FBI: Sony was attacked by hackers from North Korea
A few weeks ago it became known about a large-scale cyber attack on the company Sony (Sony Pictures Entertainment). As a result of cyber attacks, the attackers managed to gain access to several non-released films, as well as private data of the company's employees. During the investigation of this incident, conducted by the FBI and FireEye, it was found that hackers managed to penetrate the company's internal network and install Destover malware (ESET: Win32 / NukeSped.A , Microsoft: Trojan: Win32 / NukeSped.A , Symantec: Backdoor.Destover ). Due to the use of this family of malware in cyber attacks, the media reported on the so-called. “Destructive attack”, as Destover specializes in the destruction of data on computer hard drives.
The movies and other information stolen from Sony, in particular, the data of the company's employees, were made publicly available. However, the company has taken quick steps to clear a lot of such resources. Some archives with information managed to be in the possession of krebsonsecurity .
')
The malicious program used in cyber attack specializes in the complete destruction of computer hard drives data and is similar to malware with similar functions called Wiper / Shamoon . Last year, Wiper was used for cyber attacks on South Korean organizations.
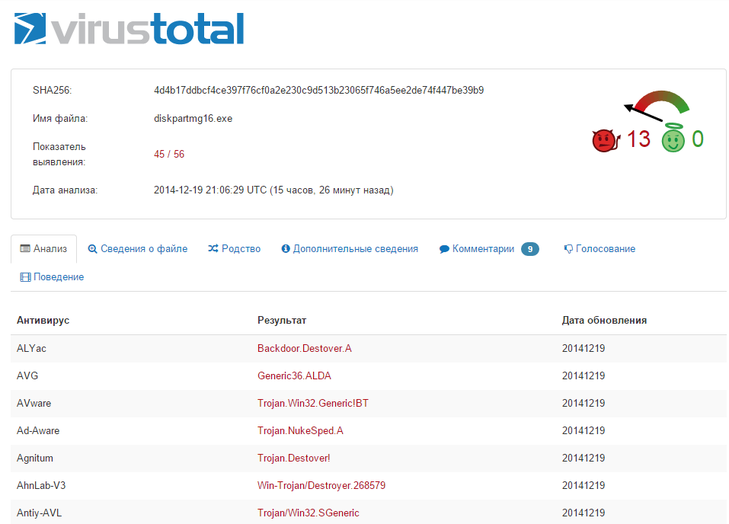
Fig. One of the malware executable files on VirusTotal has a high detection rate.
From the FBI report.
As a result of the investigation [of this incident ], which was carried out in collaboration with US government organizations, the FBI has enough information to conclude that the North Korean government is responsible for carrying out these actions [ cyber attack ]. While we can not publish the full information on this investigation due to the need to protect our sources, however, our conclusions are based on the following information:
Some additional information is contained in the krebsonsecurity report .
CrowdStrike says FBI results matches own findings. Sony malware matches Silent Chollima (North Korean actor) in attacks tracing to '06
- Nicole Perlroth (@nicoleperlroth) December 19, 2014The movies and other information stolen from Sony, in particular, the data of the company's employees, were made publicly available. However, the company has taken quick steps to clear a lot of such resources. Some archives with information managed to be in the possession of krebsonsecurity .
')
The malicious program used in cyber attack specializes in the complete destruction of computer hard drives data and is similar to malware with similar functions called Wiper / Shamoon . Last year, Wiper was used for cyber attacks on South Korean organizations.

Fig. One of the malware executable files on VirusTotal has a high detection rate.
From the FBI report.
It has been the responsibility of the FBI to be responsible for these actions. This information is subject to the following:
- FBI knows North Korean actors previously developed. For example, there were similarities of code, encryption algorithms, data deletion methods, and compromised networks.
- It has been previously identified that North Korea has been identified as the FBI. For example, the FBI has been identified as having been able to get rid of it.
- Formerly, the tools are used in the North Korean economy.
As a result of the investigation [of this incident ], which was carried out in collaboration with US government organizations, the FBI has enough information to conclude that the North Korean government is responsible for carrying out these actions [ cyber attack ]. While we can not publish the full information on this investigation due to the need to protect our sources, however, our conclusions are based on the following information:
- Technical analysis of the malware that was used in this attack to destroy hard drive data shows its similarity to other malware, which, according to the FBI, was developed by people from North Korea.
- The FBI also found a significant similarity to the infrastructure of the attackers, which was used in this cyber attack, on the other, which was used for cyber attacks on US government organizations and is owned by North Korea. For example, the FBI found that some IP addresses that belong to North Korea’s infrastructure interacted with computers that have IP addresses that are hardcoded in the [ Destover ] malware code.
- The software tools that were used in the attack on Sony have similar features with other tools that were used in cyber attacks on banks and media resources of South Korea in March last year. These attacks were carried out from North Korea.
Some additional information is contained in the krebsonsecurity report .
Source: https://habr.com/ru/post/244853/
All Articles