IPv6 at gunpoint

It would seem, why now generally remember about IPv6? Indeed, despite the fact that the last blocks of IPv4-addresses were distributed to regional registrars, the Internet works without any changes. The fact is that IPv6 first appeared in 1995, and its entire title was described in the RFC in 1998. Why is it important? Yes, for the reason that it was developed without taking into account threats, with the same trust scheme as IPv4. And in the development process, there were tasks to make a faster protocol and with a larger number of addresses, and not a safer and more secure one.
Briefly about the growth rate
If you examine the graphs provided by the regional registrar of IP addresses and autonomous systems, you may find that as of September 1, 2014, the number of registered IPv6 autonomous systems has already exceeded 20%. At first glance, this is a serious figure. But if you take into account only the real amount of IPv6 traffic in the world, now it is about 6% of all global Internet traffic, although just three years ago it was only 0.5%.
')

Fig. 1. Real volume of IPv6 traffic
By the most conservative estimates, it is expected that by the end of 2015 the share of IPv6 traffic will reach at least 10%. And the growth will continue. In addition, a special protocol for regional registrars has recently entered into force. Now a new block of IPv4-addresses will be issued only if the company proves that it has already implemented IPv6. Therefore, if someone needs a subnet of white IPv4 addresses, they will have to implement IPv6. This fact will also serve to further increase IPv6 systems and increase traffic. As for ordinary users, providers around the world began to emerge, which provide end-users with honest IPv6 addresses. Therefore, IPv6 will occur more and more often, and we cannot ignore this.
What's new in IPv6?
The first thing that catches your eye is the addresses. They are longer, written in hexadecimal form and difficult to remember. Although, after working for some time with IPv6, you find that the addresses are generally memorized, especially if abbreviated forms of recording are used. Recall that IPv4 uses 32-bit addresses that limit the address space of 4,294,967,296 (2 ^ 32) to possible unique addresses. In the case of IPv6, 128 bits are already allocated for the address. Accordingly, addresses are available 2 ^ 128. This is about 100 addresses for each atom on the surface of the Earth. That is, the address should be enough for quite a long time.
Addresses are written as eight groups of hexadecimal values. For example, an IPv6 address might look like 2001: DB8: 11 :: 1. It is important to note that there may be several IPv6 addresses on one interface, and this is a standard situation. For example, the interface may have a private address, a white address, and another DHCPv6 address will arrive at an additional address. And everything will work properly, for each task will use your address. If you need to go out into the world, the white address will be used. Need to neighbor server? Will go through a private address. All this will be solved by the usual analysis of the destination field.
All IPv6 addresses are divided into two groups: link locale and global unicast. By name, it is obvious that Link local is an address that is used only within one link. Such addresses are further used to operate a number of mechanisms, such as automatic address configuration, neighbor discovery, in the absence of a router, and the like. Such addresses are not allowed to enter the world.
Link local address is assigned automatically as soon as the host goes online, something remotely such addresses are similar to the APIPA mechanism in Windows. Such an address always starts with FE80, but the last 64 bits is the MAC address with FFFE inserted in the middle, plus one bit is inverted. The mechanism for the formation of such an address is also called EUI-64. As a result, the address will be unique, as the MAC addresses are usually different for all hosts. But some operating systems use a random identifier instead of the EUI-64 mechanism.
What are other news
Only the addresses of the change, of course, do not end. The title was also significantly simplified (see Fig. 2).
