Sniff the output Tor node and analyze the resulting content.

The concept of “network over network” did not appear yesterday. Back in the middle of the last decade, Hacker wrote about onion and garlic routing in the person of Tor and I2P, and even published reviews of the relevant software in the Sharowarez category, but real interest in them in society appeared on the wave of well-known recent information shows and loud exposures. What are the darknets? Who lives there? What are they interested in, what do they breathe, what do they buy and what do they sell? Let's try to deal with this hacker: using sniffer and direct immersion.
WARNING
All information is provided for informational purposes only. Neither the editors nor the author are responsible for any possible harm caused by the materials of this article.
Onion Domain Monitoring System
Each resident of the network can provide its computing resources for the organization of the Node-server - the node element of the network, which acts as an intermediary in the information exchange of the network client. There are two types of nodes in this darknet: intermediate and output (the so-called exit node). The latter are an extreme link in the operation of decrypting traffic, and therefore represent the end point, which can become a channel for leaking interesting information.
Our task is very specific: it is necessary to collect existing and, most importantly, relevant onion-resources. At the same time, one cannot completely trust the internal search engines and site directories, because the relevance of the information contained in them, as well as its completeness, leaves much to be desired.
')
However, the solution to the problem of aggregation of relevant sites lies on the surface. In order to compile a list of recently visited onion-resources, it is necessary to track the fact of access to them. As we have said, the exite node is the end point along the path of the encrypted pacts, which means we can freely intercept packets of HTTP / HTTPS protocols of the Tor user who surfs in the “traditional web”.
It is known that the HTTP packet may contain information about previously visited resources. The data is in the Referer request header, which may contain the URL of the source of the request. In the “traditional web”, this information helps webmasters to determine which search engine queries and sites from which users of a controlled web resource come from.
In our case, it is enough to run through the dump of the intercepted traffic with a regular expression containing the string onion.
Passive monitoring system
There is a huge amount of available articles about configuring exit node, so here we will not focus on the configuration process of the output node, but we will only note the most important.
First, in the torrc configuration file, you need to set an Exit Policy that allows traffic to be transmitted across all ports. This setting is not some kind of magic manipulation and only gives hope to "see" something interesting on a non-trivial port.
>> ExitPolicy accept *:* The Nickname field does not carry any meaning, so the only recommendation in this case is not to use compromising node names (for example, WeAreCapturingYourTraffic) and not to use numbers that may give rise to the idea of a whole network of similar nodes (for example, NodeNumber3).
After starting the Tor server, you need to wait until the process of uploading its coordinates to the server of directories is completed - this will help our node to “declare” all the participants of the darknet about themselves.
After we have raised the output node and have already started passing through the traffic of the Tor-users, it is necessary to start the packet sniffer and catch the passing traffic. In our case, tshark acts as a sniffer, which listens to interface # 1 (Tor hangs on it) and kindly puts the dump into the dump.pcap file:
>>tshark -i 1 -w dump.pcap All the described actions should be carried out for as many servers as possible in order to gather more interesting information. It is worth noting that the dump is growing quite quickly and must be periodically taken for analysis.
Malvar and darknet
More and more malware (mobile and desktop Trojans) is able to work with its C & C servers located in Tor. The advantages compared with the classical approach to managing a botnet are obvious: you don’t need to worry about getting a domain into the blacklists of providers, it’s not practical (impractical - it’s not a synonym for impossible ’) to identify the botmaster, and, due to the darknet architecture, it’s impossible to“ turn off ” server.
So, one of the first to start working with Tor was the ZeuS banking trojan, the developers of which pulled the tor.exe utility along with their malware. By introducing it into the svchost.exe process, the villains thereby initiated a secure connection of their offspring with the command server. The reasons are clear - it is unlikely that someone will come running and de-energize your server or even worse - take it under the hood.
Six months after the appearance of the Tor-botnets, the functionality for working with onion-domains begins to be introduced into mobile Trojans, and now the virus makers have stopped using fully prepared Tor-clients, and they are implementing their implementations and changing the existing solutions.
Thus, many onion-domains at the moment are nothing more than a means of administering a particular botnet.
Administrative panel of one of the botnets
Fragment of the source code of one of the mobile malware
Active system
Before turning to the results obtained during the operation of the passive monitoring system, we will discuss the concept of an active system. Until now, the idea of intercepting data passing through Tor output nodes was in the air. In this case, the system has a passive concept of collecting information, and its operators have to be content with the results that fall into their “networks”. However, much more information can be obtained about the darknet’s internal resources if the concept of an active monitoring system is used to gather it.
A prerequisite for the normal exchange of information with external Internet resources through the exit node is the presence of a response from the web server, which our output node must deliver to the Tor-user. Otherwise, if only unanswered requests to web servers go through the node, we can conclude that a DDoS attack is taking place.
The main point of the active system is the ability to organize a MITM attack: we can redirect the user to a web resource under our control or add our code to the content of the response in order to provoke a leak of any information from the client browser.
The topic of de-anonymization of the user and the description of her technician require a separate article, but it can be concluded that a number of her technician can help in obtaining information about current resources. The task is not trivial, and it can be approached in a number of ways.
In this case, it all depends on the owner’s fantasy exit node. For example, you can use social engineering techniques and provoke (on behalf of the administration of the requested resource) the resident of the darknet to send any information about yourself and the resources visited. As an alternative, you can try to load a “payload” on the victim’s side.

