Access certification: reduce risks, armed with relevant data
Internal policies and rules of the company require managers to constantly monitor the relevance of the level of employee access. For healthcare organizations, government departments, financial institutions, any joint-stock companies and enterprises that accept credit cards for payment, this is a task of key importance. Incorrect organization of the process of certification of access rights can be very expensive for a company. The consequences can be different: from "only" the deterioration of the image to the fall of the shares, fines, or even civil and criminal lawsuits. Let's look at the challenges associated with access certification and how to solve them.
Certification
In most organizations, access certification is a boring mechanical job. To determine whether the employee still works in the company and if he needs the access rights that he has, IT managers have to look at long lists in spreadsheets. Most often, they have no idea what information is available to each individual employee, and can only speculate: once a person is still working in a company, access can be confirmed. The situation is worsened by the presence in the “check all” checkboxes in such lists, which saves managers time: simply select this option and the job is done.
But does “blind certification” pose any threat when managers distribute access rights without knowing their relevance? Well, is it true that bad things can happen? In fact, this approach is fraught with serious trouble. Let us give an example: in October 2010, former trader of Societe Generale, Jerome Kerviel, was sentenced to three years in prison and paid 4.9 billion euros. As it turned out, Kervier performed risky stock exchange transactions without management control and used for this the passwords that he had preserved from previous positions in the company.
Anything like this can happen in any organization if managers blindly leave access rights to employees on the basis that they are still working in the company. How, for example, to be with an employee who was recently transferred from another department? Leave him access to the files that were needed for his previous work, or is it still not worth doing?
')
Source of the problem
Often there are three reasons for the problems associated with certification:
Lack of information
Too often, managers, whose tasks include the revision of access rights, do not have a complete picture of what, in fact, needs to be revised. They can make sure that all employees still work in their departments or in the company as a whole, but usually they do not have details about the level of access of each individual person. Accordingly, there is no possibility to reliably find out whether the employee needs to retain his access rights. Instead, you have to blindly leave everything as it is.
Some organizations delegate certification to application developers, but they usually also do not have information on the current role of employees and the relevance of access levels. For example, if a developer a few years ago gave an access to an employee in response to an e-mail request, now he can only find the name of this employee in the list of the company's personnel department and make sure that the person is still working in this organization. Most likely, he does not have data on the current duties of this employee, as well as no information on whether the same level of access is needed to perform these duties. And what if a person was recently promoted or transferred to another department?
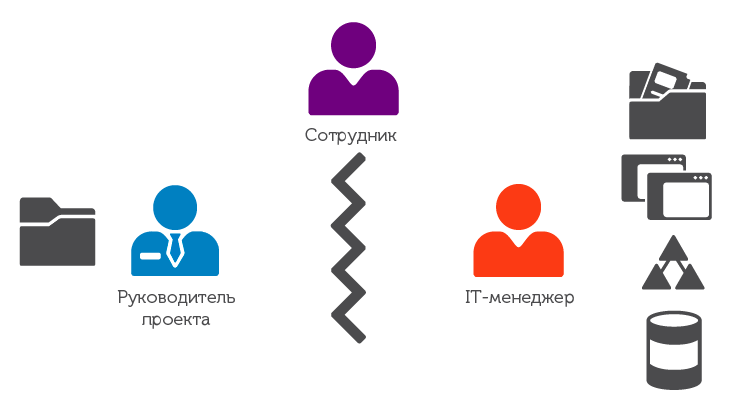
Fig. 1. Usually the project manager sees that the employee belongs to his team and performs certain duties, but does not know what kind of access rights he has. On the other hand, the IT manager sees which systems and applications are available to the employee, but he does not know either the duties of the employee or the need to access these or other applications.
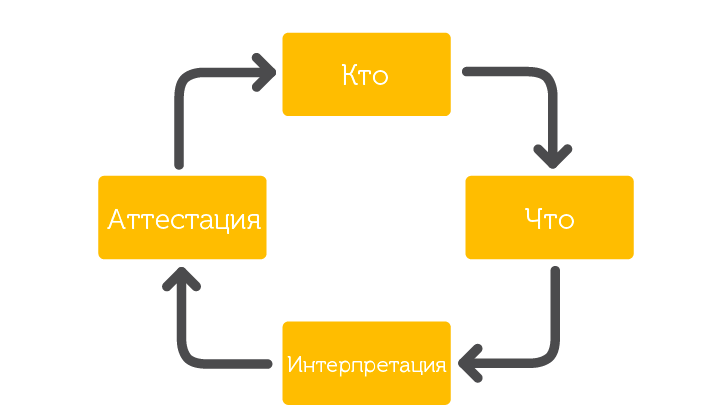
Fig. 2. Parts of the solution to the problem of access certification.
No matter who is involved in access certification, a project manager, or an application developer, in such situations, problems arise precisely because of a lack of information.
Misunderstanding
In other organizations, managers are provided with lists of all access rights for each specific employee (quite likely, generated by a self-made program). But not always these lists are easy to understand. Here is an example: the project manager sees that Vasily Pupkin has access to \\ DC7 \ C $ \, but will he understand what this means? Most likely, he will not know which server or shared folder is spoken about, whether Vasily has access to all the data on this server, and so on. Agree, the situation is ambiguous.

