Brief history of hacking. A story from the head of information security at Yandex
Hello! My name is Anton Karpov, in Yandex I manage the information security service. Recently, I was faced with the task of telling schoolchildren - students of the Small ShAD of Yandex - about the profession of a security specialist. I decided that instead of the boring theory, which can be read in textbooks (and what you can tell in one lecture!), It is better to tell the story of computer security. Based on the lecture, I prepared this short story.
Like it or not, and information security is strongly associated with many hackers. Therefore, I want to tell you today about hackers and their history. Nowadays, a hacker is an attacker who does something illegal, hacks some systems with material gain for himself. But this was not always the case.

')
Let us go back half a century ago, in the 1960s, when computers gradually began to penetrate our lives. Hacking began even then, with attempts to use equipment for other purposes. For example, to run on it the same written game. In those days, the concept of "hacker" is a very enthusiastic person trying to do something unusual with the system. After all, access to computers was mainly among university employees, and not much was allocated to everyone’s processor time. You, literally, were allowed to work with a computer only a few hours a week, on a strict schedule. But even in such conditions, people managed to find time for experiments. Hackers of that time were interested in not just solving some computational problem, they wanted to understand how the machine works and works. The culture of hacking came from very enthusiastic people.

In the 70s, hacking was finally formed as an attempt to “play” with the information system, bypassing its limitations. There was no Internet then, but there was already a telephony. Therefore, there was such a thing as phreaking. The father of the phreaking is considered to be John Draper, known by the nickname “Captain Crunch”. Once he found a gift in the Captain Crunch cornflakes, a whistle. Telephone lines at that time were analog and telephone sets communicated with each other through the exchange of tones. It turned out that the tone of the whistle detected by Draper coincides with the tone used by the telephone equipment to transmit commands. Phreakers (so called enthusiasts of "games" with ATS) began using whistles to emulate a system of commands and dial free of charge from street phones to neighboring cities and states. The next step was the creation of a “blue box” - a device that emulated all the same tone commands. He allowed not only to dial the necessary numbers, but also to use secret service lines. By giving a signal at a frequency of 2600 Hz, it was possible to transfer telephone systems to administrative mode and get through to numbers that are not available to the average person, for example, to the White House. Entertainment continued until the late 80s, when a popular newspaper published a large article about the “blue box”, which attracted the attention of the police to phreakers. Many phreakers, including Draper himself, were arrested. Later still managed to figure out what they did it all not for the sake of money, but rather from sports interest and self-indulgence. At that time, the criminal code simply did not have any articles related to fraud with information systems, so that soon all phreakers were released.

In the 1980s, the word “hacker” first gained a negative connotation. The image of a hacker as a person who can do something illegal for profit has already begun to form in people's minds. In 1983, one of the founders of the hacking group “414s” appeared on the cover of Newsweek, which became famous for a series of hacks of serious computer systems. Hackers have their own magazines and other ways to exchange information.
During these years, the authorities of Western countries are beginning to form laws related to computer security. However, the scale, of course, can not be compared with today. So, a lot of noise happened around the case of Kevin Polesen, who, thanks to his phreaking skills, first got through to the radio station KIIS-FM, which allowed him to win a Porsche car as part of the ongoing competition. Compared to modern attacks, which allow millions of dollars to be dismissed - this is just a trifle, but then this story caused a very big resonance.