Exit node in the course of its operation

Tshark catches packets that pass through the exit node in clear text
Traditional web technologies can also help in this task. For example, cookies that website owners use to obtain statistical information about visitors. It should be noted that cookies have a limited lifetime and, in addition, the user can delete them at any time. For this reason, developers use various tricks to increase the lifetime and amount of information stored in cookies.
One way is to use the Flash repository, in which case the information is stored in LSO files (local shared objects), which are similar to cookies and are also stored locally on the user's computer. In addition, there is an even more powerful tool for working with cookies - the evercookie javascript library. This library provides the ability to create hard-to-delete cookies by using common HTTP cookies, LSO files and HTML5 tags at the same time. And all this information can be retrieved by an active monitoring system.
Darknet Heroes
Like Zuckerberg and his Facebook, the darknets have their heroes. On the pages of our magazine one could read about Ross William Ulbricht and his Silk Road project, the visitor of which could order any “means of delivery to the next world” - from drugs to weapons. The popularity of the project brought the scale of its business, but this does not mean that the site was the only one of its kind. With each announcement of the closure of Silk Road, like mushrooms after rain, alternatives appeared in the form of small shops selling prohibited substances. Moreover, a group of anarchist developers, taught by “silk” experience, presented the concept of the DarkMarket store, which is devoid of the drawbacks of traditional darknet stores. However, this decentralized site has yet to reach an audience, while a significant portion of Tor users already contribute to the ecosystem of existing sites.
Dark web spiders
So, having received a huge dump at your disposal, you should analyze it for onion-resources. A cursory reading of the dump “diagonally” allowed us to make up the categories of web applications of the darknet and derive a psychological portrait of a typical Tor-user.