Fig. 3. The control panel of the manager displays the number of employees and their duties. On the presence of unsolved problems or problems encountered graphics in the form of traffic lights.
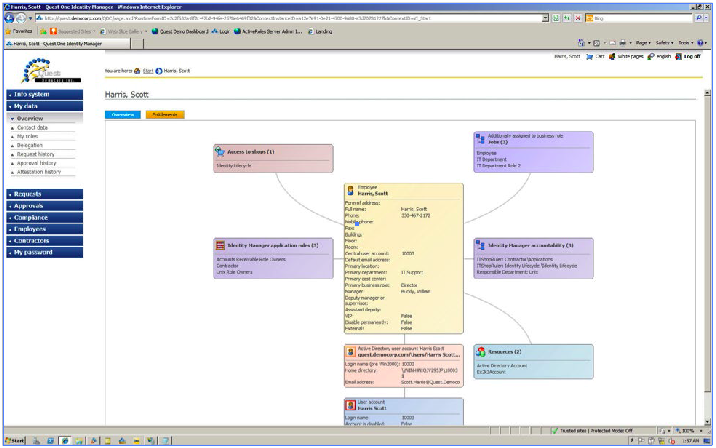
Fig. 4. The Entitlements tab displays all network elements that the employee has access to.
On the part of the IT-manager, too, there is a misunderstanding, but with exactly the opposite. It’s quite clear to him what \\ DC7 \ C $ \ is, but he doesn’t know what Vasily Pupkin is doing exactly, and whether he really needs access to \\ DC7 \ C $ \.
Lack of clearly defined certification process
In many organizations, the difficulties of access certification are shifted to automated systems. It is believed that if there is a well-established algorithm that automatically issues access rights and cancels them when an employee leaves, there is no need for regular certification. But in practice it does not work. Users are constantly given access to new programs and applications, and at the same time it is far from always canceled on time. The classic example is the transfer of an employee within a company, as is the case with the Societe Generale trader. Often, after a change in the position or duties of the employee, the old access remains simply because nobody has taken care to close it. The man is still working in the company, what's the problem?
