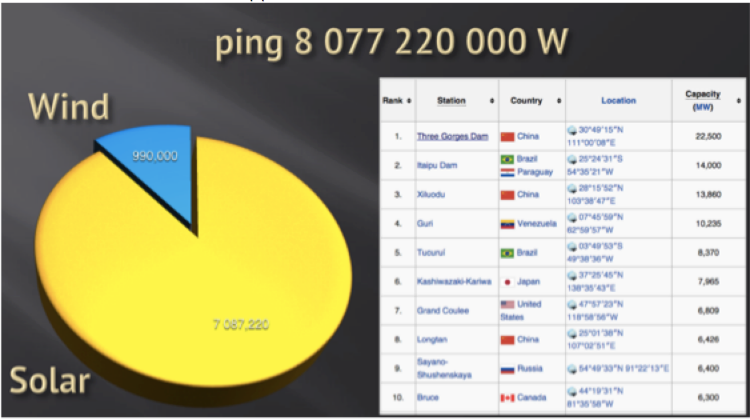
Positive Technologies experts Sergey Gordeychik and Alexander Timorin followed the main report. They showed how to break into the solar and wind energy systems, which generate 8 GW of electricity, which is comparable to the fifth power plant in the world.
Readers of our blog are already partially familiar with the problems of smart grids from this article . The number of SmartGrid devices connected to the Internet without any protection is growing like an avalanche. In the world there are dozens of platforms, hundreds of vendors and millions of end devices.
After the presentation, Positive Technologies specialists from the SCADA StrangeLove group received a lot of questions about such vulnerabilities.
This prompted them to organize the non-commercial SCADASOS initiative to raise awareness in this area, urging volunteers to look for solar and wind installations connected to the Internet using Shodan or Google , and then report these facts to manufacturers, local CERT or IB community. “And do not try to break anything. This could be your grandmother’s hospital or cottage, ”the group said in a statement.
Next, we list the most memorable performances.
An excellent report was presented by Sylvain Muno, familiar from PHDays 2012 and the project osmocombb. The Frenchman spoke about the standard of satellite communications GMR-1 (GEO Mobile Radio), which he traditionally hacked.
Next was a series of studies on intercepting and spying on users of mobile network operators and SS7 protocol vulnerabilities. Our readers should remember publications on this topic (about NSA surveillance , about tapping Ukrainian mobile phones , etc.).
Tobias Engel: SS7: Locate. Track. Manipulate
SS7map: mapping vulnerability of the international mobile roaming infrastructure
Karsten Nohl: Mobile self-defense
By the way, Carsten Nol (on PHDays IV) introduced the SnoopSnitch utility , which detects attacks using baseband debugging features. I also liked the ss7map project.
In Hamburg, a lot of words were said about encryption in 3G / 4G, which, as it turned out in practice, is no better than in 2G, since many providers use the unsafe streaming algorithm A5 / 1, and even if they use A5 / 3, in some cases together with too short 64-bit keys on SIM-cards. Much has also been said about the disadvantages of SIM-card encryption in this blog.
The second day was calmer
Iridium Pager Hacking is worth mentioning about tapping satellite pagers - an excellent example of reverse engineering, on the one hand, in the broad sense of the word, and on the other hand, carelessness based on security by obscurity.
For those who want to immerse themselves in the topic of glitching, this performance is worth a look (the same topic was touched on PHDays III).
Well, just a star of the congress - a study about the Internet toilets. Technically empty, but the performance and sensitive topic did not leave anyone indifferent. Some participants are confident that this report was supposed to be a “keynote” at the conference.
And then the terrible happened, the NSA broke everything again!

Jacob Applebaum, a researcher and one of the main documentalists of Edward Snowden, said that the NSA has methods for decoding PPTP, IPSEC, SSL, SSH traffic. Among the priority targets for hacking in the documents of the American intelligence service, Zoho, the anonymous Tor network, the Truecrypt file encryption application and the Russian Mail.Ru service are noted.

The third day
The final third of the conference started with a speech by Richard Matthew Stallman, who spoke about freedom in general and free software in particular (something like this ).

Many, however, wanted to quickly see the X-ray scanners, where a number of interesting pictures were expected.
What else would you like to mention at 31C3? Apple's impressive hack , a wonderful Advanced binary tricks report, attempts to shove a computer in your ear and control your brain . In addition, Marina Krotofil touched upon the unusual topic of “hacking” the chemical process (and not the system that controls this process), and experts from Positive Technologies talked a bit about USB modems during Lighting Talks.
The conference in Hamburg left a distinct feeling that it would not become calmer in our world in the near future. A simple guy live remotely receives the biometric data of Angela Merkel, everyone is watching each other, and even a certain Mutti, whoever he is, is watching us.

Source: https://habr.com/ru/post/247129/
All Articles