"Iron" vulnerability in DRAM allows you to change the contents of someone else's memory
Published article Yoongu Kim & others. Disturbance Errors , which describes how to change the contents of a DRAM memory that does not require access to this address. In fact, this means a violation of memory isolation between processes or virtual machines. Of the 129 memory modules tested, 110 were susceptible to vulnerabilities, including all modules released after 2012.
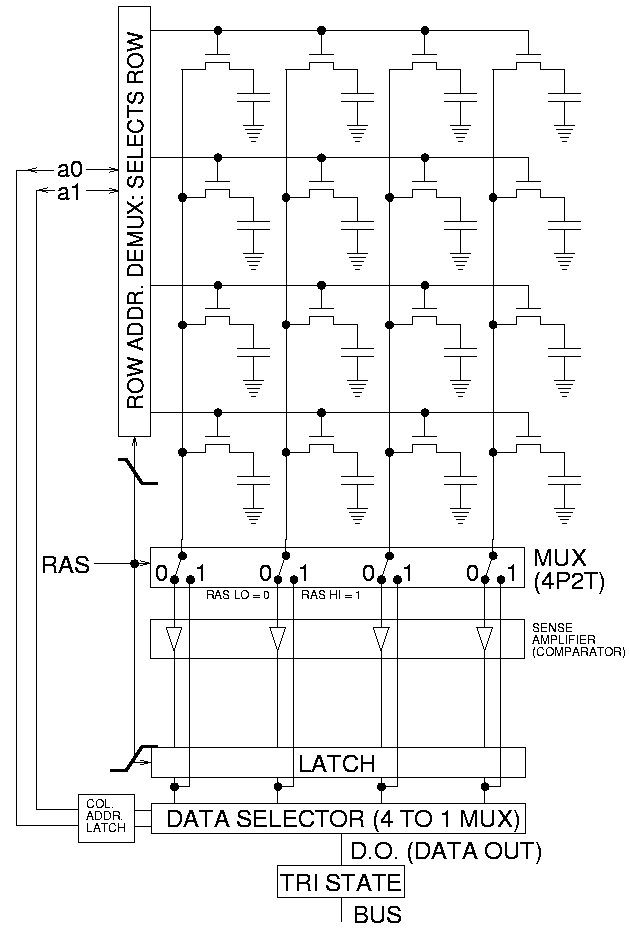
DRAM is a two-dimensional lattice, in the nodes of which there are memory cells, each of which stores one bit. Each cell consists of a transistor, and a capacitor that can be charged or not charged, which corresponds to the value of bits 1 or 0. Capacitors lose charge over time, so it is necessary periodically (every few tens of milliseconds) to overwrite information (regeneration). In modern chips, several independent modules ("banks") are made to improve performance, with separate output stages.
')
To read the information, one of the horizontal lines ( wordline ) is energized, so that the corresponding transistor line opens. At the same time, the charges of the capacitors of the cells in the given line are read from the vertical lines ( bitline ). After this, the wordline closes, allowing you to go on to read another line.
It turned out that if the wordline is turned on and off periodically, the induced currents lead to an increase in leakage in the neighboring cells of the same bank, and if many switches are made between regeneration cycles, this may be enough to switch a bit from 0 to 1 or vice versa.
The effect can be achieved with code that does not require any special privileges. The simplest attack looks like this:
The X and Y addresses must be in the same bank, but on different DRAM lines. A cache reset is needed to ensure read from RAM on each cycle. Two addresses must be used to enable wordline on / off on each cycle. This code does not cause the vulnerability, since the DRAM logic optimizes wordline inclusion, and the necessary constant switching does not occur:
To cause an error, it is necessary to make several hundred thousand cycles during the time between two regenerations (usually 64 ms), which is quite achievable. The presence of the ECC does not help much, as there are frequent errors in several bits simultaneously.
DRAM Organization

DRAM is a two-dimensional lattice, in the nodes of which there are memory cells, each of which stores one bit. Each cell consists of a transistor, and a capacitor that can be charged or not charged, which corresponds to the value of bits 1 or 0. Capacitors lose charge over time, so it is necessary periodically (every few tens of milliseconds) to overwrite information (regeneration). In modern chips, several independent modules ("banks") are made to improve performance, with separate output stages.
')
To read the information, one of the horizontal lines ( wordline ) is energized, so that the corresponding transistor line opens. At the same time, the charges of the capacitors of the cells in the given line are read from the vertical lines ( bitline ). After this, the wordline closes, allowing you to go on to read another line.
It turned out that if the wordline is turned on and off periodically, the induced currents lead to an increase in leakage in the neighboring cells of the same bank, and if many switches are made between regeneration cycles, this may be enough to switch a bit from 0 to 1 or vice versa.
Demonstration
The effect can be achieved with code that does not require any special privileges. The simplest attack looks like this:
code1a: mov (X), %eax ; X mov (Y), %ebx ; Y clflush (X) ; , X clflush (Y) ; , Y mfence ; jmp code1a The X and Y addresses must be in the same bank, but on different DRAM lines. A cache reset is needed to ensure read from RAM on each cycle. Two addresses must be used to enable wordline on / off on each cycle. This code does not cause the vulnerability, since the DRAM logic optimizes wordline inclusion, and the necessary constant switching does not occur:
code1b: mov (X), %eax clflush (X) mfence jmp code1b To cause an error, it is necessary to make several hundred thousand cycles during the time between two regenerations (usually 64 ms), which is quite achievable. The presence of the ECC does not help much, as there are frequent errors in several bits simultaneously.
Source: https://habr.com/ru/post/244741/
All Articles