The nineties - this is the era of active development of the Internet, at the same time for criminal hacking is finally fixed. During the nineties, one of the most famous hackers of the twentieth century, Kevin Mitnick, who had hacked into the internal network of DEC, was convicted twice. Personal computers have already become relatively accessible to ordinary people, and no one really thought about security. A huge number of ready-made programs appeared, with the help of which it was possible to hack user computers without having any serious technical skills and abilities. What is worth only the well-known program winnuke, which allows you to send Windows 95/98 to the "blue screen" by sending a single IP packet. In general, the nineties are considered the golden years of dark hackers: there are plenty of opportunities for fraud, computer systems are connected via the Internet, and there are still no serious security mechanisms in mass OS.
Another distinctive feature of the nineties - a huge number of Hollywood films “about hackers” as an illustration of the fact that the hacking of computer systems is gradually becoming an “ordinary wonder” for the masses. Remember, almost every such film necessarily included some virus that blew up the monitors;). Maybe it was because of the film industry that users in the head had a stereotype that “security is a virus”, which, of course, helped many antivirus companies to make their fortune.
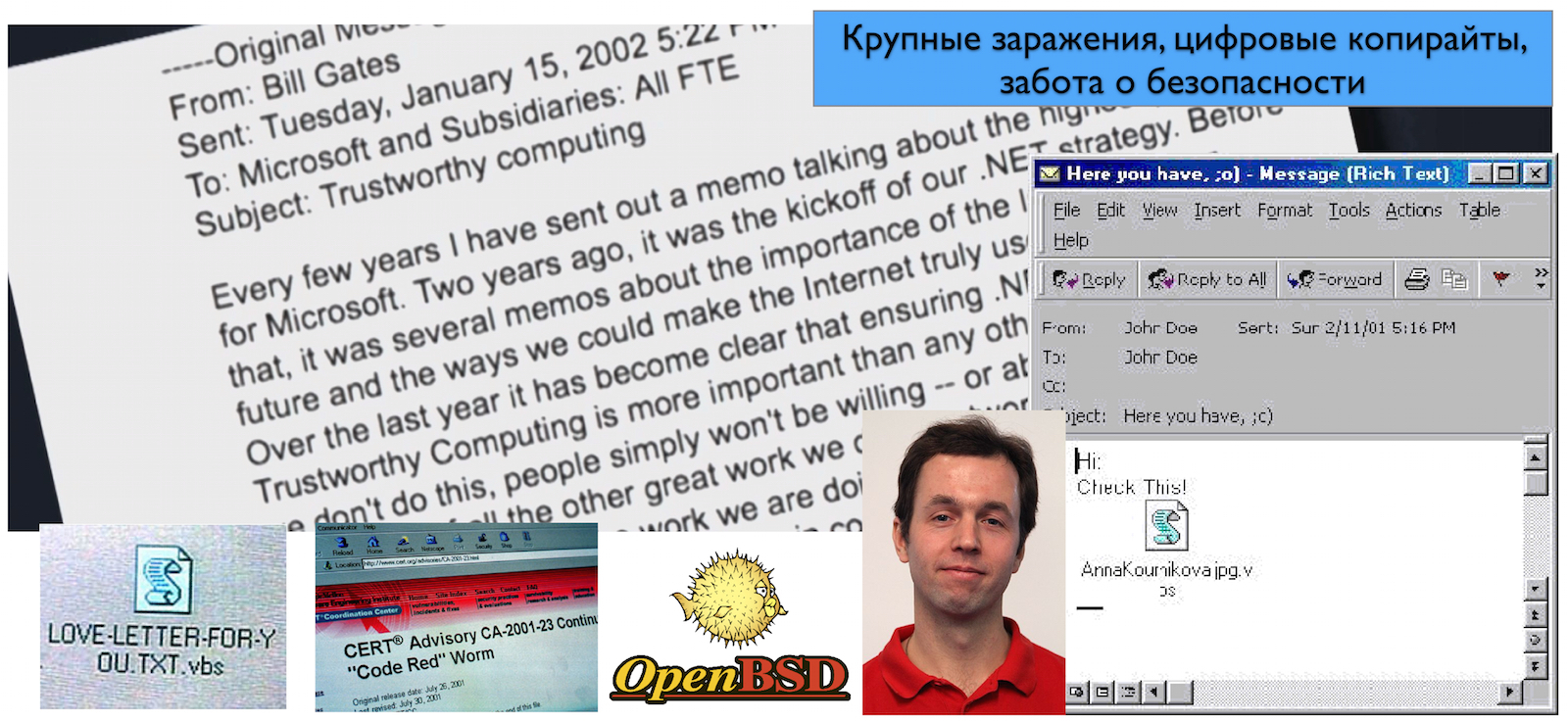
In 2002, Bill Gates wrote to his employees at Microsoft, stating that the situation needed to be corrected, and it was time to start developing software with an eye to security. This initiative is called “Trustworthy computing”, and it is still developing. Starting with Windows Vista, this idea began to come to life. The number of vulnerabilities in the OS from Microsoft has noticeably decreased, exploits for them are less likely to appear in public access. No matter how surprising it sounds, in terms of the security approach, the latest versions of Windows are much more reliable than other common operating systems. Thus, in OS X, only recently mechanisms began to appear that make exploitation of vulnerabilities more difficult.
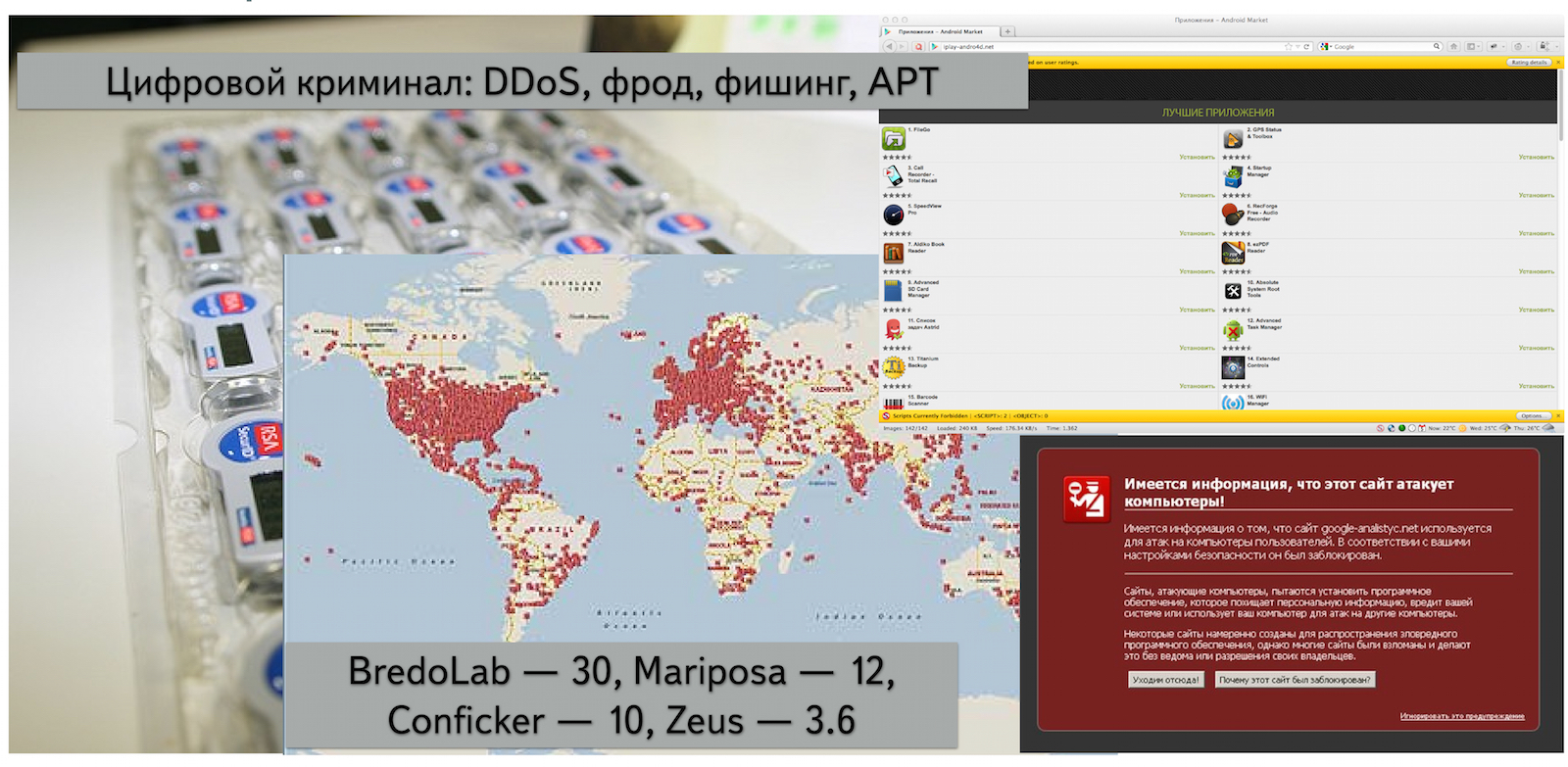
Zero years of our century. Digital crime is breaking new ground. Communication channels have become thicker, it has become easier to make massive DDoS attacks. No one is engaged in hacking computer systems just for fun, this is a multi-billion dollar business. Botnets are flourishing: huge systems made up of millions of infected computers.
Another characteristic feature of the last decade is the fact that the attacker's focus has shifted to the user, to his personal computer. Systems are becoming more complex, a modern browser is no longer just a program that can render HTML, display text and images. This is a very complex mechanism, a full-fledged window to the Internet. Almost no one uses individual instant messengers and email clients anymore, all interaction with the Internet occurs via the browser. It is not surprising that one of the main methods of infecting users in our days - drive-by-downloads - happens just with the help of a browser. Of course, in modern browsers, mechanisms to combat this have begun to appear, users are trying to warn that the visited site can be dangerous. But the browser still remains one of the main intermediaries in infecting user machines.
Another major malware distribution channel is mobile devices. If in the official app stores the program somehow checks for harmfulness, then from unofficial sources you can put practically anything on your device. And in general, the security of mobile devices now is a rather young and a bit messy industry, which is connected with the speed with which modern mobile platforms burst into our lives.