An example of an onion resource logged
It should be noted that per day (weekday) of continuous traffic interception a dump of one node grows to 3 GB. So, simply opening it with Wireshark will not work - the program will simply choke on such a large file. To analyze the dump, it is necessary to split it into files no larger than 200 MB in size (determined empirically). To do this, along with Wireshark is the editcap utility:
>> editcap -c 200000 input.pcap output.pcap In this case, the value 200,000 is the number of packets in one file.
When analyzing a dump, our task is to search for strings containing the substring ".onion". We are very likely to find the internal resources of Tor.
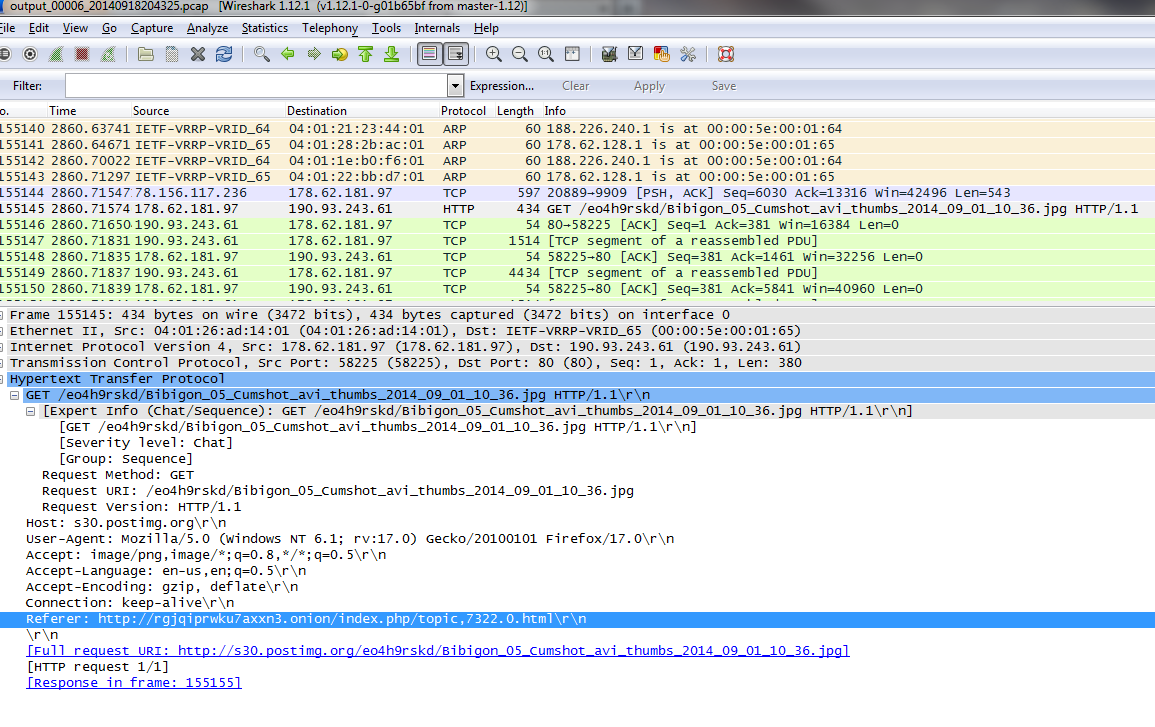
Example of a Referer Content Header
So, what are the interest of darknet users? From the onion-resources that have fallen into our networks, we have compiled a small list.
Adult, intimate services.
Pornography, resources with girls of easy behavior and various forums to increase the "physical" characteristics of many in the external network, and inside the darknet. As they say, no comment.
Resource offering intimate services
Politics.
It turns out that they are also interested in politics here! In our dump, a sufficiently large number of Ukrainian web resources located in the external network was found.
Prohibited content.
Various materials on the construction of prohibited devices (bomb), a description of psychotropic substances with the possibility of their acquisition were actively visited. Logically: a rare individual surfit through the darknet classic external web resources.
Marketa

