Open recursive DNS server. Part 2
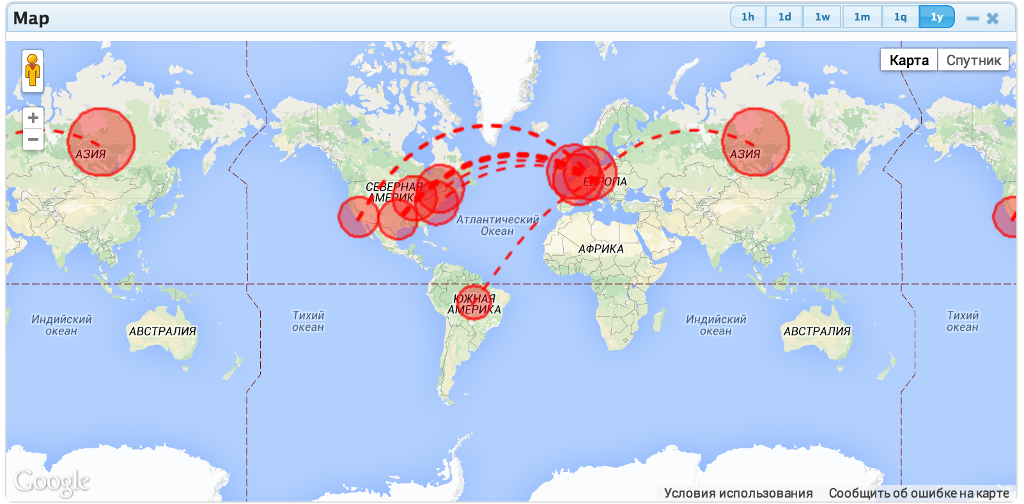
Almost 4 months ago I opened my recursive DNS server for all Internet users (see previous article ). The accumulated amount of data at the first stage of the test was large enough, for its visualization, I drove the data into the database and built dynamic changing graphs and a map. The recorded video can be viewed under the cut. The result was quite interesting, so I didn’t completely shut down the DNS server, but limited myself to including zones (used for attacks) in RPZ lists (what is RPZ can be found in this article ). “Relaxing” on “small” attacks (no more than 100 requests per second), I did not block the answers for the two DNS zones and received the first abuse report. Abuse-report was sent to the data center of my provider from the "robot". The load on his network from my server was small and periodically reached 100 requests per second. Given the fact that millions of open resolvers could be used, the maximum load on his network could be significant. Abuse-report and motivated me to go to the second part of the test. Turning off the open recursive DNS and continued to monitor the behavior of the attackers.
Visualization of the attack described in the first article :
')
Test environment description
When writing the last article, all data was collected and processed almost in manual mode. It was long, tedious, and sometimes the results had to be checked. Since I’m lazy enough, I like to automate processes and analyze data, I asked myself to create a small system for reporting and analyzing incoming logs from a DNS server in near real time mode (if this is interesting, I can describe it in a separate article). All graphs and tables used in this article were generated using jqPlot, jqGrid and Google Maps. I use the Infoblox virtual device as a DNS server, but its syslog format is similar to bind.
Attacks
During testing, my server was used to conduct DrDoS attacks (Amplification + Reflection), as well as attempts were made to implement cache poisoning. According to some queries, it was obvious that the DGA (Domain Generation Algorithm) mechanism is used, possibly for cache poisoning, possibly for communicating with control centers (since these domains were used only for attacks) or when attacking with phantom domains.
After turning off the recursive server, the parasitic load decreased, but did not disappear completely.
The peak load on the “open” server reached 3 thousand requests per second and on average kept about 100 requests per second; on a closed server, the maximum load decreased to 20 requests per second with rare peaks to 100 requests (the rate limit is set to 300 requests per minute with the possibility of growth up to 1000).

As can be seen in the graph below, the companies in the United States suffered the most from the actions of the attackers.