Let's summarize what hacking is today and what we should expect in the near future. At the beginning of the two thousandths, if any vulnerability was found in Windows, an exploit appeared almost immediately in free access, which allowed to get control on the user's computer. Then over the monetization of vulnerabilities almost never thought. Of course, there were programs that stole user data, drove computers into botnets, but the vulnerabilities themselves that compromised a computer were relatively easy to exploit, and therefore, to write an exploit. For about the past five years, it has become very difficult to find a working exploit for a newly discovered vulnerability in public access. Now it is a huge business. After all, it is much more difficult to write an exploit for a vulnerability in a system in which mechanisms like DEP and ASLR are implemented.
Recent years also show that all of us are waiting for the security problems of the so-called “Internet of Things”. Computers with Internet access are now increasingly in one form or another present in a wide variety of household and medical devices, as well as cars. And the vulnerabilities in them are exactly the same as in ordinary computers. Studies on breaking into things familiar to us are becoming a popular topic at the world's leading security conferences. After all, if attackers begin to take advantage of such vulnerabilities, this will pose a serious danger to the health and lives of users. The more important is the role of a security professional.
Like it or not, and information security is strongly associated with many hackers. Therefore, I want to tell you today about hackers and their history. Nowadays, a hacker is an attacker who does something illegal, hacks some systems with material gain for himself. But this was not always the case.