A typical dark market product catalog
Darknet and their web resources are a real bazaar of all kinds of illegal goods. The abundance of markets with drugs and weapons is manifested not only in the form of links leading from external Internet resources to the darknet, but also in the referrer of Tor-users.
These resources offer not only various types of chemical compounds, but also material for fans of the Breaking Bad - those who like to make drugs with their own hands. Moreover, the creators of such sites provide their customers with a service no worse than any AliExpress - there is a system of discounts for regular customers and a refund for low-quality goods. There is also some sort of transaction codes to track order status.
Let's try to visit the classic darknet market. After a short registration procedure, where only a login and password are requested from us, we get into the control panel of our “cryptocurrency” account. The interface of the market is designed in such a way that the user is not distracted by extraneous controls and enjoys an abundance of offers of all kinds of nishtyakov.
Caution Big Data
Within 24 hours of continuous traffic interception, a 3 GB dump is generated at the output node.
Costing:
10 nodes × 3 GB × 7 days = = 210 GB. If you want to participate in the process of parsing the accumulated information - write me an e-mail.
The largest number of positions is observed in the categories with narcotic substances, recipes and some abstract “Digital Goods” - look here. We sort by descending price and see that the most expensive items in this category are stolen account bases. There is plenty to choose from: from expensive bank accounts (the cost of the base is about a thousand dollars) to the recently leaked bases from online services.
By the way, the “leaked” accounts of Yahoo and Google have very positive reviews - and this means that the people who acquire them are incompetent in matters of information security. Invites to other resources, dubious and “secret methods of earning on the Internet” are all pretty monetized.
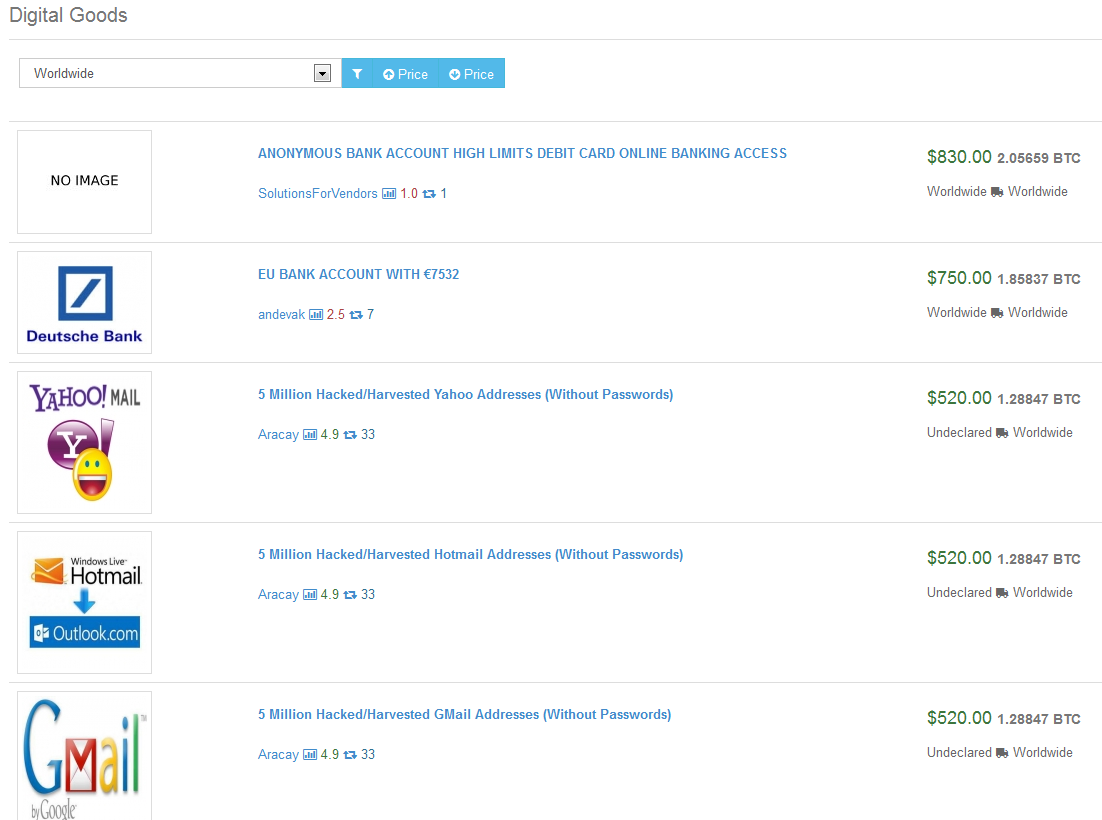
Costly Digital Goods Representatives
Another market met us with a dubious interface and the same category of Digital Goods, where the subcategory with the interesting name 0day was discovered, in which ... the same "new secret recipes" turned out to be. Conclusion: traditional cybercrime offers are practically absent in traditional Darket markets.

Such are the "zirodede" ...
Remarkable is the fact that on some large sites there are reward programs for found vulnerabilities (bug bounty).
True, the quality of reports is none - mostly “bugs” are more likely to be visual. In addition, the store forums are filled with messages: “Am I anonymous if I buy drugs from you from my iPad?”
Among the garbage and flooding there are proposals for money laundering. As the description of services says, the user transfers his bitcoins and for a small percentage of the service owners distribute this money into a lot of controlled wallets, thereby initiating a multitude of transactions.
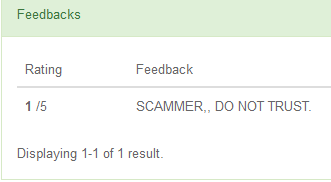
Fidbek for "Digital goods": carefully scam!
For those who wish to raise their own market in the darknet, but do not understand anything in the process of developing web applications, on the Internet open-ended groups of developers who specialize in such services.
The cost of developing a resource for the darknet is not very different from the market prices for typical online stores, but there is a specificity here. For example, payment to these developers occurs exclusively through cryptocurrency.

