Electronic Signature: Enterprise Practical Use of the CyberSafe Enterprise Software Product. Part one
We are all accustomed to the term “electronic digital signature”, but now it is more correct to use another term - “electronic signature”, since in April 2011 Federal Law No. 63-FZ “On electronic signature” entered into force (hereinafter simply the law “On electronic signature "). It is this law that replaced Law No. 1- “On Electronic Digital Signature”. Therefore, what we used to call “digital signature” is now simply called “electronic signature”.
This part of the article focuses on the use of electronic signatures in a commercial enterprise. First, we will consider when the electronic signature will be useful and useful at every enterprise, and then we will consider its practical use.
First of all, you need to say what an electronic signature is. This is information that is attached to other information (to the information to be signed) in order to determine the person who signed the information, as well as the fact that the information remains unchanged after it is signed.
The Law on Electronic Signature itself states the following: “electronic signature is information in electronic form that is attached to other information in electronic form (signed information) or otherwise associated with such information and which is used to determine the person signing the information” .
Thus, the main task of the electronic signature is to establish the authorship of the document and ensure that the document has not been changed after its signing.
')
If you delve into the law "On electronic signature", then the electronic signature is simple and strengthened. A simple electronic signature confirms only the fact of electronic signing of a document by a certain person.
Strengthened electronic signature, in turn, is divided into reinforced unqualified and reinforced qualified. Reinforced unqualified electronic signature allows you to:
Also, enhanced unqualified ES should be obtained as a result of cryptographic transformation of information using an electronic signature key.
Reinforced qualified ES is the same as reinforced unqualified, but the ES verification key is specified in the qualified certificate, and means are used to create and verify the ES that receive confirmation of compliance with the requirements established by the Law On Electronic Signature. The CyberSafe program, considered further, offers just the option of enhanced qualified electronic signature.
The most common variant of the internal workflow of the enterprise - this service notes. It makes no sense to print the document and sign it personally if you can digitally sign it and send it further down the chain.
The electronic signature here saves not only time but also money - the consumption of paper and printer toner is reduced. Of course, the cost of one printed sheet of paper may not be very high, but for the year you can save quite a decent amount, and this is not to mention the time, which today is expensive.
Typically, the company uses network printers. Network printer can be located in another office or even on another floor. The employee who has printed the service note needs to leave his office, get to the printer and find his note among the other documents. 10-15 minutes are spent on everything about everything, and if we take into account the human factor (conversations with employees in the next room), then much more. As a result, these 10-15 minutes could be spent more productively than searching for a printed document.
The second example is the process of negotiating a contract. Imagine that an employee Ivanov prepares a contract and sends it for approval to the head. The principle is the same as with the memo - why waste time on printing a dialect, if you can sign it with an electronic signature? The head makes changes to the contract, signs it and sends it to Ivanova. Considering that there will be a lot of changes (after all, mistakes are inevitable anyway), the use of an electronic signature again saves a lot of time and money.
In large corporate networks, where a manager and even an ordinary employee Ivanov can have detractors, an electronic signature is a reliable way to verify the authorship of the document and its immutability (that no one without Ivanov’s knowledge or his manager made any changes to it).
You can argue that they have access rights and you can see who last edited the document. Why do we need an electronic signature? Everything seems to be correct, if not for one thing. In any system, there is a user with maximum rights - the administrator, who can not only change the document itself, but also its attributes (including the time / date of the change, the author of the last change, etc.).
When exchanging information with remote branches and partners of the company, email is usually used. And here you can use an electronic signature so that your partners and employees of remote branches can be sure that this message was sent precisely by you, and not by someone who wants to appear to you.
Yes, there is no practice of concluding contracts in full in electronic form. A wet seal and signature is still needed. Therefore, to seal the contract with a partner in a fully electronic form will not work. But then you can safely exchange messages with your partners and have no doubt that someone will forge your message or the message of a partner.
As for the exchange of documents with remote branches, then you can use an electronic signature, as in the internal document management. Now the document flow between branches takes place in semi-digital form. Namely: the document must first be printed out, then the manager must sign it, after which the secretary of the manager scans it and sends it by e-mail to a remote branch office, where it is printed again.
The electronic signature allows you to reduce this process: the document is signed with an electronic signature and sent to a remote branch where the recipient can verify the electronic signature and make sure that the document was signed by the manager.