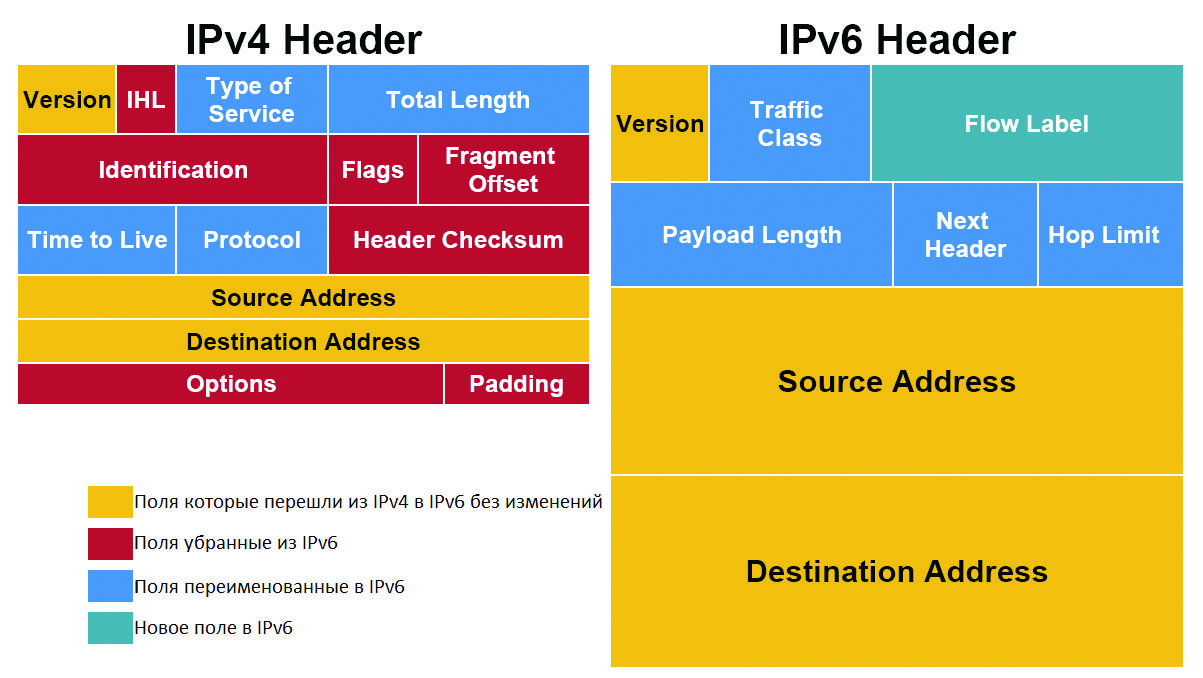
Fig. 2. Comparing IPv6 and IPv4 Headers
Now everything that is not necessary for routing a packet from point A to point B has become optional. And once optional, it moves to the extension header, which lies between the IPv6 header and TCP / UDP data. In this very extension-header, fragmentation, IPsec, source routing, and many other features already live.
The routers have been drastically simplified because there is no need to recalculate checksums, and as a result, IPv6 is processed faster than IPv4. Checksums removed altogether. First, the frame at the L2 level has a CRC, and second, the upstream protocols (TCP) will also ensure the integrity of the delivery. As a result, extra fields were thrown out of the header, it became easier, faster and more reliable.
Autoconfiguration and service protocols
There are two main options for assigning IPv6 addresses: stateless autoconfiguration is when the router sends clients the network address, default gateway and other necessary information, and statefull autoconfiguration when using a DHCPv6 server. Therefore, if earlier DHCP was the only option for distributing information, then in IPv6 it became additional.
ICMP version 6 also did not go unnoticed, many features were added to it. For example, the mechanism of Router discovery - clients can listen to what the router tells them (ICMPv6 type 134 router advertisement messages that come as part of the stateless autoconfiguration process), and when turned on, they can immediately call the router to help, they say, help them configure (ICMPv6 type 133 messages router solicitation).
Another added mechanism is Neighbor discovery - we can say that this is a kind of ARP replacement, which helps to find the mac addresses of neighbors, routers, and even detect duplicate addresses in a segment (duplicate address detection DaD), works exclusively on multicast. There is no clean Broadcast in IPv6, but one should not forget that stupid penny switches are broadcasting the whole multicast, in the end some of the new mechanisms are reduced to nothing.
IPv6 Pentester Toolkit
Before proceeding to the vulnerabilities and attacks, it would be nice to consider what tools there are in the pentester's arsenal. Until recently, there was only one set of utilities for carrying out attacks against the IPv6 and ICMPv6 protocols. It was THC-IPV6 from the notorious Mark van Hauser, the same author of the THC-hydra brute-forcer, and a host of other indispensable tools. It was he who in 2005 seriously became interested in this topic and came to grips with IPv6 protocol resolution. And until recently, remained a pioneer.
But in the last year the situation began to change. More and more researchers are turning their attention to IPv6, and, accordingly, new utilities and new scanners have begun to appear. But for today THC-IPV6 still remains the best set of utilities for pentester. It includes more than 60 tools, divided into various categories - from scanning and mitmes to fluding and fuzzing. But let's not forget the labor tool scapy, a utility that allows you to manually create any packages, with any headers, even if such variations are not provided for in any RFC.
Exploration in IPv6 networks
Before attacking a target, you need to somehow find it, so standard pentest usually begins with a search for live hosts. But a problem appears here: we cannot scan the entire range. Scanning just one subnet will drag on for years, even if you send a million packets per second. The reason is that only the subnet / 64 (or they are also called prefixes) is larger than the entire Internet today, and much more. Therefore, the most serious problem with IPv6 is target detection.
