Microsoft and Adobe released a set of updates, December 2014
Microsoft has released the latest scheduled set of security updates this year. As part of it, 24 vulnerabilities in products such as MS Windows, Internet Explorer, Office, and Exchange Server (three updates with the Critical status and four Important) were closed. As usual, one of the MS14-080 updates fixes vulnerabilities in the Internet Explorer browser that attackers can use to remotely install malicious code into the system. However, within the framework of this patch tuesday, no vulnerabilities that were used by the attackers in exploited real cyber attacks were closed . A reboot is required to use MS14-080.

Another critical update MS14-084 fixes a memory-corruption type CVE-2014-6363 vulnerability in the VBScript Scripting Engine component (vbscript.dll) that Internet Explorer uses to execute VBScript scripts. This year, vbscript.dll has been patched more than once.
')
The MS14-080 update fixes fourteen vulnerabilities in Internet Explorer, most of which are of the Remote Code Execution type and can be used by attackers to install malware into the system. One of the vulnerabilities CVE-2014-6368 can be used to bypass ASLR in the context of a browser process (Internet Explorer ASLR Bypass Vulnerability).
Update MS14-081 fixes two vulnerabilities CVE-2014-6356 (invalid index) and CVE-2014-6357 (use-after-free) in Office 2007-2010-2013 (Word & Web Apps). Both vulnerabilities are of the Remote Code Execution type and can be used by attackers to install malware through a specially crafted Office file. Critical. Exploitation More Likely .
The MS14-082 update fixes the use-after-free CVE-2014-6364 RCE vulnerability in MS Office 2007-2010-2013. As in the previous case, attackers can remotely execute malicious code using a specially prepared Office document. Important. Exploitation More Likely .
Update MS14-083 also fixes vulnerabilities in Office (MS Excel 2007-2010-2013) that could lead to remote code execution. Two vulnerabilities are being fixed: CVE-2014-6360 and CVE-2014-6361. Important. Exploitation Less Likely .
The MS14-075 update fixes four different vulnerabilities in MS Exchange Server 2007-2010-2013 and Outlook Web App (OWA) online access service. Vulnerability Information Disclosure type CVE-2014-6319 (Outlook Web App Token Spoofing) can be used by attackers to unauthorized information from the Exchange server and allow them to send emails on behalf of one of the Exchange Server users. Two other vulnerabilities, CVE-2014-6325 and CVE-2014-6326 (Outlook Web App XSS) of type Elevation of Privilege are also present in the Exchange Server, if successfully exploited, an attacker can perform a wide range of actions on a user account, including reading it messages and change permissions. The latest vulnerability CVE-2014-6336 is of type information disclosure. Due to an error in the implementation of the OWA mechanism for working with redirection markers when redirecting a user by URL links, this can be used by attackers to redirect the user to an arbitrary domain. Important. Exploitation Less Likely .
Update MS14-085 fixes one Information Disclosure type CVE-2014-6355 vulnerability in the Graphics component (MS Graphics Component - windowscodecs.dll). Using a specially crafted JPEG image file that can be placed on a website, an attacker can find out information about the vulnerable system. This vulnerability can be used in conjunction with other RCE vulnerabilities when attacking Internet Explorer, as it will help attackers bypass the ASLR. Important. Exploitation Less Likely .
1 - Exploitation More Likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploitation Less Likely
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).
Adobe has also updated its Flash Player ( APSB14-27 ), Acrobat & Reader ( APSB14-28 ), and ColdFusion ( APSB14-29 ) products .
As part of APSB14-27, the company fixed six vulnerabilities in its Flash Player. One of the vulnerabilities of CVE-2014-9163 was seen in the exploitation by hackers. Most closed vulnerabilities are related to various types of memory-corruption and buffer-overflow. They can be used by attackers to remotely execute code on a vulnerable system.
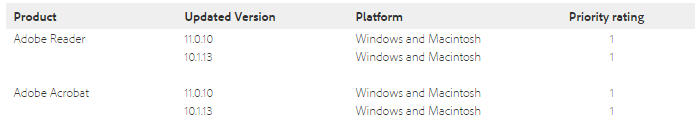
Update APSB14-28 fixes 20 vulnerabilities in Reader & Acrobat. Vulnerabilities can also be used for remote code execution in the system by malicious users. The current versions of these products are listed in the table below.
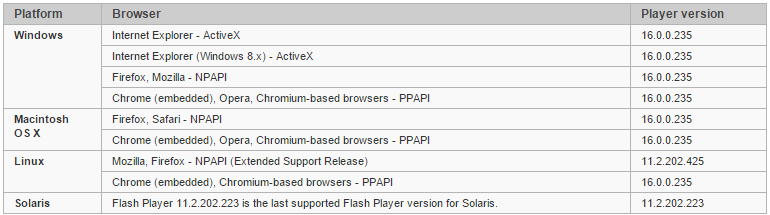
We also recommend updating your Flash Player. Browsers such as Internet Explorer 10 & 11 on Windows 8 / 8.1 and Google Chrome update their Flash Player versions automatically. For IE, see the updated Security Advisory 2755801 . Check your version of Flash Player for relevance here , the table below shows these versions for various browsers.

