How to show the most dangerous vulnerabilities
On duty, I often have to carry out an instrumental security audit of various enterprises. The procedure for drafting the final report contains one unpleasant feature that I have long wanted to get rid of. In addition to the most dangerous vulnerabilities of the system, the client should always show links to public exploits for these errors. And these links had to be searched manually.
In most cases, the customer takes any serious measures to protect - only if he knows about hacking tools that automate attacks through the vulnerabilities he has found. The discovered holes themselves do not frighten, but such programs are very even: thanks to them, an entire army of schoolchildren, kulkhackers, disgruntled ex-employees and saboteurs from competing organizations can pull on black hats. Grsecurity creator Brad Spengler said that only public exploits make changes in the public understanding of the level of existing security, and my experience fully confirms this point.

')
At some point, I realized that searching for links to exploits is a very important job, but so routine and mechanical that it’s just a sin not to automate it. Initially, a simple console script was written, which gradually acquired a GUI and learned to understand the various formats of vulnerability scan systems reports. All improvements and improvements to PT Exploit Explorer were later carried out based on the wishes of users, and this process continues to this day.
Judging by the feedback from the first users, the advantages of the utility include a fairly quick and error-free search for exploits on the list of several thousand vulnerabilities; This saves a lot of time for a security professional. The main reason why the utility turned out to be in demand not only in our or other information security companies, but also in various other organizations, is the ability to use the resulting report to prioritize when determining the priority of eliminating vulnerabilities - and as an argument in a dispute with IT specialists. Let me give you one of the reviews: “The Java script ptee.jar, which is looking for ready-made exploits, is a great thing! Give some thanks to the developer. The report sent to the IT department acted like boiling water over the head. ”
