Own tor2web-service using Nginx and Lua

We will discuss how to make a gateway from the Internet to hidden sites Tor.
The Tor network is a proxy server system that allows you to establish an anonymous network connection. With Tor, you can anonymously connect to regular servers and host non-listenable servers on the Tor network itself. In the latter case, a hidden server is created in the onion zone. The server name includes 16 letters and numbers (fingerprint).

')
How can I access hidden servers:
- install Tor and send browser traffic through it. The Tor Browser is a portable application that includes everything you need;
- However, not all people install the Tor browser, so you need a way to show the contents of the hidden server to the average user on the network. Tor2web services that provide direct access to hidden sites come to the rescue.
Hidden Wiki site ( kpvzxxbbraaigawj.onion ) can be opened in a regular browser ( kpvzxxbbraaigawj.tor2web.fi ). If the user connects to the site via tor2web, then he loses anonymity in exchange for access to a hidden site without installing Tor. I will give a list of similar services, some of which are closed.
- * .Tor2web.org (3 servers)
- * .Tor2web.fi
- * .Tor2web.blutmagie.de
- * .onion.sh (disabled)
- * .onion.to (disabled)
- * .onion.lu (disabled)
- * .t2w.pw (disabled)
- * .tor2web.ae.org (disabled)
Consider existing ways to run tor2web-service, after which I will share my own.
Project Tor2web-3.0?

Tor2web-3.0 is an important part of the GlobaLeaks project, which facilitates network users access to hidden servers.
Site example: kpvzxxbbraaigawj.tor2web.org
3 servers are connected to the Tor2web-3.0 project. You can install Tor2web on your server and join their network. Disconnected .lu and .to servers belong to the same people.
Tor2web-3.0 is installed as a separate service. The code is written in Python. There were practically no complaints about Tor2web-3.0, but I wanted to avoid an additional participant (user - Nginx - Tor2web-3.0 - Tor - the target site). In addition, I do not like network software written in Python.
Polipo?
Polipo is an HTTP server that can redirect connections to a SOCK5 server. Previously, Polipo was used for this purpose as part of a Tor browser.
It would be possible to build a chain: Nginx - Polipo - Tor. As in the case of Tor2web-3.0, there is an extra participant, since Nginx cannot proxy traffic through the SOCK5 server. In addition, for the normal display of sites, I would like to replace the onion-link in the server response with links to the gateway: s / .onion / .onion.xx /
Patch Nginx?
There is a patch for Nginx that adds the ability to proxy traffic through a SOCK5 server. In fact, the SOCKS5 protocol is very simple, so it is strange that there is still no official module. This solution looks tempting, but it is not brought to mind: Nginx would have to be patched with every update. I want to have a solution that would work on a regular Nginx from
Writing a module for Nginx on Lua

Nginx has long supported the ability to embed scripts on Lua. The Lua code is provided with a wide range of possibilities, including manipulation with direct access sockets. Unfortunately, I did not find the module for connecting to the SOCKS5 server, so I wrote my own . For each request, a connection to the Tor program is established through port 9050, a SOCKS5 handshake takes place and the address of the target site is transmitted. After this, the socket is used as if it were a direct socket to the target site. User request is read into memory, edited and transmitted to the server. The server response is read, edited (replacing links) and transmitted to the user. All operations are non-blocking. I designed this part as a separate onion2web module.
When you first connect to the site, the user sees a stub with a form to confirm the visit to the site. It is necessary that it was impossible to include images from hidden services in the pages of ordinary sites.
The socks5 module contains functions by which the socket is forwarded through the SOCK5 server. Functions are described on the module page . The onion2web module contains one function handle_onion2web, which serves the tor2web gateway. See usage example below. It is possible to set the address and port totor and disable the form of confirmation of entry to the site.
Flaws:
- a very simple HTTP client version 1.0 is implemented, in which keep-alive and compression of transmitted data are disabled.
- The request and the answer are read entirely in memory, and then transferred to the recipient. This increases memory consumption and slows down the transfer of information, especially in the direction from the site to the user. I suspect that you need to communicate with the SOCKS5 server in a separate coroutine . Difficulties will arise with the substitution of addresses in the server response (the boundary of data blocks may fall on the address being replaced).
- The form of the dagger does not contain protection from CSRF and always redirects to the main page (it is better to redirect to the path that was originally opened).
- The server's response must be edited more carefully: replace links only in HTML and only in attributes.
I stopped at this variant and used it for my tor2web gateway . The disadvantages of the site itself include the absence of SSL. I think there are other disadvantages. And in general, while the decision is rather a crutch.
How to raise your tor2web gateway
Looking for a domain, server and wildcard SSL certificate for this domain.
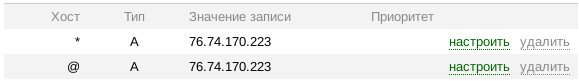
In the domain you need to register all the subdomains with the IP address of our server:
The server will require Tor, Nginx with a fresh ngx_lua and my onion2web module to connect to the SOCKS5 server from Nginx. Debian Wheezy has the nginx-extras package, which contains the ngx_lua too old. (This old ngx_lua does not support some of the methods used, for example, ngx.req.raw_header.) The nginx-extras version of wheezy-backports contains fairly fresh ngx_lua. The onion2web module can be installed via luarocks (this will automatically install the socks5 module as a dependency).
Installation for Debian Wheezy:
# echo deb http://ftp.us.debian.org/debian/ wheezy-backports main > /etc/apt/sources.list.d/wheezy-backports.list # apt-get update # apt-get install tor luarocks nginx-extras/wheezy-backports # luarocks install onion2web In Nginx we create the following site:
server { listen 80; server_name *.onion.gq; location / { default_type text/html; content_by_lua ' require("onion2web").handle_onion2web(".onion.gq"); '; } } The domain appears in the config in two places: server_name and inside the Lua-code.
Site ready: kpvzxxbbraaigawj.onion.gq
Sources of the socks5 module: github.com/starius/lua-resty-socks5
Sources of the onion2web module: github.com/starius/onion2web
Source: https://habr.com/ru/post/243055/
All Articles