')
Let us go back half a century ago, in the 1960s, when computers gradually began to penetrate our lives. Hacking began even then, with attempts to use equipment for other purposes. For example, to run on it the same written game. In those days, the concept of "hacker" is a very enthusiastic person trying to do something unusual with the system. After all, access to computers was mainly among university employees, and not much was allocated to everyone’s processor time. You, literally, were allowed to work with a computer only a few hours a week, on a strict schedule. But even in such conditions, people managed to find time for experiments. Hackers of that time were interested in not just solving some computational problem, they wanted to understand how the machine works and works. The culture of hacking came from very enthusiastic people.

In the 70s, hacking was finally formed as an attempt to “play” with the information system, bypassing its limitations. There was no Internet then, but there was already a telephony. Therefore, there was such a thing as phreaking. The father of the phreaking is considered to be John Draper, known by the nickname “Captain Crunch”. Once he found a gift in the Captain Crunch cornflakes, a whistle. Telephone lines at that time were analog and telephone sets communicated with each other through the exchange of tones. It turned out that the tone of the whistle detected by Draper coincides with the tone used by the telephone equipment to transmit commands. Phreakers (so called enthusiasts of "games" with ATS) began using whistles to emulate a system of commands and dial free of charge from street phones to neighboring cities and states. The next step was the creation of a “blue box” - a device that emulated all the same tone commands. He allowed not only to dial the necessary numbers, but also to use secret service lines. By giving a signal at a frequency of 2600 Hz, it was possible to transfer telephone systems to administrative mode and get through to numbers that are not available to the average person, for example, to the White House. Entertainment continued until the late 80s, when a popular newspaper published a large article about the “blue box”, which attracted the attention of the police to phreakers. Many phreakers, including Draper himself, were arrested. Later still managed to figure out what they did it all not for the sake of money, but rather from sports interest and self-indulgence. At that time, the criminal code simply did not have any articles related to fraud with information systems, so that soon all phreakers were released.

In the 1980s, the word “hacker” first gained a negative connotation. The image of a hacker as a person who can do something illegal for profit has already begun to form in people's minds. In 1983, one of the founders of the hacking group “414s” appeared on the cover of Newsweek, which became famous for a series of hacks of serious computer systems. Hackers have their own magazines and other ways to exchange information.
During these years, the authorities of Western countries are beginning to form laws related to computer security. However, the scale, of course, can not be compared with today. So, a lot of noise happened around the case of Kevin Polesen, who, thanks to his phreaking skills, first got through to the radio station KIIS-FM, which allowed him to win a Porsche car as part of the ongoing competition. Compared to modern attacks, which allow millions of dollars to be dismissed - this is just a trifle, but then this story caused a very big resonance.