Fortunately, there is a way out. First you need to find the AS (autonomous system), which belongs to the target (object pentest). There are quite enough services that allow searching by AS of their owners, you can do it directly on the websites of regional registrars (the European registrar is the RIPE NCC). Then, knowing the AS number belonging to a particular company, you can already search for the IPv6 subnets assigned to it.
The most convenient such search service is Hurricane Electric (bgp.he.net). As a result, you can find several huge subnets, which, as we have seen, it is unrealistic to scan for live hosts. Therefore, it is necessary to compile a list of frequently used addresses and scan them already dotted over them.
How can I build such a dictionary? If we analyze how in companies that have already implemented IPv6, addresses are assigned to clients, then we can distinguish three main groups: autoconfiguration, manual address assignment, and DHCPv6.
Autoconfiguration can be done in three ways: based on the mac address, using the privacy option (that is, randomly and, for example, changing once a week) and fixed random (completely random). In this situation, it is possible to scan only those addresses that are based on poppy. As a result, subnetworks comparable in size to class A IPv4 may come out; the process of working with such networks is not very fast, but still it is quite real. For example, knowing that the target company uses the laptops of a certain vendor in large quantities, you can build a scan based on the knowledge of how the address will be formed.
If the addresses are set manually, they can be assigned either randomly or by some pattern. The second, of course, is more common in life. And the pattern can be :: 1, :: 2, :: 3 or :: 1001, :: 1002, :: 1003. Also, service ports are sometimes used as an address, depending on the server: for example, a web server may have an address: 2: 80.
If we take DHCPv6, then in this case usually addresses are distributed sequentially from the pool (exactly the same behavior can be observed with a regular DHCPv4 server). Often in DHCPv6 you can find a pool like :: 1000-2000 or :: 100-200. Therefore, in the end, we take the alive6 utility (it is included in the THC-IPV6 kit and, like all the tools we are considering today, defaults to Kali Linux) and run:
# alive6 -p eth0 2001:67c:238::0-ffff::0-2 Alive: 2001:db8:238:1::2 [ICMP echo-reply] Alive: 2001:db8:238:3::1 [ICMP echo-reply] Alive: 2001:db8:238:3::2 [ICMP echo-reply] Alive: 2001:db8:238:300::1 [ICMP echo-reply] Scanned 65536 systems in 29 seconds and found 4 systems alive With such a detection of live machines, only the part responsible for the host address will change. Using this approach, it is possible to find live hosts in previously detected subnets quite effectively and within a reasonable time frame.
But that's not all - naturally, you can use the DNS. With the advent of IPv6, the DNS zone transfers and dictionary DNS brute-force have not gone away. By applying all these techniques together, you can detect up to 80% of all enabled hosts on a given IPv6 subnet, which is very good. In the case of the compromise of only one host, it will not be difficult to find all its neighbors using multicast. It will be enough to run the same utility, alive6, only with the -l key.
From the fresh features of THC-IPV6, and in particular the alive6 utilities, we can note the ability to search for live hosts, passing the whole IPv4 subnet as a pattern for iterating:
# alive6 -4 192.168.0/24 If we take the classical scan, then almost nothing has changed. The same Nmap, the same port scan options, the only difference is that now you can only scan one host at a time, but this is an obvious solution.
Perhaps the only additional technique for port scanning is IPv4 scanning at the beginning, and then obtaining IPv6 information on these hosts. That is a kind of expansion of the attack surface. To do this, you can use either the auxiliary module of the meta-exploit ipv6_neighbor, or individual scripts ipv6_surface_analyzer. They work according to a similar principle - they take an IPv4 subnet as input, scan it, find live hosts, check ports for openness, and then, after determining the MAC address, calculate the IPv6 address from it and already try to work on it. Sometimes it really helps, but in some cases (privacy option) IPv6 addresses cannot be detected, even though they exist.
INFO
When using IPv4 and ARP, it was sometimes quite useful to watch the ARP cache; that on Linux, that on the Windows platform, this could be done using the arp -a command.
Now, in the case of IPv6, in Linux, the ip -6 neighbor show command is used to look at the neighbors, and in a Windows environment, this can be done with the netsh interface ipv6 show neighbors command.
IPv6 Perimeter Threats
If you look at the outer perimeter, you may find that many companies that have already begun to implement IPv6 are in no hurry to close their administrative ports (SSH, RDP, Telnet, VNC, and so on). And if almost everyone tries to somehow filter IPv4, then they either forget about IPv6 or don’t know that they need to be protected in the same way as in the case of IPv4. And if you can partially understand the IPv4 telnet used - for example, limited memory or CPUs do not allow full use of SSH - then every device that supports IPv6 today will simply support the SSH protocol. There are even cases when ISPs put IPv6 administrative ports on their routers into the world. It turns out that even providers are more vulnerable to IPv6 attacks. This happens for various reasons. Firstly, there are not so many good IPv6 firewalls, and secondly, they still need to be purchased and configured. Well, the main reason - many do not even suspect the threat of IPv6. There is also an opinion that as long as there are no IPv6 hackers, Malvari and IPv6 attacks, then there seems to be no defense against anything.