Services of web application developers for darknet
Closed resources
Quite often we came across various resources closed to the eyes of the ordinary visitor. One can only guess about the content hidden behind them: perhaps this is another forum or a market, perhaps this is the admin of some botnet. Very rarely, a closed resource asked for a name and password - more often we just ran into a 404 error, but at the same time recent logs on web resource scripts were recorded in the logs.
Exploit trojans
In our logs there was not a single resource on this topic. However, this is how a representative of a “closed community of information security specialists” comments on this situation:
“Darknets in general, and Tor in particular, have not made any changes to standard cybercrime business processes. The sites where malware is sold, exploits for vulnerabilities, sploit packs, etc., still remain in the external network. There is simply no need to go on darknets - it cuts off the solvent audience and customers, complicates the service. Malware developers want to maximize their communication with customers, and in this process Tor is an inconvenient and questionable tool. Only from the point of view of the functioning of Malvari darknet is a good means of preserving the botnet admin panel. As for the card pads, carders are very greedy and lazy people. Why go to the darknet, if it is enough to restrict access to content by standard means of web engines? Or enter a membership fee for participation in the forum? Zero-day vulnerabilities are already hard to find, not only in the darknet, but also in closed areas on the traditional web. Exploiters are now working in teams and directly with specific customers, so now they hardly need forums, much less darknets. ”

Example of a closed area
The process of “googling” inside Torion onion-resources gave several links to sellers of the ZeuS banking trojan, but all these links were inside a large market that, along with the Trojan, sells drugs and similar stuff.
Not by Tor'om
The technological essence of the darknet boils down to the organization of an additional network layer that runs on top of the IP protocol. All this makes it possible to perform anonymous data transfer (Tor) and in some cases anonymously host your web application (I2P).
It is worth noting that Tor is more focused on preserving the anonymity of the information exchange participant, while I2P and Freenet are more suitable for implementing anonymous hosting. Darkers' content diggers cannot be ignored by I2P and Freenet, a small anonymous peer-to-peer network, because this is a real “quiet pool”.
I2p
After installing the I2P Java client on page 127.0.0.1:7658, a “stub” appears for the local site. In order for this site to be visible to all participants of this darknet, you need to configure the tunnel. For addressing within the network, identifiers are used, which are Base64 strings. To match a hard-to-read identifier with a unique name of our project (for example, project.i2p), you need to register a domain name for this identifier. Do not let the lack of a domain name system bother you - it simply does not exist, since it would in itself be a “narrow neck” in the work of the network, that is, would pose a threat to the integrity of the transmitted information.
DNS is implemented as a distributed hash table storage system. After a unique address has been created (the internal service allows to be convinced of its uniqueness), you can activate the project. Information about the project should be entered into the distributed address storages, after which it will be distributed among all users of the network. This fact simplifies the collection of information on internal resources.
Coming to light
Do not take to heart the assertions about absolute anonymity on the darknet: more and more studies are proving that anonymity in Tor and similar networks is just an alternative to other means of protecting yourself from the attention of your neighbor. The darknet is currently only hope for anarchists (and those who want to increase their “device”), a market for drug addicts and a field for research.
Using the passive monitoring system, we were able to determine the target audience of the darknet, rummaged a little in the current content and found the starting point for an active monitoring system, which, in turn, has a chance to firmly answer the question whether there is anonymity on the darknet.
Thanks
Thanks to Amiran Gebenov for help in configuring and administering the described monitoring system.
The author: Denis Makrushin

First published in Hacker magazine dated 09/2014.
Subscribe to "Hacker"
Source: https://habr.com/ru/post/244485/
All Articles