The program allows you to search for links to exploits in public databases, including Rapid7 and exploit-db. The utility is fully compatible with our corporate software (XSpider vulnerability scanner and MaxPatrol security and compliance monitoring system), as well as reports from other vulnerability detection systems in any uncompressed format.
The program can be used both in console mode and in interactive mode (launch without parameters). This is done so that it can be integrated into various projects as an external module.
For example: java -jar ptee.jar -html "vulnerability report.xml":
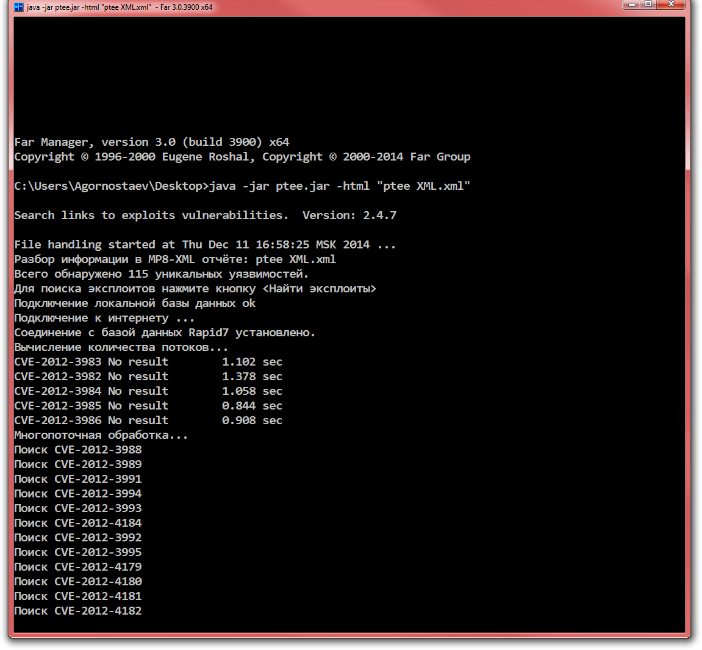
The resulting report will be presented as a file of vulnerability report.html:
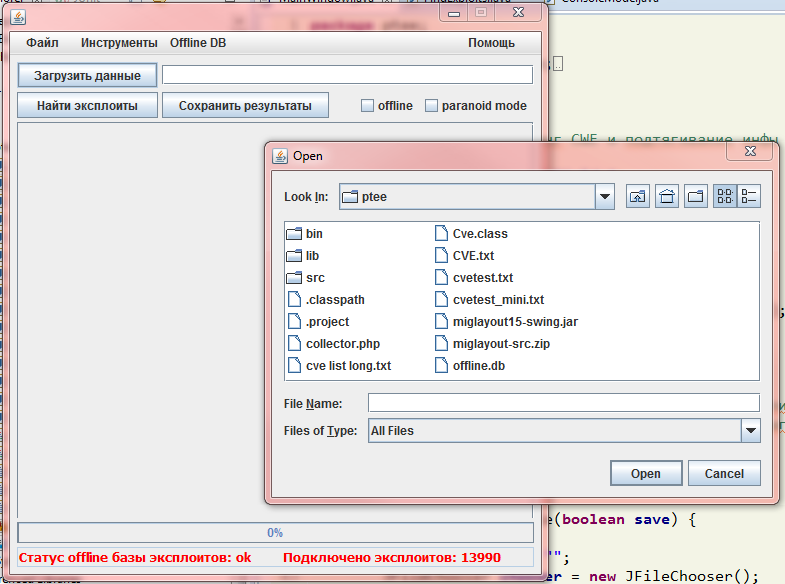
To search for exploits, you must download a report file that contains lists of vulnerabilities in the CVE-XXXX-XXXXXX format, and click the "Find Exploits" button. You can also create a report file yourself - the utility is able to process text files with an arbitrary list of vulnerabilities from the CVE database.
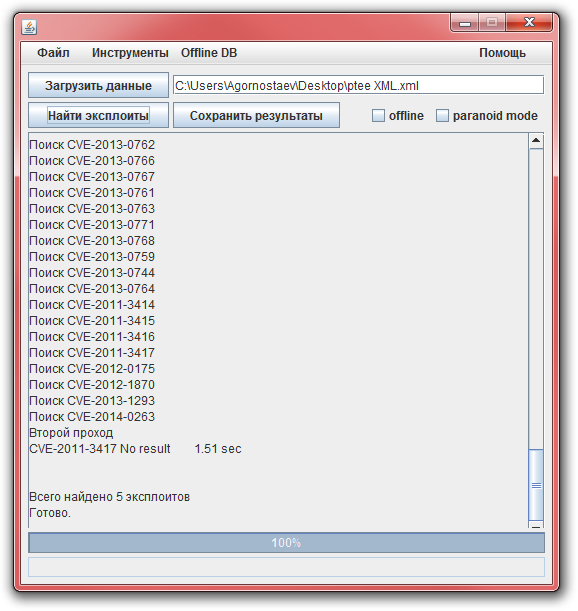
During the search, service information will be displayed on the screen. The appearance on the screen of the number of exploits found means that you can save the search results by clicking on the appropriate button.
Report generation with vulnerabilities, their corresponding exploits and rank interpretation of the results is made in HTML, CSV and text file formats.
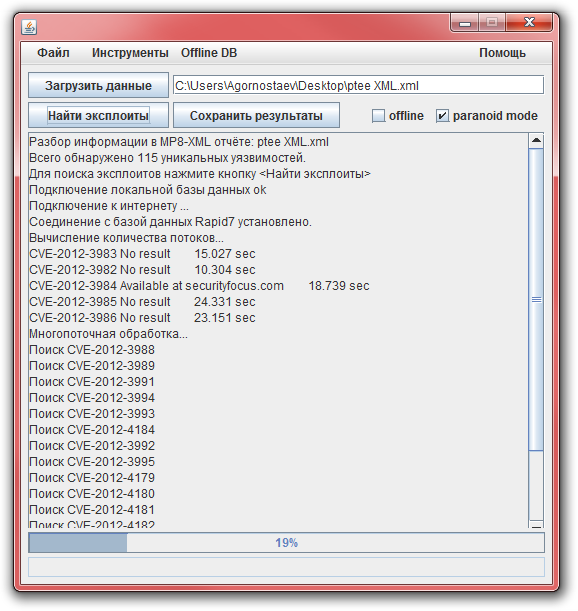
Consider two more settings. When the offline option is enabled, the utility uses data from previous searches that were previously cached in the offline.db file. If you activate paranoid mode, the report timeout will increase significantly, but the search efficiency will be higher. “Paranoid mode” allows detecting exploits for this vulnerability in closed or paid databases (via www.securityfocus.com ).
Script-kiddies will not be able to use such software, however, a security specialist will know that methods of operating errors already exist, and the script may soon appear in the public domain.
Here is the final report:

As an epilogue, I recall the results of the study of Positive Technologies, according to which in 2013, 86% of the corporate systems of large companies were exposed to vulnerabilities that allow them to gain complete control over critical resources. These are not postcards, but payment systems, e-mail, storages of personal data and documents, ERP systems, automated process control systems. And for an attack in 82% of cases, it was enough for a hacker to have a medium or low qualification.
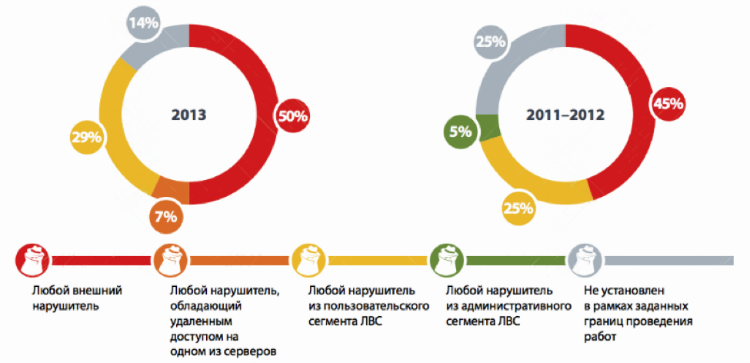
A public exploit greatly reduces even this low threshold of entry and seriously increases the likelihood of an incident. In some cases, the process of installing updates is associated with various difficulties, so it is better to follow the main “factories” for the production of hacker programs from time to time and compare the results with your vulnerabilities.
Download PT Exploit Explorer at www.ptsecurity.ru/lab/freeware .
Author: Andrey Gornostaev, Senior Specialist, Design Solutions Department, Positive Technologies.
In most cases, the customer takes any serious measures to protect - only if he knows about hacking tools that automate attacks through the vulnerabilities he has found. The discovered holes themselves do not frighten, but such programs are very even: thanks to them, an entire army of schoolchildren, kulkhackers, disgruntled ex-employees and saboteurs from competing organizations can pull on black hats. Grsecurity creator Brad Spengler said that only public exploits make changes in the public understanding of the level of existing security, and my experience fully confirms this point.

')
At some point, I realized that searching for links to exploits is a very important job, but so routine and mechanical that it’s just a sin not to automate it. Initially, a simple console script was written, which gradually acquired a GUI and learned to understand the various formats of vulnerability scan systems reports. All improvements and improvements to PT Exploit Explorer were later carried out based on the wishes of users, and this process continues to this day.
Judging by the feedback from the first users, the advantages of the utility include a fairly quick and error-free search for exploits on the list of several thousand vulnerabilities; This saves a lot of time for a security professional. The main reason why the utility turned out to be in demand not only in our or other information security companies, but also in various other organizations, is the ability to use the resulting report to prioritize when determining the priority of eliminating vulnerabilities - and as an argument in a dispute with IT specialists. Let me give you one of the reviews: “The Java script ptee.jar, which is looking for ready-made exploits, is a great thing! Give some thanks to the developer. The report sent to the IT department acted like boiling water over the head. ”
How it works
The program allows you to search for links to exploits in public databases, including Rapid7 and exploit-db. The utility is fully compatible with our corporate software (XSpider vulnerability scanner and MaxPatrol security and compliance monitoring system), as well as reports from other vulnerability detection systems in any uncompressed format.
The program can be used both in console mode and in interactive mode (launch without parameters). This is done so that it can be integrated into various projects as an external module.
For example: java -jar ptee.jar -html "vulnerability report.xml":

The resulting report will be presented as a file of vulnerability report.html:

To search for exploits, you must download a report file that contains lists of vulnerabilities in the CVE-XXXX-XXXXXX format, and click the "Find Exploits" button. You can also create a report file yourself - the utility is able to process text files with an arbitrary list of vulnerabilities from the CVE database.

During the search, service information will be displayed on the screen. The appearance on the screen of the number of exploits found means that you can save the search results by clicking on the appropriate button.
Report generation with vulnerabilities, their corresponding exploits and rank interpretation of the results is made in HTML, CSV and text file formats.
Consider two more settings. When the offline option is enabled, the utility uses data from previous searches that were previously cached in the offline.db file. If you activate paranoid mode, the report timeout will increase significantly, but the search efficiency will be higher. “Paranoid mode” allows detecting exploits for this vulnerability in closed or paid databases (via www.securityfocus.com ).

Script-kiddies will not be able to use such software, however, a security specialist will know that methods of operating errors already exist, and the script may soon appear in the public domain.
Here is the final report:

As an epilogue, I recall the results of the study of Positive Technologies, according to which in 2013, 86% of the corporate systems of large companies were exposed to vulnerabilities that allow them to gain complete control over critical resources. These are not postcards, but payment systems, e-mail, storages of personal data and documents, ERP systems, automated process control systems. And for an attack in 82% of cases, it was enough for a hacker to have a medium or low qualification.

A public exploit greatly reduces even this low threshold of entry and seriously increases the likelihood of an incident. In some cases, the process of installing updates is associated with various difficulties, so it is better to follow the main “factories” for the production of hacker programs from time to time and compare the results with your vulnerabilities.
Download PT Exploit Explorer at www.ptsecurity.ru/lab/freeware .
Author: Andrey Gornostaev, Senior Specialist, Design Solutions Department, Positive Technologies.
Source: https://habr.com/ru/post/245885/
All Articles