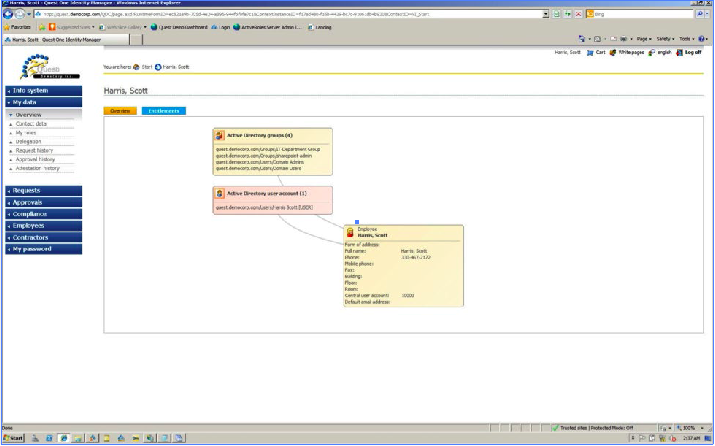
Fig. 5. Details on employee access Scott Harris: he belongs to the IT group, is a SharePoint administrator, administrator and domain user.
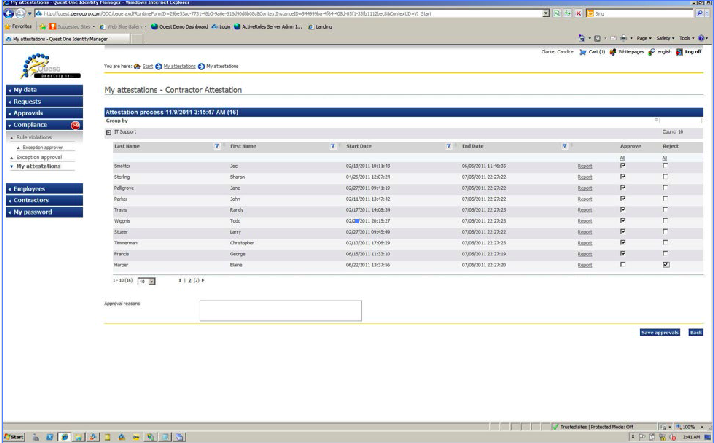
Fig. 6a. This example shows how manager Candace Clark expels Elaine Harper from the contractor team.
There is a lack of clear interaction between IT managers who see what access rights each individual employee has and project managers who understand the current responsibilities of their employees.
Optimal approach to access certification
Each problem has a solution if it is broken down into small parts, and access certification is no exception. The process can be divided into the following components:
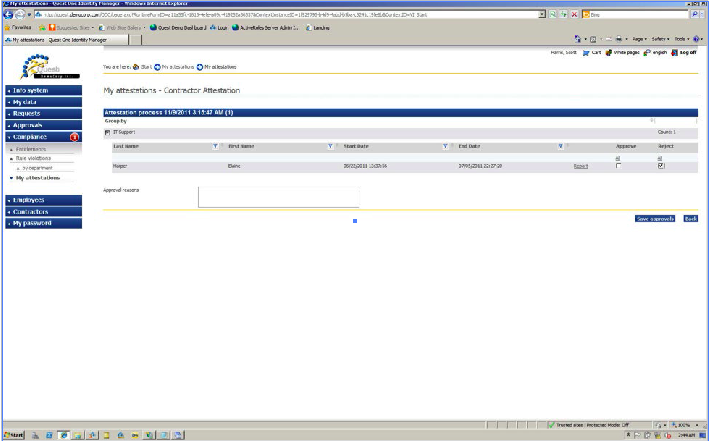
Fig. 6b. As soon as Candice Clark has removed Elaine Harper from the list of employees, administrator Scott Harris receives a notification of this with the "confirm" option. As soon as Scott confirms the exception, Elaine will immediately cancel the access rights.