Threats waiting inside LAN
If you recall IPv4, then there are three attacks that are still effective on local networks - ARP spoofing, DHCP spoofing, as well as ICMP redirects (this class of attacks was covered in detail during my performance on PHDays, so you can search corresponding video on the web).
In the case of IPv6, when the attacker is in the same local segment as the victim, the situation, oddly enough, remains about the same. Instead of ARP, NDP appeared, DHCP was replaced by auto-configuration, and ICMP was just updated to ICMPv6. It is important that the concept of attacks remained virtually unchanged. But in addition, new mechanisms like DAD were added, and, accordingly, new vectors and new attacks immediately appeared.
Neighbor Discovery Protocol (NDP) is a protocol by which IPv6 hosts can discover each other, determine the link-level address of another host (instead of ARP, which was used in IPv4), discover routers, and so on. In order for this mechanism to work, and it works with the use of a multicast, each time a link-locale or global IPv6 address is assigned to an interface, the host joins the multicast group. Actually, only two types of messages are used in the process of neighbor discovery: information request, or NS (neighbor solicitation), and information provision - NA (neighbor advertisement).
The interaction in this mode can be seen in Fig. 3

Fig. 3. Full time job ND
As a result, an attacker needs only to launch the parasite6 utility, which will respond to all NSs flying in a single segment (see Figure 4). Before that, you need to remember to enable forwarding (echo 1> / proc / sys / net / ipv6 / conf / all / forwarding), otherwise, it will not be a MITM attack, but a DoS.

Fig. 4. Parasite6 utility operation
The downside of such an attack is that the attacker will try to poison the ND cache of all hosts, which, firstly, is noisy, and secondly, is difficult in the case of large volumes of traffic. Therefore, you can take scapy and carry out this attack manually and precisely. First you need to fill in all the necessary variables.
>>> ether=Ether(src="00:00:77:77:77:77", dst="00:0c:29:0e:af:c7") , - , — - . >>> ipv6=IPv6(src="fe80::20d:edff:fe00:1", dst="fe80::fdc7:6725:5b28:e293") , ( ), — IPv6- . >>> na=ICMPv6ND_NA(tgt="fe80::20d:edff: fe00:1", R=0, S=0, O=1) The third variable needs to specify the correctly built NA packet, where ICMPv6ND_NA is ICMPv6 Neighbor Discovery - Neighbor Advertisement, and tgt is the router's address itself, which is advertised as the attacker's address. It is important to set all the flags correctly: R = 1 means that the sender is a router, S = 1 will say that the announcement is sent in response to the NS message, and O = 1 is the so-called override-flag.
>>> lla=ICMPv6NDOptDstLLAddr (lladdr="00:00:77:77:77:77") — Link local ICMPv6NDOptDstLLAddr (ICMPv6 Neighbor Discovery Option — Destination Link-Layer). - . >>> packet=ether/ipv6/na/lla , . >>> sendp(packet,loop=1,inter=3) The value loop = 1 says that you need to send infinitely, every three seconds.
In the end, after a while, the victim updates his neighbor’s cache and sends all traffic destined to the router right into the attacker's hands. It should be noted that in order to create a full-fledged MITM, you will need to run another instance of scapy, where the addresses will be inverted to poison the router. As you can see, nothing complicated.
It is also worth noting that in IPv6 there is no concept of gratuitous NA, as it was in the days of ARP (gratuitous ARP is an ARP response sent without a request). But at the same time, the ND cache does not live long and quickly becomes obsolete. It was designed to avoid sending packets to non-existent MAC addresses. Therefore, in the IPv6 network, NS - NA messaging occurs very often, which plays into the hands of the attacker.
End Host Threats
And since we started talking about RA, then we’ll move smoothly to the threats of end-hosts, and in particular to those hosts whose work with IPv6 was not planned. That is, we consider the attack on hosts operating in the default IPv6 configuration in a conventional IPv4 network. What happens if any modern OS gets an RA package? Since any system now supports IPv6 and expects such packets, it will immediately turn into a so-called dual stack. This is a situation where both IPv4 and IPv6 are used simultaneously within the same OS. At the same time, a whole series of previously inaccessible vectors will immediately open. For example, you can scan a target, because IPv4 is usually filtered, and IPv6, as we already know, is often not thought of at all.