It is still difficult for a person to get used to an electronic signature and is not treated as something serious. While on the document will not be "wet" his signature, still, do not consider it signed. Employees will still use copies of paper documents, lose their private keys, not considering them something important. How to overcome the psychological barrier? How to overcome the very “without a piece of paper - you're a bug, and with a piece of paper - a man”?
It turns out that there is a way out and it consists in another piece of paper. It is necessary inside the company to adopt "the provision on electronic document circulation". All employees must familiarize themselves with it and affirm the adoption of this provision by their signature, which has not yet been e. Then the staff will understand that everything is serious - they are asked to sign. After that, they will begin to use electronic signatures, become serious about their private keys, etc.
In addition to the psychological barrier, there is another - educational. It will be quite difficult for an experienced employee with experience who is several years away from retirement to explain what an electronic signature is and how to use it correctly. He relatively recently mastered working with regular e-mail, and here asynchronous cryptography, public and private keys, etc. This is the main problem that I encountered relatively recently on my own experience.
There is a solution, but it is not as simple as in the first case. At first, the task of learning to work with electronic signature can be placed on the shoulders of the IT department. If all else fails, then you can go to the services of third-party specialists. After all, there are trainings on working with computers, office applications, and e-mail. Similarly, you can find courses on modern workflow.
As with all innovations, you need to be ready for a wave of rejection. But when employees understand how good the electronic signature is, they will stop working in the old manner. In order to facilitate the transition to an electronic signature, it is necessary in the very situation described above to provide for a certain transitional period when it is still possible to use ordinary signatures. Just do not need to install too much time, otherwise everyone will continue to use the usual signatures.
There is another problem, but it is of a technical nature, therefore, it is solved quite simply. For the operation of an electronic signature, a certification authority (CA) for an electronic signature or certification authority is required. The law "On electronic signature" clearly states what a CA is:
Consequently, the certification authority will either have to create its own, or use external centers, for example, a CyberSafe certification authority.
The main task of CA is the issuance of cryptographic certificates and confirmation of their authenticity.
Before proceeding to the practical part of our article, you need to talk about the choice of software. Why choose CyberSoft products?
First, the development company has all the necessary licenses of the FSB and FSTEC, as you can see at:
cybersafesoft.com/eng/certificates
Secondly, the source code of the library, which is used by CyberSafe software products, is open to everyone and everyone can be convinced of the reliability of the solutions used in software products and that there are no “holes”, “loopholes”, backdoors and other misunderstandings in the program. Once the source code is posted on public display, it means that companies have nothing to hide. Try to find the source code of the same BitLocker from Microsoft.
Now a little specifics. The source code of the encryption library is available at:
www.assembla.com/spaces/cybersafe-encryption-library/wiki
A link to it is on the main page of the site cybersafesoft.com/rus .
For encryption and signing, the SMIME_OSSL_Sign () function is used, the code of which is shown in Listing 1. As you can see, the implementation uses OpenSSL, for which for many years there have been no complaints.
Listing 1. The SMIME_OSSL_Sign () function used to encrypt and sign a message / document
Thirdly, the CyberSafe Enterprise program can operate as a certification authority. Therefore, we can assume that you have already solved the third, technical problem.
The theory and any reasoning and thinking mean nothing without practice. Consider using CyberSafe to sign service documents. Install the CyberSafe program. When you first start the program, you must accept the certificate from CyberSoft CA. In principle, this is written in the program manual, but it is better to say this once again than not to accept the certificate.
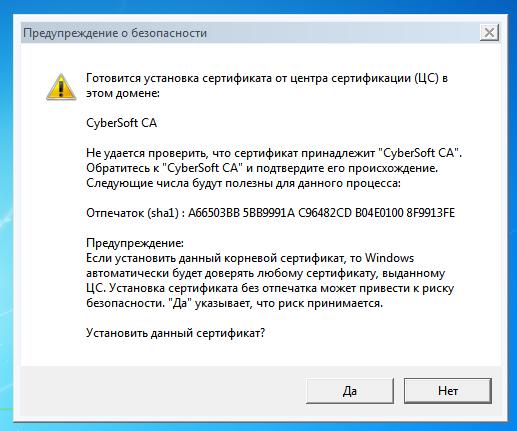
Fig. 1. First launch of the program
Next, go to Keys and Certificates, Private Keys and click the Create button. In the window that appears, enter your email address, password, your first and last name, so that your employees will immediately know who the certificate belongs to. Select the certificate validity period and key length. For powerful computers, it is better to choose the maximum key length, for not very powerful ones - 4096 bits. Remember, the longer the key, the more reliable the protection. Be sure to turn on the Publish checkbox , after creation - your certificate will be automatically published on the CyberSafe server and your employees will be able to easily find it. If you are not going to create your own certificate server or use some kind of external server, then publishing the certificate on the CyberSafe server is the best solution. If you rushed and did not turn on this switch, it does not matter: after creating a certificate, select it and click the Public button.
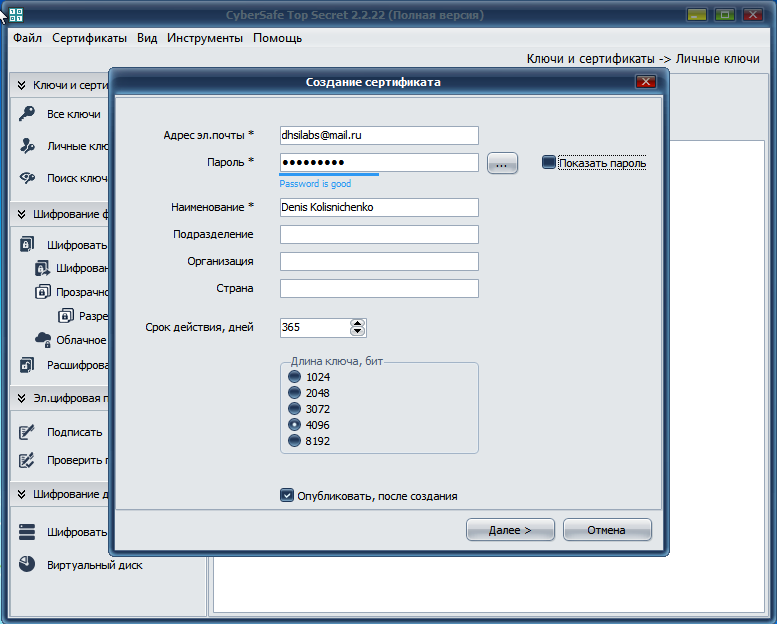
Fig. 2. Creating a certificate
Click Next and wait for the program to complete the certificate creation (Fig. 3).
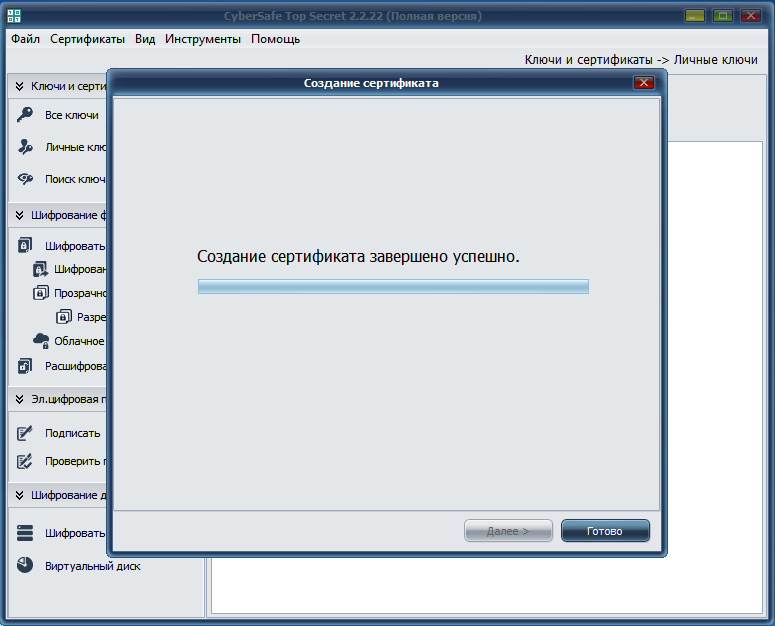
Fig. 3. Certificate created
Click Finish . Then the program will ask you to confirm your e-mail. A confirmation code will be sent to it, which will need to be entered in the appeared window (Fig. 4).

