Korplug RAT is used in targeted attacks against users of Afghanistan and Tajikistan.
Korplug RAT is a remote access tool, also known as PlugX . Recently, we paid more attention to the attackers' campaigns to spread this malicious program. One of these campaigns is used to carry out targeted attacks on Afghanistan and Tajikistan.

Often, in targeted attacks, attackers resort to the services of new modifications of malware. Further, the detection of such malware can help unambiguously identify the source of the attack, i.e. the cybercrime group. As an example, you can take the latest modification of the BlackEnergy malware (BlackEnergy Lite aka BlackEnergy 3). This modification was used in targeted attacks on Ukraine and Eastern European countries by a group of cybercriminals called Quedagh or Sandworm. It clearly differed from its previous second version, numerous files of which can still be found on users' computers.
')
In other cases, attackers use more common tools to achieve their criminal goals. For example, the Korplug RAT , which is a widely known malicious tool, has been repeatedly used by Chinese APT groups since 2012 to conduct targeted attacks. Over the past few weeks, we have seen a large number of Korplug detections in many unrelated incidents.
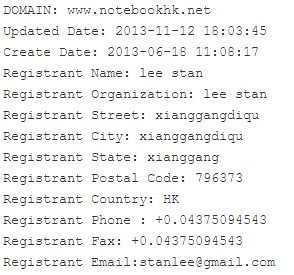
Among these infections, we were able to detect several successful infections, where the Korplug samples used interacted with one C & C server.
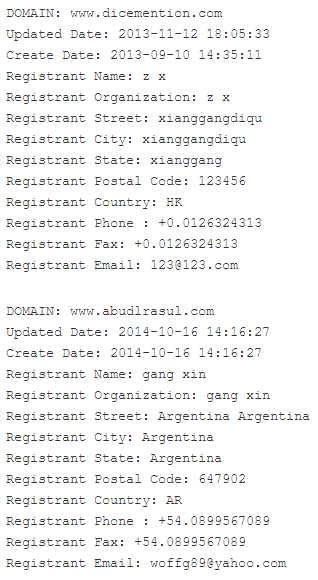
Other malware samples interacted with C & C servers whose addresses differ from the above, but they belong to the same IP address.
By taking these C & C server addresses as a starting point, we were able to detect a certain number of malware victims who were infected using various fake documents. These documents were sent in phishing messages and contained exploits. In addition, for the same purpose, self-extracting RAR archives with the .SCR extension were used.

A fake document might look like this.

