Vulnerability in one of the Alfa-Bank services allowed to view statements for any client
A month ago, while looking at Alfa-Bank’s mobile Internet banking application, I decided to check how secure it was.

Since I am a customer of this bank, I was wondering if they pay due attention to the safe storage of customer data. I will clarify that I am a client of the Ukrainian branch and, accordingly, had the opportunity to check only that part of the mobile application that is intended for Ukrainian clients.
')

To track the traffic sent by the mobile application to the server, install Fiddler .
The program is extremely easy to use, installed and configured according to the instructions quite easily. Additionally, in the program settings you need to enable decrypting https traffic
In the phone, in the wi-fi settings, you need to specify the proxy address raised by this application and in order for the program to decrypt mobile HTTPS traffic, we need to additionally install a certificate ( IOS , Android ).
After all these actions, we launch Fiddler and Alfa-Bank mobile application. Now all requests sent by the mobile phone will be displayed in Fiddler. In our case, this turned out to be the SOAP protocol with requests in XML format.
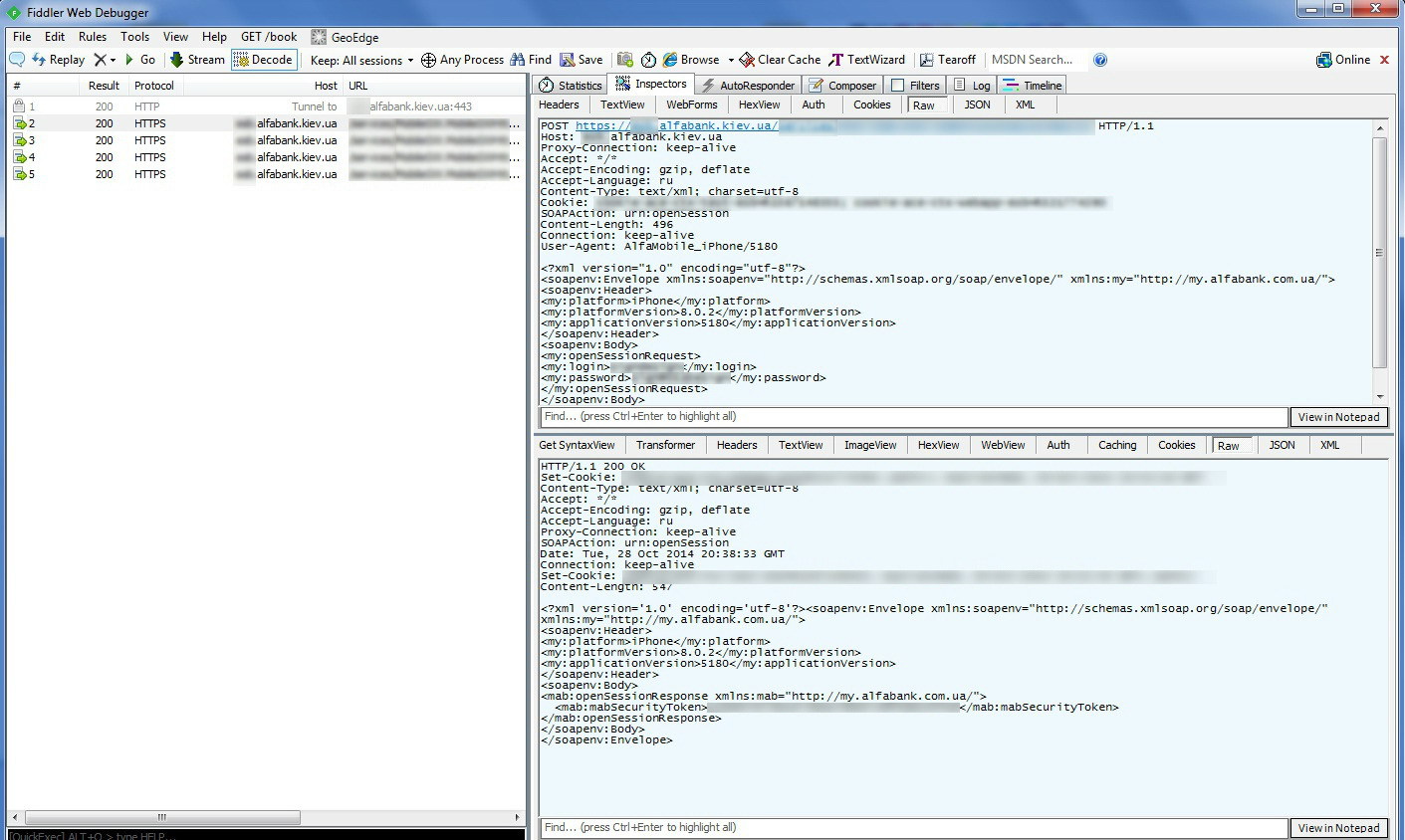
I was looking for typical mistakes that developers make. The most common of these is the lack of access permissions when querying using an identifier. We search for errors as follows. We take a mobile application request, logged by Fiddler and reproduce it in the Google Chrome browser using the “Postman” plugin:

