Top10 non-standard IT security events 2014
 In our working terminology, there is one well-established English phrase "threat landscape". It is not normally translated into Russian (threat landscape, yeah). If everything is extremely simplified, then it is such a thing, on the basis of which companies make a choice: to buy more hardware or spend money to protect the existing infrastructure. The dependence here is direct: if your trains constantly go off the rails, then this is not decided at all by purchasing new locomotives.
In our working terminology, there is one well-established English phrase "threat landscape". It is not normally translated into Russian (threat landscape, yeah). If everything is extremely simplified, then it is such a thing, on the basis of which companies make a choice: to buy more hardware or spend money to protect the existing infrastructure. The dependence here is direct: if your trains constantly go off the rails, then this is not decided at all by purchasing new locomotives.Assessing the landscape (well, again) on a scale from friendly to gloomy can be different. Here, for example, is the version from our security experts: the results of 2014 , the forecast for 2015, and, for fans of numbers, numbers . What do the companies themselves think? We regularly ask them about it (more here ), but this year we decided to use another non-standard method.
We monitor all relevant news in the field of IT-security, we are engaged in editing the site Threatpost . We decided to select 10 events of the outgoing year (for the English version of the site) by a single criterion: the popularity of the relevant articles. And we received an interesting set of news relevant for IT professionals, our current and potential customers and security guards. It has absolutely no politics (that is, stories about Snowden and the NSA), and quite a few topics on the strategic plan. But on the foreground came the problems that need to be taken into account when assessing this very landscape now. Read more - under the cut.
10th place. TrueCrypt: the first (conditionally) verified distribution after the May epic failure
News The drama is in the details .
')
“There is such a thing. TrueCrypt is unsafe, but we will not tell you why. Use standard encryption in Windows. And we say goodbye. " In the free interpretation, the message on the website of the developers of the popular encryption system TrueCrypt sounded like this (and still hangs there, by the way). When you choose a security system (and no matter whether paid or free, encryption or antivirus), you evaluate the convenience, functionality, and arguments of the effectiveness of a particular security approach. But first of all, you should trust it, as it is too expensive to audit the code yourself (even if it is available).
In the case of TrueCrypt, we dealt with a really effective, simple and free encryption tool, which, in addition, was developed by an anonymous group of authors. Until now, it is unclear what exactly happened: either an incurable bug really showed up, or the authorities recommended covering the shop, or just tired of coding. More than half a year has passed since the closure of the project, and it seems that we will not know the whole truth.
All hope is only for the collective initiative of the Open Crypto Audit Project , the purpose of which, as applied to TrueCrypt, is exactly that code audit (and not only). At the end of June, a verified distribution of TrueCrypt version 7.1a was posted on GitHub. Does this mean that the holes were not found and everything is fine? Alas, no, this is still far away. So far, we have managed to make sure that the source code and builds of this version are, ummm, really source codes and builds of this version. It is the code of version 7.1a that was investigated in the first part of the audit (the results were published in April). We are waiting for updates that can be monitored, for example, here .
9th place. UltraDNS DDoS Attack
News
The April attack on the UltraDNS service with a capacity of up to 100 gigabits per second using the DNS Amplification method led to the inaccessibility of the company's clients (among which, for example, the Forbes magazine website) for several hours. It seems to be nothing special, especially compared to other DDoS attacks of this year, with a capacity of up to 400 Gb / s (already using vulnerabilities in the NTP protocol). The problem is that such attacks have become the norm. Unlike the most complex attacks, sometimes aimed at single targets (for example, see our latest Regin campaign report , 27 victims), DDoS is a universal problem. According to our data, at least 18% of companies have already encountered DDoS. And if, for example, spam (problem number one) causes indirect damage, then the loss from the inaccessibility of the website is direct and results in lost sales and loss of reputation. The trend of this year was just “shoulder” attacks, using holes in the fundamental network protocols, as well as combining DDoS and targeted attacks on AKA “stun and steal wallet”. We will return to this topic today.
In topic: A detailed description of the DDoS-Trojan for Linux.

Targeted attack Dark Hotel - a non-trivial way to steal data from employees on a business trip.