Fig. 4. Enter the confirmation code to publish the certificate
Then you will receive a message that the certificate has been successfully published (Fig. 5). I think it is not necessary to say that Internet access is required to publish a certificate on the CyberSafe server.

Fig. 5. Certificate successfully published
Your colleagues also need to install CyberSafe and go through the process of creating a certificate and publishing it on the CyberSafe server. To search for the certificate of a colleague by his e-mail, click the Search button and enter the e-mail (Fig. 6). Next you need to add the certificate of your colleague, and he needs to add your certificate.

Fig. 6. Adding a colleague certificate
Look at the pic. 7. Your certificate is displayed in the list as a pair of keys - public and private key. Colleagues added using the Search button will appear as a single key and contain only the public (public) keys of your colleagues.

Fig. 7. List of keys and certificates
Now we will try to encrypt and sign a service note. Create a memo in any text editor. This may be Word, or maybe just Notepad - the essence of this will not change.
Go to the Email section . digitally sign, sign and click add. files . Select the previously created service memo (Fig. 8). You can select several files at once or even the entire folder (using the Add. Folder button), but now for the sake of simplicity, we will work with one file. Select it and click Next .
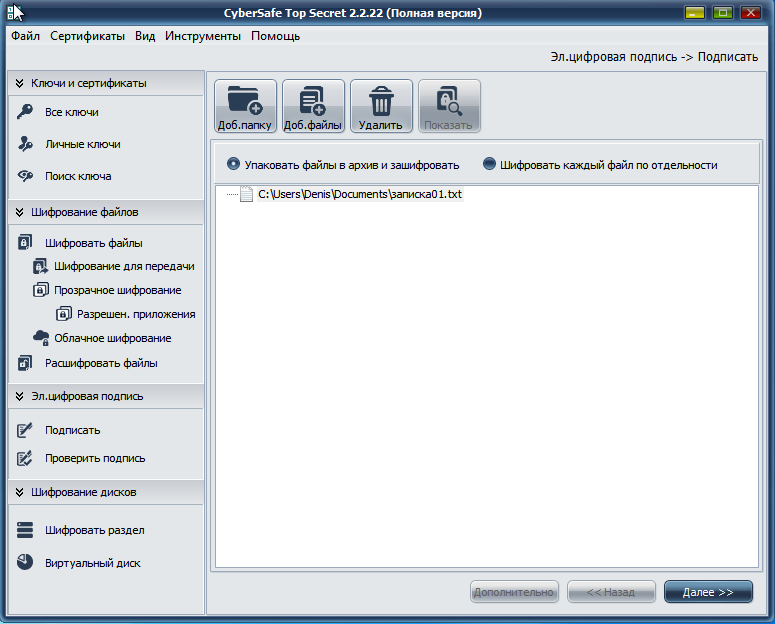
Fig. 8. Added Memo
Select file encryption option - Encrypt files with recipient keys (Fig. 9). This means that recipients' public keys will be used to encrypt the file. If you do not select your key, even you will not be able to decrypt this file, despite the fact that you encrypted it (Fig. 10).
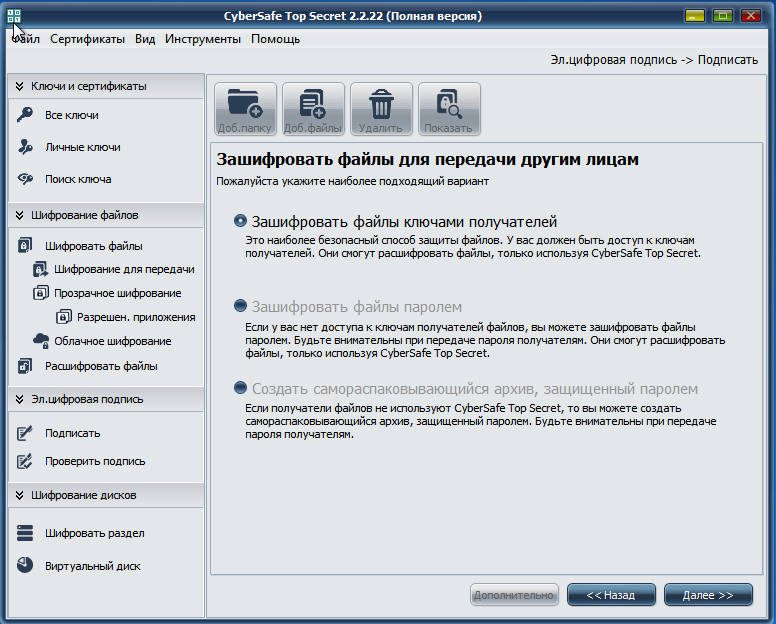
Fig. 9. Encrypting files for transfer to others
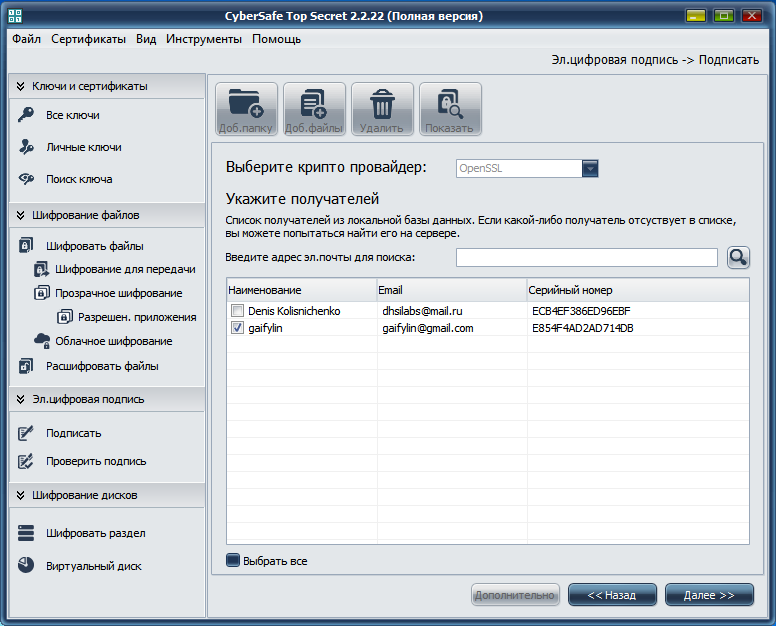
Fig. 10. Select file recipients
For the experiment, I did not choose my certificate (Fig. 10) and when I tried to decrypt the file that I had just encrypted, I received the message Error decrypting the file! Perhaps the file is encrypted with another key .