In addition, in most OSs, IPv6 takes precedence over IPv4. If, for example, a DNS query arrives, then it is highly likely that IPv6 will work earlier. This opens up tremendous scope for various MITM attacks. For one of the most efficient, you will need to place your malicious IPv6 router. Each IPv6 router must join a special multicast group. This is FF02 :: 2. As soon as the router joins such a multicast group, it immediately starts sending messages - RA. Cisco routers send them every 200 seconds by default. Another caveat is that customers do not need to wait 200 seconds, they send an RS-message - Router Solicitation - to this multicast address and thus immediately require all the information. This whole mechanism is called SLAAC - Stateless Address Autoconfiguration. And accordingly, an attack on him with the obvious name SLAAC attack was developed.
The attack is that you need to install your router (you should not be taken literally, any Linux or even a virtual machine can act as a router), which will send RA messages, but this is only half the battle. Also, an attacker will need to start a DHCPv6 server, DNSv6 and NAT64 translator. As a service capable of sending RA messages, you can use Router Advertisement Daemon (radvd), this is an open source implementation of an IPv6 router. As a result, after the correct configuration of all the daemons, the victim will receive RA and turn into a dual stack, and all victim traffic will go completely unnoticed through IPv6.
On the attacker's router, this traffic will be overridden on normal IPv4 and then go to the real router. DNSv6 requests will also have priority and will also be processed on the attacker's side.
Thus, the attacker successfully becomes in the middle and can observe all traffic of the victim. And the victim will not suspect anything. Such an attack carries the maximum threat; it works even with the use of IPv4 firewalls and static ARP records, when it would seem that there is no way to affect the victim.
How to protect IPv6
If we talk about protection from the above attacks, it is first clear that at the perimeter, you must carefully filter all traffic and disable unused services, and special attention should be paid to administrative services. In order to reduce the impact of local attacks aimed at the ICMPv6 service protocol, you can limit the surface of such attacks by breaking large networks into subnets (what else is called microsegmentation). The same network infrastructure can be divided into several Vlans, with a separate IPv6 prefix for each such vlan. In this case, the attacker will be able to attack the hosts that are only in the same vlan with him, which already greatly limits the possible damage from the attacks.

Fig. 5. Scheme SLAAC attack
Fig. 6. Result of SLAAC attack
Separately, there is protection against false RA messages, which, as is known, should only come from routers. Cisco has implemented a feature called Router Advertisement Guard, which prevents the injection of untrusted RA messages by tagging potentially insecure ports. That is, RA packets will simply not be received from user ports. This feature works by analogy with DHCP snooping. The only drawback is that this feature is available only on a certain class of hardware - on catalysts of the 2960S, 3560 and 3750 series. In addition, in 2012, DHCPv6 Guard and NDP Snooping appeared, again, they are analogs of DHCP Snooping and Dynamic ARP Inspection from the IPv4 world . These protection mechanisms are available on the 4500/4948 Catalyst and on the 7600 Series routers.
If we consider the protection of end hosts, then all the latest versions of Windows allow you to completely disable the processing of RA-messages. If all IPv6 settings are configured manually, this can be a good option, although it breaks down the canonical IPv6 mechanisms somewhat. Turns off quite easily, right on the interface with the command
netsh int ipv6 set int X routerdiscovery=disabled where X is the interface index (you can view IPv6 interface indexes with the netsh int ipv6 show int command). The result is checked using the netsh int ipv6 show int X command.
If we consider the situation with the detection of attacks IPv6, then in general, everything is fine there. Detecting IPv6 attacks is easy enough, but for now they are difficult to prevent.
We finish the story
What we have in the dry residue? As it turned out, the IPv6 protocol itself is not safer, but at the same time, it is not more leaky than IPv4. The problem lies in the lack of knowledge and experience with this protocol. You need to filter IPv6 on the perimeter and turn it off if it is not used on end devices. Many people believe that IPv6 is much safer than IPv4, because IPv6 requires the use of IPsec. But this is a myth. Yes, IPsec can immediately work in an IPv6 environment, but it is never mandatory. IPv6 makes some things better, others worse, but most things are just different from what everyone got used to. In other words, IPv6 is no more or less secure than IPv4, IPv6 is simply unique and brings its own security considerations.
Author: Alexander Dmitrienko, PentestIT

First published in Hacker magazine dated 11/2014.
Subscribe to "Hacker"


Source: https://habr.com/ru/post/244383/
All Articles