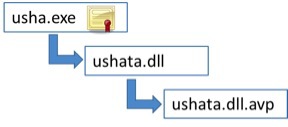
In all these cases, as a result of successful exploitation of the vulnerability, three new files are written to the disk, and the malicious component Korplug is loaded into memory.
Malicious software Korplug RAT uses a special method to deceive AV-products, which is to use the executable file of any security product that allows you to load the externally specified dynamic library into memory.
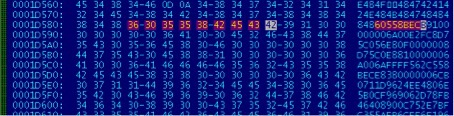
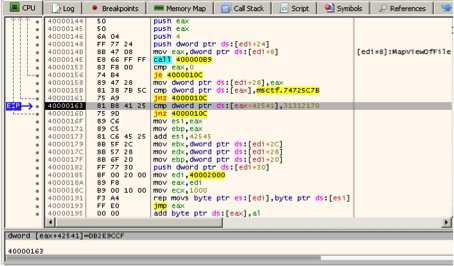
The above RTF documents are exploits for CVE-2012-0158 in MS Word. The screenshot below shows the beginning of the exploit's shellcode to this vulnerability; the specified ASCII characters correspond to the pusha instructions ; push ebp; mov ebp, esp .
It is interesting to note that these documents also contain an exploit for a newer vulnerability CVE-2014-1761 , which has been repeatedly used by attackers in targeted attacks to deliver such malicious programs as BlackEnergy , Sednit , MiniDuke , etc. However, this exploit was not properly developed and contained an invalid pointer in the shellcode instructions.
Below in the screenshot we see the instructions of the shellcode, which is executed at the first stage of the exploit. The instructions verify the presence of the “p! 11” tag, from which the new instructions of the second stage of the shell code begin. After that, he tries to load them into memory. Even in the presence of this tag and the shell code in memory, it is located at a different offset, that is, different from the one that the malware is trying to use.
We were able to detect the victims of Korplug in the following countries.
From the topic of the above documents, which were used to distribute malware, it can be argued that the attackers were interested in collecting intelligence information on military and diplomatic topics. You can also note the following pattern: other malicious programs were found on the victims' computers, including remote access tools (RAT), Trojans, keyloggers. One of these malicious programs interacted with a remote server, the domain address of which coincided with the same address that was used in the Korplug samples.
Since the capabilities of these malicious programs overlapped with the capabilities of Korplug , it is not quite clear to us why they were used by attackers. Perhaps they were just experimenting with different types of malware, or they were used to perform those tasks that cannot be performed by Korplug functions. Together with Korplug , on infected computers, the two below mentioned families of malicious programs were most common.
DarkStRat
This malware is also another remote access tool (RAT). His research shows DarkStRat's relationship with China and Spain. In particular, the commands given by the bots are written in Spanish. In parentheses is their translation into Russian.
DarkStRat malware can manage processes and services on an infected machine, transfer files to a remote server and copy them from there, follow the instructions of the command interpreter, etc. The Delphi language was used to write DarkStRat , one of the modifications is connected to the dicemention.com domain. Also, some samples of this malware are digitally signed by Nanning weiwu Technology co., Ltd.
File stealer
Another type of malware that often met with Korplug . This malware is written in C and contains functions for stealing files from hard drives of infected computers. The list of such files is specified in a special configuration file. In addition to recursively searching for these files on hard drives, it is able to track the connection to the system of removable media and network folders, waiting for a special system event DBT_DEVICEARRIVAL.
In addition to its functions of stealing files and transferring them to a remote server of attackers, this malicious program specializes in stealing passwords stored by a user on a computer from various Internet accounts, as well as a list of URLs visited by a user in the browser and information about accounts used in the following applications.
The malware uses the following domains to communicate with the C & C server manager.
Some samples of this File Stealer are signed by the already mentioned digital certificate issued by Nanning weiwu Technology co., Ltd.

Often, in targeted attacks, attackers resort to the services of new modifications of malware. Further, the detection of such malware can help unambiguously identify the source of the attack, i.e. the cybercrime group. As an example, you can take the latest modification of the BlackEnergy malware (BlackEnergy Lite aka BlackEnergy 3). This modification was used in targeted attacks on Ukraine and Eastern European countries by a group of cybercriminals called Quedagh or Sandworm. It clearly differed from its previous second version, numerous files of which can still be found on users' computers.
')
In other cases, attackers use more common tools to achieve their criminal goals. For example, the Korplug RAT , which is a widely known malicious tool, has been repeatedly used by Chinese APT groups since 2012 to conduct targeted attacks. Over the past few weeks, we have seen a large number of Korplug detections in many unrelated incidents.
Among these infections, we were able to detect several successful infections, where the Korplug samples used interacted with one C & C server.

Other malware samples interacted with C & C servers whose addresses differ from the above, but they belong to the same IP address.

By taking these C & C server addresses as a starting point, we were able to detect a certain number of malware victims who were infected using various fake documents. These documents were sent in phishing messages and contained exploits. In addition, for the same purpose, self-extracting RAR archives with the .SCR extension were used.

A fake document might look like this.

In all these cases, as a result of successful exploitation of the vulnerability, three new files are written to the disk, and the malicious component Korplug is loaded into memory.