Further from the list Sign with private key you need to choose your key so that the program signs notes on your behalf. You can choose an encryption algorithm and key length. To start encryption, click the Cipher button . The program will report that our file is encrypted successfully (Fig. 12). From fig. 12 shows who signed the document and to whom it is intended (who can read it).
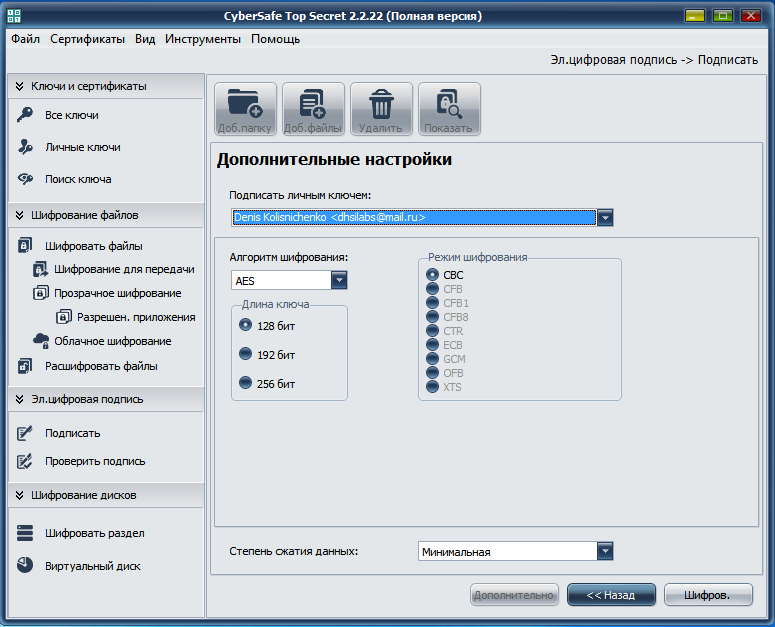
Fig. 11. Sign the note with your key
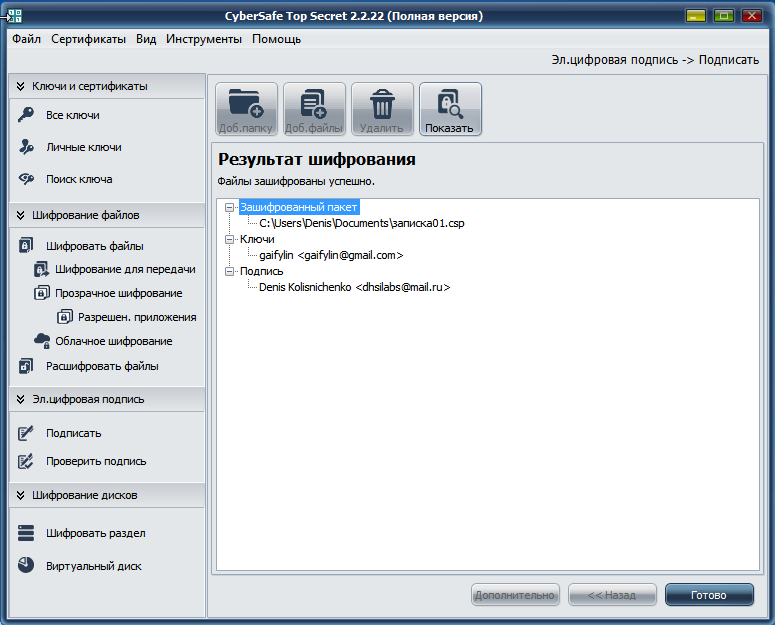
Fig. 12. The note is encrypted
As you can see, we not only signed the service memo, but also protected it from other users. No one except the users selected as recipients will be able to read it.
The package containing the encrypted service note will be placed in the directory with the source file, the package name will be the same as the file being encrypted (in our case, note01), and the extension will be csp. This file (with the extension .csp) must be transferred to recipients, for example, sent by e-mail or transferred in some other way.
Let's see how the recipient can open it, decrypt the files in the package and verify your signature. The recipient should start the CyberSafe program, go to the Email section . digital signature, Verify signature , click Add. files and select the package (file with the extension .csp). In the field above, you can select the folder in which the decrypted files will be placed (Fig. 13).
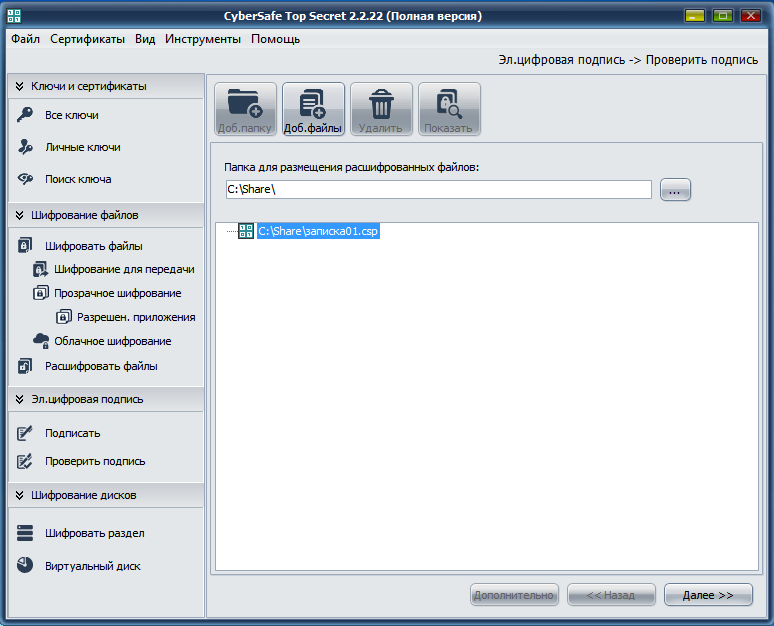
Fig. 13. Selecting the .csp package
Then you need to click the Next button and select a certificate for decryption. Since the package was addressed to your colleague, he must select his certificate (Fig. 14). After clicking the Next button, the program will ask you to enter the certificate password. If the password is correct, the program will decrypt the files and report that the decryption was successful (Fig. 15).
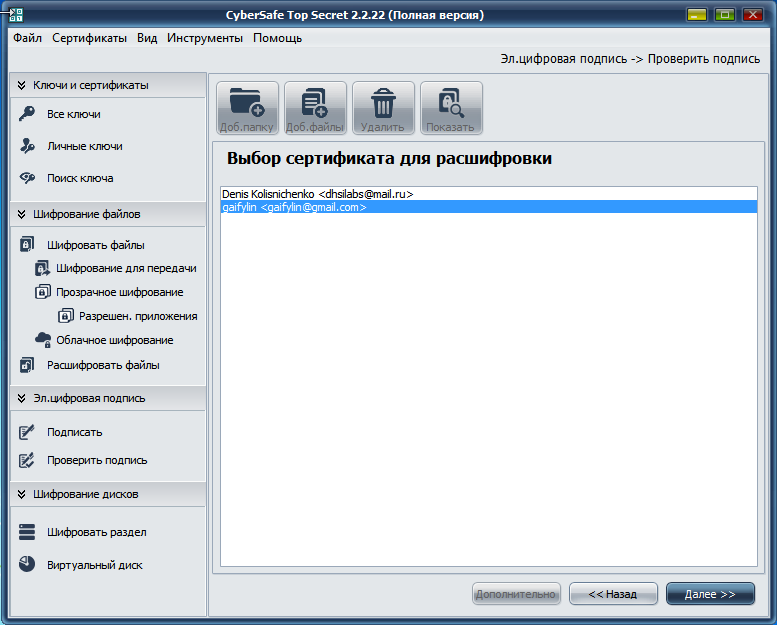
Fig. 14. Choosing a certificate