The nineties - this is the era of active development of the Internet, at the same time for criminal hacking is finally fixed. During the nineties, one of the most famous hackers of the twentieth century, Kevin Mitnick, who had hacked into the internal network of DEC, was convicted twice. Personal computers have already become relatively accessible to ordinary people, and no one really thought about security. A huge number of ready-made programs appeared, with the help of which it was possible to hack user computers without having any serious technical skills and abilities. What is worth only the well-known program winnuke, which allows you to send Windows 95/98 to the "blue screen" by sending a single IP packet. In general, the nineties are considered the golden years of dark hackers: there are plenty of opportunities for fraud, computer systems are connected via the Internet, and there are still no serious security mechanisms in mass OS.
Another distinctive feature of the nineties - a huge number of Hollywood films “about hackers” as an illustration of the fact that the hacking of computer systems is gradually becoming an “ordinary wonder” for the masses. Remember, almost every such film necessarily included some virus that blew up the monitors;). Maybe it was because of the film industry that users in the head had a stereotype that “security is a virus”, which, of course, helped many antivirus companies to make their fortune.

In 2002, Bill Gates wrote to his employees at Microsoft, stating that the situation needed to be corrected, and it was time to start developing software with an eye to security. This initiative is called “Trustworthy computing”, and it is still developing. Starting with Windows Vista, this idea began to come to life. The number of vulnerabilities in the OS from Microsoft has noticeably decreased, exploits for them are less likely to appear in public access. No matter how surprising it sounds, in terms of the security approach, the latest versions of Windows are much more reliable than other common operating systems. Thus, in OS X, only recently mechanisms began to appear that make exploitation of vulnerabilities more difficult.

Zero years of our century. Digital crime is breaking new ground. Communication channels have become thicker, it has become easier to make massive DDoS attacks. No one is engaged in hacking computer systems just for fun, this is a multi-billion dollar business. Botnets are flourishing: huge systems made up of millions of infected computers.
Another characteristic feature of the last decade is the fact that the attacker's focus has shifted to the user, to his personal computer. Systems are becoming more complex, a modern browser is no longer just a program that can render HTML, display text and images. This is a very complex mechanism, a full-fledged window to the Internet. Almost no one uses individual instant messengers and email clients anymore, all interaction with the Internet occurs via the browser. It is not surprising that one of the main methods of infecting users in our days - drive-by-downloads - happens just with the help of a browser. Of course, in modern browsers, mechanisms to combat this have begun to appear, users are trying to warn that the visited site can be dangerous. But the browser still remains one of the main intermediaries in infecting user machines.
Another major malware distribution channel is mobile devices. If in the official app stores the program somehow checks for harmfulness, then from unofficial sources you can put practically anything on your device. And in general, the security of mobile devices now is a rather young and a bit messy industry, which is connected with the speed with which modern mobile platforms burst into our lives.

Let's summarize what hacking is today and what we should expect in the near future. At the beginning of the two thousandths, if any vulnerability was found in Windows, an exploit appeared almost immediately in free access, which allowed to get control on the user's computer. Then over the monetization of vulnerabilities almost never thought. Of course, there were programs that stole user data, drove computers into botnets, but the vulnerabilities themselves that compromised a computer were relatively easy to exploit, and therefore, to write an exploit. For about the past five years, it has become very difficult to find a working exploit for a newly discovered vulnerability in public access. Now it is a huge business. After all, it is much more difficult to write an exploit for a vulnerability in a system in which mechanisms like DEP and ASLR are implemented.
Recent years also show that all of us are waiting for the security problems of the so-called “Internet of Things”. Computers with Internet access are now increasingly in one form or another present in a wide variety of household and medical devices, as well as cars. And the vulnerabilities in them are exactly the same as in ordinary computers. Studies on breaking into things familiar to us are becoming a popular topic at the world's leading security conferences. After all, if attackers begin to take advantage of such vulnerabilities, this will pose a serious danger to the health and lives of users. The more important is the role of a security professional.
Source: https://habr.com/ru/post/244559/
All Articles