Regin Trojan: Who is spying on GSM via Windows?
In several recent publications of our blog, we talked about the vulnerabilities of mobile networks , as well as the possibilities of wiretapping on the basis of such vulnerabilities. At the same time, readers in the comments have repeatedly expressed doubt that it is so easy to get into the operator’s internal technological network. However, a recent example with the Regin Trojan shows that this is not only possible, but has been done systematically for many years.
Reports about this Trojan recently released Symantec ( on Sunday ) and Kaspersky Lab ( on Monday ). In some details, they differ, but the general picture is this: the Trojan is a very serious development and is well hidden, most likely it was created at the state level (Symantec speaks directly of the Western intelligence service ), its main purpose is espionage, and the main targets of the attack are communication operators, through which this espionage was carried out.
')
According to the Symantec report, the Regin Trojan has been working covertly since 2008. In this case, spyware software is installed in four stages, traces of presence are carefully destroyed, so at the moment it is even difficult to say exactly how the attack begins - perhaps through infected sites or via instant messengers. Once installed, Regin can intercept traffic and logs, take screenshots, record clicks and mouse movements, read deleted files - in general, a complete spyware collection.
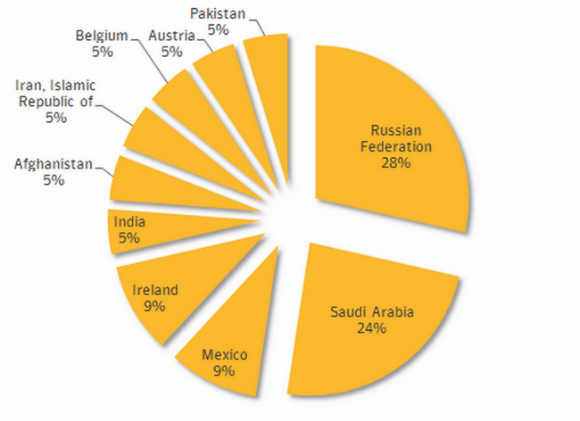
Most of the victims of this trojan, Symantec experts found in Russia (28%) and Saudi Arabia (24%), followed by Mexico and Ireland (9%), followed by India, Iran, Pakistan, Afghanistan, Belgium and Austria (5%). "Kaspersky Lab" gives a more extensive geography - traces of the Trojan were found in 14 countries, to the previous list were added Germany, Brazil, Indonesia, Malaysia, Syria, Algeria, as well as the harmless Pacific islands of Fiji and Kiribati.
At the same time, neither Symantec nor the LC do not speak directly who could have designed such a trojan. But they emphasize that such a serious development, which took months or even years, was most likely conducted “at the state level”.
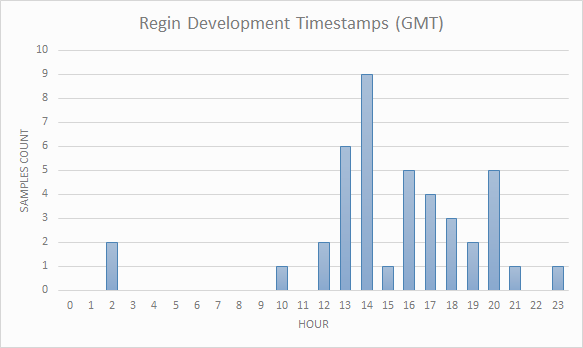
However, there are some additional hints in the reports. For example, Kaspersky Lab provides timestamps statistics (marks about the time at which the malware code was updated during development). According to the statistics obtained, it can be concluded that the Trojan authors work full time in the office. And even with a lunch break:
According to Symantec statistics, 28% of Trojan victims are telecoms, 48% are individuals and small businesses. The remaining infected - state, energy, financial and research companies. Kaspersky Lab clarifies that among the “individuals” the Trojan-spy was especially interested in characters who are engaged in mathematical or cryptographic research.
LK experts also note as the most interesting case of an attack on a large GSM-operator. They found a log according to which attackers using Regin gained access to the base station controller (Base Station Controller) and could change the settings, as well as execute various control commands. The log is dated 2008, but this does not mean that the virus has stopped working. Since that time, attackers could improve their “sweep marks” technique and stopped posting such logs.
Thus, we return to what this post started with: it’s not so difficult to get into the operator’s internal network. For example, because the components of the cellular network, including the base stations mentioned above, are built on a modular basis - new software controls roll over existing software that is not updated. As a result, the system not only retains all its vulnerabilities, but also acquires new ones.
In particular, for some operators a large number of critical systems, including OSS, stand on outdated and unpatched MS Windows. We talked about such security issues in more detail in the Five Nightmares for Telecom report on PHDays III ( slides , video ). And here we will give only one illustrative example of such a “discovery” - this was one of the security audits conducted by Positive Technologies experts:
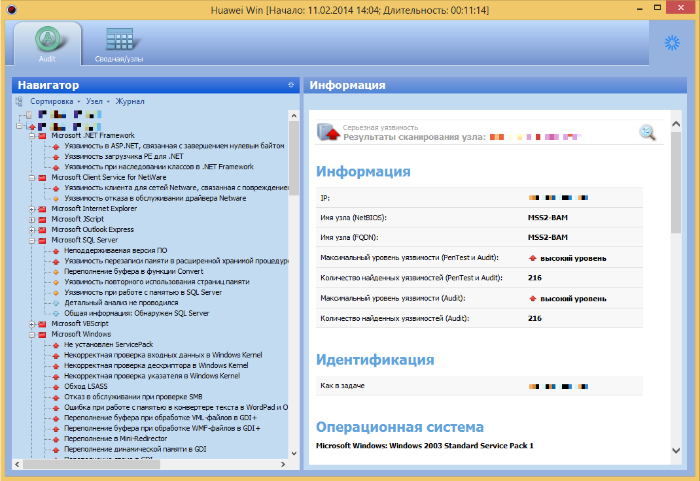
Vulnerabilities can be present not only in the operating system, but also in telecommunications equipment, the correct setting of which is very important.
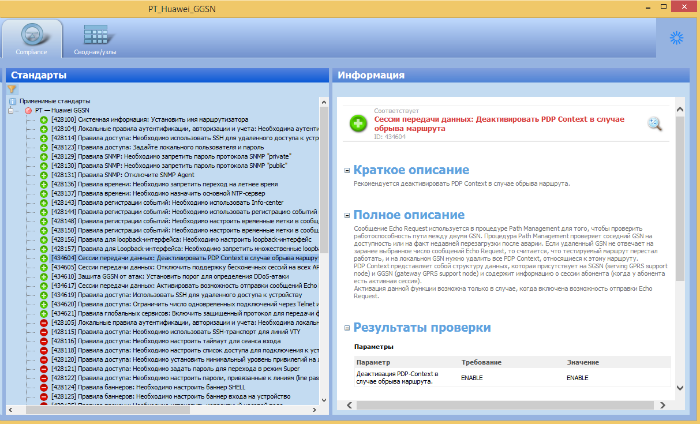
By the way, for lovers of conspiracy it is another interesting detail from the Symantec report. A command file was found in the user module of the Regin Trojan, which has the following functionality:
Skip Russian or English Microsoft files when scanning- that is, for some reason, a spyware program is not interested in files in Russian and English. In this regard, some experts suggest that the main goal of this trojan is not Russia, but other countries are Arab. However, the idea is controversial. After all, we are talking only about one of the configurations of the Trojan, which fell into Symantec. As the researchers themselves note, this spyware software provides ample opportunities for sharpening for a specific “client”.
Source: https://habr.com/ru/post/244073/
All Articles