Analyzing the number of requests sent to the network of each company can indirectly help to identify victims and possible infected networks. For example, the China Telecom network is likely infected, and the client of Rostelecom was attacked. The table below shows the information to organizations, the number of IP addresses and the number of requests processed. Information about companies was obtained using the whois service.
| A country | Company | Number of requests | IP count |
| United States | SoftLayer Technologies Inc. | 3965202 | 36 |
| United States | SingleHop, Inc. | 2617987 | 27 |
| United States | PSINet, Inc. | 1994461 | 22 |
| France | OVH SAS | 1051080 | 304 |
| United kingdom | Hosting Services Inc | 938367 | four |
| Germany | 1 & 1 Internet AG | 761020 | 12 |
| United States | PrivateSystems Networks | 748641 | four |
| Russian Federation | OJSC Rostelecom Ticket 09-39331, RISS 15440, UrF | 687028 | one |
| United States | Time Warner Cable Internet LLC | 671211 | 1568 |
| Canada | OVH Hosting, Inc. | 592920 | 213 |
| United States | Akamai Technologies, Inc. | 176327 | 4410 |
| China | China Telecom | 51565 | 207 |
| United States | AT & T Internet Services | 27502 | 854 |
DrDOS attack
The domains listed in the table below were used for the attack. Domain freeinfosys.com appeared after the "closing" of the recursive server. Which may mean that someone uses outdated databases that are rarely checked.
To determine if your server is being attacked or used to conduct attacks, it is enough to analyze which domains and how often you applied with the ANY + E request.
| Domain | Request | Flag | Number of requests |
| webpanel.sk | ANY | + E | 14962032 |
| oggr.ru | ANY | + E | 8300693 |
| energystar.gov | ANY | + E | 6676350 |
| doleta.gov | ANY | + E | 6326853 |
| 067.cz | ANY | + E | 2463053 |
| sema.cz | ANY | + E | 1251206 |
| GUESSINFOSYS.COM | ANY | + E | 690320 |
| jerusalem.netfirms.com | ANY | + E | 587534 |
| paypal.de | ANY | + E | 454756 |
| nlhosting.nl | ANY | + E | 414113 |
| freeinfosys.com | ANY | + E | 352233 |
| krasti.us | ANY | + E | 333806 |
| doc.gov | ANY | + E | 259248 |
| svist21.cz | ANY | + E | 231946 |
| wradish.com | ANY | + E | 117294 |
When using ANY + E, all information on the zone is requested and the EDNS functionality is activated in order to get the maximum possible UDP packet size. A list of the 10 most frequent requests and their flags is given in the table below.
| Request | Flags | Number of requests |
| ANY | + E | 43500439 |
| A | -ED | 17339 |
| ANY | + | 11932 |
| A | - | 9853 |
| A | -EDC | 8956 |
| AAAA | -EDC | 4749 |
| AAAA | -ED | 4467 |
| ANY | - | 2289 |
| A | + E | 1899 |
| Rrsig | + E | 1124 |
Cache Poisoning, Random domain attack and DGA
During the operation of the DNS server, a small number of attacks on cache poisoning were detected. In the statistics of the Infoblox DNS server, it was stated that the answers were received with the wrong ports and query ID, but, unfortunately, no log files were found for analysis.
In addition, suspicious requests of the form were detected:
- ndnaplaaaaeml0000dgaaabbaaabgnli.energystar.gov;
- mmokojaaaaeml0000dgaaabbaaabgclm.doleta.gov;
- oaanjeaaaaesc0000deaaabbaaabicoc.webpanel.sk;
- cnklipaaaaesh0000claaabbaaabfgoa;
- 2d852aba-7d5f-11e4-b763-d89d67232680.ipvm.biz.
It is possible that these records are partly related to detected attempts to cache the cache, trying to conduct an attack using phantom domains (the authoritative server does not respond and thus the outbound connection pool is clogged) or the work of “unknown animals” (malware) trying to contact the control center.
findings
- Any DNS server is a great source of information about the behavior of ordinary users and malware;
- Log analysis will help improve the quality of DNS;
- A large number of requests "ANY + E" shows that your server is or is participating in the attack;
- Malware used a small number of domains to carry out DrDOS attacks (no more than 3x-4x simultaneously);
- Blocking such suspicious domains (for example, RPZ) will reduce the load on the server and the network;
- Too long DNS names (as in the example above) are a reason to scrutinize the client's behavior (a host is infected or someone is using DNS tunnels).
Source: https://habr.com/ru/post/246123/
All Articles