Fig. 15. Files decrypted successfully
You also need to check the signature to make sure that no one has replaced the package during its transmission. To do this, click Check Signature . Since the program accesses the certificate authority when verifying the signature, you need access to the Internet to verify the signature. The result of the signature verification is shown in Fig. 16 - the signature is verified, the certificate is trusted and is not on the list of revoked, and the package has not been modified after signing.
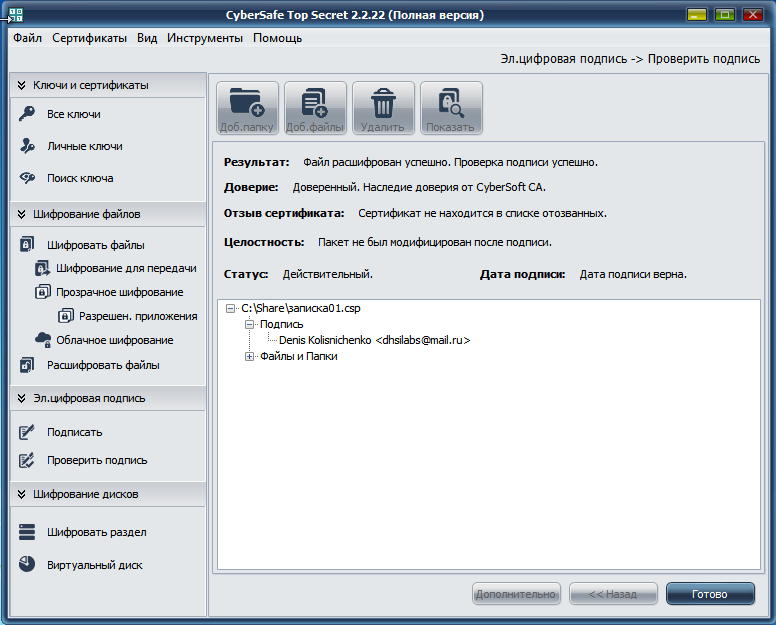
Fig. 16. Everything is good
Now let's see how the program responds to a non-standard situation. Imagine that someone modified the note package01.csp. The program will report an error and refuse to decrypt the files (Fig. 17).
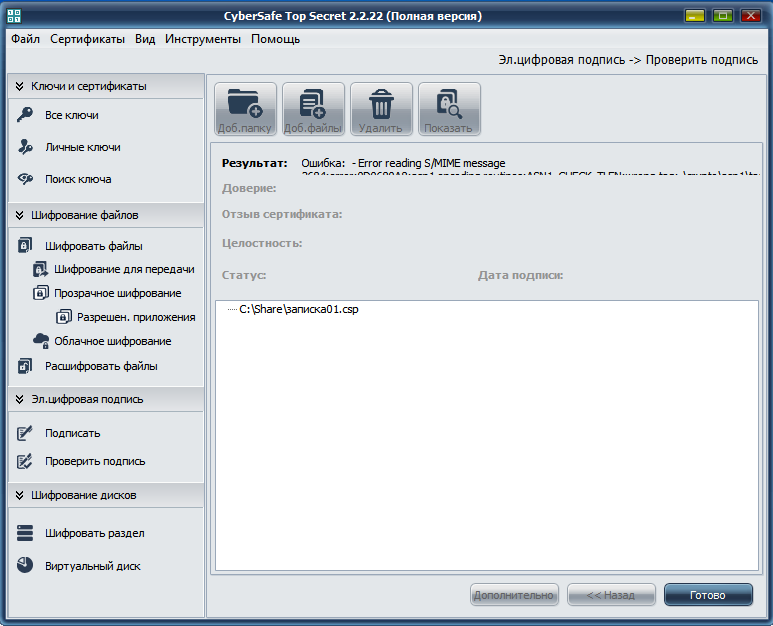
Fig. 17. Error
If the method of brute force does not work, then the attacker, having made his way to your colleague’s computer at lunchtime, can go another way. He can delete the certificate issued for your colleague's e-mail (gaifylin@gmail.com), and create it again for the same e-mail and try to decrypt the memo. The logic is simple - he cannot use the certificate of your colleague, because he does not know his password, but he can delete it and create a certificate for the same e-mail. However, he will fail, because he can create at least one hundred certificates for one e-mail - the one that was first published on the CyberSafe key server will be considered trusted. He creates a certificate, enters a password from him that was specified when it was created, but, alas, he will not be able to read the service note (Fig. 18).
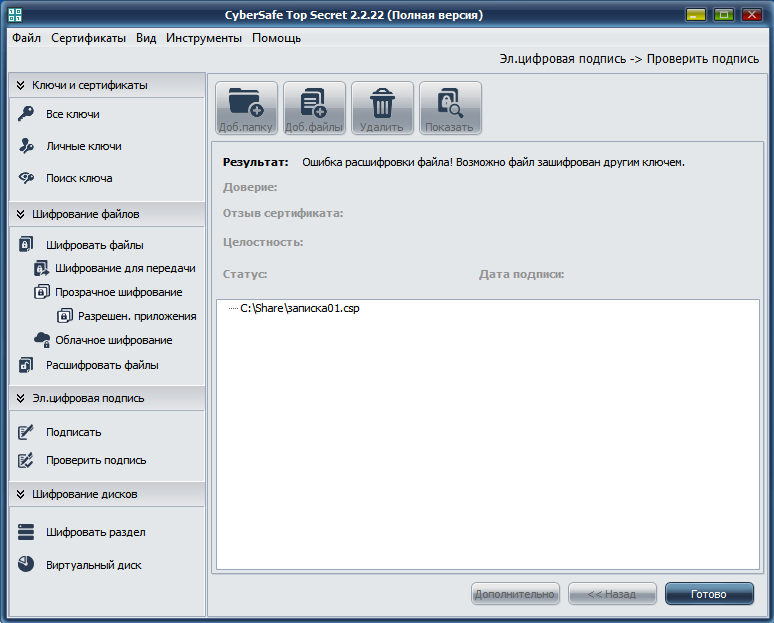
Fig. 18. Error decrypting file! The file may be encrypted with another key.
So, we have just encrypted and signed a service memo and we learned from our own experience that the program really works and protects your data from unauthorized reading and alteration.
From all that has been written earlier, it can be concluded that ES is a very useful innovation in the enterprise, since enterprises will have the following advantages when using ES:
The whole system described above will fit only for commercial organizations, but it cannot be used for state-owned enterprises, where a certified crypt-provider is needed. Also, the described system can be used between different organizations for any documents, if the parties have agreed to consider the keys and CAs to be trusted.
It is worth noting that the current version of CyberSafe is not a full-fledged corporate version, since at the moment there is no centralized issuance and distribution of keys. Therefore, in this version, the encryption administrator can generate keys and certificates and write users to tokens (which will be discussed in the second part of the article). A full corporate version is expected by mid-2015.
This ends the first part of the article. In the second part, we’ll talk about the use of electronic signatures in state organizations and banks. We will talk about the use of certified cryptographic provider and tokens. In principle, everything that will be discussed in the second part of the article can also be used in commercial enterprises, if necessary.
Federal Law of April 6, 2011 No. 63- (as amended on June 28, 2014) “On Electronic Signature”
Comparison of different versions of CyberSafe
What is an electronic signature?
This part of the article focuses on the use of electronic signatures in a commercial enterprise. First, we will consider when the electronic signature will be useful and useful at every enterprise, and then we will consider its practical use.
First of all, you need to say what an electronic signature is. This is information that is attached to other information (to the information to be signed) in order to determine the person who signed the information, as well as the fact that the information remains unchanged after it is signed.
The Law on Electronic Signature itself states the following: “electronic signature is information in electronic form that is attached to other information in electronic form (signed information) or otherwise associated with such information and which is used to determine the person signing the information” .
Thus, the main task of the electronic signature is to establish the authorship of the document and ensure that the document has not been changed after its signing.
')
If you delve into the law "On electronic signature", then the electronic signature is simple and strengthened. A simple electronic signature confirms only the fact of electronic signing of a document by a certain person.
Strengthened electronic signature, in turn, is divided into reinforced unqualified and reinforced qualified. Reinforced unqualified electronic signature allows you to:
- Identify the person who signed the electronic document;
- Determine whether the document was changed after signing (which is not possible with a simple electronic signature).
Also, enhanced unqualified ES should be obtained as a result of cryptographic transformation of information using an electronic signature key.
Reinforced qualified ES is the same as reinforced unqualified, but the ES verification key is specified in the qualified certificate, and means are used to create and verify the ES that receive confirmation of compliance with the requirements established by the Law On Electronic Signature. The CyberSafe program, considered further, offers just the option of enhanced qualified electronic signature.
Cases of the use of electronic signature in the enterprise
Internal document flow
The most common variant of the internal workflow of the enterprise - this service notes. It makes no sense to print the document and sign it personally if you can digitally sign it and send it further down the chain.
