A vulnerability has been discovered in the anti-counterfeiting system.

Egyptian engineer Yasser Ali, while researching the work of PayPal, discovered a vulnerability that allowed him to completely circumvent the CSRF attack protection system used by the service ( cross-site request forgery ). He described this vulnerability in detail in his blog ; we translated and adapted the post describing the vulnerability.
For a successful attack of this kind, the attacker needs to force the victim to fraudulently get a specially prepared link with which he can create requests on behalf of the victim. The attack is possible only if the user is authorized on the website that is being exposed to it.
')
The post was prepared specifically for the corporate blog site on payment systems c monitoring Web-payment.ru exchangers.
Reusable CSRF Tokens
The first thing that Ali discovered was the possibility of multiple use of a CSRF token, which allows you to verify the authenticity of each request made by the user. The token can be found in the body of any request, and its Auth parameter is changed for each individual request in order to ensure security. However, after a detailed study, it was found that Auth continues to act for a specific name or email address of the user, even when reused. In case an attacker succeeds in finding any of the previously generated CSRF tokens, he can easily perform actions on behalf of any user authorized at the moment.
However, this possibility does not seem to pose a real danger, since it is impossible to get the Auth value from the victim’s session.
Bypassing the CSRF authorization system
It is known that the Auth parameter checks every user request. Ali decided to check what would happen if an “unauthorized” attacker attempted to send a request for sending money. In this case, PayPal will ask the attacker to provide your email address or password. In response, the attacker can provide the victim's email, enter any password, and thus intercept the request, which will contain a genuine reusable CSRF authorization token, which allows to authorize requests of this user.
Further analysis showed that by intercepting a POST request from pages that can provide tokens before the user is authorized, the attacker can get CSRF Auth, applicable to all users. Such a magical CSRF Auth can, for example, be found at www.paypal.com/eg/cgi-bin/webscr?cmd=_send-money . Having done all these actions, an attacker can fake almost any request on behalf of a real user.
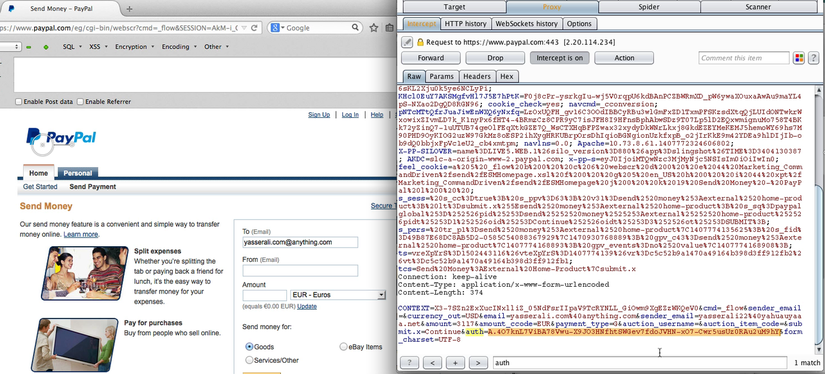
The application generates a genuine Auth-token for a logged out user!
After checking the process of changing the password on the service, Ali came to the conclusion that the hacker would not be able to change the user's password without knowing his secret questions. In addition, the user, in turn, cannot change his secret questions without knowing his password.
Changing security questions to bypass the security system
Further research has shown that the process of "creating" secret questions, which starts as soon as the user starts registration, is not password protected and can be used to reset secret questions multiple times without entering a password. Thus, with CFSR Auth at its disposal, an attacker can fake this procedure and change the victim's secret questions.

The first attempt to "create" secret questions is not password protected and can be used many times later
Having performed all the actions described above, an attacker can make an attack aimed at specific PayPal users by faking inquiries using the CSRF principle and gaining full control over their accounts with its help. Among other things, the attacker will be able to fake the following requests:
- Add / Delete / Confirm Email Addresses
- Change secret questions
- Change shipping address or billing address
- Change payment methods
- Change user settings (notifications, mobile number settings)
- Add privileged users to a business account
- ... much more ...
Ali also wrote an interactive server in Python to automate the process and demonstrate how a cracker could take advantage of this vulnerability in practice.
Video from the author, showing the process of hacking:
However, the bugs themselves were discovered in early August, the engineer reported in time about the vulnerabilities that were closed, and information about them was made public after that, so at the moment they no longer pose any threat to PayPal.
For his find, Ali, by his own admission, received the maximum reward that PayPal offers to all who report any critical problems in protecting the system, $ 10,000.

Source: https://habr.com/ru/post/245445/
All Articles