be secure.

Another critical update MS14-084 fixes a memory-corruption type CVE-2014-6363 vulnerability in the VBScript Scripting Engine component (vbscript.dll) that Internet Explorer uses to execute VBScript scripts. This year, vbscript.dll has been patched more than once.
')
The MS14-080 update fixes fourteen vulnerabilities in Internet Explorer, most of which are of the Remote Code Execution type and can be used by attackers to install malware into the system. One of the vulnerabilities CVE-2014-6368 can be used to bypass ASLR in the context of a browser process (Internet Explorer ASLR Bypass Vulnerability).
Update MS14-081 fixes two vulnerabilities CVE-2014-6356 (invalid index) and CVE-2014-6357 (use-after-free) in Office 2007-2010-2013 (Word & Web Apps). Both vulnerabilities are of the Remote Code Execution type and can be used by attackers to install malware through a specially crafted Office file. Critical. Exploitation More Likely .
The MS14-082 update fixes the use-after-free CVE-2014-6364 RCE vulnerability in MS Office 2007-2010-2013. As in the previous case, attackers can remotely execute malicious code using a specially prepared Office document. Important. Exploitation More Likely .
Update MS14-083 also fixes vulnerabilities in Office (MS Excel 2007-2010-2013) that could lead to remote code execution. Two vulnerabilities are being fixed: CVE-2014-6360 and CVE-2014-6361. Important. Exploitation Less Likely .
The MS14-075 update fixes four different vulnerabilities in MS Exchange Server 2007-2010-2013 and Outlook Web App (OWA) online access service. Vulnerability Information Disclosure type CVE-2014-6319 (Outlook Web App Token Spoofing) can be used by attackers to unauthorized information from the Exchange server and allow them to send emails on behalf of one of the Exchange Server users. Two other vulnerabilities, CVE-2014-6325 and CVE-2014-6326 (Outlook Web App XSS) of type Elevation of Privilege are also present in the Exchange Server, if successfully exploited, an attacker can perform a wide range of actions on a user account, including reading it messages and change permissions. The latest vulnerability CVE-2014-6336 is of type information disclosure. Due to an error in the implementation of the OWA mechanism for working with redirection markers when redirecting a user by URL links, this can be used by attackers to redirect the user to an arbitrary domain. Important. Exploitation Less Likely .
Update MS14-085 fixes one Information Disclosure type CVE-2014-6355 vulnerability in the Graphics component (MS Graphics Component - windowscodecs.dll). Using a specially crafted JPEG image file that can be placed on a website, an attacker can find out information about the vulnerable system. This vulnerability can be used in conjunction with other RCE vulnerabilities when attacking Internet Explorer, as it will help attackers bypass the ASLR. Important. Exploitation Less Likely .
1 - Exploitation More Likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploitation Less Likely
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).

Adobe has also updated its Flash Player ( APSB14-27 ), Acrobat & Reader ( APSB14-28 ), and ColdFusion ( APSB14-29 ) products .
As part of APSB14-27, the company fixed six vulnerabilities in its Flash Player. One of the vulnerabilities of CVE-2014-9163 was seen in the exploitation by hackers. Most closed vulnerabilities are related to various types of memory-corruption and buffer-overflow. They can be used by attackers to remotely execute code on a vulnerable system.
Update APSB14-28 fixes 20 vulnerabilities in Reader & Acrobat. Vulnerabilities can also be used for remote code execution in the system by malicious users. The current versions of these products are listed in the table below.

We also recommend updating your Flash Player. Browsers such as Internet Explorer 10 & 11 on Windows 8 / 8.1 and Google Chrome update their Flash Player versions automatically. For IE, see the updated Security Advisory 2755801 . Check your version of Flash Player for relevance here , the table below shows these versions for various browsers.


be secure.
Source: https://habr.com/ru/post/245485/
All Articles