The electronic signature here saves not only time but also money - the consumption of paper and printer toner is reduced. Of course, the cost of one printed sheet of paper may not be very high, but for the year you can save quite a decent amount, and this is not to mention the time, which today is expensive.
Typically, the company uses network printers. Network printer can be located in another office or even on another floor. The employee who has printed the service note needs to leave his office, get to the printer and find his note among the other documents. 10-15 minutes are spent on everything about everything, and if we take into account the human factor (conversations with employees in the next room), then much more. As a result, these 10-15 minutes could be spent more productively than searching for a printed document.
The second example is the process of negotiating a contract. Imagine that an employee Ivanov prepares a contract and sends it for approval to the head. The principle is the same as with the memo - why waste time on printing a dialect, if you can sign it with an electronic signature? The head makes changes to the contract, signs it and sends it to Ivanova. Considering that there will be a lot of changes (after all, mistakes are inevitable anyway), the use of an electronic signature again saves a lot of time and money.
In large corporate networks, where a manager and even an ordinary employee Ivanov can have detractors, an electronic signature is a reliable way to verify the authorship of the document and its immutability (that no one without Ivanov’s knowledge or his manager made any changes to it).
You can argue that they have access rights and you can see who last edited the document. Why do we need an electronic signature? Everything seems to be correct, if not for one thing. In any system, there is a user with maximum rights - the administrator, who can not only change the document itself, but also its attributes (including the time / date of the change, the author of the last change, etc.).
Exchange documents with affiliates and partners
When exchanging information with remote branches and partners of the company, email is usually used. And here you can use an electronic signature so that your partners and employees of remote branches can be sure that this message was sent precisely by you, and not by someone who wants to appear to you.
Yes, there is no practice of concluding contracts in full in electronic form. A wet seal and signature is still needed. Therefore, to seal the contract with a partner in a fully electronic form will not work. But then you can safely exchange messages with your partners and have no doubt that someone will forge your message or the message of a partner.
As for the exchange of documents with remote branches, then you can use an electronic signature, as in the internal document management. Now the document flow between branches takes place in semi-digital form. Namely: the document must first be printed out, then the manager must sign it, after which the secretary of the manager scans it and sends it by e-mail to a remote branch office, where it is printed again.
The electronic signature allows you to reduce this process: the document is signed with an electronic signature and sent to a remote branch where the recipient can verify the electronic signature and make sure that the document was signed by the manager.
Some problems of introducing electronic signature in an enterprise
It is still difficult for a person to get used to an electronic signature and is not treated as something serious. While on the document will not be "wet" his signature, still, do not consider it signed. Employees will still use copies of paper documents, lose their private keys, not considering them something important. How to overcome the psychological barrier? How to overcome the very “without a piece of paper - you're a bug, and with a piece of paper - a man”?
It turns out that there is a way out and it consists in another piece of paper. It is necessary inside the company to adopt "the provision on electronic document circulation". All employees must familiarize themselves with it and affirm the adoption of this provision by their signature, which has not yet been e. Then the staff will understand that everything is serious - they are asked to sign. After that, they will begin to use electronic signatures, become serious about their private keys, etc.
In addition to the psychological barrier, there is another - educational. It will be quite difficult for an experienced employee with experience who is several years away from retirement to explain what an electronic signature is and how to use it correctly. He relatively recently mastered working with regular e-mail, and here asynchronous cryptography, public and private keys, etc. This is the main problem that I encountered relatively recently on my own experience.
There is a solution, but it is not as simple as in the first case. At first, the task of learning to work with electronic signature can be placed on the shoulders of the IT department. If all else fails, then you can go to the services of third-party specialists. After all, there are trainings on working with computers, office applications, and e-mail. Similarly, you can find courses on modern workflow.
As with all innovations, you need to be ready for a wave of rejection. But when employees understand how good the electronic signature is, they will stop working in the old manner. In order to facilitate the transition to an electronic signature, it is necessary in the very situation described above to provide for a certain transitional period when it is still possible to use ordinary signatures. Just do not need to install too much time, otherwise everyone will continue to use the usual signatures.