8th place. Bypass lock system in iOS 7.1.1
News
The April update of iOS 7.1.1, as well as the patch for Mac OS X, actually closes a serious hole in the Apple implementation of the SSL protocol (but not this one ). As is often the case, the old bugs were replaced by new ones, one of which allowed partially bypassing the blocking system on the Apple iPhone 5 / 5s, and accessing the address book. It is noteworthy that the traditional scheme of such hacks "quickly press different buttons and poke the screen in various ways" this time the Siri voice assistant was turned on.
As we all know, any news about Apple is a powerful traffic generator, so the holes in the Apple devices simply had to get into our rating. As in the case of UltraDNS, it’s not the vulnerability itself that is indicative, but the industry’s attention to mobile devices: companies increasingly see them as a threat, although they understand that it’s not possible to “take and prohibit” using smartphones at work.
According to our data, in 22% of companies have already encountered security problems associated with theft or loss of mobile phones. Any bypass of the security system in such a situation is a problem. Especially if corporate smartphones were not really protected. Or if the security systems did not work. Along with the lock bypass, another problem was discovered in the same version of iOS: mail encryption did not apply to attachments. Access to the file system of the phone provided access to attachments, which, you see, is somehow not correct.

Epic Turla is a March study of complex relationships between different APTs.
7th place. Broken internet, behave accordingly
News
If I were asked non-verbally to convey the status of security on the Internet with the help of two music videos, I would do it this way (we’ll like your options in the comments, let's talk about music and associations).
Desired state of affairs:
The real state of affairs:
Verbally, the state of security on the Internet was expressed in February of this year by the head of our team of experts Kostin Raju: the Internet is broken. This is not paranoia, not FUD, not advertising: this is the case. Wherever you look, there are large-scale and poorly treatable problems everywhere: with critical network protocols, with encryption, with mail, with the web, and with everything.
What to do? Going back to typewriters and other cyberpunk will not help , it’s like making a bet on horse craving at the dawn of a car boom. It is necessary to take this fact into account and build a protection strategy accordingly. "You have not closed there ... but an open fracture!" Consider this sad fact and go back to the details.
6th place. Tor Nox
News
Another interesting story about the credibility of security systems, in this case: the anonymity tool. At the end of October, researcher Josh Pitts discovered an output Tor host that, on the fly, added malicious code to any executable file downloaded by the user. The node located in Russia was promptly blocked by the network administration. The way to protect against such hacks is clear: do not trust anyone. More specifically: another layer of encryption never hurts. HTTPS traffic was naturally not affected by this hack.

Cross-platform (Windows, Max OS X, Linux, iOS) spy campaign The Mask / Careto .
5th place. DDoS + Targeted Attack. Defeat Code Spaces
News
When the American retail network Target stole data from 70 million customers, it was unpleasant, but the shops and goods in them remained in place. If your business is 100% networked, then a targeted attack can destroy it entirely overnight. This is exactly what happened in June of this year with Code Spaces, which sold its own joint development and version tracking system.
The initial DDoS attack on the company's servers was followed by hacking the Amazon EC2 control panel, and then they started extorting money from the service creators. The attempt to restore access was unsuccessful: the hacker re-gained control and deleted almost all the data. Within 12 hours the company was destroyed: it was impossible to restore the data and repair the damage, and most importantly, restore the reputation.
In the old version of the Code Spaces website, special attention was paid to the reliability of data backup. “A simple backup does not make sense without a clear recovery plan after a failure, which has been tested in practice and has repeatedly proven its efficiency.” Gold words!
4th place. POOOOODLE
News
The fashionable trend in IT security this year is to invent non-standard names not only for malware, but also for vulnerabilities or specific attack scenarios. In this case, POODLE is short for Padding Oracle On Downgraded Legacy Encryption. The essence of the attack: make the client and server, when establishing a secure connection, make a downgrade from a secure (TLS) protocol to an insecure and outdated one (SSL 3.0, which marks the coming of age this year). As a result, under certain conditions, it is possible to intercept protected traffic and, for example, stealing a cookie and then intercepting a session. The conditions for the attack are so specific that real cases of exploitation have not been fixed. However, during October, the developers of the main browsers released an update, completely disabling SSLv3, which solves the problem. Of all the unpleasant news of 2014, this one looks the most positive: they found a hole, promptly closed the hole.