In this request, we replace the integer identifier with a larger or smaller value and check the server response. If the server returns an error or an empty request, then everything is fine; if the client data, then there is a vulnerability. It did not take long to search. When requesting the formation of statements, there was no check for access rights. For data access, an identifier such as cardContractId was used. By increasing or decreasing its value, it was possible to receive extracts from other users.
On the same day, I sent a message about the found vulnerability via the Alfa-Bank website, but within a few days, without receiving an answer, I called the customer service and asked the security service to contact me. It is necessary to pay tribute, the officer of the Security Council called me back on the same day and after a little more than a week the vulnerability was eliminated.
However, I would like to refer to the management of the division of the bank responsible for developing software products. Bank services are actively developing and acquiring functionality, in which, whether you like it or not, vulnerabilities appear. Existing communication channels practically do not react when sending requests in electronic form. For example, my two reports on XSS vulnerabilities on other Alfa-Bank resources, filed a few months ago, remained unanswered.
Organize a separate communication channel for filing applications on the found vulnerabilities and create a reward program. Such programs exist in Google, Amazon, Yandex, and even Privatbank, and they very effectively help in quickly closing security holes. Do not wait until the attackers begin to exploit the found vulnerabilities and customers will inform you about the problems already in fact.

Since I am a customer of this bank, I was wondering if they pay due attention to the safe storage of customer data. I will clarify that I am a client of the Ukrainian branch and, accordingly, had the opportunity to check only that part of the mobile application that is intended for Ukrainian clients.
')

Training
To track the traffic sent by the mobile application to the server, install Fiddler .
The program is extremely easy to use, installed and configured according to the instructions quite easily. Additionally, in the program settings you need to enable decrypting https traffic
In the phone, in the wi-fi settings, you need to specify the proxy address raised by this application and in order for the program to decrypt mobile HTTPS traffic, we need to additionally install a certificate ( IOS , Android ).
After all these actions, we launch Fiddler and Alfa-Bank mobile application. Now all requests sent by the mobile phone will be displayed in Fiddler. In our case, this turned out to be the SOAP protocol with requests in XML format.

Now a little about the process of finding vulnerabilities
I was looking for typical mistakes that developers make. The most common of these is the lack of access permissions when querying using an identifier. We search for errors as follows. We take a mobile application request, logged by Fiddler and reproduce it in the Google Chrome browser using the “Postman” plugin:

In this request, we replace the integer identifier with a larger or smaller value and check the server response. If the server returns an error or an empty request, then everything is fine; if the client data, then there is a vulnerability. It did not take long to search. When requesting the formation of statements, there was no check for access rights. For data access, an identifier such as cardContractId was used. By increasing or decreasing its value, it was possible to receive extracts from other users.
On the same day, I sent a message about the found vulnerability via the Alfa-Bank website, but within a few days, without receiving an answer, I called the customer service and asked the security service to contact me. It is necessary to pay tribute, the officer of the Security Council called me back on the same day and after a little more than a week the vulnerability was eliminated.
However, I would like to refer to the management of the division of the bank responsible for developing software products. Bank services are actively developing and acquiring functionality, in which, whether you like it or not, vulnerabilities appear. Existing communication channels practically do not react when sending requests in electronic form. For example, my two reports on XSS vulnerabilities on other Alfa-Bank resources, filed a few months ago, remained unanswered.
Organize a separate communication channel for filing applications on the found vulnerabilities and create a reward program. Such programs exist in Google, Amazon, Yandex, and even Privatbank, and they very effectively help in quickly closing security holes. Do not wait until the attackers begin to exploit the found vulnerabilities and customers will inform you about the problems already in fact.
Source: https://habr.com/ru/post/243105/
All Articles