Memo: How startups provide data protection in the cloud

Translator's note: Over the past few years, the topic of information security has finally ceased to be a lot of geeks and a specialist, and now everyone is interested. After Snowden's revelations, users of various online services began to think about the security of their data. Now companies that do not provide this security may face huge image and financial losses in the event of a hacker attack. Often, user credentials are stolen through third-party services (as was the case with Dropbox and Yandex ), but even in such a situation, a shadow falls on the company, and its customers remain unhappy.
However, not all creators of new projects pay proper attention to data protection (as a result, scandals arise, such as the situation with the anonymous Whisper application, the information of users of which was not as anonymous as expected).
')
Stephen Kochi, the main evangelist for security company Alert Logic, wrote a story about how startups approach information security when using cloud services.
Many years ago, when I created a security and development business, I had big plans and a small start-up capital. When I started working on the necessary infrastructure and development platforms, I quickly realized the real value of building a business. It was at the dawn of the 2000s, when the cloud infrastructure was not available: if you worked with something, you paid at full cost. Besides the fact that I had to hire staff, work directly on the project, understand finance, sell and be a marketer, I also had to create the infrastructure that my team needed to work.
If you are creating a startup in the cloud, then you most likely have your own list of critical business tasks. Cloud services are diverse, you can start to use them in the format of "self-service" - all this simplifies the implementation of many things. But even in this case, security often goes into the background. However, it is important to understand that the cloud is an extension of your business networks, regardless of whether you are aware of any of them or not. A security breach not only puts your internal network at risk, it can also threaten your customers' data.
Public Cloud Security Threats
Although using a public cloud has significant financial benefits, it, like any infrastructure, has its own set of threats. For several years, we have seen an increase in the frequency of attacks from the public cloud and the diversity of the malware used for this. With the increase in incidents related to tracking vulnerabilities, web applications and brute force attacks, it becomes critical to build an understanding of the types of threats specific to the cloud - thanks to this, you can create a suitable comprehensive security strategy to protect your ecosystem from attacks.
Model of separation of responsibilities for security
In a public cloud, the key to security is a clear understanding of the existence of a security sharing model between you (the client) and the service provider. Without this understanding, you may be misguided that your provider will protect you, while the responsibility for certain security functions will in fact lie with you.
For example, your service provider is responsible for 100% of the core services, such as computing power, data storage, databases, network services. At the network level, your service provider is responsible for network segmentation, perimeter protection services, protection against DDOS attacks and spoofing. But you, the end user, are responsible for detecting network threats, notifying the service provider about them and any other [security related] incidents. At the host level, you are responsible for managing access, updates, strengthening and monitoring security systems and analyzing log files. The components of your web application are 100% your responsibility. To understand the division of responsibility between you and your provider, look at the chart below:
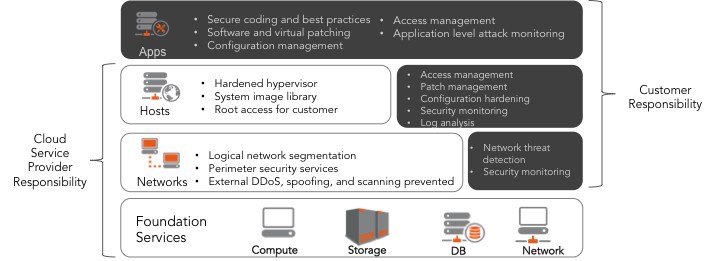
Understanding your role and the role of your cloud provider will not only help you make the most appropriate decision regarding cloud infrastructure, it will help your cybersecurity strategy to effectively and economically protect your data from threats in the cloud immediately after its implementation.
Best cloud security practices
Keep your code safe
Code security is 100% your responsibility. First, make sure that security is part of your software development lifecycle (SDLC). To do this, formulate a task list like this:
- Make sure that your code is constantly updated and that you are using the latest plug-ins.
- Use program control over the speed of operations to avoid becoming a victim of a botnet.
- Use encryption wherever possible.
- Test all libraries and solutions that involve third-party development.
- Be aware of all possible vulnerabilities of the products you use.
- Finally, constantly check the code after adding updates.
Create Access Control Policies
First, determine what is in your assets. Once you have your list, define the roles and responsibilities required to access the assets. Centralize authentication whenever possible — to implement authentication, start with a privilege assignment model.
Use update management techniques
Again, formulate a list of important procedures:
- Make a list of your resources.
- If possible, develop a plan for their standardization.
- Do research for vulnerabilities that could affect you. Classify risks based on the types of vulnerabilities and the likelihood of their occurrence.
- If possible, test updates before their release.
- Set a schedule for regular updates and do not forget to include third-party products that require manual updates to be installed.
Log Management
Logs are currently not only useful for controlling costs; they are becoming a serious security tool. You can use log data to track malicious activity and to investigate. The essence of the process of turning logs into an effective tool for security is continuous monitoring, which is necessary to search for anomalous behavior.
Build your security toolkit - you should treat your cloud as a business network. You need to implement a comprehensive security strategy that covers all areas of your responsibility. Use IP tables, web application firewalls, antivirus, intrusion detection system, encryption and log management. Explore new security options and make sure that the solutions you use are optimal for your business.
Stay informed - you need to stay informed of all the vulnerabilities that may arise in your ecosystem. The sites listed below contain some of the best material on this topic. These resources can help you be aware of emerging and spreading vulnerabilities, exploits and attacks:
- securityfocus.com
- www.exploit-db.com
- seclists.org/fulldisclosure
- www.securitybloggersnetwork.com
- www.sans.org
- www.nist.gov
*** In Russian, vulnerabilities are discussed at www.securitylab.ru , xakep.ru (plus the corresponding section on Habré).
Know your service provider
Finally, find out exactly how security responsibility is distributed between you and your particular provider, and what it can offer in terms of your security. It is also necessary to constantly test the system to ensure that a high level of security is maintained.
Posts and related links:
Source: https://habr.com/ru/post/243001/
All Articles