Fig. 7. You can set a schedule for regular certification of employee access rights.
Who: determine the number of employees
The first step is to make sure that your list of employees is up to date. You need to rely on the list that made up the personnel department, because if a person no longer works in the company, they definitely know about it. Also, personnel officers should clarify the structure of departments in order to involve project managers in the certification process. One cannot do without their participation, because they know the duties of their employees and the level of access they need.
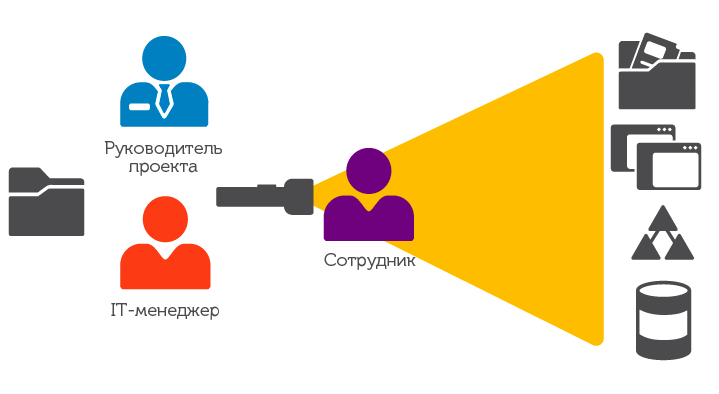
Fig. 8. With the help of suitable tools, both project managers and IT managers can clearly see which network resources each employee has access to. This will allow them to make informed decisions about access certification.
What: determine what access is required
The next step will be to identify all potential levels of admission and detailed consideration of which of them each individual employee already has. For many, this item may turn out to be the most time consuming, since it is necessary to obtain a list of users from the administrators responsible for each application, the “shared” folder, etc. If you already have a similar list, sorted by department or official duties, it should also be taken into account.
Interpretation: “translate” the names of all network elements into an understandable language
To prevent “blind certification”, this step is critical. As already mentioned, the project manager can see that the employee has access to the server, but does not understand the code by which it is designated. The project manager must clearly understand what he is giving access to, and not “blindly” assume that everything is in order.
Certification: Determine whether the user needs access
All previous steps provided the basis for correct access certification. A clear vision of who is granted access, which employee’s current rights, as well as the clear names of each admission (and not just the code in the table) help determine whether the requested level of access is needed to perform an employee’s current duties.
Conclusion
Certification of access in many organizations creates difficulties due to lack of information, misunderstanding and lack of a well-established process. Project managers understand the responsibilities of their team, but not their access rights, and IT managers, on the contrary, see the access rights of employees, but do not know their current responsibilities. In addition, it is simply impossible to replace the interaction between IT and project managers with an automated process. Since “blind” certification usually puts the organization at serious risk, a new look at the difficulties associated with access certification is needed.
Dell One Identity provides a clear, comprehensive view of employees and their level of access in an easy-to-understand format. Clear process organization and suitable certification tools allow companies to save time and provide better network protection and compliance with the needs of the organization.
Detailed information about the Dell One Identity can be found here .
Certification
In most organizations, access certification is a boring mechanical job. To determine whether the employee still works in the company and if he needs the access rights that he has, IT managers have to look at long lists in spreadsheets. Most often, they have no idea what information is available to each individual employee, and can only speculate: once a person is still working in a company, access can be confirmed. The situation is worsened by the presence in the “check all” checkboxes in such lists, which saves managers time: simply select this option and the job is done.
But does “blind certification” pose any threat when managers distribute access rights without knowing their relevance? Well, is it true that bad things can happen? In fact, this approach is fraught with serious trouble. Let us give an example: in October 2010, former trader of Societe Generale, Jerome Kerviel, was sentenced to three years in prison and paid 4.9 billion euros. As it turned out, Kervier performed risky stock exchange transactions without management control and used for this the passwords that he had preserved from previous positions in the company.
Anything like this can happen in any organization if managers blindly leave access rights to employees on the basis that they are still working in the company. How, for example, to be with an employee who was recently transferred from another department? Leave him access to the files that were needed for his previous work, or is it still not worth doing?
')
Source of the problem
Often there are three reasons for the problems associated with certification:
- Lack of information.
- Misunderstanding of information with which to deal.
- Lack of clearly defined access certification process.
Lack of information
Too often, managers, whose tasks include the revision of access rights, do not have a complete picture of what, in fact, needs to be revised. They can make sure that all employees still work in their departments or in the company as a whole, but usually they do not have details about the level of access of each individual person. Accordingly, there is no possibility to reliably find out whether the employee needs to retain his access rights. Instead, you have to blindly leave everything as it is.
Some organizations delegate certification to application developers, but they usually also do not have information on the current role of employees and the relevance of access levels. For example, if a developer a few years ago gave an access to an employee in response to an e-mail request, now he can only find the name of this employee in the list of the company's personnel department and make sure that the person is still working in this organization. Most likely, he does not have data on the current duties of this employee, as well as no information on whether the same level of access is needed to perform these duties. And what if a person was recently promoted or transferred to another department?