There is another problem, but it is of a technical nature, therefore, it is solved quite simply. For the operation of an electronic signature, a certification authority (CA) for an electronic signature or certification authority is required. The law "On electronic signature" clearly states what a CA is:
Certification Authority - a legal entity or an individual entrepreneur performing the functions of creating and issuing certificates of keys for verification of electronic signatures, as well as other functions stipulated by this Federal Law
Consequently, the certification authority will either have to create its own, or use external centers, for example, a CyberSafe certification authority.
The main task of CA is the issuance of cryptographic certificates and confirmation of their authenticity.
Practical part
Before proceeding to the practical part of our article, you need to talk about the choice of software. Why choose CyberSoft products?
First, the development company has all the necessary licenses of the FSB and FSTEC, as you can see at:
cybersafesoft.com/eng/certificates
Secondly, the source code of the library, which is used by CyberSafe software products, is open to everyone and everyone can be convinced of the reliability of the solutions used in software products and that there are no “holes”, “loopholes”, backdoors and other misunderstandings in the program. Once the source code is posted on public display, it means that companies have nothing to hide. Try to find the source code of the same BitLocker from Microsoft.
Now a little specifics. The source code of the encryption library is available at:
www.assembla.com/spaces/cybersafe-encryption-library/wiki
A link to it is on the main page of the site cybersafesoft.com/rus .
For encryption and signing, the SMIME_OSSL_Sign () function is used, the code of which is shown in Listing 1. As you can see, the implementation uses OpenSSL, for which for many years there have been no complaints.
Listing 1. The SMIME_OSSL_Sign () function used to encrypt and sign a message / document
function SMIME_OSSL_Sign (
AFileSpec, ACertFileSpec: String;
out ErrMesg: String;
SMIME: Boolean = False): Boolean;
function getCertInfo (certSpec: String; var ACert: PX509; var AKey: PEVP_PKEY): Boolean;
var
tbio: PBIO;
cert: PX509;
key: PEVP_PKEY;
begin
Result: = False;
tbio: = nil;
// Read certificate and private key
// must contain "BEGIN \ END CERTIFICATE" and "BEGIN \ END RSA PRIVATE KEY"
tbio: = BIO_new_file (PAnsiChar (AnsiString (certSpec)), 'r');
if tbio = nil then
Exit;
try
ACert: = PEM_read_bio_X509 (tbio, nil, nil, nil);
BIO_reset (tbio);
AKey: = PEM_read_bio_PrivateKey (tbio, nil, nil, nil {PAnsiChar (pass)});
Result: = (ACert <> nil) and (AKey <> nil);
finally
if Assigned (tbio) then
BIO_free (tbio);
end;
end;
var
scert: array of PX509;
skey: array of PEVP_PKEY;
i: Integer;
inf,
outf: PBIO;
certs: TStringList;
cms: PCMS_ContentInfo;
outFileSpec: String;
flags: Cardinal;
begin
Result: = False;
SSL_InitBIO;
SSL_InitEVP;
SSL_InitPEM;
SSL_initSk;
SSL_InitPKCS7;
SSL_InitCMS;
SSL_InitERR;
SSL_InitX509;
OPENSSL_add_all_algorithms_noconf ();
OpenSSL_add_all_ciphers;
OpenSSL_add_all_digests;
ERR_load_crypto_strings ();
certs: = TStringList.Create;
try
StrToStrings (ACertFileSpec, ',', certs);
if certs.Count = 0 then
begin
ErrMesg: = stNoSignCertificates;
Exit;
end;
SetLength (scert, certs.Count);
SetLength (skey, certs.Count);
for i: = 0 to certs. Count - 1 do
begin
scert [i]: = nil;
skey [i]: = nil;
end;
// Open content being signed
inf: = BIO_new_file (PAnsiChar (AnsiString (AFileSpec)), 'r');
if (inf = nil) then
begin
ErrMesg: = Format (stErrorOpenFile, [AFileSpec]);
Exit;
end;
flags: = CMS_BINARY or CMS_PARTIAL or CMS_STREAM;
cms: = CMS_sign (nil, nil, nil, inf, flags);
if (cms = nil) then
begin
ErrMesg: = Format (stErrorSignFile, [AFileSpec]);
Exit;
end;
for i: = 0 to certs. Count - 1 do
if getCertInfo (certs.Strings [i], scert [i], skey [i]) then
begin
if CMS_add1_signer (cms, scert [i], skey [i], nil, 0) = nil then
begin
ErrMesg: = stErrorAddSigner;
Exit;
end;
end;
outFileSpec: = GetTmpFileSpec;
outf: = BIO_new_file (PAnsiChar (AnsiString (outFileSpec)), 'w');
if (outf = nil) then
begin
ErrMesg: = Format (stErrorCreateSignedFile, [AFileSpec]);
Exit;
end;
// Display the message S / MIME
{if SMIME_write_CMS (outf, cms, inf, flags) = 0 then
begin
ErrMesg: = Format (stErrorWriteFile, [outFileSpec]);
Exit;
end;
}
if i2d_CMS_bio_stream (outf, cms, inf, flags) = 0 then
begin
ErrMesg: = Format (stErrorWriteFile, [outFileSpec]);
Exit;
end;
finally
if Assigned (cms) then
CMS_ContentInfo_free (cms);
if Assigned (inf) then
BIO_free (inf);
if Assigned (outf) then
BIO_free (outf);
for i: = 0 to certs. Count - 1 do
begin
if Assigned (scert [i]) then
X509_free (scert [i]);
if Assigned (skey [i]) then
EVP_PKEY_free (skey [i]);
scert [i]: = nil;
skey [i]: = nil;
end;
certs.Free;
end;
if FileExists (outFileSpec) then
begin
try
DeleteFile (AFileSpec);
CheckCopyFile (outFileSpec, AFileSpec);
DeleteFile (outFileSpec);
Result: = True;
except
on E: Exception do
ErrMesg: = E.Message;
end;
end;
if not result then
begin
ErrMesg: = Format (stErrorSignFile, [AFileSpec]);
end;
end;
Thirdly, the CyberSafe Enterprise program can operate as a certification authority. Therefore, we can assume that you have already solved the third, technical problem.
The theory and any reasoning and thinking mean nothing without practice. Consider using CyberSafe to sign service documents. Install the CyberSafe program. When you first start the program, you must accept the certificate from CyberSoft CA. In principle, this is written in the program manual, but it is better to say this once again than not to accept the certificate.