- exe is a legitimate executable file that is digitally signed by one of the security companies (a legitimate file) and loads the dynamic library into memory;
- dll - a small loader, made in the form of a dynamically connected library;
- dll.avp - file with executable code Korplug .
Malicious software Korplug RAT uses a special method to deceive AV-products, which is to use the executable file of any security product that allows you to load the externally specified dynamic library into memory.
The above RTF documents are exploits for CVE-2012-0158 in MS Word. The screenshot below shows the beginning of the exploit's shellcode to this vulnerability; the specified ASCII characters correspond to the pusha instructions ; push ebp; mov ebp, esp .

It is interesting to note that these documents also contain an exploit for a newer vulnerability CVE-2014-1761 , which has been repeatedly used by attackers in targeted attacks to deliver such malicious programs as BlackEnergy , Sednit , MiniDuke , etc. However, this exploit was not properly developed and contained an invalid pointer in the shellcode instructions.
Below in the screenshot we see the instructions of the shellcode, which is executed at the first stage of the exploit. The instructions verify the presence of the “p! 11” tag, from which the new instructions of the second stage of the shell code begin. After that, he tries to load them into memory. Even in the presence of this tag and the shell code in memory, it is located at a different offset, that is, different from the one that the malware is trying to use.

We were able to detect the victims of Korplug in the following countries.
- Afghanistan
- Tajikistan
- Russia
- Kyrgyzstan
- Kazakhstan
From the topic of the above documents, which were used to distribute malware, it can be argued that the attackers were interested in collecting intelligence information on military and diplomatic topics. You can also note the following pattern: other malicious programs were found on the victims' computers, including remote access tools (RAT), Trojans, keyloggers. One of these malicious programs interacted with a remote server, the domain address of which coincided with the same address that was used in the Korplug samples.
Since the capabilities of these malicious programs overlapped with the capabilities of Korplug , it is not quite clear to us why they were used by attackers. Perhaps they were just experimenting with different types of malware, or they were used to perform those tasks that cannot be performed by Korplug functions. Together with Korplug , on infected computers, the two below mentioned families of malicious programs were most common.
DarkStRat
This malware is also another remote access tool (RAT). His research shows DarkStRat's relationship with China and Spain. In particular, the commands given by the bots are written in Spanish. In parentheses is their translation into Russian.
- CERRAR (close)
- DESINSTALAR (remove)
- SERVIDOR (server)
- INFO
- MAININFO
- Ping
- REBOOT
- POWEROFF
- PROC
- KILLPROC
- VERUNIDADES (view units)
- LISTARARCHIVOS (get file list)
- EXEC
- DELFILE
- DELFOLDER
- RENAME
- MKDIR
- CAMBIOID (change id)
- GETFILE / SENDFILE / RESUMETRANSFER
- SHELL
- SERVICIOSLISTAR (get the list of services)
- INICIARSERVICIO (start the service)
- DETENERSERVICIO (stop service)
- BORRARSERVICIO (remove service)
- INSTALARSERVICIO (install service)
DarkStRat malware can manage processes and services on an infected machine, transfer files to a remote server and copy them from there, follow the instructions of the command interpreter, etc. The Delphi language was used to write DarkStRat , one of the modifications is connected to the dicemention.com domain. Also, some samples of this malware are digitally signed by Nanning weiwu Technology co., Ltd.
File stealer
Another type of malware that often met with Korplug . This malware is written in C and contains functions for stealing files from hard drives of infected computers. The list of such files is specified in a special configuration file. In addition to recursively searching for these files on hard drives, it is able to track the connection to the system of removable media and network folders, waiting for a special system event DBT_DEVICEARRIVAL.
In addition to its functions of stealing files and transferring them to a remote server of attackers, this malicious program specializes in stealing passwords stored by a user on a computer from various Internet accounts, as well as a list of URLs visited by a user in the browser and information about accounts used in the following applications.
- Microsoft Messenger
- Microsoft Outlook
- Microsoft Internet Explorer
- Mozilla firefox
The malware uses the following domains to communicate with the C & C server manager.
- newvinta.com
- worksware.net
Some samples of this File Stealer are signed by the already mentioned digital certificate issued by Nanning weiwu Technology co., Ltd.
Source: https://habr.com/ru/post/243603/
All Articles