Fig. 1. Usually the project manager sees that the employee belongs to his team and performs certain duties, but does not know what kind of access rights he has. On the other hand, the IT manager sees which systems and applications are available to the employee, but he does not know either the duties of the employee or the need to access these or other applications.

Fig. 2. Parts of the solution to the problem of access certification.
No matter who is involved in access certification, a project manager, or an application developer, in such situations, problems arise precisely because of a lack of information.
Misunderstanding
In other organizations, managers are provided with lists of all access rights for each specific employee (quite likely, generated by a self-made program). But not always these lists are easy to understand. Here is an example: the project manager sees that Vasily Pupkin has access to \\ DC7 \ C $ \, but will he understand what this means? Most likely, he will not know which server or shared folder is spoken about, whether Vasily has access to all the data on this server, and so on. Agree, the situation is ambiguous.

Fig. 3. The control panel of the manager displays the number of employees and their duties. On the presence of unsolved problems or problems encountered graphics in the form of traffic lights.

Fig. 4. The Entitlements tab displays all network elements that the employee has access to.
On the part of the IT-manager, too, there is a misunderstanding, but with exactly the opposite. It’s quite clear to him what \\ DC7 \ C $ \ is, but he doesn’t know what Vasily Pupkin is doing exactly, and whether he really needs access to \\ DC7 \ C $ \.
Lack of clearly defined certification process
In many organizations, the difficulties of access certification are shifted to automated systems. It is believed that if there is a well-established algorithm that automatically issues access rights and cancels them when an employee leaves, there is no need for regular certification. But in practice it does not work. Users are constantly given access to new programs and applications, and at the same time it is far from always canceled on time. The classic example is the transfer of an employee within a company, as is the case with the Societe Generale trader. Often, after a change in the position or duties of the employee, the old access remains simply because nobody has taken care to close it. The man is still working in the company, what's the problem?

Fig. 5. Details on employee access Scott Harris: he belongs to the IT group, is a SharePoint administrator, administrator and domain user.

Fig. 6a. This example shows how manager Candace Clark expels Elaine Harper from the contractor team.
There is a lack of clear interaction between IT managers who see what access rights each individual employee has and project managers who understand the current responsibilities of their employees.
Optimal approach to access certification
Each problem has a solution if it is broken down into small parts, and access certification is no exception. The process can be divided into the following components:

Fig. 6b. As soon as Candice Clark has removed Elaine Harper from the list of employees, administrator Scott Harris receives a notification of this with the "confirm" option. As soon as Scott confirms the exception, Elaine will immediately cancel the access rights.

Fig. 7. You can set a schedule for regular certification of employee access rights.
Who: determine the number of employees
The first step is to make sure that your list of employees is up to date. You need to rely on the list that made up the personnel department, because if a person no longer works in the company, they definitely know about it. Also, personnel officers should clarify the structure of departments in order to involve project managers in the certification process. One cannot do without their participation, because they know the duties of their employees and the level of access they need.

Fig. 8. With the help of suitable tools, both project managers and IT managers can clearly see which network resources each employee has access to. This will allow them to make informed decisions about access certification.
What: determine what access is required
The next step will be to identify all potential levels of admission and detailed consideration of which of them each individual employee already has. For many, this item may turn out to be the most time consuming, since it is necessary to obtain a list of users from the administrators responsible for each application, the “shared” folder, etc. If you already have a similar list, sorted by department or official duties, it should also be taken into account.
Interpretation: “translate” the names of all network elements into an understandable language
To prevent “blind certification”, this step is critical. As already mentioned, the project manager can see that the employee has access to the server, but does not understand the code by which it is designated. The project manager must clearly understand what he is giving access to, and not “blindly” assume that everything is in order.
Certification: Determine whether the user needs access
All previous steps provided the basis for correct access certification. A clear vision of who is granted access, which employee’s current rights, as well as the clear names of each admission (and not just the code in the table) help determine whether the requested level of access is needed to perform an employee’s current duties.
Conclusion
Certification of access in many organizations creates difficulties due to lack of information, misunderstanding and lack of a well-established process. Project managers understand the responsibilities of their team, but not their access rights, and IT managers, on the contrary, see the access rights of employees, but do not know their current responsibilities. In addition, it is simply impossible to replace the interaction between IT and project managers with an automated process. Since “blind” certification usually puts the organization at serious risk, a new look at the difficulties associated with access certification is needed.
Dell One Identity provides a clear, comprehensive view of employees and their level of access in an easy-to-understand format. Clear process organization and suitable certification tools allow companies to save time and provide better network protection and compliance with the needs of the organization.
Detailed information about the Dell One Identity can be found here .
Source: https://habr.com/ru/post/244051/
All Articles