Fig. 1. First launch of the program
Next, go to Keys and Certificates, Private Keys and click the Create button. In the window that appears, enter your email address, password, your first and last name, so that your employees will immediately know who the certificate belongs to. Select the certificate validity period and key length. For powerful computers, it is better to choose the maximum key length, for not very powerful ones - 4096 bits. Remember, the longer the key, the more reliable the protection. Be sure to turn on the Publish checkbox , after creation - your certificate will be automatically published on the CyberSafe server and your employees will be able to easily find it. If you are not going to create your own certificate server or use some kind of external server, then publishing the certificate on the CyberSafe server is the best solution. If you rushed and did not turn on this switch, it does not matter: after creating a certificate, select it and click the Public button.

Fig. 2. Creating a certificate
Click Next and wait for the program to complete the certificate creation (Fig. 3).

Fig. 3. Certificate created
Click Finish . Then the program will ask you to confirm your e-mail. A confirmation code will be sent to it, which will need to be entered in the appeared window (Fig. 4).

Fig. 4. Enter the confirmation code to publish the certificate
Then you will receive a message that the certificate has been successfully published (Fig. 5). I think it is not necessary to say that Internet access is required to publish a certificate on the CyberSafe server.

Fig. 5. Certificate successfully published
Your colleagues also need to install CyberSafe and go through the process of creating a certificate and publishing it on the CyberSafe server. To search for the certificate of a colleague by his e-mail, click the Search button and enter the e-mail (Fig. 6). Next you need to add the certificate of your colleague, and he needs to add your certificate.

Fig. 6. Adding a colleague certificate
Look at the pic. 7. Your certificate is displayed in the list as a pair of keys - public and private key. Colleagues added using the Search button will appear as a single key and contain only the public (public) keys of your colleagues.

Fig. 7. List of keys and certificates
Now we will try to encrypt and sign a service note. Create a memo in any text editor. This may be Word, or maybe just Notepad - the essence of this will not change.
Go to the Email section . digitally sign, sign and click add. files . Select the previously created service memo (Fig. 8). You can select several files at once or even the entire folder (using the Add. Folder button), but now for the sake of simplicity, we will work with one file. Select it and click Next .

Fig. 8. Added Memo
Select file encryption option - Encrypt files with recipient keys (Fig. 9). This means that recipients' public keys will be used to encrypt the file. If you do not select your key, even you will not be able to decrypt this file, despite the fact that you encrypted it (Fig. 10).

Fig. 9. Encrypting files for transfer to others

Fig. 10. Select file recipients
For the experiment, I did not choose my certificate (Fig. 10) and when I tried to decrypt the file that I had just encrypted, I received the message Error decrypting the file! Perhaps the file is encrypted with another key .
Further from the list Sign with private key you need to choose your key so that the program signs notes on your behalf. You can choose an encryption algorithm and key length. To start encryption, click the Cipher button . The program will report that our file is encrypted successfully (Fig. 12). From fig. 12 shows who signed the document and to whom it is intended (who can read it).

Fig. 11. Sign the note with your key

Fig. 12. The note is encrypted
As you can see, we not only signed the service memo, but also protected it from other users. No one except the users selected as recipients will be able to read it.
The package containing the encrypted service note will be placed in the directory with the source file, the package name will be the same as the file being encrypted (in our case, note01), and the extension will be csp. This file (with the extension .csp) must be transferred to recipients, for example, sent by e-mail or transferred in some other way.
Let's see how the recipient can open it, decrypt the files in the package and verify your signature. The recipient should start the CyberSafe program, go to the Email section . digital signature, Verify signature , click Add. files and select the package (file with the extension .csp). In the field above, you can select the folder in which the decrypted files will be placed (Fig. 13).

Fig. 13. Selecting the .csp package
Then you need to click the Next button and select a certificate for decryption. Since the package was addressed to your colleague, he must select his certificate (Fig. 14). After clicking the Next button, the program will ask you to enter the certificate password. If the password is correct, the program will decrypt the files and report that the decryption was successful (Fig. 15).

Fig. 14. Choosing a certificate

Fig. 15. Files decrypted successfully
You also need to check the signature to make sure that no one has replaced the package during its transmission. To do this, click Check Signature . Since the program accesses the certificate authority when verifying the signature, you need access to the Internet to verify the signature. The result of the signature verification is shown in Fig. 16 - the signature is verified, the certificate is trusted and is not on the list of revoked, and the package has not been modified after signing.

Fig. 16. Everything is good
Now let's see how the program responds to a non-standard situation. Imagine that someone modified the note package01.csp. The program will report an error and refuse to decrypt the files (Fig. 17).

Fig. 17. Error
If the method of brute force does not work, then the attacker, having made his way to your colleague’s computer at lunchtime, can go another way. He can delete the certificate issued for your colleague's e-mail (gaifylin@gmail.com), and create it again for the same e-mail and try to decrypt the memo. The logic is simple - he cannot use the certificate of your colleague, because he does not know his password, but he can delete it and create a certificate for the same e-mail. However, he will fail, because he can create at least one hundred certificates for one e-mail - the one that was first published on the CyberSafe key server will be considered trusted. He creates a certificate, enters a password from him that was specified when it was created, but, alas, he will not be able to read the service note (Fig. 18).

Fig. 18. Error decrypting file! The file may be encrypted with another key.
So, we have just encrypted and signed a service memo and we learned from our own experience that the program really works and protects your data from unauthorized reading and alteration.
findings
From all that has been written earlier, it can be concluded that ES is a very useful innovation in the enterprise, since enterprises will have the following advantages when using ES:
- The ability to protect documents from unauthorized reading and changes
- Reduction of paper workflow due to the transfer of part of internal documents into electronic form
- The ability to determine the legal status of the document on ES (to establish the authorship of the document).
The whole system described above will fit only for commercial organizations, but it cannot be used for state-owned enterprises, where a certified crypt-provider is needed. Also, the described system can be used between different organizations for any documents, if the parties have agreed to consider the keys and CAs to be trusted.
It is worth noting that the current version of CyberSafe is not a full-fledged corporate version, since at the moment there is no centralized issuance and distribution of keys. Therefore, in this version, the encryption administrator can generate keys and certificates and write users to tokens (which will be discussed in the second part of the article). A full corporate version is expected by mid-2015.
This ends the first part of the article. In the second part, we’ll talk about the use of electronic signatures in state organizations and banks. We will talk about the use of certified cryptographic provider and tokens. In principle, everything that will be discussed in the second part of the article can also be used in commercial enterprises, if necessary.
Links
Federal Law of April 6, 2011 No. 63- (as amended on June 28, 2014) “On Electronic Signature”
Comparison of different versions of CyberSafe
Source: https://habr.com/ru/post/247019/
All Articles