3rd place. Shellshock
News Background The development of events . FAQ .
$ env 'x = () {:;}; echo vulnerable '' BASH_FUNC_x () = () {:;}; echo vulnerable 'bash -c "echo test"
Another victim of creative naming (but you must admit, Shellshock sounds more interesting than CVE-2014-6271 ), this time is a serious bug in the universal command shell for Unix-based operating systems. The second after the bug in OpenSSL is the case when the question “which systems are subject to it” can be answered with “yes, everything!”, And even not very much to lie. Shellshock is being actively exploited, the search for vulnerable systems is perfectly scaled , and the administrators of the affected servers have again got a chance to play the game “how to fix everything and not break anything”.
In the wake of the story of Shellshock and Heartbleed, we received a lot of feedback from our customers, and I particularly wanted to point out the difficulties that small business is experiencing with such vulnerabilities. If a large company can easily allocate a noticeable resource for finding vulnerable sites and updating them, in small companies often either one IT specialist answers all or there is no “admin” on the staff at all. Therefore, the typical question asked by the owners of such companies is "how much does bashbug (heartbleed, etc.) threaten my business?".
This is actually a non-trivial question. Is the office mail server, which was once set up long ago, and since then “it works”? File server? What about cloud infrastructure leased from a third-party company? Network router? What else? And what if it suddenly turns out that the patch released by the vendor does not really close the hole? Vulnerability in Bash brought a lot of problems to operators of critical systems, for which the update just can not be rolled, but on the other side - thousands of small companies that suddenly had to understand the unfriendly, confusing and dangerous IT-environment.
2nd place. Heartbleed
News Background Conclusions .
I won’t even spend time describing a bug, better than the XKCD still fails:
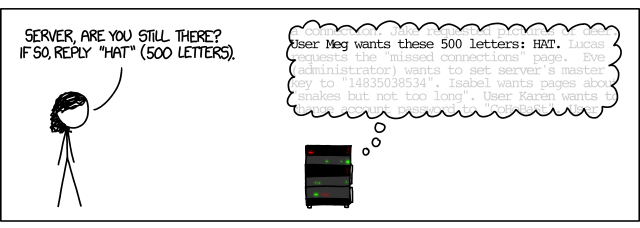
There has been a lot of controversy about what is cooler - Heartbleed or Shellshock ? On the one hand, the vulnerability in Bash leads to the execution of arbitrary code, while the hole in OpenSSL only allows access to data. On the other hand, the story of Heartbleed caused much more interest. Perhaps it is in absolute uncertainty at the time of publication of data on vulnerability. Who is affected? Who was hacked? Could they steal data and which ones? Who are the victims - mail on yahoo or online banking? Okay, we patched our servers, but did the contractors do it? Partners? Can I trust them with my data? I think it was already saying that the internet is broken? :)
1 place. Hiding malicious code in PNG image metadata.
News Reddit talk .
Um ...

Well actually this is an interesting web attack method. We load an innocent image in PNG format, from which we pull out metadata, but the malicious code is hidden in them. As a result, an invisible iframe is redirected to a visitor of an infected site with a redirect to another site from which an attack is already being carried out. Interestingly, yet another method of obfuscating malicious code is somehow not enough for sensation, and yet this is the most visited article on the English version of Threatpost in the outgoing year.
How so? Thank you need to tell the discussion on Reddit at the link above. And, more importantly, the original interpretation of the original news article in the style “In PNG, we found zero day! 111 AAAAA!”. The prospect of being attacked as a result of loading a simple image really looks awesome. Fortunately, this time the broken Internet did not work out completely.
So, the most popular story of the year was not about technology at all, but about perception. What happened to this news can be compared with the hacking of Sony Pictures Entertainment, which is even discussed in cinema magazines, completely losing any technical details along the way, but making you think about network security in general. Cyber attacks have become so common that just “one more” no longer attracts attention, the eye is blurred, the sight is shot down. Only apocalyptic news such as Sony Hack, Shellshock and "infect the whole world with one picture" are of the greatest interest. In 2014 there were a lot of them, and this is bad. I hope that as a result of these high-profile events, the companies will reconsider their view on the protection of important data. And it will be good.
Source: https://habr.com/ru/post/246745/
All Articles